Computer Networks for dummies
Hello!
After reading such material as “PHP 7 D. Koterova”, or “byte Of Python”, one very interesting question may arise, and no, it will not be related to the language the book was about, it will be taken as a rule from the first chapters books that are usually devoted to the "Internet device", as a rule, such books do not immerse the user very deeply, and leave it at the level of application data, that is, no further than the HTTP protocol, and TCP / IP. But as we all know, there are very "gluttonous" minds, which alone
The basic terms and concepts of computer networks, roughly speaking, computer networks, are ordinary "networks" consisting of finite machines. End machines are any computers on the network that want to exchange data.
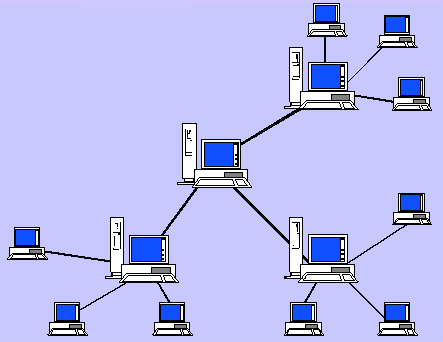
Such networks, as a rule, transmit data on physical transmitters, namely (the most popular / easy-to-understand types will be considered):
The question immediately arises with an edge, are all computers simply connected via cable to each other, the answer is yes and no. As you know, if you bought a new laptop, you would have to connect it to all the computers in the world, but you don’t do it, instead of this you either simply plug in your laptop, cable, or connect via WI-FI, here’s ours " yes and no ”it appears, as you see manually, you don’t do everything, but when you connect to your Internet at home, you buy it from the provider, so you’re connecting“ by cable ”to the provider, which already connects you to the entire Internet . But, this still does not cancel the question, is the provider also connected to all the PCs in the world? No, everything is different, to begin with, there are many providers, there are providers who buy Internet from a regional provider (this is a provider,
But, as you yourself understand, this is not all, we cannot be directly connected through providers via cable to providers, and those with providers to a higher level, and so on. No, this is not so, in fact, between end systems, providers, and other nodes, there are special switches and kilometers of cables, about switches - namely, routers, routers, these are special blocks, computers that have several inputs / outputs ( it may be that and that, such inputs / outputs are called interfaces), and have on board a table that describes 1 address in the network of the next router or the final system, for sending data to the final system for which the request was made, 2 kilometers (these are not exact definitions; they are considered to be special units there), 3netmask (this is not all, but routers will not be revealed in detail in this article).
Now the network looks like this.
The computers are highlighted, they want to communicate with each other, on the way they have several routers, and other computers. The question arises, how does the router find out exactly where the final system is, is there a router at all, and which path is longer, and which router to send data to. When asked about where the final system is, and which router will send the data to next, the network addressing is answered, namely IP addresses, approx: 192.168.0.1, the router accepts all the data it received from the computer, or from another router, looks at everything 4 address blocks (blocks are separated by a dot), let's say the initial path is 176.123.82.129, the data comes to router 176.123.82.130, two routers, 176.123.82.120, 176.123.82.125, and one computer 176.123.82.129 are connected to it, this router will look at its address table, and send the data to where it “reaches faster” to the final system, that is, it will send the data there itself due to the IP in the data and its table. The length of the path is calculated using a table with "mileage" (not accurate, because there is a unit of calculation). Everything is with routers, in fact they still have a lot of inaccuracies and functions, but I will not disclose them in detail here, because it will take a lot of time.
What do we get in the end? We have networks, from end systems, providers, they are interconnected by cables, but through adapters “routers”, which act as the main data routers.
Not much clarification, “data” is a data packet containing bits of information, the processing order of such a “packet” on the router, something like this - a packet arrives, usually a packet, this is only part of all the data transmitted by the final system, and so, the router does the processing , takes out the headers of the network layer of the network (more on that later) back packs the packet, sends it according to the principle described above. I’ll clarify, routers, there are those that wait until all data arrives with the destination system, and which immediately send data, without waiting for the others, but when the others arrive, he sends them to the same place where he sent the first (all these calculations are done by the router itself , due to the headers in each individual package), and to engage in further processing,
As you understand, for all of the above to work correctly, there must be some standard, this de facto standard is the TCP / IP protocol stack + OSI layer.
First, a few terms.
What is a protocol? A protocol is a certain rule of communication between two systems, the most etching and popular example, this is the interaction of two people, let's say you fit into a person, what do you usually tell him? “Hello”, the person will process this and answer “Hello”, after that, after the communication agreement has passed, you ask “how much time”, the person will process this and answer for example “14:00”, after this conversation will end with the words “ thank you and goodbye. This type of communication, and there is a protocol, namely from the example above, we had almost a browser and hosting that work through HTTP TCP.
What is a port? How do computers communicate through networks? Computers communicate through special applications, and so, these applications work through special "sockets" interfaces, in order to correctly process an HTTP request to a web server, let's say that the web server calls the HTTP process located on port 80, this port will work hosting, in order for the web server to process TCP, you need to access the process with port 443. That is, the port is the identifier of the process on the destination system so that the socket can access it.
What is a socket?One of the most common questions for beginners, the socket, is just an interface between the protocol of the application layer of the network and the computer process, roughly speaking, there are two houses facing each other, Ivan lives in the left house, Sergey in the right house, Ivan wanted to send a letter to Sergey, then Ivan leaves his house, through the door (the process on the computer sends a packet, through the socket, in this case, the door), cross the road, the sidewalk (computer network, routers), knock on the door, shake hands with Sergey, and go through the door to his house (makes a request knocking ", agrees about the" shakes hands ", and the package comes through socket 'door').
What is a process? Everything is simple here, it is a “program” that works in the background, all the time, let's say this is an HTTP handler.
What is the agreement mentioned earlier? This is not a mandatory procedure, the agreement of two processes on communication on such a port, such as IP, for example, a browser and a web server, start communication only after an agreement such as "three-way handshake", this is when you enter the address of the website, browser in the address bar of the browser first sends a request to the server with the question “we will work”, the server can answer “yes” or “no”, if so, the browser sends another request, and the connection is started, if not, the browser sends us some kind of error about access denied . I note that not all computer networks and protocols necessarily have some kind of “agreement”.
Let's go back to the five-level network model, and so, five network levels, these are special network operation levels that make it easier to calculate at what level the error was detected, this allows the application to work more easily with data from the network, and allows developers to add their own protocol Do not study higher mathematics.
I will give an example used in the book Computer Networks. Visually ”, with some modification. Imagine an airport, an airport, in fact, is a network model, only in other realities, how does an airport work? A person (will act as a package), enters the buildings, and goes to the ticket office, to buy a ticket, he buys a ticket, and goes to check in baggage, reaching baggage check-in, check in baggage, then he goes on boarding the plane, and then the plane takes off acceleration on the runway, and only then flies (the packet “flies” over the network), after which the plane lands, and everything described earlier occurs, only in the reverse order, namely, the plane lands on the runway, the person leaves the plane, a person picks up luggage, and at will can file a sting I have a ticket. Now imagine, if instead of each separate service, there was only one, which would deal with boarding a plane, and selling tickets, and so on. Here, queues simply come to mind first, there would be huge queues. All the same thing happens with the network model.
For example, we have a chat, one application on our PC, and another on our friend’s PC, we send messages, and the following happens, namely, the packet is collected by the client (our) end machine process, and sent through the socket to the model level called “Transport” one, in turn, composes a packet through the TCP protocol (data length, data ...), and sends the packet even lower to the network layer, which through the IP protocol adds data to the packet about the receiver of the packet (all data other than those originally transmitted are called heading vkami, then we will call them that)) (this data is generated by the process itself), then the process sends the packet to the data link layer, this layer is responsible for finding and fixing errors on the network, as well as routing in the local network, for example WI -FI, the channel layer, in turn, sends to the physical layer, physical layer, encrypts all the data, and sends it through the interface (port on the PC, or via WI-Fi) to the location where the network layer provided, after which the data is processed on the destination machine of the recipient , namely, the physical layer at the recipient decrypts the data and transfers it to the channel one, it also decrypts it (removes its headers, taking all the necessary data), and sends the data to the network layer, it processes whether the address is taken correctly, is everything works, picks up with howls, and gives the data to the transport layer, which, in turn, finally decrypts everything, and gives the data to our “chat”.
I’ll clarify if our process suddenly wants to take only data from the network layer, then it will not be able to skip the first two levels, that is, it will need to decrypt the physical layer first, send the data to the channel layer, and only after that get to the network layer, jump over the levels not possible. It is important! It will be needed for further homework (the answer will be described at the end).
Here's what the network layers look like
I’ll clarify, for beginners, the question may arise: what do the arrows between the network levels mean? In fact, these arrows do not exist, in fact, the right pillar of the levels works with the packet simply on the protocol on which it was sent in the left column, it doesn’t communicate with the level that sent this packet, it only works with the packet , on the protocol on which the level of the left column worked.
Now think about the pros, for example, the main plus is that if, for example, an error occurred at the data link layer, it will not be difficult for us to find out, just by skipping the special return request over the network. Another plus, if we want to add our protocol, we don’t have to change all levels of the network, we just make a protocol that will work correctly with the current network level. Next, each level will be discussed in more detail.
But for starters, the question is routers, do they work with network layers? Which ones? To what reach? Which read? (Answer at the end).
Application level, this is not a mandatory level in using the network, it is mainly responsible for formatting the data that comes to the transport layer, on the final receiver system, for example, a web server and web browser, they directly work with HTML markup, when developing the web, we decided it’s not very good to transfer directly to the layout through the transport layer, and the HTTP application layer protocol was created, this protocol is specially created for transmitting HTML documents. But as I mentioned earlier, the application level is not necessary at all, almost all chat programs, even before the popularity of online chats, exchanged data through the transport layer, without using the application.
Transport level, this network level is responsible for transporting data over the network, that is, it receives the data itself, its length, and some other headers, and sends it all to the network level, this level should reference again when the system crashes, and one of the most The popular protocol of this level is TCP, followed by UPD.
The network level , this level is responsible for the packet addressing, it is saved at this level, IP address, net mask, there are some more headers, but we will not consider them. He is responsible for routing the packet over the network.
Channel level, this level is responsible for routing the packet on the local network, for example, to determine which computer to send the packet to on the WI-FI network, and this level is also responsible for detecting and correcting errors during packet transmission.
The physical level , this level directly works with PC interfaces, and is engaged in data encryption, in different types of frequencies, we will not consider it in detail.
There are many types of networks, ranging from application networks to low-level ones. I will consider here the two most popular types of networks, these are “P2P”, and “client server”. But for starters, the terms.
What is a customer? This client is, as a rule, the host machine (or the process of the host machine), which requests data from the server.
What is a server? A server, this is usually a destination machine (or a process of a destination machine), which, upon request, returns the requested data, or any other response, in general, a server is called that processes the requests that come to it, and responds to them.
P2P (decryption - "peer-to-peer"), this is the type of network when, on a computer network, all the end machines can be both servers and clients, for example, a group of skype, when you call someone, you become a client (your skype), which requests a video exchange from the server (from Skype of the one you are calling to), now you have disconnected from the call, and the one you just spoke to sharply called you, now you are not a client, but a server (your Skype does not now make requests, but answers them), and Skype is the one called, not the server but the client (does not respond to requests, but sends them). This is how P2P works when all the machines are potentially both clients and servers. Again, an example of such a network is Skype.

Client server, this is the type of network when we strictly have strictly clients, and a server / server. That is, you can always only send requests, and the server can answer them, so the chat can work, your client (process) sends requests to check for new messages in the database, if any, the server will return them, if not, return another the answer is, when you send messages, it flies to the server with a request like “save the new message to the database”. That is, we have a group of clients, and the server, if two clients want to communicate, everything will go through the server, and the clients will only make requests to the server, asking them to "return all new messages", and the server will only respond. An example of such a network, this is the most applied network at the moment, is the web. All your actions in the browser, such as entering an address in the address bar, make a request to the server, and the server only responds. Your browser cannot become a server, and the server cannot become a browser. (Browser client process, server server process).

Security in computer networks, this is now one of the most popular topics, information security, and a short article is not enough to explain even the most basic aspects. Here I will only talk about a couple of the most popular vulnerabilities, and attacks on computer networks.
Packet interception , as mentioned earlier, end machines exchange data through packets passing through the network. As you understand in the realities of our world, there are a lot of virtual structures that are associated with finances, for example, it can be banks, and just paying for a book in an online store is not important. All your data, in any case, will be transferred to another destination machine (server), and processed, and so, the essence of this vulnerability is that the data that is transmitted to the server, namely the packets, can be intercepted.
Accordingly, passwords or credit card numbers may be stolen. It can be that packages of a web browser, that packages of any P2P network. This vulnerability can be resolved by making a binding agreement between clients and servers that was discussed earlier.
DDoS attack, this is an attack that is currently one of the most popular in computer networks. It works like this, with more end systems, through advertising, spam, and other advertising methods, malicious software (process) is installed that is not visible, and it usually works without any user actions, in the background, at a certain hour “H”, all computers infected with this process, begin to send a huge number of requests to a specific server, in order to disable this server, or router, on the way to the server. In the request, as a rule, there is not much weight flying (for the vastness of the attack), while the most complex information for processing by the server.
Attacks of this type disable the server, thereby losing the ability of the server to respond to more and more new requests, thus the server crashes and the operation fails, and there are very frequent cases when the router goes down on the way to server, because they have a clogged buffer, and the ability to send packets further is lost. Such attacks are usually very quickly fixed, but when such attacks occur on some kind of Internet exchange, or banks, users, that the structures themselves, suffer losses.
You can protect yourself from such an attack by analyzing the number of requests per second from the same IP. The minimum dangerous attack size at the moment is 100 thousand requests per second. There is also a parent of a DDoS attack, namely DoS, but at the moment this attack is not so scary, because the power of even the most outgoing servers allows you to handle such a not significant load.
In conclusion, I want to say some details about this article.
Thank you all very much for reading!
UPD: the article is intended for those who did not know anything about networks, but want to start at least not with complex books, but with a general overview.
After reading such material as “PHP 7 D. Koterova”, or “byte Of Python”, one very interesting question may arise, and no, it will not be related to the language the book was about, it will be taken as a rule from the first chapters books that are usually devoted to the "Internet device", as a rule, such books do not immerse the user very deeply, and leave it at the level of application data, that is, no further than the HTTP protocol, and TCP / IP. But as we all know, there are very "gluttonous" minds, which alone
Each of the protocols ideally “knows nothing” about which protocol “stands above it”committed is not enough. There are a lot of options to take your "gluttony", and today I will talk about all the main points of computer networks, briefly.
First, what we will return to
The basic terms and concepts of computer networks, roughly speaking, computer networks, are ordinary "networks" consisting of finite machines. End machines are any computers on the network that want to exchange data.

Such networks, as a rule, transmit data on physical transmitters, namely (the most popular / easy-to-understand types will be considered):
- Fiber optic: the highest data transfer rate due to data transmission using light signals.
- Twisted pair: lower speed (depending on type), data transmission is carried out using electric signals via eight copper cables.
The question immediately arises with an edge, are all computers simply connected via cable to each other, the answer is yes and no. As you know, if you bought a new laptop, you would have to connect it to all the computers in the world, but you don’t do it, instead of this you either simply plug in your laptop, cable, or connect via WI-FI, here’s ours " yes and no ”it appears, as you see manually, you don’t do everything, but when you connect to your Internet at home, you buy it from the provider, so you’re connecting“ by cable ”to the provider, which already connects you to the entire Internet . But, this still does not cancel the question, is the provider also connected to all the PCs in the world? No, everything is different, to begin with, there are many providers, there are providers who buy Internet from a regional provider (this is a provider,

But, as you yourself understand, this is not all, we cannot be directly connected through providers via cable to providers, and those with providers to a higher level, and so on. No, this is not so, in fact, between end systems, providers, and other nodes, there are special switches and kilometers of cables, about switches - namely, routers, routers, these are special blocks, computers that have several inputs / outputs ( it may be that and that, such inputs / outputs are called interfaces), and have on board a table that describes 1 address in the network of the next router or the final system, for sending data to the final system for which the request was made, 2 kilometers (these are not exact definitions; they are considered to be special units there), 3netmask (this is not all, but routers will not be revealed in detail in this article).
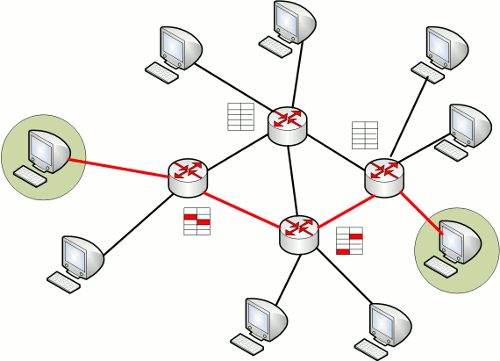
Now the network looks like this.

The computers are highlighted, they want to communicate with each other, on the way they have several routers, and other computers. The question arises, how does the router find out exactly where the final system is, is there a router at all, and which path is longer, and which router to send data to. When asked about where the final system is, and which router will send the data to next, the network addressing is answered, namely IP addresses, approx: 192.168.0.1, the router accepts all the data it received from the computer, or from another router, looks at everything 4 address blocks (blocks are separated by a dot), let's say the initial path is 176.123.82.129, the data comes to router 176.123.82.130, two routers, 176.123.82.120, 176.123.82.125, and one computer 176.123.82.129 are connected to it, this router will look at its address table, and send the data to where it “reaches faster” to the final system, that is, it will send the data there itself due to the IP in the data and its table. The length of the path is calculated using a table with "mileage" (not accurate, because there is a unit of calculation). Everything is with routers, in fact they still have a lot of inaccuracies and functions, but I will not disclose them in detail here, because it will take a lot of time.
What do we get in the end? We have networks, from end systems, providers, they are interconnected by cables, but through adapters “routers”, which act as the main data routers.
Not much clarification, “data” is a data packet containing bits of information, the processing order of such a “packet” on the router, something like this - a packet arrives, usually a packet, this is only part of all the data transmitted by the final system, and so, the router does the processing , takes out the headers of the network layer of the network (more on that later) back packs the packet, sends it according to the principle described above. I’ll clarify, routers, there are those that wait until all data arrives with the destination system, and which immediately send data, without waiting for the others, but when the others arrive, he sends them to the same place where he sent the first (all these calculations are done by the router itself , due to the headers in each individual package), and to engage in further processing,
Five layer TCP / IP network model
As you understand, for all of the above to work correctly, there must be some standard, this de facto standard is the TCP / IP protocol stack + OSI layer.
First, a few terms.
What is a protocol? A protocol is a certain rule of communication between two systems, the most etching and popular example, this is the interaction of two people, let's say you fit into a person, what do you usually tell him? “Hello”, the person will process this and answer “Hello”, after that, after the communication agreement has passed, you ask “how much time”, the person will process this and answer for example “14:00”, after this conversation will end with the words “ thank you and goodbye. This type of communication, and there is a protocol, namely from the example above, we had almost a browser and hosting that work through HTTP TCP.
What is a port? How do computers communicate through networks? Computers communicate through special applications, and so, these applications work through special "sockets" interfaces, in order to correctly process an HTTP request to a web server, let's say that the web server calls the HTTP process located on port 80, this port will work hosting, in order for the web server to process TCP, you need to access the process with port 443. That is, the port is the identifier of the process on the destination system so that the socket can access it.
What is a socket?One of the most common questions for beginners, the socket, is just an interface between the protocol of the application layer of the network and the computer process, roughly speaking, there are two houses facing each other, Ivan lives in the left house, Sergey in the right house, Ivan wanted to send a letter to Sergey, then Ivan leaves his house, through the door (the process on the computer sends a packet, through the socket, in this case, the door), cross the road, the sidewalk (computer network, routers), knock on the door, shake hands with Sergey, and go through the door to his house (makes a request knocking ", agrees about the" shakes hands ", and the package comes through socket 'door').
What is a process? Everything is simple here, it is a “program” that works in the background, all the time, let's say this is an HTTP handler.
What is the agreement mentioned earlier? This is not a mandatory procedure, the agreement of two processes on communication on such a port, such as IP, for example, a browser and a web server, start communication only after an agreement such as "three-way handshake", this is when you enter the address of the website, browser in the address bar of the browser first sends a request to the server with the question “we will work”, the server can answer “yes” or “no”, if so, the browser sends another request, and the connection is started, if not, the browser sends us some kind of error about access denied . I note that not all computer networks and protocols necessarily have some kind of “agreement”.
Let's go back to the five-level network model, and so, five network levels, these are special network operation levels that make it easier to calculate at what level the error was detected, this allows the application to work more easily with data from the network, and allows developers to add their own protocol Do not study higher mathematics.
I will give an example used in the book Computer Networks. Visually ”, with some modification. Imagine an airport, an airport, in fact, is a network model, only in other realities, how does an airport work? A person (will act as a package), enters the buildings, and goes to the ticket office, to buy a ticket, he buys a ticket, and goes to check in baggage, reaching baggage check-in, check in baggage, then he goes on boarding the plane, and then the plane takes off acceleration on the runway, and only then flies (the packet “flies” over the network), after which the plane lands, and everything described earlier occurs, only in the reverse order, namely, the plane lands on the runway, the person leaves the plane, a person picks up luggage, and at will can file a sting I have a ticket. Now imagine, if instead of each separate service, there was only one, which would deal with boarding a plane, and selling tickets, and so on. Here, queues simply come to mind first, there would be huge queues. All the same thing happens with the network model.
For example, we have a chat, one application on our PC, and another on our friend’s PC, we send messages, and the following happens, namely, the packet is collected by the client (our) end machine process, and sent through the socket to the model level called “Transport” one, in turn, composes a packet through the TCP protocol (data length, data ...), and sends the packet even lower to the network layer, which through the IP protocol adds data to the packet about the receiver of the packet (all data other than those originally transmitted are called heading vkami, then we will call them that)) (this data is generated by the process itself), then the process sends the packet to the data link layer, this layer is responsible for finding and fixing errors on the network, as well as routing in the local network, for example WI -FI, the channel layer, in turn, sends to the physical layer, physical layer, encrypts all the data, and sends it through the interface (port on the PC, or via WI-Fi) to the location where the network layer provided, after which the data is processed on the destination machine of the recipient , namely, the physical layer at the recipient decrypts the data and transfers it to the channel one, it also decrypts it (removes its headers, taking all the necessary data), and sends the data to the network layer, it processes whether the address is taken correctly, is everything works, picks up with howls, and gives the data to the transport layer, which, in turn, finally decrypts everything, and gives the data to our “chat”.
I’ll clarify if our process suddenly wants to take only data from the network layer, then it will not be able to skip the first two levels, that is, it will need to decrypt the physical layer first, send the data to the channel layer, and only after that get to the network layer, jump over the levels not possible. It is important! It will be needed for further homework (the answer will be described at the end).
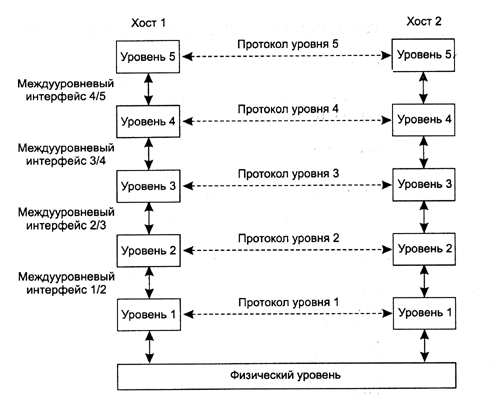
Here's what the network layers look like

I’ll clarify, for beginners, the question may arise: what do the arrows between the network levels mean? In fact, these arrows do not exist, in fact, the right pillar of the levels works with the packet simply on the protocol on which it was sent in the left column, it doesn’t communicate with the level that sent this packet, it only works with the packet , on the protocol on which the level of the left column worked.
Now think about the pros, for example, the main plus is that if, for example, an error occurred at the data link layer, it will not be difficult for us to find out, just by skipping the special return request over the network. Another plus, if we want to add our protocol, we don’t have to change all levels of the network, we just make a protocol that will work correctly with the current network level. Next, each level will be discussed in more detail.
But for starters, the question is routers, do they work with network layers? Which ones? To what reach? Which read? (Answer at the end).
Application level, this is not a mandatory level in using the network, it is mainly responsible for formatting the data that comes to the transport layer, on the final receiver system, for example, a web server and web browser, they directly work with HTML markup, when developing the web, we decided it’s not very good to transfer directly to the layout through the transport layer, and the HTTP application layer protocol was created, this protocol is specially created for transmitting HTML documents. But as I mentioned earlier, the application level is not necessary at all, almost all chat programs, even before the popularity of online chats, exchanged data through the transport layer, without using the application.
Transport level, this network level is responsible for transporting data over the network, that is, it receives the data itself, its length, and some other headers, and sends it all to the network level, this level should reference again when the system crashes, and one of the most The popular protocol of this level is TCP, followed by UPD.
The network level , this level is responsible for the packet addressing, it is saved at this level, IP address, net mask, there are some more headers, but we will not consider them. He is responsible for routing the packet over the network.
Channel level, this level is responsible for routing the packet on the local network, for example, to determine which computer to send the packet to on the WI-FI network, and this level is also responsible for detecting and correcting errors during packet transmission.
The physical level , this level directly works with PC interfaces, and is engaged in data encryption, in different types of frequencies, we will not consider it in detail.
What types of networks are there?
There are many types of networks, ranging from application networks to low-level ones. I will consider here the two most popular types of networks, these are “P2P”, and “client server”. But for starters, the terms.
What is a customer? This client is, as a rule, the host machine (or the process of the host machine), which requests data from the server.
What is a server? A server, this is usually a destination machine (or a process of a destination machine), which, upon request, returns the requested data, or any other response, in general, a server is called that processes the requests that come to it, and responds to them.
P2P (decryption - "peer-to-peer"), this is the type of network when, on a computer network, all the end machines can be both servers and clients, for example, a group of skype, when you call someone, you become a client (your skype), which requests a video exchange from the server (from Skype of the one you are calling to), now you have disconnected from the call, and the one you just spoke to sharply called you, now you are not a client, but a server (your Skype does not now make requests, but answers them), and Skype is the one called, not the server but the client (does not respond to requests, but sends them). This is how P2P works when all the machines are potentially both clients and servers. Again, an example of such a network is Skype.

Client server, this is the type of network when we strictly have strictly clients, and a server / server. That is, you can always only send requests, and the server can answer them, so the chat can work, your client (process) sends requests to check for new messages in the database, if any, the server will return them, if not, return another the answer is, when you send messages, it flies to the server with a request like “save the new message to the database”. That is, we have a group of clients, and the server, if two clients want to communicate, everything will go through the server, and the clients will only make requests to the server, asking them to "return all new messages", and the server will only respond. An example of such a network, this is the most applied network at the moment, is the web. All your actions in the browser, such as entering an address in the address bar, make a request to the server, and the server only responds. Your browser cannot become a server, and the server cannot become a browser. (Browser client process, server server process).

And just a little bit about security in networks.
Security in computer networks, this is now one of the most popular topics, information security, and a short article is not enough to explain even the most basic aspects. Here I will only talk about a couple of the most popular vulnerabilities, and attacks on computer networks.
Packet interception , as mentioned earlier, end machines exchange data through packets passing through the network. As you understand in the realities of our world, there are a lot of virtual structures that are associated with finances, for example, it can be banks, and just paying for a book in an online store is not important. All your data, in any case, will be transferred to another destination machine (server), and processed, and so, the essence of this vulnerability is that the data that is transmitted to the server, namely the packets, can be intercepted.
Accordingly, passwords or credit card numbers may be stolen. It can be that packages of a web browser, that packages of any P2P network. This vulnerability can be resolved by making a binding agreement between clients and servers that was discussed earlier.
What is the agreement mentioned earlier? This is not a mandatory procedure, the agreement of two processes on communication on such a port, such as IP, for example, a browser and a web server, start communication only after an agreement such as "three-way handshake", this is when you enter the address of the website, browser in the address bar of the browser First, it sends a request to the server with the question “we will work”, the server can answer “yes” or “no”, if so, the browser sends another request, and the connection is started, if not, the browser writes us some kind of error about access denied . I note that not all computer networks and protocols necessarily have some kind of “agreement”.And in this binding agreement, we agree to work on a protocol that encrypts data, for example, HTTPS, and the process of its processor is located on port 443 (this is also a port for TCP). That is, to agree to communicate on port 443, this is TCP with an operating time that works with HTTPS. What is HTTPS? This is a protocol, namely HTTP, which is encrypted with a special utility “SSL, TSL”, and most importantly, such a packet is encrypted both on the client and on the server, accordingly, intercepting such a packet, the attacker will not be able to decrypt anything and detect passwords and other ...
DDoS attack, this is an attack that is currently one of the most popular in computer networks. It works like this, with more end systems, through advertising, spam, and other advertising methods, malicious software (process) is installed that is not visible, and it usually works without any user actions, in the background, at a certain hour “H”, all computers infected with this process, begin to send a huge number of requests to a specific server, in order to disable this server, or router, on the way to the server. In the request, as a rule, there is not much weight flying (for the vastness of the attack), while the most complex information for processing by the server.
Attacks of this type disable the server, thereby losing the ability of the server to respond to more and more new requests, thus the server crashes and the operation fails, and there are very frequent cases when the router goes down on the way to server, because they have a clogged buffer, and the ability to send packets further is lost. Such attacks are usually very quickly fixed, but when such attacks occur on some kind of Internet exchange, or banks, users, that the structures themselves, suffer losses.
You can protect yourself from such an attack by analyzing the number of requests per second from the same IP. The minimum dangerous attack size at the moment is 100 thousand requests per second. There is also a parent of a DDoS attack, namely DoS, but at the moment this attack is not so scary, because the power of even the most outgoing servers allows you to handle such a not significant load.
Conclusions
In conclusion, I want to say some details about this article.
- In no case do not use this article as a textbook on computer networks, because this is just a “snack” for the novice in web programming, before a special study of computer networks, nothing more.
- This article shows only the basics of the basics, all moments bordering on the basics were missed, and not all network layer protocols were shown.
- This article does not talk about some things that you can take for the basics, such as router buffering, or data transfer delays, or data units of measurement at different levels, or the detailed operation of a router, and so on and so forth ... They were missed. for complex, and can confuse the beginner.
Thank you all very much for reading!
UPD: the article is intended for those who did not know anything about networks, but want to start at least not with complex books, but with a general overview.
