EU GDPR: Regulatory Compliance for Cloud Computing

We are often afraid of changes in Russian legislation and their possible impact on business. Meanwhile, regulators in the EU demonstrate an enviable sense of purpose in this matter. Under the cut, another batch of innovations. Read the post, if suddenly, your projects relate to user data.
EU GDPR is the European General Data Protection Regulation(General Data Protection Regulation (Regulation [EU] 2016/679)). It will enter into force on May 25, 2018 and will replace national data protection laws. After that, it will become even more important for European companies to ensure data security, because the penalties for leaks and misuse of data will be tightened. EU GDPR provides for fines, penalties and public censure for unwittingly or irresponsibly disclosing personal and corporate data of customers and third-party companies. And to avoid this, we will have to strengthen data protection measures.
Traditional network-centric solutions, such as firewalls and intrusion detection systems, cannot protect against hacking by privileged users and from targeted cyber attacks. There are other methods, such as managing information and event security ( SIEM) and database auditing and protection (DAP). Due to stricter data retention requirements and increasingly frequent leaks, businesses will have to move from network-centric solutions to data-centric solutions. Strict access control, key management and encryption, along with reconnaissance, become necessary, because as soon as you transfer everything to the cloud, you only have a browser as an interface.
Protections require huge amounts of data processed by companies. This includes all personal data. Their leakage or other disclosure without permission under the new rules is unacceptable. Personal data cannot be transferred to other countries without proper supervision and permission - this is a problem for international corporations that have to correctly share data or pay fines up to € 10 million. And IT professionals will need to puzzle over how to strike a balance between data protection requirements and the interests of company employees who need quick access to information and applications.
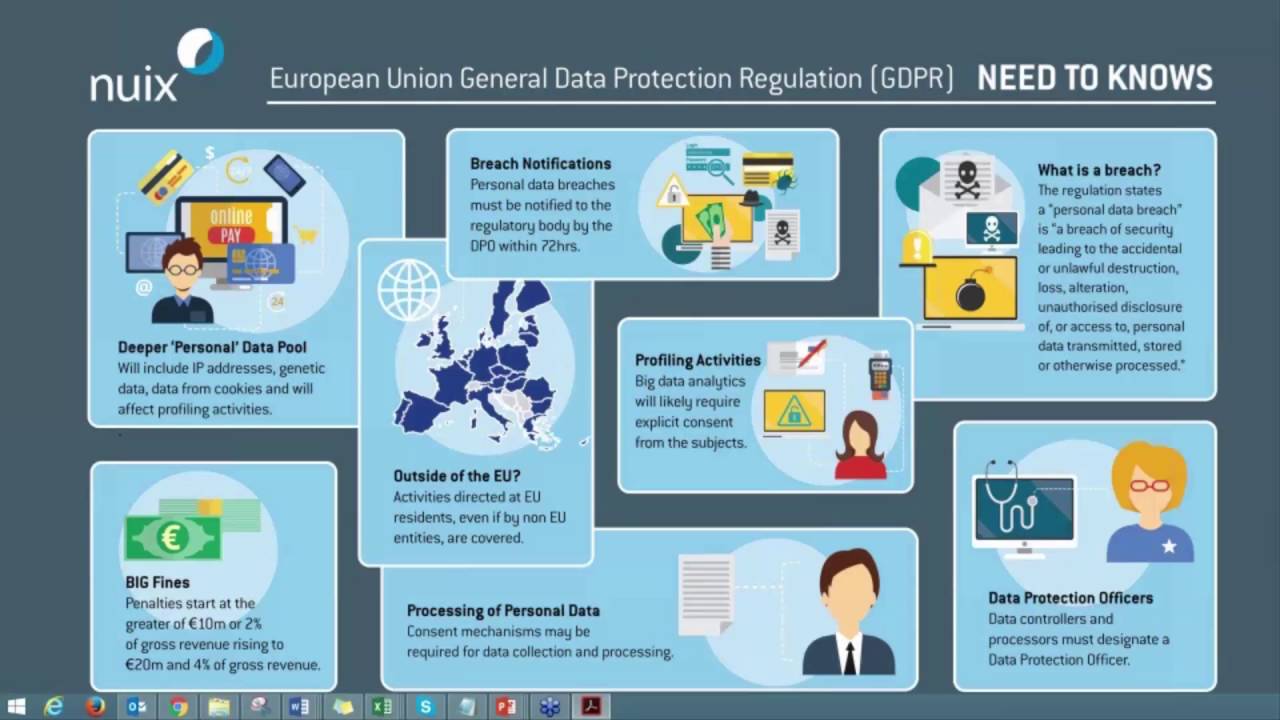
New requirements and cloud computing
In order for the data processing processes in the organization to meet EU GDPR requirements, it is necessary to deploy such security mechanisms throughout the network so that unauthorized users cannot access the network. It is important to hire reliable employees for database management and system administration. It is recommended to organize processes so that different privileges are assigned to users depending on their positions.
The data management system needs to be supplemented with effective technologies for enforcing system policies for secure access to information, as well as its storage, retrieval or manipulation.
Cloud computing allows you to centralize all work with data, improve the security of the company’s network, easily protect data and manage access from any one system. Data can be securely stored in private, hybrid or public clouds, with secure encrypted access.
Cloud computing is a broad term that describes various infrastructure and software solutions for ubiquitous access (usually via the Internet) to shared pools of configurable resources (computer networks, servers, storage, data, computers, applications and services). One of the most common cloud applications is application and desktop delivery, so employees get access to centralized data from anywhere in the world.
When applications are delivered, data and software are transferred to an isolated environment deployed on a client device and executed there. No need to install or store anything. The user sends keystrokes and mouse clicks to the server, and in response receives screen updates. Access to data is regulated only by authentication, in addition, you can enable two-factor authentication or fine filtering based on the user's location, device type or MAC address.
Moving data from user devices to the cloud significantly reduces the risk of leaks or losses, and helps organizations comply with EU GDPR requirements. In addition, the clouds are characterized by scalability, dynamism and mobility while maintaining a high level of security and business continuity.

Cloud benefits
Pushed by the revolution in mobile IT and the requirements of the EU GDPR, many organizations are moving towards the clouds, receiving in return improved security, wider and easier scalability, use on any mobile device and lower costs.
Security . Centralized data storage in the cloud eliminates the risk of physical theft, the most common form of data leakage.
Scalability . Companies can easily scale their cloud infrastructure in contrast to traditional data centers. Typically, personal data is stored in organizations for years, so ordinary data centers can be overloaded with a huge amount of information that accumulates for a long time.
Mobility. Clouds provide employees with secure access to data, applications and desktops from any device from anywhere. Organizations can adhere to the principles of BYOD (bring-your-own-device) and CYOD (choose-your-own-device), while preserving labor productivity and improving data protection.
Cost reduction . Clouds allow companies to save significantly. Improving hardware utilization increases business efficiency. Centralized deployment of applications and desktops reduces the burden on IT employees, which further increases the cost savings.
Create a secure cloud solution using Parallels Remote Application Server (RAS)
Although cloud solutions allow you to create efficient, scalable and reliable systems, the potential of such solutions is fully revealed in the virtualization of applications, desktops, files and folders that can be delivered to various devices. Thanks to centralized application management, data storage and maintenance, IT departments have more control, they can remotely strictly separate corporate and personal data.
Parallels Remote Application Server(RAS) is a solution for delivering virtual applications and desktops. It allows you to safely work from anywhere, on almost any device, including Android and iOS. RAS can be used to create any cloud infrastructure, because it works seamlessly with Microsoft Remote Desktop Services (RDS), Citrix XenServer, VMware EXSi, Microsoft Hyper-V, Nutanix Acropolis (AHV) and KVM. Parallels RAS can be deployed in a private, hybrid, or public cloud such as Amazon Web Services (AWS) and Windows Azure.
To reduce the risk of data leakage, you can force the use of access rules and scatter data on protected storages. This strengthens the division into user groups, departments, and regions.
Parallels RAS can centrally deploy critical OS updates and security patches to all users at the same time, reducing downtime and increasing security. RAS also supports continuous availability, resource-oriented balancing, and universal printing.
Because of these capabilities, as well as strong data protection, many companies use Parallels RAS to provide access to applications, desktops, and data.
Improving Business Security
Data is not stored locally . Data is stored in the cloud data center of our company, they are provided with secure access through encrypted connections. Nothing is saved on devices. Remote users receive only a projection of data, applications and desktops located on the server.
Advanced filtering . Parallels RAS integrates with Active Directory and offers advanced filtering options to prevent unauthorized access. Filtering rules allow administrators to restrict access to important data (for example, details of bank card owners) by user, group, MAC address, IP address and other criteria.
Login. There are two login modes: private and public. In the first case, user data (name and password) can be stored on the device. When you log in publicly, nothing is saved on the device. This improves the security of shared workstations and tablets.
Data sharing . Parallels RAS can create an unlimited number of farms and sites. A farm is a group of servers used to deliver applications to users, and a platform is a group of farms. However, each site has an independent Activity Directory. The sites cannot share data, which guarantees perfect sharing of information.
Desktop Replacement. Parallels RAS offers companies the ability to replace Windows desktops, turning them into secure pseudo-thin clients. Based on security requirements, administrators can decide which applications will run locally. You can block any local operations on the machine and allow only those operations that are performed remotely on the server.
Restriction on copying and pasting . To avoid leaks from applications and desktops, you can disable the use of the buffer - copying and pasting data.
Increased security. All data is stored on servers with centralized security management and backups. Only mouse clicks, keystrokes, and screen redraws are sent to and from client devices. This prevents leaks, viruses, trojans and protects against other vulnerabilities and threats on clients.
Smart Card Authentication . Parallels RAS makes it easy to organize user authentication in a virtual application using smart cards. Redirecting virtual desktops and applications can be challenging, and using smart cards can improve security.
Two-factor authentication. Enhances security by using different types of tokens for the second level of authentication. It can be provided using a Dual Shield server, SafeNet or RADIUS.
SSL certificates / encryption . The Secure Client Gateway acts as a proxy between the Parallels client software running on client devices and Parallels RAS. Data exchange is encrypted in the gateway using SSL.
Conclusion
Parallels RAS is one of the core virtualization solutions. It improves the security and convenience of end-user access to data, desktops and applications on any device and anywhere in the world. For four consecutive years, Parallels RAS has won the prestigious Govies Government Security Award. This solution is used by thousands of organizations across the globe. Parallels RAS provides employees and users with real-time access to virtualized applications on any device, including zero and thin clients, mobile workstations and a variety of end devices.
