Artificial intelligence will save from ransomware
Acronis True Image is a reliable solution for protecting user data. In Acronis True Image 2017 and Acronis True Image 2017 New Generation, we set a very high bar in everything regarding reliability, simplicity and usability. These products included the backup and recovery of Facebook social network profile data, the proactive protection system from Acronis Active Protection ransomware, the Blockron-based Acronis Notary data notification function, and the digital signature of electronic documents using Acronis ASign. In addition, we added NAS support and the ability to wirelessly backup mobile devices to the macOS version of the program.

Every year the number of threats continues to grow, they become more complicated and dangerous. According to Kaspersky Lab, in the second quarter of 2017, 15,663 new modifications of ransomware were detected (for comparison, over the same period in 2016, there were almost 70% fewer new malware - 9,226) and 268,284 attacks were recorded.

Figure 1. The number of new ransomware modifications according to Kaspersky Lab
The two largest attacks took place this year. First, in May, WannaCry ransomware attacked telephone companies, hospitals, factories, and hundreds of other organizations in more than 100 countries, and then, in June, NotPetya ransomware made thousands of users around the world regret the lack of backup copies of their data.

Figure 2. The number of ransomware attacks according to Kaspersky Lab
Today, the world's largest media speak about these cyber attacks, so users are beginning to better understand the scale of the threat. According to our global studyalmost 50% of respondents know about ransomware on the topic of data protection, against 35% in the past. The study was conducted in August this year, and users from the USA, Great Britain, Australia, Japan, Germany, France and Spain took part in it.
However, the low user awareness and the constant complication of the ransomware code leaves no doubt that the number of attacks will increase, which means that data protection solutions should also be improved.
Therefore, one of the main innovations of Acronis True Image 2018 is Acronis Active Protection 2.0 technology, which is designed to “repel attacks." Acronis Active Protection technology introduced at the beginning of the year is based on behavioral heuristics that help identify suspicious activity and prevent ransomware attacks. This approach to protection worked perfectly and works for most existing malware, however, their modern versions are so advanced that they can "trick" the system. Imagine a malware that is embedded in MS Word, and, encrypting all the documents as a whole, leaves the headers intact. In this case, the behavioral heuristic does not classify this process as dangerous, and the malware manages to “partially encrypt” almost all files before you can do anything.
In order to counter such attacks, the Acronis Active Protection 2.0 introduced the ML (machine learning) Engine, which analyzes the operation of both infected and non-infected programs, generates characteristic patterns based on their comparison, and, in the event of their subsequent detection, stops suspicious processes .
In St. Petersburg and Moscow, we have already deployed more than 20 physical farms, and we also have a virtual Microsoft Azure cloud, which automatically downloads and analyzes processes in various operating systems and programs in pure form and when infected with ransomware. The algorithm “learns” how these processes differ and what indicators can signal infection.
Our internal tests showed that even if the attack was not recorded based on behavioral heuristics, ML Engine Acronis Active Protection 2.0 noticed and blocked it. In addition to this, machine learning helped us find and formulate new rules for the heuristic component. To the existing rules, the "robot" found another 100. The most attentive and picky ones might already ask themselves: how much space on the hard drive and in memory does such an algorithm require? The answer will surprise you a little: the system takes up less than 14 mb! If we talk about loading memory, then there is nothing to worry about: ML Engine runs in the background and turns on only once every 30 seconds, without consuming a lot of memory.
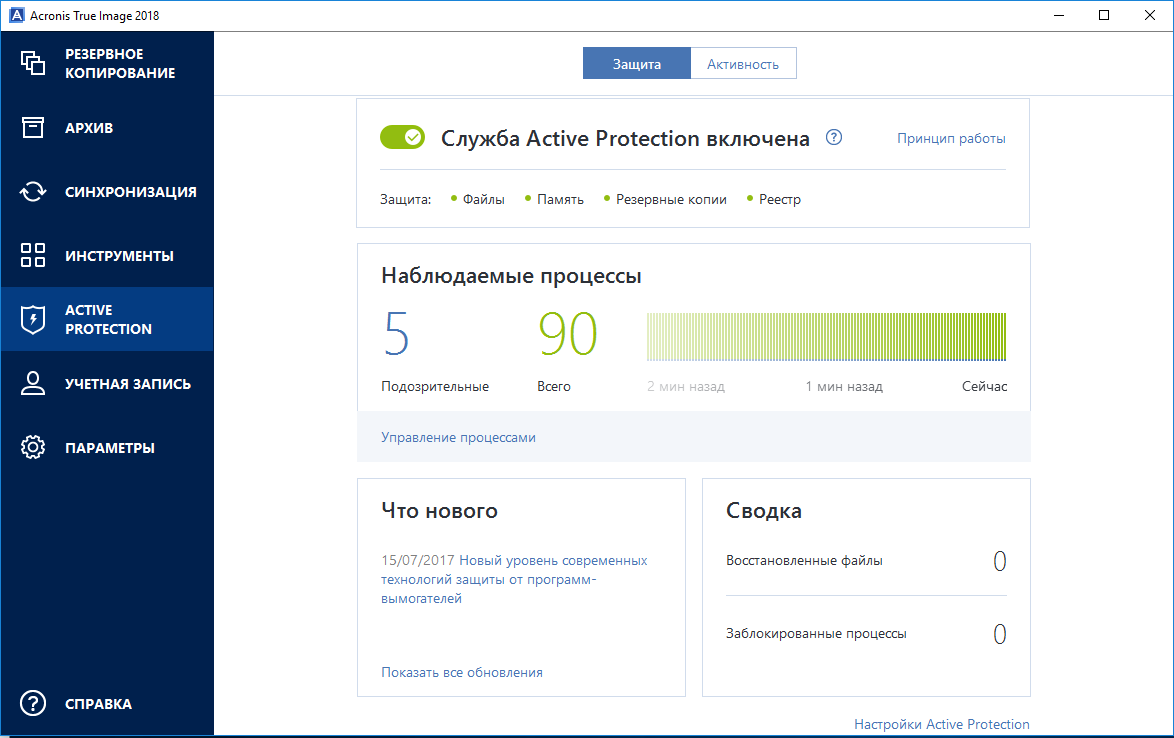
Acronis Active Protection 2.0 also got a dashboard that shows a graph of all the processes in the system, including suspicious ones. Processes without a digital signature (or with an invalid signature) are considered suspicious or if there is a suspicion that code was injected into the process using DLL Injection. If such processes begin to modify user files, then these files are stored in the cache. If too many files are modified, then our heuristics work, the system pauses the process and informs the user that it is most likely a ransomware program and suggests adding these processes to the black list or allowing them to continue working. Also on this dashboard displays information about upcoming updates, statistics on the number of Active Protection processes blocked, the number of files recovered after an attack,
Among the other functions that we have updated, we can note the Bootable Media Builder. Now, when creating a bootable flash drive or CD / DVD, we use the Windows Recovery Partition. If earlier for this it was necessary to download a special kit from Microsoft with a size of 4 to 6 GB depending on the assembly, then in Acronis True Image 2018 we decided to do everything a little more elegant without loading too much. On modern Windows systems, there are Recovery sections from which we can take this ADK itself (a set of tools for deploying and evaluating Windows) and based on it we make bootable media without loading special whales.

We also got the opportunity to convert backups to virtual disks in VHD (x) format. This virtual disk can be used in different ways: for example, as a storage medium (log in, browse folders and files, some of them can be restored by simple copying without resorting to True Image). You can boot as a Hyper-V virtual machine (starting with Windows 7, it is available in PRO versions), or you can boot natively as with WRP.
Another innovation will be useful for our users - the system of cloning active Windows disks. Cloning a disk will help, for example, when moving from HDD to SSD or if there is a suspicion that the disk may soon become unusable. Now, to copy the system disk, you do not need to reboot - you can connect the new device to USB on the fly and clone it.
One of the main innovations in the UI is the data analysis interface in backup - this is a way to visualize the backup process, show the user what happens in the process and what data we save.
Acronis True Image 2018 shows statistics for each backup: right below the blocks where it is shown what and where to backup, a diagram is displayed showing proportionally how many photos are in the archive, how many video and audio files, documents, how much space system files occupy (these are files located in Windows or macOS system folders). Plus, the activity tab shows the entire history of backup operations like statuses or errors. All this made the process of working with backups more visual and pleasing to the eye.


We have added some more useful features to the product. Firstly, it is an opportunity to postpone backup until the laptop is connected to the network. As you know, backing up is a rather energy-intensive process (many disk accesses and copying operations, especially if the backup is rarely performed and a lot of data is copied and transferred at a time), and if it starts when the battery is already a little bit, it can play a cruel joke. To prevent this from happening, it is possible to prevent the application from starting any backup until the device is connected to the mains. The second feature was the automatic backup of mobile devices over Wi-Fi networks on the NAS. If the phone is on the same network as the NAS and they have backup configured, the phone immediately starts to backup on its own without user intervention - you don’t even need to connect to the computer.
In Acronis True Image 2018, we have expanded support for social media backups. To Facebook, which became supported with Acronis True Image 2017, we added Instagram support. In September, users around the world will have the opportunity to backup all their photos, videos, information / statistics from the profile. Unfortunately, due to the technical limitations of Instagram itself, the user cannot restore all the data, as implemented on Facebook, that is, back up more than 150 comments under one post, but you can restore both individual and all profile photos with one click.
What can be said in the end: the development of Acronis True Image 2018 has become a real challenge for us. We seriously expanded its functionality and added demanded features, both in the software part and in the UI part. We have reason to believe that True Image 2018 will set a new standard for smart backup systems for home users, data protection for the whole family and small businesses.

Every year the number of threats continues to grow, they become more complicated and dangerous. According to Kaspersky Lab, in the second quarter of 2017, 15,663 new modifications of ransomware were detected (for comparison, over the same period in 2016, there were almost 70% fewer new malware - 9,226) and 268,284 attacks were recorded.

Figure 1. The number of new ransomware modifications according to Kaspersky Lab
The two largest attacks took place this year. First, in May, WannaCry ransomware attacked telephone companies, hospitals, factories, and hundreds of other organizations in more than 100 countries, and then, in June, NotPetya ransomware made thousands of users around the world regret the lack of backup copies of their data.

Figure 2. The number of ransomware attacks according to Kaspersky Lab
Today, the world's largest media speak about these cyber attacks, so users are beginning to better understand the scale of the threat. According to our global studyalmost 50% of respondents know about ransomware on the topic of data protection, against 35% in the past. The study was conducted in August this year, and users from the USA, Great Britain, Australia, Japan, Germany, France and Spain took part in it.
However, the low user awareness and the constant complication of the ransomware code leaves no doubt that the number of attacks will increase, which means that data protection solutions should also be improved.
Therefore, one of the main innovations of Acronis True Image 2018 is Acronis Active Protection 2.0 technology, which is designed to “repel attacks." Acronis Active Protection technology introduced at the beginning of the year is based on behavioral heuristics that help identify suspicious activity and prevent ransomware attacks. This approach to protection worked perfectly and works for most existing malware, however, their modern versions are so advanced that they can "trick" the system. Imagine a malware that is embedded in MS Word, and, encrypting all the documents as a whole, leaves the headers intact. In this case, the behavioral heuristic does not classify this process as dangerous, and the malware manages to “partially encrypt” almost all files before you can do anything.
In order to counter such attacks, the Acronis Active Protection 2.0 introduced the ML (machine learning) Engine, which analyzes the operation of both infected and non-infected programs, generates characteristic patterns based on their comparison, and, in the event of their subsequent detection, stops suspicious processes .
In St. Petersburg and Moscow, we have already deployed more than 20 physical farms, and we also have a virtual Microsoft Azure cloud, which automatically downloads and analyzes processes in various operating systems and programs in pure form and when infected with ransomware. The algorithm “learns” how these processes differ and what indicators can signal infection.
Our internal tests showed that even if the attack was not recorded based on behavioral heuristics, ML Engine Acronis Active Protection 2.0 noticed and blocked it. In addition to this, machine learning helped us find and formulate new rules for the heuristic component. To the existing rules, the "robot" found another 100. The most attentive and picky ones might already ask themselves: how much space on the hard drive and in memory does such an algorithm require? The answer will surprise you a little: the system takes up less than 14 mb! If we talk about loading memory, then there is nothing to worry about: ML Engine runs in the background and turns on only once every 30 seconds, without consuming a lot of memory.
Acronis Active Protection 2.0 also got a dashboard that shows a graph of all the processes in the system, including suspicious ones. Processes without a digital signature (or with an invalid signature) are considered suspicious or if there is a suspicion that code was injected into the process using DLL Injection. If such processes begin to modify user files, then these files are stored in the cache. If too many files are modified, then our heuristics work, the system pauses the process and informs the user that it is most likely a ransomware program and suggests adding these processes to the black list or allowing them to continue working. Also on this dashboard displays information about upcoming updates, statistics on the number of Active Protection processes blocked, the number of files recovered after an attack,

Among the other functions that we have updated, we can note the Bootable Media Builder. Now, when creating a bootable flash drive or CD / DVD, we use the Windows Recovery Partition. If earlier for this it was necessary to download a special kit from Microsoft with a size of 4 to 6 GB depending on the assembly, then in Acronis True Image 2018 we decided to do everything a little more elegant without loading too much. On modern Windows systems, there are Recovery sections from which we can take this ADK itself (a set of tools for deploying and evaluating Windows) and based on it we make bootable media without loading special whales.

We also got the opportunity to convert backups to virtual disks in VHD (x) format. This virtual disk can be used in different ways: for example, as a storage medium (log in, browse folders and files, some of them can be restored by simple copying without resorting to True Image). You can boot as a Hyper-V virtual machine (starting with Windows 7, it is available in PRO versions), or you can boot natively as with WRP.
Another innovation will be useful for our users - the system of cloning active Windows disks. Cloning a disk will help, for example, when moving from HDD to SSD or if there is a suspicion that the disk may soon become unusable. Now, to copy the system disk, you do not need to reboot - you can connect the new device to USB on the fly and clone it.
One of the main innovations in the UI is the data analysis interface in backup - this is a way to visualize the backup process, show the user what happens in the process and what data we save.
Acronis True Image 2018 shows statistics for each backup: right below the blocks where it is shown what and where to backup, a diagram is displayed showing proportionally how many photos are in the archive, how many video and audio files, documents, how much space system files occupy (these are files located in Windows or macOS system folders). Plus, the activity tab shows the entire history of backup operations like statuses or errors. All this made the process of working with backups more visual and pleasing to the eye.


We have added some more useful features to the product. Firstly, it is an opportunity to postpone backup until the laptop is connected to the network. As you know, backing up is a rather energy-intensive process (many disk accesses and copying operations, especially if the backup is rarely performed and a lot of data is copied and transferred at a time), and if it starts when the battery is already a little bit, it can play a cruel joke. To prevent this from happening, it is possible to prevent the application from starting any backup until the device is connected to the mains. The second feature was the automatic backup of mobile devices over Wi-Fi networks on the NAS. If the phone is on the same network as the NAS and they have backup configured, the phone immediately starts to backup on its own without user intervention - you don’t even need to connect to the computer.
In Acronis True Image 2018, we have expanded support for social media backups. To Facebook, which became supported with Acronis True Image 2017, we added Instagram support. In September, users around the world will have the opportunity to backup all their photos, videos, information / statistics from the profile. Unfortunately, due to the technical limitations of Instagram itself, the user cannot restore all the data, as implemented on Facebook, that is, back up more than 150 comments under one post, but you can restore both individual and all profile photos with one click.
What can be said in the end: the development of Acronis True Image 2018 has become a real challenge for us. We seriously expanded its functionality and added demanded features, both in the software part and in the UI part. We have reason to believe that True Image 2018 will set a new standard for smart backup systems for home users, data protection for the whole family and small businesses.
