About the features of scanning executable files by antiviruses and trusting the results of VirusTotal
Hello. Below will be a lot of silly text, nostalgic memories and shkolotnogo code. In addition, the effectiveness of the VirusTotal service, as well as anti-virus engines with respect to executable files, will be considered.
Part 1. Delusional-nostalgic entry
A lot has changed in my life. I became interested (in places - before lack of sleep) my current work, there has been a war in my region for the fourth year, a lot has changed and rethought in my personal life.
Many views and opinions have changed.
About 15-20 years ago, I was interested in the topic of hacking and writing malicious code, then my interests changed to exactly the opposite - protection from this business, and then I realized that money and personal interests rule everything, and not altruism and the desire to help at all.
But that is. In any case, IT turned out to be part of even my present work, although it does not at all relate to the initial specialization.
About 10 years ago I wrote in a very narrow circle about the possibility of removing an anti-virus detection using self-extracting archives. Then it seemed to be on Virusinfo, then some people reposted it under their nickname on DrWeb - so to speak, without copyrights and with their authorship, then there was even a scandal - but that too was not true for a long time.
And recently, I remembered the old. Much has passed, many things have been updated and keeping up with progress, not changing the topic, turned out to be difficult.
But the essence remained the same: sensations, money and personal interests. And a game of ignorance - which sometimes reaches the point where Meltdown / Specter seeks vulnerabilities in TVs and on-board computers of cars)))
But enough of this uninteresting nonsense. So, I decided to recall the old, and since I remembered little, I decided to remove the detects from several viruses in the old fashioned way.
We will need:
- knowledge of school bat-scripts of Windows at the student level.
- Quick Batch File Compiler (hereinafter - QBC)
- 7za.exe from the package 7z1800-extra.7z (hereinafter - 7Z)
- upx.exe from the upx394w.zip package (hereinafter - UPX)
- eicar.com file, you can download, for example, here (hereinafter - Eicar)
- the most basic computer with Internet access running any Windows OS
Part 2. Quite a bit of theory
In order to move on, let's figure out what will be discussed. At the moment, as, however, as before, the theme of antiviruses is being actively promoted. Say, antiviruses help prevent the loss of important data, antiviruses save from vulnerabilities, antiviruses - that, antiviruses - this and so on.
Moreover, often the average user does not even understand that an antivirus is not just a scanner, it is both resident protection and heuristics, and often proactive protection, a firewall and a sandbox.
We can devote to each of these components not just an article - a book, but dwell on the most basic one: a scanner.
This component will not allow you to prevent connections to malicious sites, it will not catch malicious code on the fly, but it allows you to check the file and give an answer: should it be stored - or it is better to delete it immediately and forever.
Below we will test different anti-virus engines and see how well they cope with this task.
I would also like to mention the VirusTotal resource - it not only allows you to check the file with various anti-virus engines, but also represents a kind of sandbox for testing malicious (and generally any) code. Plus platforms - free, minus - all samples that are sent to VirusTotal are subsequently transferred to all anti-virus laboratories.
For this reason, below I will not give links to pages with scan results, but I will provide screenshots of these results obtained in the course of work. Obviously (and I want to believe it!) After this article, the results will improve.
Authors of malicious code extremely often use packers and protectors, which not only compress the malicious file, but also make it difficult to detect by signature, as well as its subsequent analysis. When using stolen licenses for protectors such as WinLicense and Themida, antivirus laboratories usually do not unpack themselves, but simply add tread signatures with a stolen key to the detector (famous detectors like Trojan: W32 / Black.A). This leads to the appearance of false positives - the authors of key generators, patchers, and some programs use similar stolen licenses, which are essentially not malicious, but are nevertheless protected from reversal.
Since everything described in this article will be provided below for review, I did not work with real malicious code (although I will provide its scan results below), but I used the Eicar file, which is popular when testing antiviruses: this is a kind of stub for which any antivirus should give a persistent detection.
So let's get started.
Part 3. Practice
So, as Eicar is now detected on VirusTotal

Frankly, what I saw was somewhat struck, because for some reason two anti-virus engines - Comodo and Malwarebytes decided not to follow common standards and ignore the detection. Nevertheless, the result is obvious - the file has a detection close to 100%.
As we agreed at the very beginning, we are a complete shkolota, and therefore we will not invent our own packaging methods, but simply pack the file into the archive using 7Z:
7za a eicar.7z eicar.comCheck the received file on VirusTotal

Yes, there are fewer detections, since not all anti-virus engines include the 7Z archive unpacker (well, or this setting is not included in VirusTotal by default) - but the detection is still high.
We complicate the task: we pack the file into the archive with a password. Let the password be fun:
7za a -mhe=on -pfun eicar-fun.7z eicar.comThe result of the check is obvious.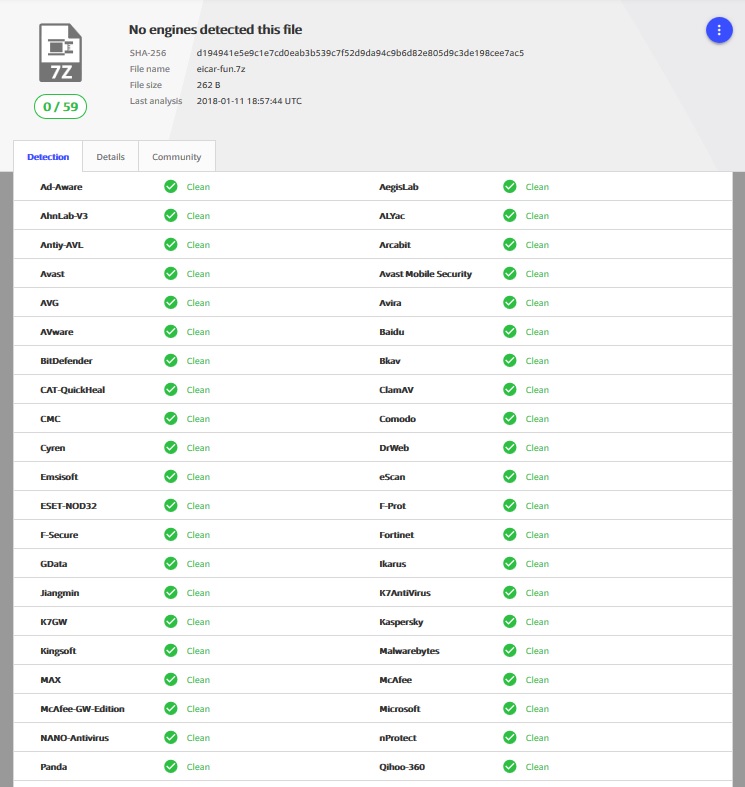

The file is clean, because even with the unpacking procedure, the antivirus does not know the password for the file.
Detect removed - but we did not receive the executable file.
In real packers, the solution can be quite complicated and we will not go into these details. We will use the services of QBC and write the simplest script:
7za e -pfun eicar-fun.7z
start eicar.comThe script simply unpacks the archive and runs the resulting file. QBC not only allows you to create the simplest executable file based on this script, but also include the necessary (7za.exe and eicar-fun.7z archive) in this file, accessed through the% myfiles% variable.
The resulting executable file can be without opening the terminal window (the so-called “Ghost”), and this is exactly what we need:
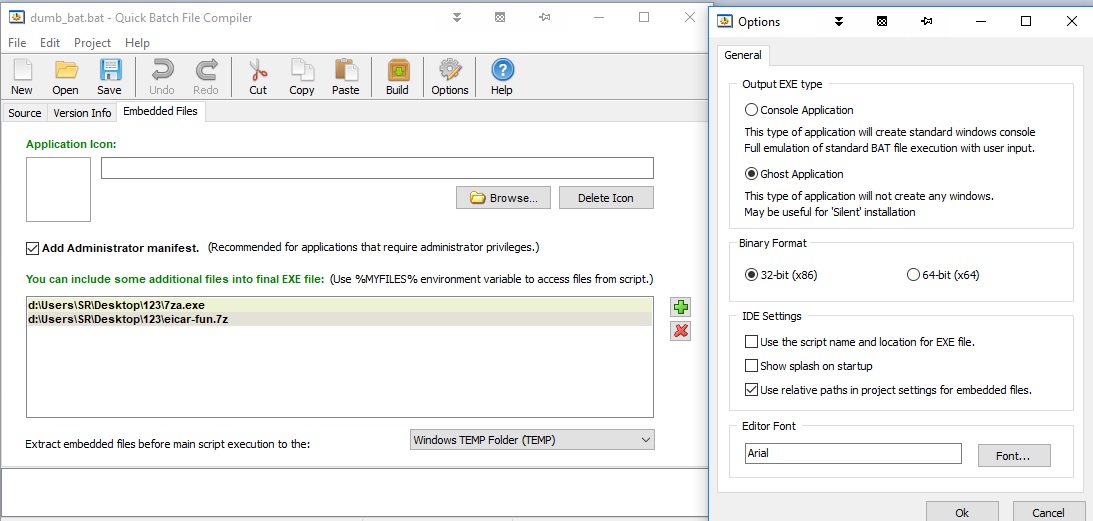
The final code looks like this:
cd %myfiles%
7za e -pfun eicar-fun.7z
start eicar.comAfter compilation, the resulting dumb_bat.exe file decompresses Eicar and launches it.
We look at the result of checking this file on VirusTotal

It's funny, the detective was reduced from 60 to unpacked files, and 41 for the file 17 - in this case none of the antivirus engines have not found the Eicar, Detective obviously have a heuristic nature, and in some cases resemble the false positive (DrWeb, Baidu and others.)
Let's go further - add protection against execution in the test environment to our script - the simplest check that the file is running in a real system. To do this, we will start unpacking only under the condition that there is a D drive in the system and there is at least one file on it:
cd %myfiles%
if exist d:/* (7za e -pfun eicar-fun.7z)
start eicar.comWatching Detects
Particular attention is paid to the bottom of the table, I highlighted it separately, because everything did not fit into one picture:


Particular attention is paid to the bottom of the table, I highlighted it separately, because everything did not fit into one picture:

So, the D disk check “broke off” the detectives of the Chinese, Russians and Ukrainians: Baidu, DrWeb, Zillya. Moreover, these engines, like several others, were stopped by timeout (!)
In fairness, it is worth noting that the re-launch still brought the scan to the end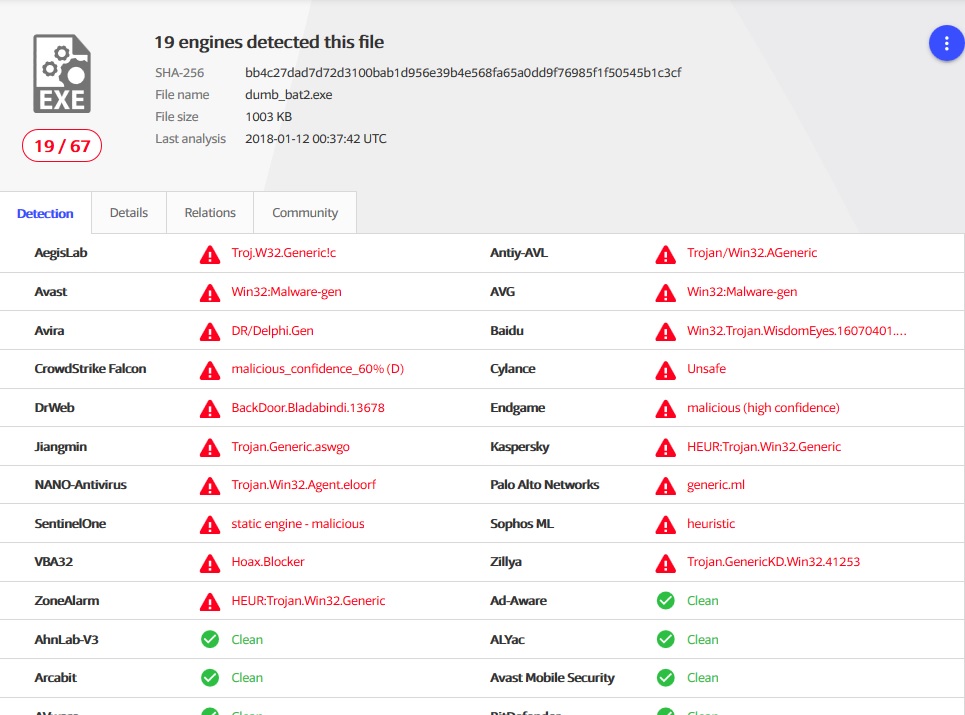

However, in this case, the experiment cannot be considered “clean”, since a considerable time has passed after the first test.
I found this situation curious - and I changed the line in the code to the following:
...
if not exist d:/* (7za e -pfun eicar-fun.7z)
...The test result is impressive.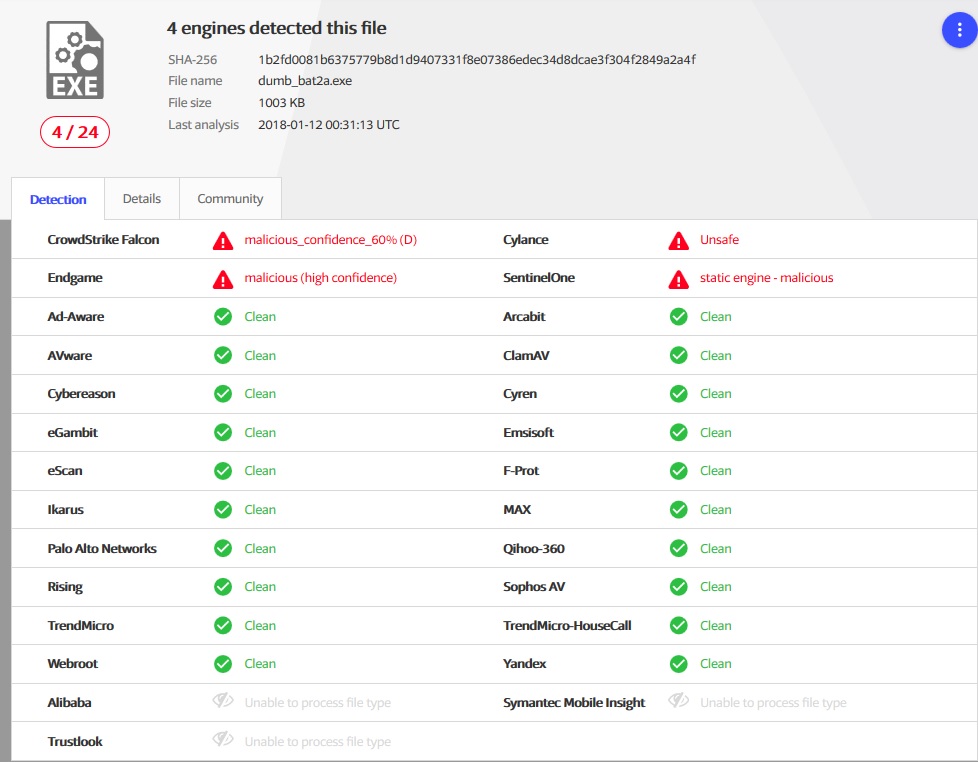

However, again, a second scan still took place.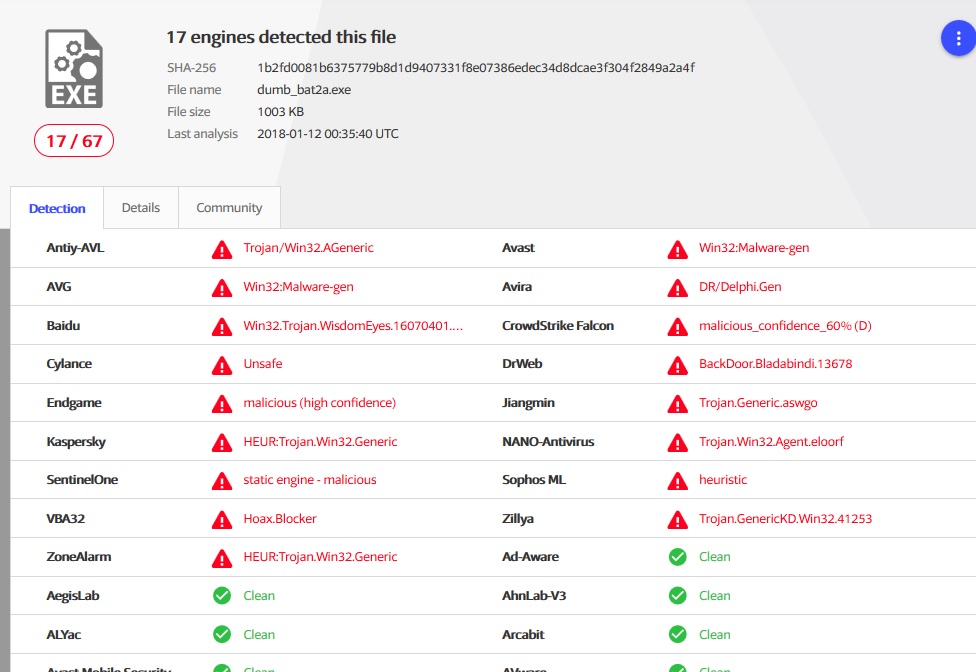

There is a difference in the work of the heuristics of a number of antiviruses (for some reason, AegisLab and Baidu did not find anything in the second case), and there is also a problem in scanning when checking for the presence of drive D. However, this is a coincidence, although during the whole study I no longer I have never watched the "dump" of so many engines at once.
Moving on - add to our file interactivity, which certainly will not be in any test environment. Change the script - make it a full-fledged console (not “Ghost”), and also add the pause command:
@cd %myfiles%
@pause
@if exist d:/* (7za e -pfun eicar-fun.7z) > nul
@start eicar.comHere is the result of such a file:
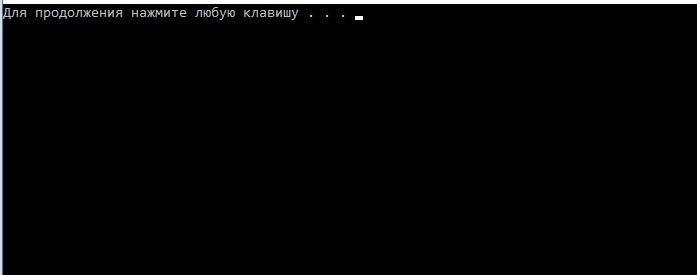
I don’t want to slander users, but it seems to me that almost everyone will press a key in this case :) In any case, we have a simple example that can be wrapped up in a much brighter wrapper of social engineering.
Detect such a file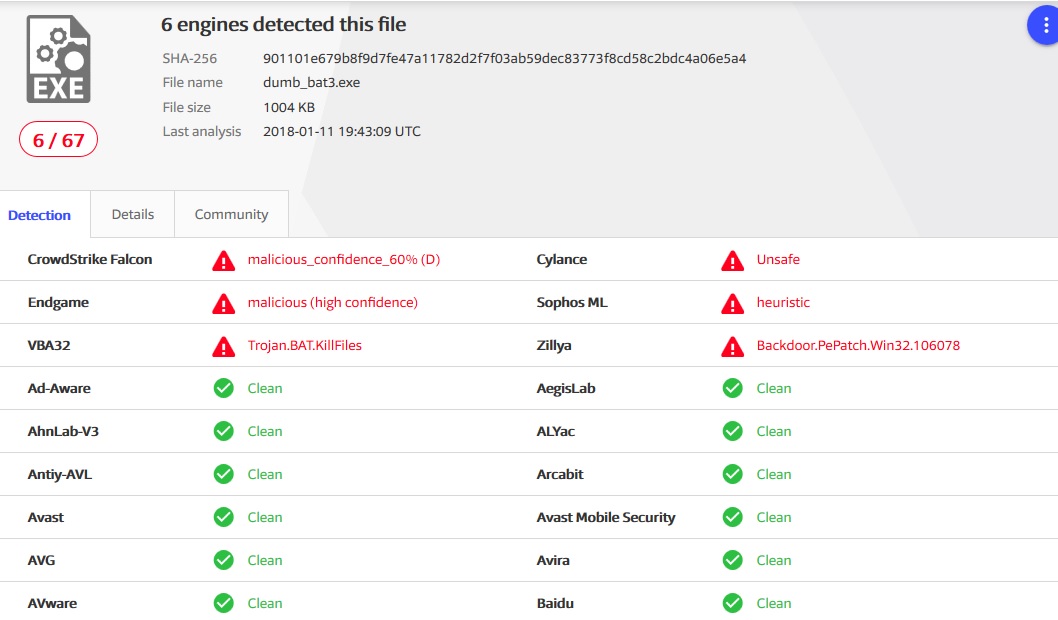

6 out of 67 detects. Six, Karl! All are heuristic. And most likely an unsuspecting user will find the file safe.
I got an interesting result after compressing the resulting file using the UPX command:
upx --best --ultra-brute --8086 --backup --compress-icons=3 dumb_bat3.exeIf we do this for our very first code - which was without any checks at all, then Antiy-AVL fell off according to the detections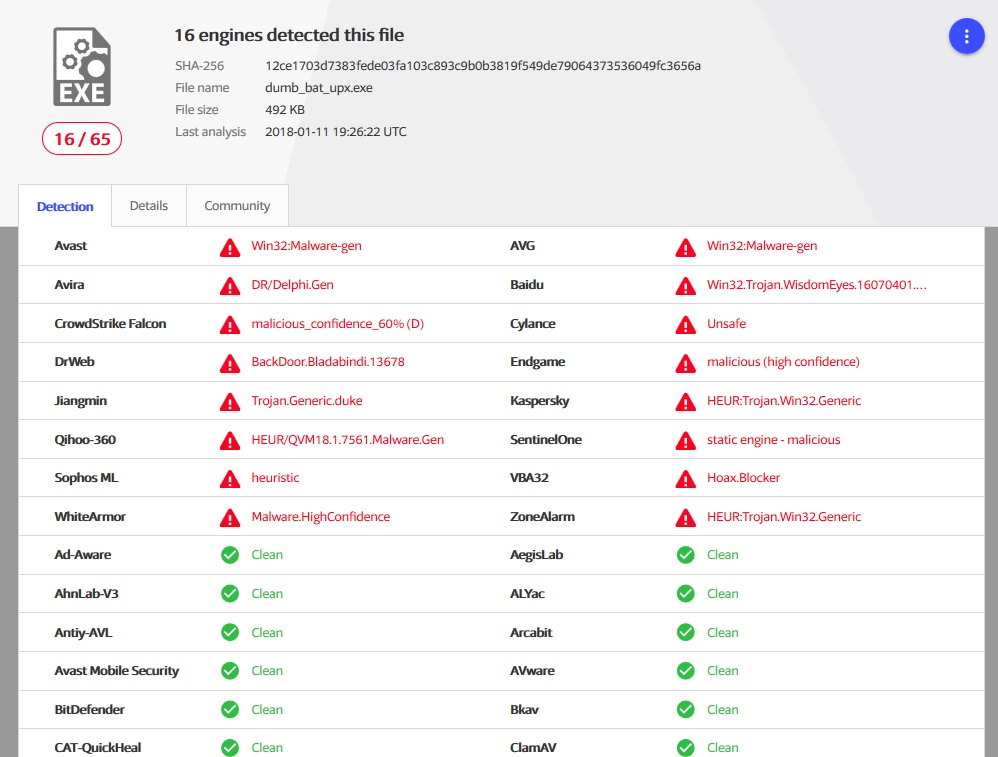

For the latest version, the file has decreased, the essence has not changed, but detections have been added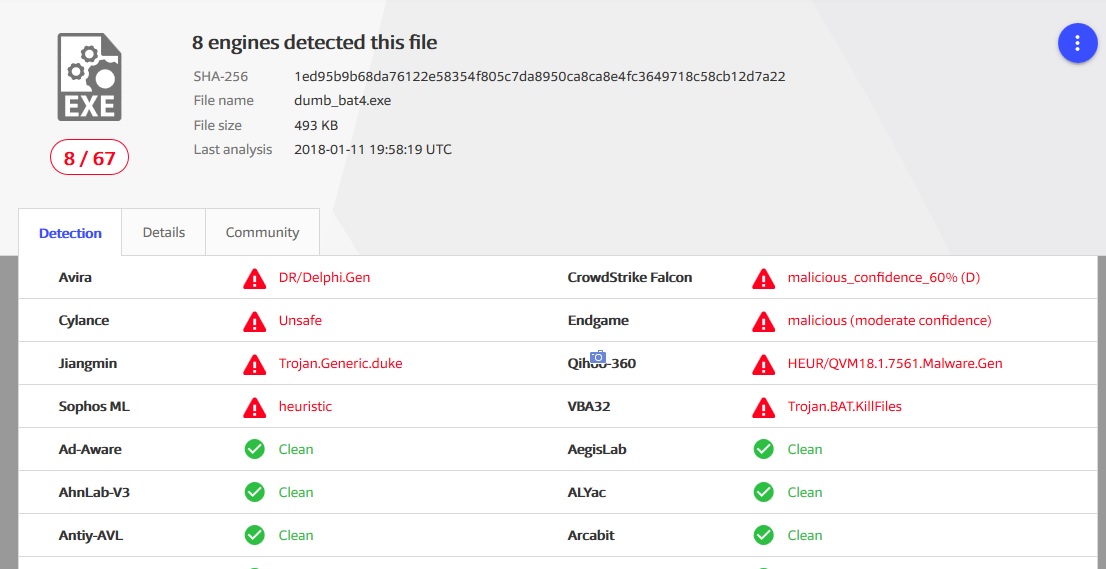

Detectives were added by the Chinese, but Ukrainian Zillya successfully failed the test.
Part 4. Conclusions
Is it possible without them? ;) Okay.
Of course, the above is primitive, simple, and life is not so. If only because in reality the execution of our file will first trigger proactivation, and then it will be blocked by the resident module, which will see the final Eicar file.
But that is not the point.
The fact is that modern anti-virus scanners have remained a junk, which they were a dozen or two years ago, absolutely grazing in front of the simplest types of code packaging. Solutions in the form of test environments - sandboxes, heuristic analyzers, etc. only added confusion, false positives, but in fact they do not protect against a real threat. With the old, open and chewed up to the guts of UPX as there was a mess - so he stayed. But I could well have packaged not the file causing the malicious activity, but the code itself, working not with the files on the disk in% temp%, but in memory, using not freely available utilities, but my own or closed developments - and thus bypassing the resident operation protection.
What we did above is a primitive way to trick an antivirus that almost anyone can understand and implement. And it worked. What to say about sophisticated specialists!

An archive with files, scripts and results can be downloaded here .
The archive did not include the following (it will not enter and will not be provided at any request for obvious reasons): files processed according to the above mechanism and containing:
- File infector Sality.aaScanning results of the infection itself
 Shame on the jungle
Shame on the jungle 'Packaging' scan results
'Packaging' scan results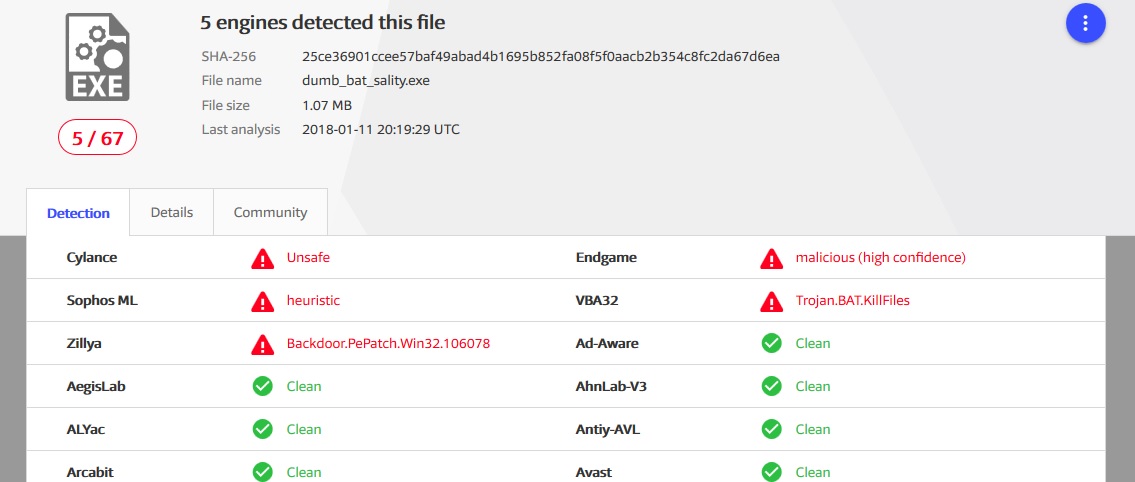
- Quite loud sensational just recently locker PetyaScanning results of the infection itself
 Twice a shame on the jungle
Twice a shame on the jungle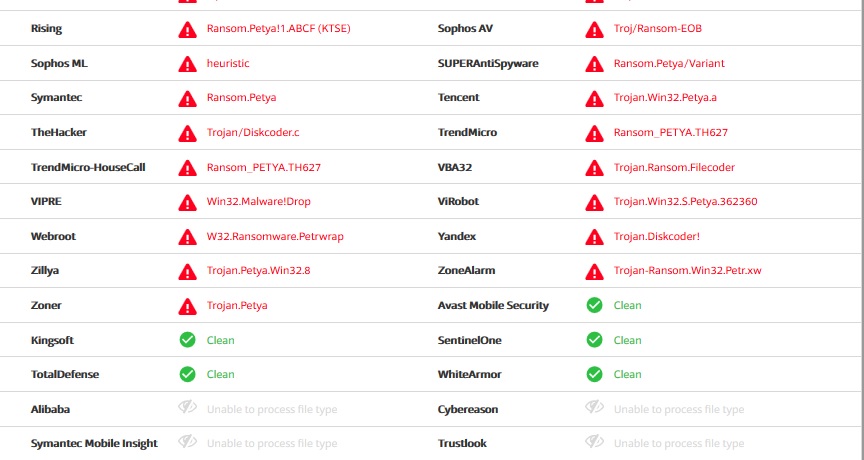 'Packaging' scan results
'Packaging' scan results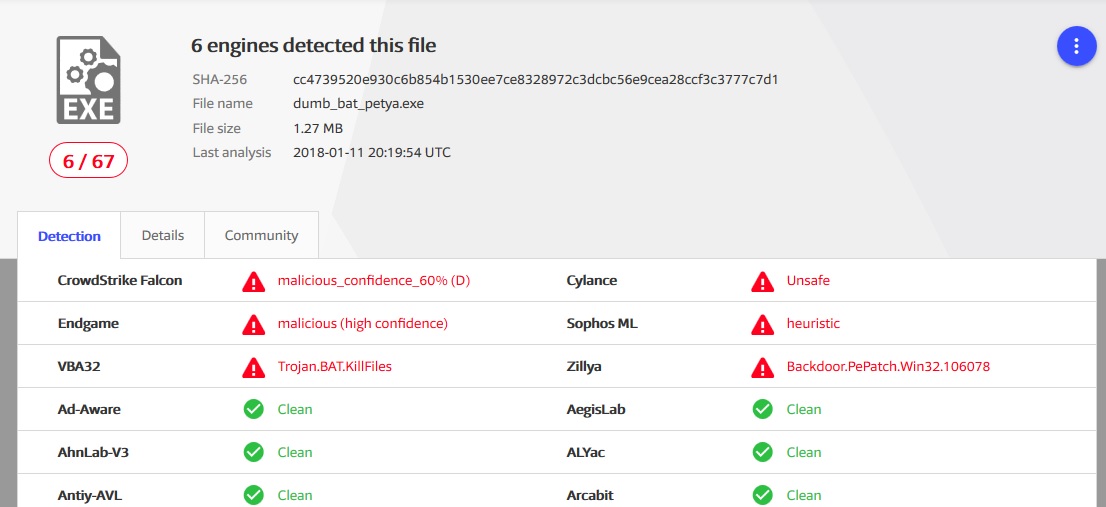
If you have read all this to the end - click here.

