How baghunters intercepted letters in the pneumatic mail on ZeroNights

Much has already been said about Bug Bounty and the need for such programs for companies seems obvious. During the existence of our own program, Mail.ru Mail has paid more than $ 250,000, the average payment is $ 379, we have already written a little more about it . And today, using the example of the recently held information security conference ZeroNights, we will talk about how you can attract hackers to participate in the search for bugs and vulnerabilities through specialized events.
This year, the ZeroNights conference was held at the A2 Green Concert Club in St. Petersburg. Despite the move from Moscow, the conference gathered more than 1,000 participants in 2 days. The conference sounded the reports of many cool professionals. If you need a hardcore - see "NUClear explotion", "From Graphic Mode To God Mode, Discovery Vulnerabilities of GPU Virtualization", "Researching Marvell Avastar Wi-Fi: From Zero Risk”. This year there were also many interesting reports about the Web, you can watch slides and WebVillage and more. Personally, the report from Ilya Nesterov and Sergey Shekyan was important to me. Distinguishing a bot from a real user is becoming more and more difficult. More about the reports here .
Our tasks
We set ourselves the following tasks:
- Brand promotion and Bug Bounty program in the community.
- Recruiting sensible professionals who successfully cope with the task.
Idea
The most difficult challenge in such projects: to develop interesting tasks that, firstly, will attract participants, and secondly, will allow us to test their real skills.
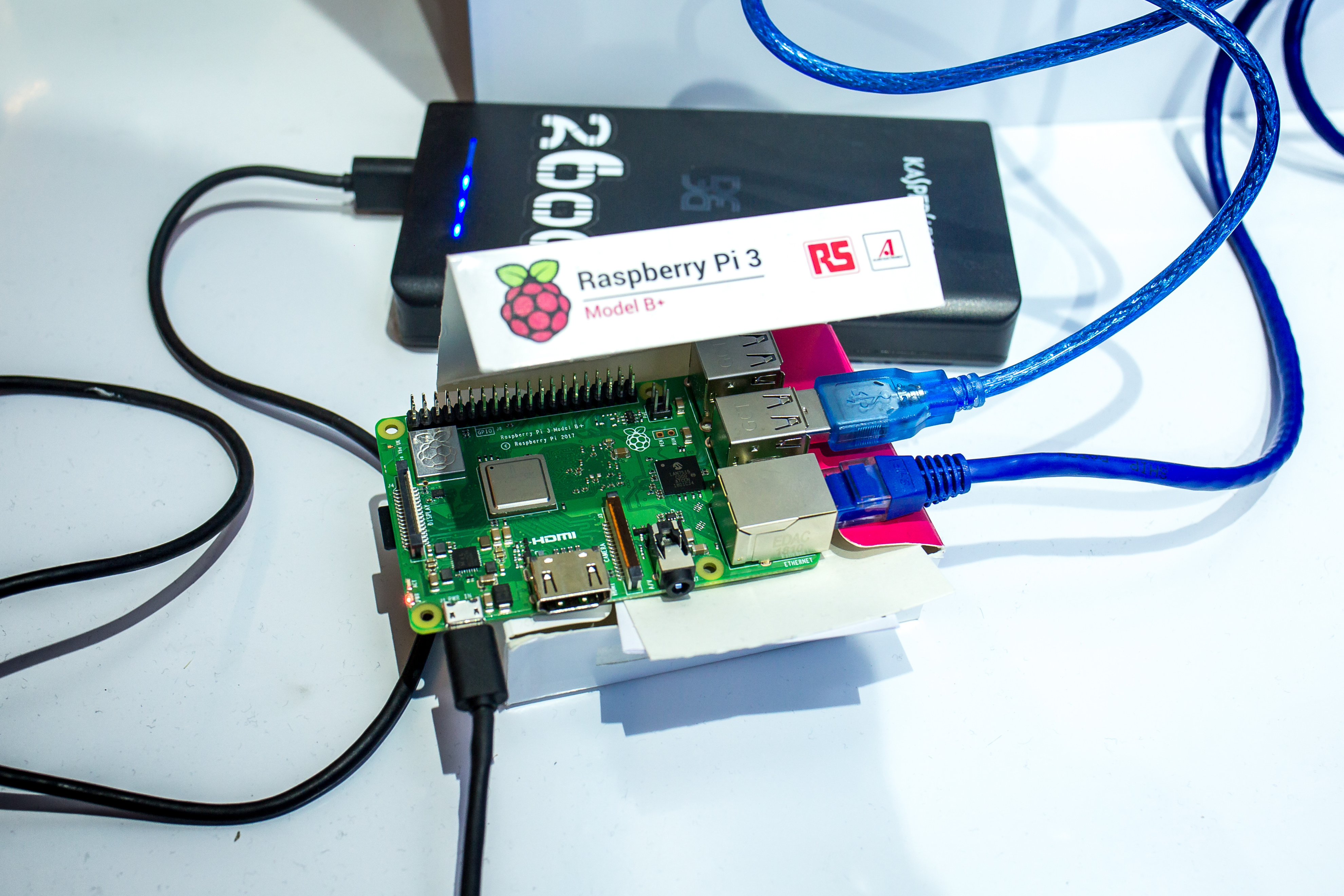
Our booth this year was an office building equipped with pneumatic post. The essence of the task: the head of the pneumatic mail sends letters to the accountant, and the task of the hacker is to change the path and intercept the letter with the help of special valves.
The stand looked like this:

Instead of the mail itself, we used tennis balls, which went down from top to bottom in the required drives, by default in the "accounting". It was necessary to activate the valves, which were controlled by the Arduino + RPi3, and redirect the "mail" to other drives.
Action scheme:
- We connect to the Wi-Fi network tasks.
- We find in the network Raspberry Pi, which is connected to the Arduino, which controls the valves.
- RPi is running a web server. Two tasks need to be accomplished - to exploit vulnerabilities and at the end they gave buttons to activate the dampers, which allowed them to redirect the “mail”
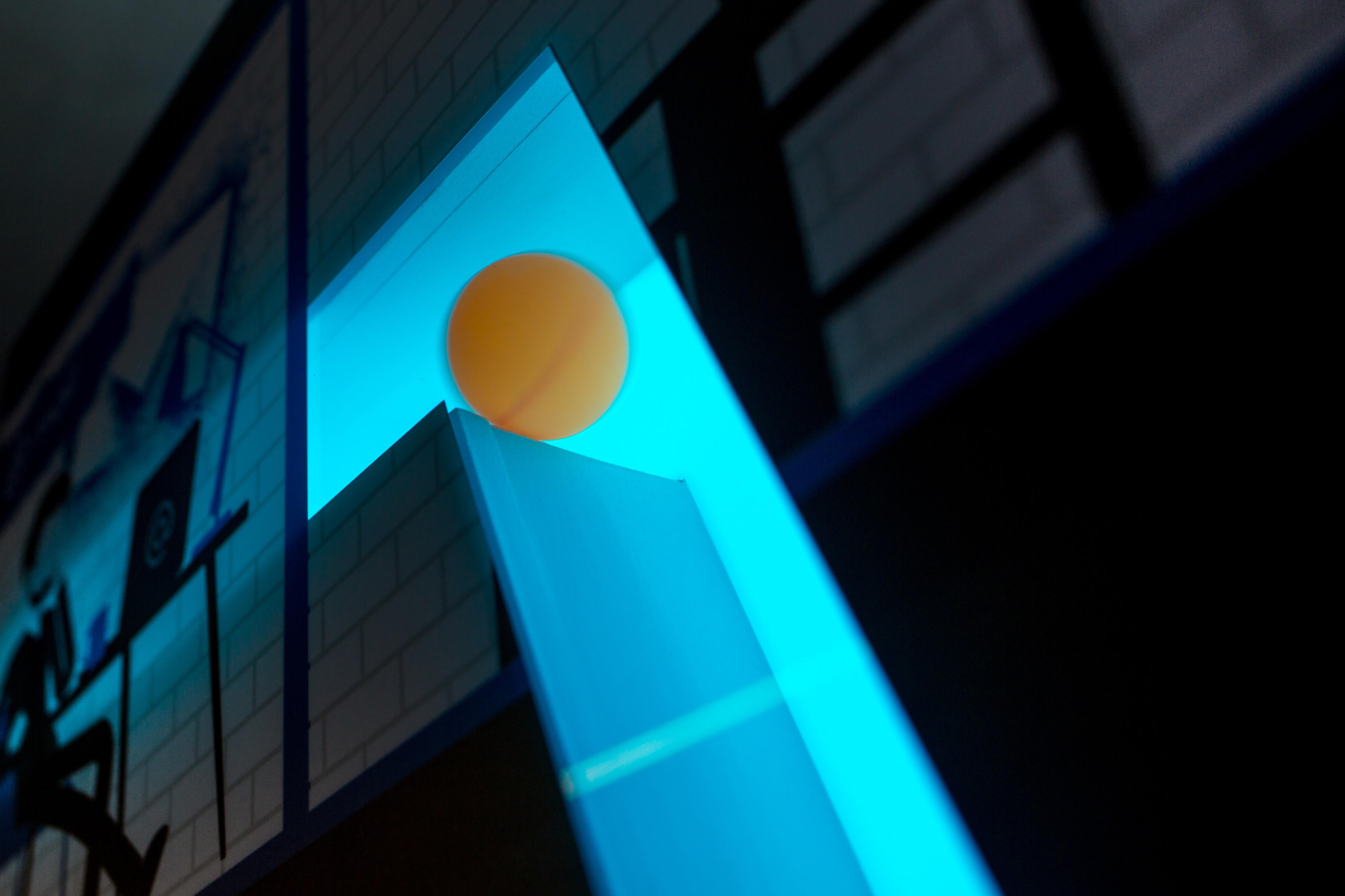
The ball symbolizes pneumatic writing:
We took the ideas for assignments from the reports of our researchers.
Tasks
In the first task, the participants had to find the RPi3 host and discover a typical configuration vulnerability for the Apache web server: the / server-status page, which displays all incoming HTTP requests. Among others, this page received a request with a secret value in the GET parameters, which allowed you to pass the first level. For this task, visitors received a $ 100 promotional code to participate in our Bug Bounty program.
Decision
Уязвимость конфигурации Apache ищется обычными инструментами типа dirbuster, строка server-status есть во всех актуальных словарях. Кроме того, мы оставили несколько подсказок, чтобы задание можно было решить без каких бы то ни было скриптов и программ, даже с обычного телефона.
To pass the second task, it was necessary to study the contents of the already known monitoring page. In the client application code, it was necessary to find a hidden method that was not called from the interface, but contained a vulnerability - a “blind” NoSQL injection in Mongodb.
Decision
Чтобы автоматизировать слепую инъекцию, необходимо решить две задачи:
Написать скрипт, который умеет получать 1 бит информации за один запрос. На выходе нужно иметь возможность вставлять в запрос интересующее логическое выражение и по ответу сервера понимать, истинно оно или ложно.
Придумать, как можно побитово получать интересующую информацию из БД (например, если вы хотите узнать значение поля secret='some_secret', можно использовать регулярные выражения. Сначала узнаём первый символ secret ~ '^a', secret ~ '^b'… secret ~ '^s'… После этого второй secret ~ '^sa', secret ~'^sb'… Аналогично получаем весь секретный токен).
Это не единственная и не самая эффективная реализация, варианты получше можно посмотреть в коде sqlmap.
Написать скрипт, который умеет получать 1 бит информации за один запрос. На выходе нужно иметь возможность вставлять в запрос интересующее логическое выражение и по ответу сервера понимать, истинно оно или ложно.
Придумать, как можно побитово получать интересующую информацию из БД (например, если вы хотите узнать значение поля secret='some_secret', можно использовать регулярные выражения. Сначала узнаём первый символ secret ~ '^a', secret ~ '^b'… secret ~ '^s'… После этого второй secret ~ '^sa', secret ~'^sb'… Аналогично получаем весь секретный токен).
Это не единственная и не самая эффективная реализация, варианты получше можно посмотреть в коде sqlmap.
The main difficulty was represented by an atypical technology stack: MeteorJS, which makes extensive use of Websockets, as well as MongoDB and Pubsub, instead of the usual HTTP requests and responses, did not allow the use of existing tools and required the participants to independently automate attacks. Many participants looked for vulnerabilities in the functionality of the MeteorJS platform itself, mistakenly mistaking it for the task code. Also for some participants there were difficulties in automating requests through Websockets.

As a prize for this contest, participants received a Mail.ru Bug Hunter sweatshirt.
results
In just two days of the conference, more than 200 people participated in our competition. 100 participants coped with the first task, 45 people completed the second task.
Of course, we successfully negotiated the task successfully on the spot. New cards for $ 100 have a deferred effect, but several of them have already been activated and we got good bugs on H1. They encourage hackers to search for new bugs, help us improve our systems and improve security. Small card - great results. A hundred bucks is a hundred bucks.

