Security Week 28: while Petya was difficult to open, Broadcomm chipset bug was closed on Android, Copycat infected 14 million devices
 Last year’s Petya cryptoclocker Trojan, of course, can do a lot - it breaks MBR and encrypts MFT, but it didn’t work out to become as famous as its epigones. But the whole story with clones - data destroyers, apparently, so upset Janus, the author of the first-born, that he took and laid out the private key to him .
Last year’s Petya cryptoclocker Trojan, of course, can do a lot - it breaks MBR and encrypts MFT, but it didn’t work out to become as famous as its epigones. But the whole story with clones - data destroyers, apparently, so upset Janus, the author of the first-born, that he took and laid out the private key to him . However, he published not just “here, own it!”, But decided to get creative and play with “white hats”, password-protected the archive and left a link to it on his Twitter with a hint in the form of a quote from the movie “Golden Eye”. Perhaps, at least they will notice and remember. The author, apparently, is a fan of Bond - hence his nickname, the name of the file with the key (Natalya), and the names of the Trojans Petya and Misha. Faster than all, they solved the riddle in Malwarebytes and uploaded the contents of the file:
Congratulations!
Here is our secp192k1 privkey:
38dd46801ce61883433048d6d8c6ab8be18654a2695b4723
We used ECIES (with AES-256-ECB) Scheme to encrypt the decryption password into the "Personal Code" which is BASE58 encoded.
A researcher from Kaspersky Lab Anton Ivanov checked right there - the key turned out to be correct. Previously, researchers were breaking Petya, which forced Janus to fix an error in new versions of the Trojan, but now victims of all real Sing can freely get their files back.
This is not the first time a cryptoclocker key has been published - for example, something like this happened a year ago with TeslaCrypt . Now Janus just closed his project, at the same time blocking the oxygen to imitators, earning on a slightly modified Petya. Alas, this charity will not help the exPetr / non-Petya victims.
Google closed Broadpwn bug in Android
News. There is an opinion that it is not easy to pick up an infection on a smartphone - you have to blame a specific fool: agree to download an unknown file such as adobe_flash_update_mamoi_klyanus_bez_virusov.apk, allow the installation of untrusted programs, and finally install everything yourself. However, there are direct and obvious threats on mobile axes - RCE-bugs that are regularly found and closed. This time, a researcher from Exodus Intelligence announced a report at Black HAT USA 2017 about a particularly unpleasant bug CVE-2017-9417Associated with Broadcomm's BCM43xx WiFi Chips. They called him Broadpwn, which, as it were, should indicate the level of danger. And it allows you to run arbitrary code in the context of the kernel, and the attack is carried out remotely. Furthermore, it is interesting that the demonstrated exploit successfully bypasses DEP and ASLR.
There is no complete list of vulnerable smartphone models, but the author of the exploit claims that there is a bug in all Samsung flagships, in many LG and HTC models, as well as in several iPhones. By the way, nothing is yet known about the possibility of using Broadpwn under iOS, and Apple is silent about this bug, as you know who. Like Apple.
 In addition to Broadpwn, patches for another 11 critical holes, including the RCE-bug CVE-2017-0540, were included in the fresh Google update, which allows you to run code in a specially created file in the context of a privileged process. This “black hole” is present in Android 5.0.2, 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1 and 7.1.2. Patches will receive the owners of Nexus and Pixel, the rest - as luck. In general, the same feeling when Google with the next update eliminates several RCE vulnerabilities at once, but you understand that there will never be a patch on your smartphone released a year ago.
In addition to Broadpwn, patches for another 11 critical holes, including the RCE-bug CVE-2017-0540, were included in the fresh Google update, which allows you to run code in a specially created file in the context of a privileged process. This “black hole” is present in Android 5.0.2, 5.1.1, 6.0, 6.0.1, 7.0, 7.1.1 and 7.1.2. Patches will receive the owners of Nexus and Pixel, the rest - as luck. In general, the same feeling when Google with the next update eliminates several RCE vulnerabilities at once, but you understand that there will never be a patch on your smartphone released a year ago. Copycat Trojan infected 14 million Android devices
News. And again about mobile hygiene. Let’s say you sacredly respect the information security standards on mobile devices, don’t go anywhere on your smartphone and install only well-known applications with millions of downloads. Nevertheless, such a dirty trick as Copycat somehow turned out to be with you, and it shows you tons of advertising pop-ups. This is a fictional story, about 14 million Android devices were in this position, of which 8 million are also not so easy to remove the Trojan, since it got root rights.
The Trojan is spread not only by traditional methods, such as malicious landing pages and spam. It is embedded in popular applications and laid out in third-party application stores that are so popular in Asia - accordingly, most infections were detected in this region.
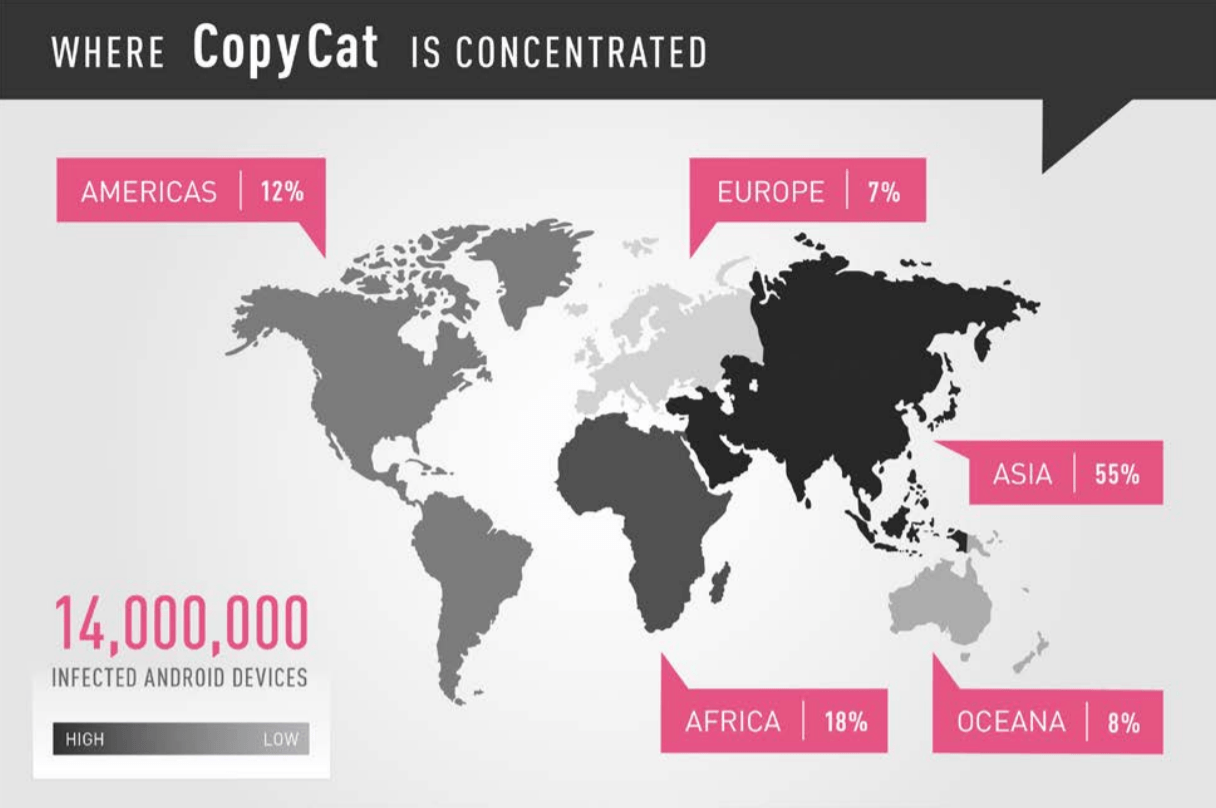
After installing and running the application with CopyCat inside, the Trojan takes out a bunch of master exploits and tries to get root rights in the system, after which it joyfully injects its library into the Zygote launcher daemon. Then he substitutes the installation referrer parameter (install_referrer) so as to receive money, which the publisher of the application invests in promotion. He also knows how to replace the advertisements displayed to the user, and is able to install third-party applications, that is, acts as a guaranteed distribution channel for anything that is ordered.

Antiquities
“Attention-629”
A dangerous non-resident virus that is written to the .COM files of the current directory. Extremely primitive. The 800th “descendant” of the virus at startup should report: “Attention! I'm virus ”, however, it contains so many errors that it is unlikely to live to such a respectable age.
Quote from the book "Computer viruses in MS-DOS" by Eugene Kaspersky. 1992 year. Page 60.
Disclaimer: This column reflects only the private opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Here it’s how lucky.
