Wordpress and Vanilla Forums zero day vulnerabilities allow remote hacking of sites

Image: Andrew Abogado , CC BY 2.0
Information security researcher David Golunski published data on critical vulnerabilities in WordPress - they allow remote execution of shell commands and resetting the administrator password by changing the Host header. In addition, the researcher spoke about two similar critical vulnerabilities in the open product Vanilla Forums.
WordPress Vulnerability
The Golunski vulnerability discovered (CVE-2017-8295) affects all versions of WordPress, including build 4.7.4. According to the researcher, he repeatedly transmitted information about security problems to the developers of the product, but they still have not issued an official fix.
The attack is described in detail in a special security bulletin published by Golunski. Its essence is to use a logical error in the Wordpress password recovery mechanism. When a user requests such a change, WordPress generates a unique secret code and sends it to an email, which is stored in the database.
When sending this message, the SERVER_NAME variable is used to obtain the server host name - this is necessary to set the values in the From / Return-Path fields. In the “From” field the sender’s address is stored, and in “Return-Path” - the address to which the 'bounce-back' messages should be delivered, they are generated in case of sending failure.
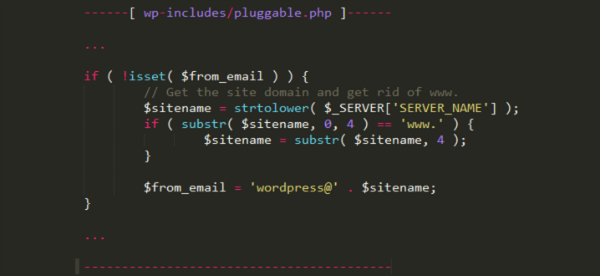
According to Golunsky, an attacker can send a special HTTP request with a predefined hostname value (for example, attacker-mxserver.com) and at the same time initiate a password reset process for a user - for example, a site administrator.
Since the host name in the HTTP request is the domain controlled by the attacker, the From and Return-Path fields in the password reset email will be changed so that they include the email address associated with the hacker domain - for example,
wordpress@attacker-mxserver.cominstead wordpress@victim-domain.com. A letter with a password reset code will still be sent to the victim’s address, however, under certain conditions, an attacker can also receive it.
- If the victim responds to the letter, the response will already be sent to the address of the cracker (now it is stored in the From field), and a link to reset the password will be saved in the correspondence history.
- If, for some reason, the delivery of the letter to the victim fails, then the message about the failure will be automatically redirected to the address of the attacker (it is specified in the Return-Path).
- Another possible scenario is to prevent the initial message from being delivered to the victim, an attacker could conduct a DDoS attack on the email server of the target user or send a large number of letters to his address, making sure that the mail address can no longer receive messages. Thus, the delivery will fail and a message will be delivered to the attacker.
Manipulations with the SERVER_NAME header using the Host HTTP header can be performed on the "default" settings of the Apache web server, which is most often used for deploying WordPress.
Since there is no official patch to close the vulnerability, it is recommended that WordPress site administrators update the configuration by activating the UseCanonicalName option - this will set the SERVER_NAME static value and make the attack impossible.
What's wrong with Vanilla Forums
A week after finding a security bug in WordPress, Golunski also posted information on two critical vulnerabilities in the popular open source software Vanilla Forums. The first one ( CVE-2016-10033 ) opens up the possibility of remote code execution, and the second (CVE-2016-10073) is similar to the vulnerability in WordPress and allows you to carry out attacks to intercept messages to reset the password. There is currently no patch for both errors. Vulnerable, including the latest version of Vanilla Forums 2.3, the researcher is sure that previous versions are also vulnerable.
According to Golunski, the ability to remotely execute shell commands appeared in the Vanilla Forums due to the fact that product developers still use a vulnerable version of the popular open source library to send PHPMailer emails. The researcher discovered the vulnerabilities in January 2017 and passed the information to the developers, the errors were not fixed and after about five months Golunsky published information about them. A similar vulnerability was previously discovered by a researcher in Wordpress.
Last year, the researcher reported on the detection of critical vulnerabilities ( CVE-2016-10033) in the PHPMailer library, which allowed remote execution of shell commands in the context of a web server - this leads to a compromise of the attacked web application. Golunski also prepared a video from which it becomes clear that an old PHPMailer exploit is suitable for attacking the Vanilla Forums.
The researcher notes that the vulnerability can be exploited even if the Vanilla Forums is installed on the Apache web server with several vhosts enabled, and the attacked software itself is not the default virtual host.
Until the developers of Vanilla Forums have released an update, Golunski recommends that site administrators who use this software set a predefined static value as the email address of the sender - this will block the use of Host headers.
To prevent attacks using the described vulnerabilities of WordPress and Vanilla Forums, Positive Technologies experts recommend using specialized protection tools - in particular, the PT Application Firewall application-level firewall allows you to reflect attempts to exploit these security errors.
