Huawei USG 6300. Basic firewall setup out of the box
The idea to write this article arose after I tried to find at least some information on setting up firewalls from Huawei on the Internet. In the Russian-language segment, I did not find anything; in the English-speaking segment, mostly outdated data on previous models and links to documentation (which, by the way, is on the manufacturer’s website in the public domain and is quite detailed).
If you have experience working with firewalls of other manufacturers, the documentation should be enough to start and work with Huawei USG, but from experience I know that the manuals are accessed when all the options have already been tried. Therefore, one of the goals of this article is to save time during the initial commissioning of this relatively new equipment. Of course, in one article it will not be possible to cover all the functionality, however, the main initial cases for setting up here will be considered. Engineers can use the article as a cheat sheet for installing network equipment, since the basic settings that will be described here, as a rule, will have to be done in all installations. A source

The article will not compare with competitors and generally a minimum of marketing, it will be a story about administration. I only mention that the main competitors of Huawei USG are Cisco ASA, CheckPoint, FortiNet, etc. Perhaps, the increased interest recently in Chinese equipment, in particular in information protection equipment, is related to the topic of "import substitution" of the above American vendors.
Huawei USG is a new generation of information protection devices, or the so-called NGFW (Next Generation FireWall). Unlike previous generation protection tools, NGFW is able to perform in-depth packet analysis (up to L7), inspect traffic at the application level, has integrated IPS, and can also interact with other similar devices, receiving from them information about potential attacks directed in their direction . It also has a simple DLP (information leak detection) mechanism.
The USG 6300 Series is the youngest series of devices targeted at small and medium-sized businesses. Brief specifications are given in the table below.
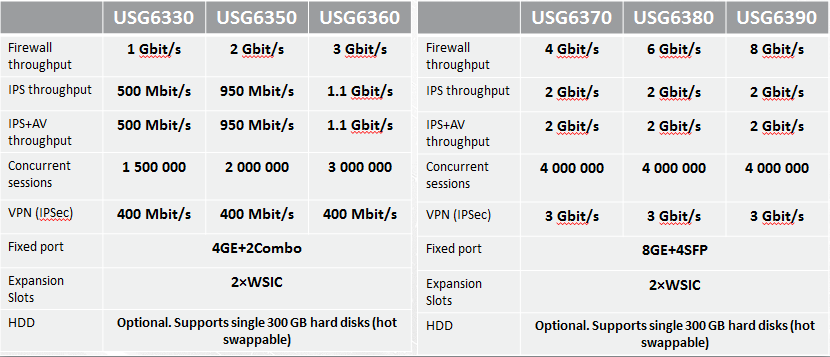
The 6300 Series devices listed in the table are designed for 19-inch rack mounting. When writing this article, the device was used Huawei USG 6320, made in the desktop version:

The main difference between the Huawei USG6320 and the rack versions of this series is that you cannot put a hard drive in it, which is used mainly for logging and generating reports based on the device from the WEB interface. Otherwise, all devices in the series (and even the older 6600 series) operate under the same VRP operating system. That is, at least at the time of writing, the “firmware” file for the 6300 and 6600 series is the same.
We connect via the console port with standard parameters (9600 baud, without parity), turn on the power and the download starts:
At the very beginning of the download, just in case, I will reset the device to the factory settings. Also, this step will be useful to you if you are dealing with a non-new device that has already been configured, and the password for the console is not known.
In order to enter the BootRom menu, you need to press Ctrl + B at the initial stage of loading. The default password to log into BootRom on most Huawei network devices is O & m15213 (the first letter is O, not zero). This is what the main BootRom menu looks like:
Select menu item 6 to reset to factory settings and then menu item 0 to reset.
After the download is complete, the device will prompt you to enter the login and password for management via the console port. Since we returned to the factory settings, the default login and password to the console will be:
The Huawei USG command line is very similar to the Cisco command line, with the exception of minor nuances. Cisco has three CLI command modes:
Unlike Cisco, the command line of Huawei network equipment (not only USG, but also switches and routers) consists of two modes:
System view combines privileged mode and global configuration mode.
Some more differences:
Thus, viewing the current working configuration (for Cisco this is show runn) in Huawei will be:
Just like in the CLI, Cisco does not have to enter the entire command. If part of the command is sufficient for recognition, then the command will be accepted, or you can use TAB to append.
First of all, it is necessary to establish which version of VRP OS is currently controlling the device, and if this is not the latest version, then the latest should be installed. You can check the VRP OS version with the command
at Cisco a similar command looks
We check:
In this case, the VRP OS version: V100R001C30SPC600PWE. That is, version 100, release 001, subrelease 30, service pack 600. It is also worth paying attention to the PWE suffix - this stands for Payload without encryption, i.e. our version of the software, in addition to being very old, will also not yet support strong encryption.
The current software version (as of March 2017) is v500r001c30spc100.
There is no point in starting to configure this device with an old version of software. Firstly, even the CLI part of the current V500 has changed, the syntax of some commands has changed, including commands related to security policy.
Secondly, the lack of strong encryption (namely, with such a version of the software, the device will be delivered to Russia to simplify importation) will, I think, not be suitable for many.
Therefore, first of all, you should update the Huawei USG VRP software to the latest version at the moment. You can download it from the manufacturer’s website if your login has the appropriate rights (as a rule, they are given to Huawei partners). If the latest version of the software is not available to you (you will see it on the website in any case, but it will not be possible to download it), you should contact the company through which your equipment was delivered or to the Russian-language support of Huawei.
I downloaded the file USG6000V500R001C30SPC100.bin VRP software from the site and put it in the folder of my TFTP server with the address 172.31.31.250.
I connected the junior port of Huawei USG to my local network 172.31.31.0 / 24 in order to download a new file from it via TFTP protocol. But for this you need to register an IP address from the network. Let's do it as follows:
The address is spelled out. But it turns out that our tftp server does not respond with USG. All this is because, by default, USG security policies are enabled and the default action is deny, i.e. to prohibit. To speed up the initial settings, I propose to make the default rule permit, and until the device is released on the Internet, this will not pose a threat to it. At the same time, it will greatly simplify the initial setup:
Check the reachability of the TFTP server:
Then we load the new version of the software from the TFTP server into flash memory using the command:
Next, you should tell the bootloader that after the reboot you need to download the software from this image, and not from what we have loaded now, for this we give the command:
Check that the next time the device boots, it will boot with the version of software we need:
Then save the configuration and reboot the device:
After rebooting, check the current version of the software:
As you can see, our version is now the latest. From this moment you can begin to configure the equipment.
Next, configure SSH for remote management, as HTTPS only is enabled by default.
We enable the ability to manage through the ssh service on all interfaces that we will participate in. Let GigabitEthernet0 / 0/7 be the WAN interface with public IP, and GigabitEthernet0 / 0/1 be the LAN interface with the network 192.168.200.0 / 24:
By default, Huawei USG has four firewall zones with the assigned priorities (in brackets): local (100), dmz (50), trust (85), untrust (5). Everything is very similar to how this is done in the Cisco ASA — users in the same zone have the same security attributes. The mechanism of operation of the security zones will be described in more detail below, but for now, we simply define the interfaces just configured in the corresponding zones:
Next, configure the default gateway:
Configure the VTY interface to support AAA:
Create a userssh user who can control the device via SSH:
Generate a local rsa key pair:
Enable the Secure Telnet (SSH) service:
We will configure userssh as an SSH administrator.
On this, you can consider the initial configuration completed and connect the cables of the external Internet and local network to the corresponding configured interfaces
I prefer to make the basic settings and upgrade the operating system from the command line, like most other configurations. Nevertheless, much (not all) could be done through the Web interface, which, in my opinion, is very well implemented, does not require Java or a client program (such as ASDM for Cisco ASA). Yes, and security policies, it seems to me, are much more visual and easier to create through the Web interface.
By default, the device’s Web interface is enabled and enabled on the Management port — on rack devices, this port is separate, and in our case in USG6320, by default, this port is the youngest on board, the one we used to update the software. By default, IP 192.168.0.1 / 24 is registered on the Management port, all types of services are allowed, and DHCP is enabled, so for opponents of the command line, you can use the WEB interface from the very beginning, knowing these parameters by default. They look like this:
The control port for https is 8443, and since we changed the address on the port a little earlier to 172.31.31.86, we will access the device from any browser as follows:
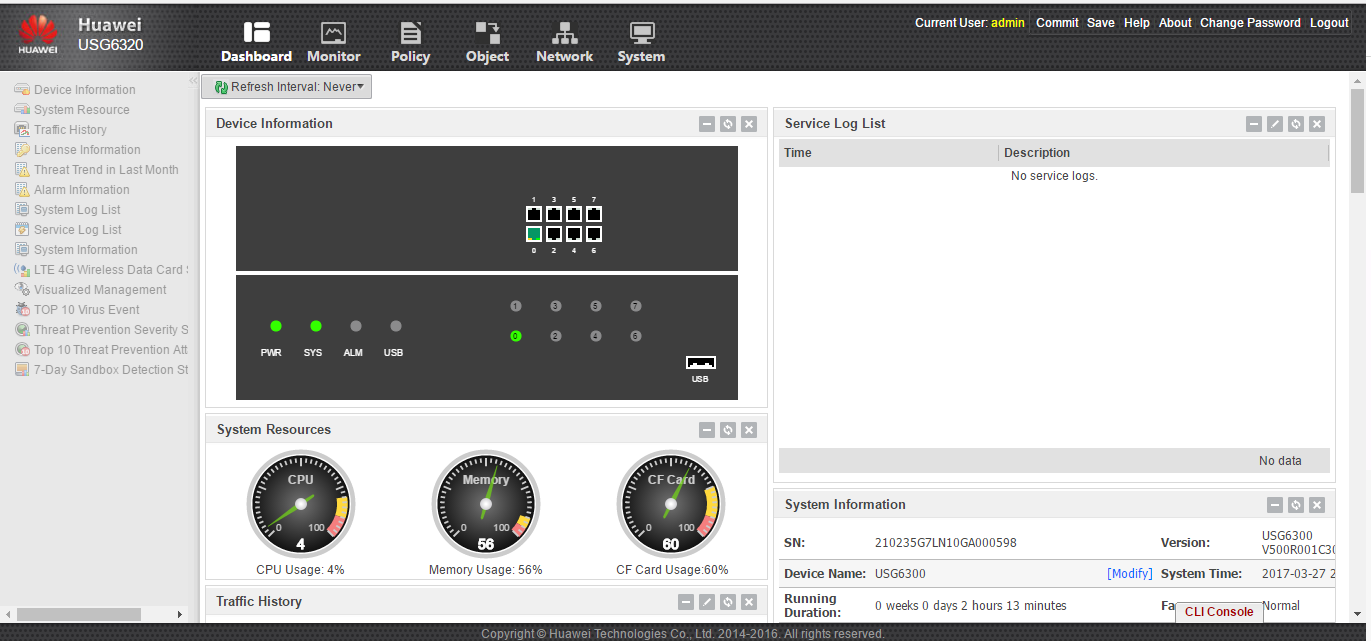
Dashboard tab of the Huawei USG web interface
First of all, you need to download purchased licenses in the System -> License Management section:
You can also use trial licenses by selecting the corresponding item with the following restrictions:
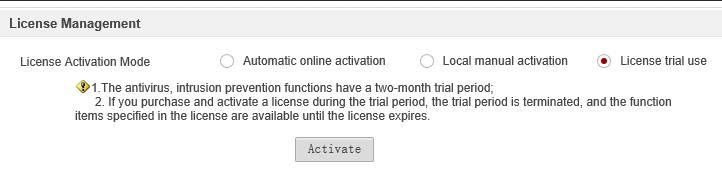
Trial antivirus and IPS subscriptions have a validity period of 2 months:
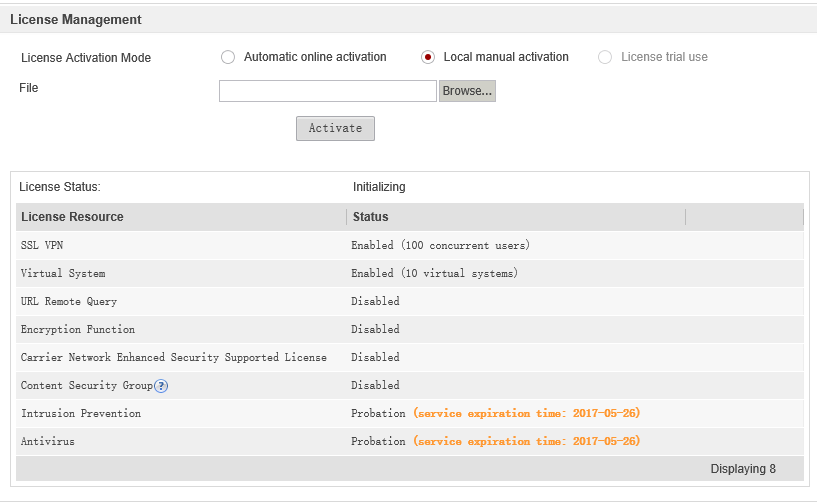
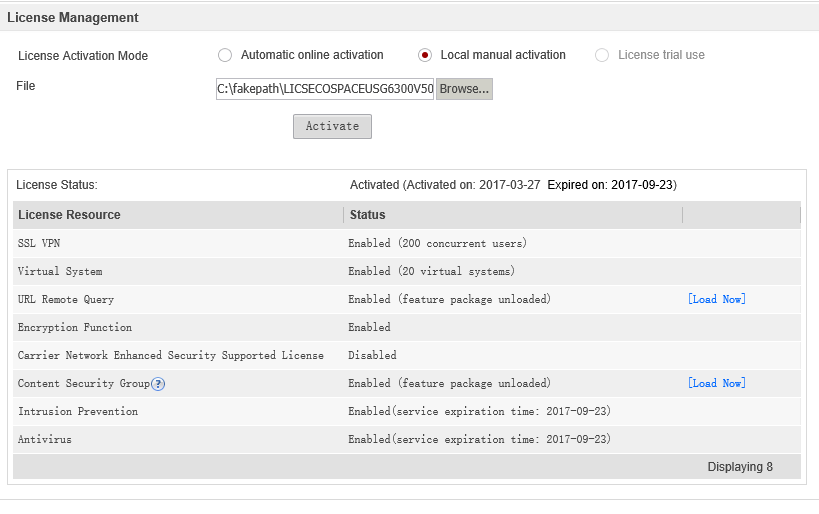
Either when Local is selected manual activation we substitute the generated file with the dat extension with a license, and our purchased licenses are activated:
Next, I propose to configure the device’s Internet connection and signature update via the Internet. Before proceeding with the settings, we briefly explain the mechanism of operation of security zones in Huawei USG.
As stated above, four security zones are configured by default:
You can change the priorities of zones, as well as add new zones, if necessary. This applies to all zones except local - its priority cannot be changed, nor can any interface be added to it.
Data streams within the same security zone are trusted and do not require security policy settings. If we need to configure the flow of data from one zone to another, then we will need to configure a security policy, taking into account the traffic directions according to the following rules.
The direction of traffic is determined by the direction of the first packet.
Let me remind you that we have already configured the interfaces and connected the cable from the provider to GigabitEhternet0 / 0/7, and the cable from our local network to GigabitEthernet0 / 0/1. If we try to ping something outside (untrust zone) directly from our device (local zone), then we will see the following picture:
All packets are lost, despite the fact that the default route is configured and the device is connected to the provider. In such a situation, a normal router would receive an ICMP response back and the picture would be different. But in our case, the security zone operation mechanism described above works and there is an initiation of data flow from the zone with priority 100 (local) to the zone with priority 5 (untrust), so we need to configure the security policy (outbound security policy) to allow walking packages in both directions. In the case of an outgoing policy with respect to traffic in the direction LOCAL → UNTRUST, our device will create a new record in the session table after each initiation of a new session in this direction. The record will contain the outgoing (source) and destination (destination) IP addresses,
If the packets exchanged by the client from the LOCAL zone and the server in the Untrust zone correspond to entries in the session table, the firewall processes the packets based on the outgoing security policy without having to check the direction of the packet transfer again. That is, in our case, we should receive ICMP ECHO from the address 8.8.8.8.
We’ll configure the policy in the Policy section by clicking the Add button with the name policy_to_Inet:
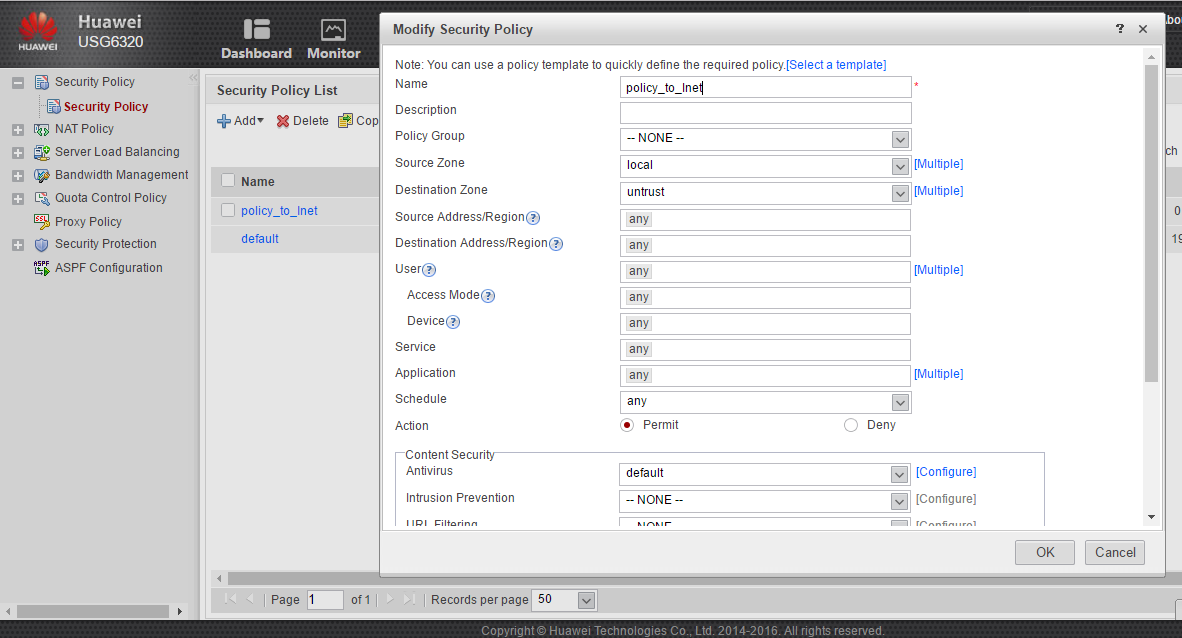
After applying the policy, we ’ll verify its functionality by running ping on the address 8.8.8.8 of our device:
In the System → Update Center section, we will try to update the IPS and antivirus signatures by clicking Update immediately opposite, for example, Antivirus Signature Database:

After a while, in the Status column, we see that the database download failed because the domain name of the update server (sec.huawei .com) could not be resolved. Indeed, in order for the names to be resolved, it is necessary to register the DNS server in the Network -> DNS section by clicking the Add button:
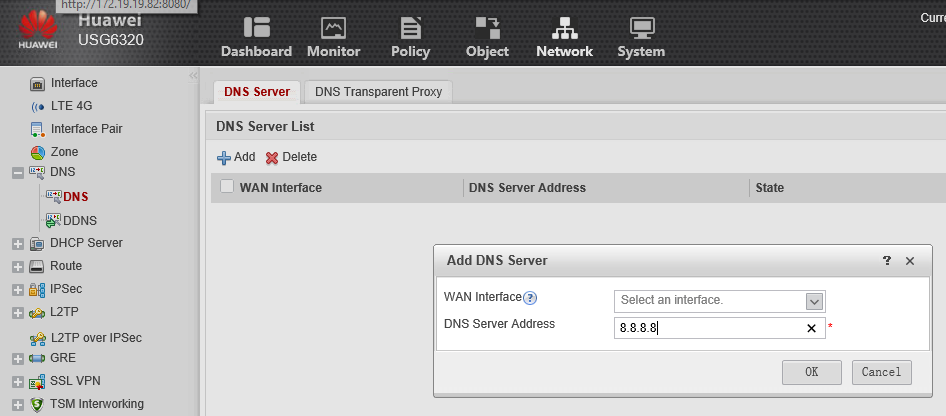
After registering the DNS server, everything turned out:
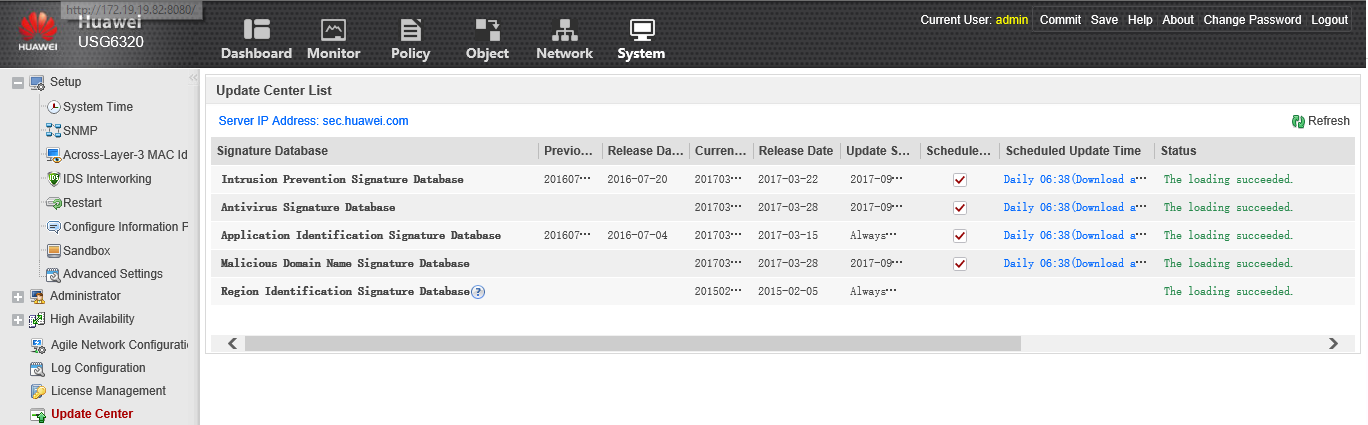
After that, all signatures will be updated according to their time in the Scheduled Update Time section, in this case every day at 6:38 a.m.
Configure Internet access for the local network 192.168.200.0 / 24 (our zone trust) via PAT. Since in this case the traffic direction will be from a zone with a high priority (trust) towards a zone, a lower priority (untrust), you need to configure outbound policy security. The rule here is exactly the same as we already did for the local zone. You can configure a new rule, or, if all other parameters are the same, add another Source Zone to the already created policy_to_Inet, in our case trust:
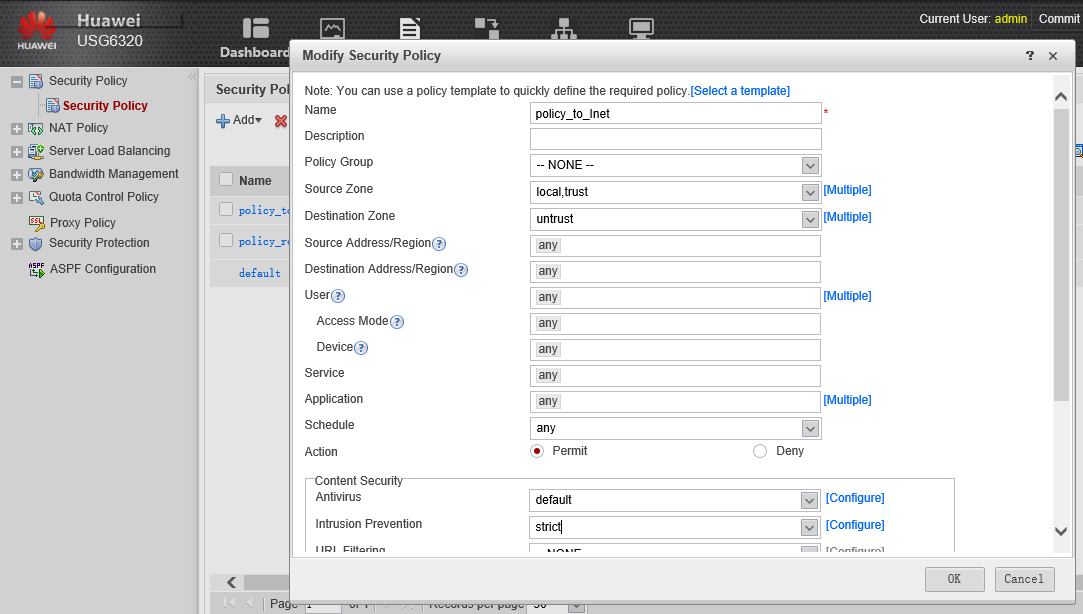
In the Content Security section, add the default predefined profile in the Antivirus subsection and the strict profile in the Intrusion Preventions subsection.
After that, create a NAT policy for the trust zone to access the Internet, "masking" the external IP address:
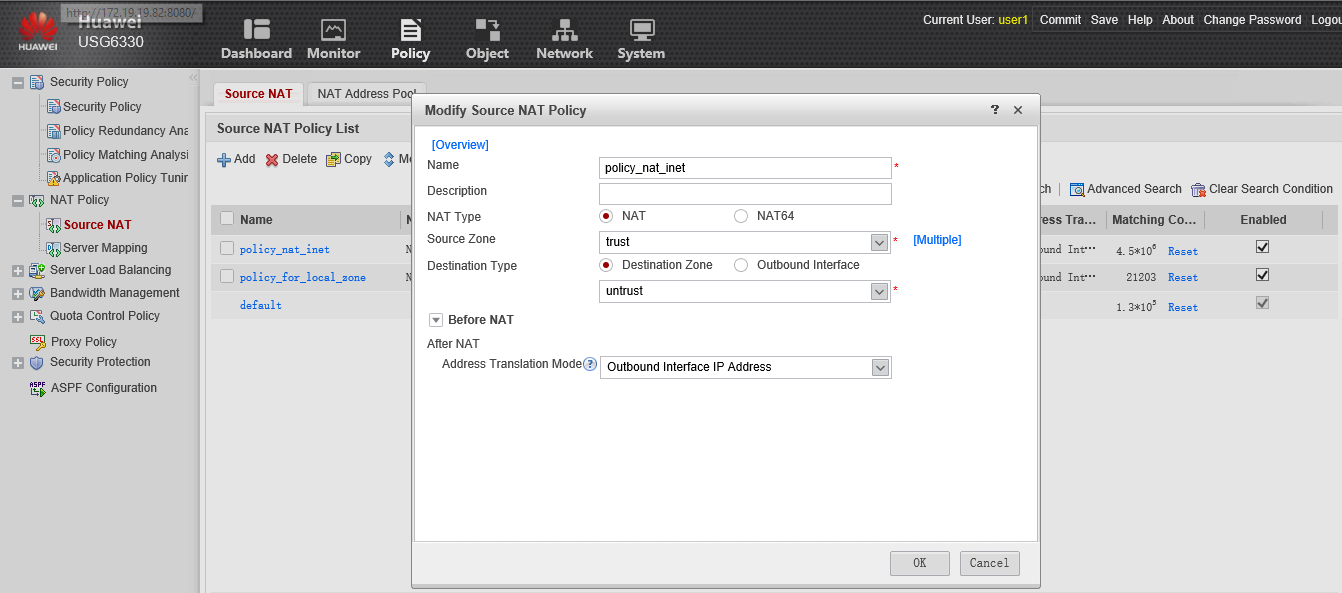
After that, users from the network 192.168.200.0 / 24 will be able to access the Internet.
The basic configuration of Huawei USG can be considered complete. The VRP device software was upgraded to the latest version, SSH was configured for remote control via the command line, setting up signature updates via the Internet and users accessing the Internet from a trusted zone.
Once again, a very good setup guide is worth mentioning (the HUAWEI USG6000 & USG9500 V500R001C30SPC200 & NGFW Module V500R002C00SPC200 Product Documentation was used in this article). In addition to the described functions, I configured IPsec site-to-site tunnels, SSL VPN for connecting remote users, integration with Microsoft Active Directory for authorizing remote SSL-VPN users and Single Sign On for domain users (access to the Internet for domain users without additional authorization) and other.
I hope this article will be useful for those who consider UTM / NGFW / Firewall devices to replace similar devices of famous American vendors.
If you have experience working with firewalls of other manufacturers, the documentation should be enough to start and work with Huawei USG, but from experience I know that the manuals are accessed when all the options have already been tried. Therefore, one of the goals of this article is to save time during the initial commissioning of this relatively new equipment. Of course, in one article it will not be possible to cover all the functionality, however, the main initial cases for setting up here will be considered. Engineers can use the article as a cheat sheet for installing network equipment, since the basic settings that will be described here, as a rule, will have to be done in all installations. A source

The article will not compare with competitors and generally a minimum of marketing, it will be a story about administration. I only mention that the main competitors of Huawei USG are Cisco ASA, CheckPoint, FortiNet, etc. Perhaps, the increased interest recently in Chinese equipment, in particular in information protection equipment, is related to the topic of "import substitution" of the above American vendors.
Huawei USG rulers and brief specifications
Huawei USG is a new generation of information protection devices, or the so-called NGFW (Next Generation FireWall). Unlike previous generation protection tools, NGFW is able to perform in-depth packet analysis (up to L7), inspect traffic at the application level, has integrated IPS, and can also interact with other similar devices, receiving from them information about potential attacks directed in their direction . It also has a simple DLP (information leak detection) mechanism.
The USG 6300 Series is the youngest series of devices targeted at small and medium-sized businesses. Brief specifications are given in the table below.

The 6300 Series devices listed in the table are designed for 19-inch rack mounting. When writing this article, the device was used Huawei USG 6320, made in the desktop version:

Its brief characteristics are as follows:
Interfaces: 8GE
Power: AC Adapter
Firewall throughput: 2 Gbit / s
IPS throughput: 700 Mbit / s
IPS + AV throughput: 700 Mbit / s
Concurrent sessions: 500,000
VPN Throughput (IPSec): 400Mbit / s
The main difference between the Huawei USG6320 and the rack versions of this series is that you cannot put a hard drive in it, which is used mainly for logging and generating reports based on the device from the WEB interface. Otherwise, all devices in the series (and even the older 6600 series) operate under the same VRP operating system. That is, at least at the time of writing, the “firmware” file for the 6300 and 6600 series is the same.
Turning on the device for the first time
We connect via the console port with standard parameters (9600 baud, without parity), turn on the power and the download starts:
***********************************************************
* *
* N G F W *
* *
***********************************************************
Base Bootrom Ver : 060 Dec 4 2015 06:55:42
Extended Bootrom Ver : 060 Dec 4 2015 07:00:34
CPLD BigVer : 02
CPLD SmlVer : 00 2015-03-19
PCB Ver : SUE1MPUB REV A
BOM Ver : 000
CPU L2 Cache : 2048 KB
CPU Core Frequency : 1000 MHz
BUS Frequency : 600 MHz
Mem Size : 2048 MB
Press Ctrl+B to enter main menu...At the very beginning of the download, just in case, I will reset the device to the factory settings. Also, this step will be useful to you if you are dealing with a non-new device that has already been configured, and the password for the console is not known.
In order to enter the BootRom menu, you need to press Ctrl + B at the initial stage of loading. The default password to log into BootRom on most Huawei network devices is O & m15213 (the first letter is O, not zero). This is what the main BootRom menu looks like:
====================< Extend Main Menu >====================
| <1> Boot System |
| <2> Set Startup Application Software and Configuration |
| <3> File Management Menu... |
| <4> Load and Upgrade Menu... |
| <5> Modify Bootrom Password |
| <6> Reset Factory Configuration |
| <0> Reboot |
| ---------------------------------------------------------|
| Press Ctrl+T to Enter Manufacture Test Menu... |
| Press Ctrl+Z to Enter Diagnose Menu... |
============================================================
Enter your choice(0-6):Select menu item 6 to reset to factory settings and then menu item 0 to reset.
After the download is complete, the device will prompt you to enter the login and password for management via the console port. Since we returned to the factory settings, the default login and password to the console will be:
Login: admin
Password: Admin@123
Huawei USG Command Line
The Huawei USG command line is very similar to the Cisco command line, with the exception of minor nuances. Cisco has three CLI command modes:
- user mode (icon>);
- privileged mode (icon #, input by enable command);
- global configuration mode (entry from the configure terminal command from privileged mode).
Unlike Cisco, the command line of Huawei network equipment (not only USG, but also switches and routers) consists of two modes:
- user mode (also icon>);
- System view mode (icon #, entry by system-view command from user mode).
System view combines privileged mode and global configuration mode.
Some more differences:
- Cisco's show command is similar to Huawei's VRP display command;
- Cisco's no command is similar to Huawei's undo.
Thus, viewing the current working configuration (for Cisco this is show runn) in Huawei will be:
display current-configurationJust like in the CLI, Cisco does not have to enter the entire command. If part of the command is sufficient for recognition, then the command will be accepted, or you can use TAB to append.
First of all, it is necessary to establish which version of VRP OS is currently controlling the device, and if this is not the latest version, then the latest should be installed. You can check the VRP OS version with the command
display version at Cisco a similar command looks
show versionWe check:
display version
17:02:50 2017/03/27
Huawei Versatile Security Platform Software
Software Version: USG6300 V100R001C30SPC600PWE (VRP (R) Software, Version 5.30)
Copyright (C) 2014-2016 Huawei Technologies Co., Ltd..
USG6320 uptime is 0 week, 0 day, 0 hour, 2 minutes
Engine Version : V200R001C10
AV Signature Database Version :
IPS Signature Database Version :
IPS Engine Version : V200R001C10SPC352
SA Signature Database Version : 2015121601
Location Signature Database Version : 2015020515
RPU's Version Information:
2048M bytes SDRAM
16M bytes FLASH
1024M bytes CFCARD
1024K bytes SRAM
PCB Version : VER.A
CPLD Version : 200
Base Bootrom Version : 060 Dec 4 2015 06:55:42
Extended Bootrom Version : 060 Dec 4 2015 07:00:34 In this case, the VRP OS version: V100R001C30SPC600PWE. That is, version 100, release 001, subrelease 30, service pack 600. It is also worth paying attention to the PWE suffix - this stands for Payload without encryption, i.e. our version of the software, in addition to being very old, will also not yet support strong encryption.
Device Software Update
The current software version (as of March 2017) is v500r001c30spc100.
There is no point in starting to configure this device with an old version of software. Firstly, even the CLI part of the current V500 has changed, the syntax of some commands has changed, including commands related to security policy.
Secondly, the lack of strong encryption (namely, with such a version of the software, the device will be delivered to Russia to simplify importation) will, I think, not be suitable for many.
Therefore, first of all, you should update the Huawei USG VRP software to the latest version at the moment. You can download it from the manufacturer’s website if your login has the appropriate rights (as a rule, they are given to Huawei partners). If the latest version of the software is not available to you (you will see it on the website in any case, but it will not be possible to download it), you should contact the company through which your equipment was delivered or to the Russian-language support of Huawei.
I downloaded the file USG6000V500R001C30SPC100.bin VRP software from the site and put it in the folder of my TFTP server with the address 172.31.31.250.
I connected the junior port of Huawei USG to my local network 172.31.31.0 / 24 in order to download a new file from it via TFTP protocol. But for this you need to register an IP address from the network. Let's do it as follows:
system-view
[USG6300]interface GigabitEthernet0/0/0
[USG6300-GigabitEthernet0/0/0] ip address 172.31.31.86 255.255.255.0
[USG6300-GigabitEthernet0/0/0]quit
[USG6300] The address is spelled out. But it turns out that our tftp server does not respond with USG. All this is because, by default, USG security policies are enabled and the default action is deny, i.e. to prohibit. To speed up the initial settings, I propose to make the default rule permit, and until the device is released on the Internet, this will not pose a threat to it. At the same time, it will greatly simplify the initial setup:
[USG6300] security-policy
[USG6300-policy-security] default action permit
Warning:Setting the default packet filtering to permit poses security risks. You are advised to configure the security policy based on the actual data flows. Are you sure you want to continue?[Y/N]Y
[USG6300-policy-security] quit
[USG6300]Ctrl+ZCheck the reachability of the TFTP server:
ping 172.31.31.250
17:46:58 2017/03/27
PING 172.31.31.250: 56 data bytes, press CTRL_C to break
Reply from 172.31.31.250: bytes=56 Sequence=1 ttl=128 time=1 ms
Reply from 172.31.31.250: bytes=56 Sequence=2 ttl=128 time=1 ms Then we load the new version of the software from the TFTP server into flash memory using the command:
tftp 172.31.31.250 get USG6000V500R001C30SPC100.bin Next, you should tell the bootloader that after the reboot you need to download the software from this image, and not from what we have loaded now, for this we give the command:
startup system-software USG6000V500R001C30SPC100.bin
Info:System software for the next startup:hda1:/usg6000v500r001c30spc100.bin, start read file....
Succeeded in setting the software for booting system.
Check that the next time the device boots, it will boot with the version of software we need:
display startup
17:50:53 2017/03/27
MainBoard:
Configed startup system software:
hda1:/suempua15v1r1c30spc600pwe.bin
Startup system software:
hda1:/suempua15v1r1c30spc600pwe.bin
Next startup system software: hda1:/usg6000v500r001c30spc100.bin
Startup saved-configuration file: NULL
Next startup saved-configuration file: NULL Then save the configuration and reboot the device:
save all
reboot
17:52:31 2017/03/27
System will reboot! Do you want to save the running configuration? [Y/N]:Y
2017-03-27 17:52:33 USG6300 %%01CFM/4/SAVE(l): When deciding whether to save configuration to the device, the user admin chose Y.
Next config file name is NULL,set to Default...
Next config file is hda1:/vrpcfg.zip
Now saving the current configuration to the device....
Info:The current configuration was saved to the device successfully..
System will reboot! Continue? [Y/N]:Y After rebooting, check the current version of the software:
display version
2017-03-27 18:37:42.590
Huawei Versatile Routing Platform Software
VRP (R) Software, Version 5.160 (USG6300 V500R001C30SPC100)
Copyright (C) 2014-2016 Huawei Technologies Co., Ltd
USG6320 uptime is 0 week, 0 day, 0 hour, 37 minutes As you can see, our version is now the latest. From this moment you can begin to configure the equipment.
Configuring Interfaces and SSH for Remote Management
Next, configure SSH for remote management, as HTTPS only is enabled by default.
We enable the ability to manage through the ssh service on all interfaces that we will participate in. Let GigabitEthernet0 / 0/7 be the WAN interface with public IP, and GigabitEthernet0 / 0/1 be the LAN interface with the network 192.168.200.0 / 24:
system-view
[USG6300] interface GigabitEthernet 0/0/7
[USG6300-GigabitEthernet0/0/7] service-manage enable
[USG6300-GigabitEthernet0/0/7] service-manage ssh permit
[USG6300-GigabitEthernet0/0/7] ip address 195.26.xxx.xxx 255.255.255.224
[USG6300-GigabitEthernet0/0/7] service-manage http permit
[USG6300-GigabitEthernet0/0/7] service-manage https permit
[USG6300-GigabitEthernet0/0/7] service-manage ping permit
[USG6300-GigabitEthernet0/0/7] quit
[USG6300] interface GigabitEthernet0/0/1
[USG6300-GigabitEthernet0/0/1] undo shutdown
[USG6300-GigabitEthernet0/0/1] ip address 192.168.200.100 255.255.255.0
[USG6300-GigabitEthernet0/0/1] service-manage http permit
[USG6300-GigabitEthernet0/0/1] service-manage https permit
[USG6300-GigabitEthernet0/0/1] service-manage ping permit
[USG6300-GigabitEthernet0/0/1] service-manage ssh permit By default, Huawei USG has four firewall zones with the assigned priorities (in brackets): local (100), dmz (50), trust (85), untrust (5). Everything is very similar to how this is done in the Cisco ASA — users in the same zone have the same security attributes. The mechanism of operation of the security zones will be described in more detail below, but for now, we simply define the interfaces just configured in the corresponding zones:
[USG6300] firewall zone trust
[USG6300-zone-trust] add interface GigabitEthernet0/0/1
[USG6300-zone-trust] quit
[USG6300] firewall zone untrust
[USG6300-zone-untrust] add interface GigabitEthernet0/0/7
[USG6300-zone-untrust] quitNext, configure the default gateway:
[USG6300] ip route-static 0.0.0.0 0.0.0.0 195.26.xxx.1Configure the VTY interface to support AAA:
[USG6300] user-interface vty 0 4
[USG6300-vty0-4] authentication-mode aaa
[USG6300-vty0-4] protocol inbound ssh
[USG6300-vty0-4] user privilege level 15
[USG6300-vty0-4] quitCreate a userssh user who can control the device via SSH:
[USG6300] aaa
[USG6300-aaa] manager-user userssh
[USG6300-aaa-manager-user-userssh] password
Enter Password:
Confirm Password:
[USG6300-aaa-manager-user-userssh] service-type ssh
[USG6300-aaa-manager-user-userssh] quit
[USG6300-aaa] bind manager-user userssh role system-admin
[USG6300-aaa] quitGenerate a local rsa key pair:
[USG6300] rsa local-key-pair createEnable the Secure Telnet (SSH) service:
[USG6300] stelnet server enableWe will configure userssh as an SSH administrator.
[USG6300] ssh user userssh
[USG6300] ssh user userssh authentication-type password
[USG6300] ssh user userssh service-type stelnetOn this, you can consider the initial configuration completed and connect the cables of the external Internet and local network to the corresponding configured interfaces
Setup using the WEB interface
I prefer to make the basic settings and upgrade the operating system from the command line, like most other configurations. Nevertheless, much (not all) could be done through the Web interface, which, in my opinion, is very well implemented, does not require Java or a client program (such as ASDM for Cisco ASA). Yes, and security policies, it seems to me, are much more visual and easier to create through the Web interface.
By default, the device’s Web interface is enabled and enabled on the Management port — on rack devices, this port is separate, and in our case in USG6320, by default, this port is the youngest on board, the one we used to update the software. By default, IP 192.168.0.1 / 24 is registered on the Management port, all types of services are allowed, and DHCP is enabled, so for opponents of the command line, you can use the WEB interface from the very beginning, knowing these parameters by default. They look like this:
interface GigabitEthernet0/0/0
undo shutdown
ip address 192.168.0.1 255.255.255.0
anti-ddos flow-statistic enable
anti-ddos syn-flood source-detect alert-rate 100
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
dhcp select interface
dhcp server ip-range 192.168.0.1 192.168.0.254The control port for https is 8443, and since we changed the address on the port a little earlier to 172.31.31.86, we will access the device from any browser as follows:
https://172.31.31.86:8443

Dashboard tab of the Huawei USG web interface
First of all, you need to download purchased licenses in the System -> License Management section:

You can also use trial licenses by selecting the corresponding item with the following restrictions:

Trial antivirus and IPS subscriptions have a validity period of 2 months:

Either when Local is selected manual activation we substitute the generated file with the dat extension with a license, and our purchased licenses are activated:

Configure security policies and signature updates
Next, I propose to configure the device’s Internet connection and signature update via the Internet. Before proceeding with the settings, we briefly explain the mechanism of operation of security zones in Huawei USG.
As stated above, four security zones are configured by default:
- Untrust (5). Определяет небезопасный сегмент сети, такой как Интернет, имеет наименьший уровень безопасности 5.
- DMZ (50). Определяет сегмент, в котором, как правило, располагаются сервера, к которым необходимо предоставить доступ снаружи. Но в то же время из этой зоны запрещен доступ к более защищенным сегментам сети.
- Trust (85). Определяет защищенный сегмент сети, где, как правило, располагаются рабочие станции пользователей.
- Local (100). Зона самого устройства USG, включая его интерфейсы.
You can change the priorities of zones, as well as add new zones, if necessary. This applies to all zones except local - its priority cannot be changed, nor can any interface be added to it.
Data streams within the same security zone are trusted and do not require security policy settings. If we need to configure the flow of data from one zone to another, then we will need to configure a security policy, taking into account the traffic directions according to the following rules.
- Inbound: traffic from the lower priority zone to the higher priority zone.
- Outbound: traffic from a higher priority zone to a lower priority zone is forwarded.
The direction of traffic is determined by the direction of the first packet.
Let me remind you that we have already configured the interfaces and connected the cable from the provider to GigabitEhternet0 / 0/7, and the cable from our local network to GigabitEthernet0 / 0/1. If we try to ping something outside (untrust zone) directly from our device (local zone), then we will see the following picture:
[USG6300]ping 8.8.8.8
PING 8.8.8.8: 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
--- 8.8.8.8 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet lossAll packets are lost, despite the fact that the default route is configured and the device is connected to the provider. In such a situation, a normal router would receive an ICMP response back and the picture would be different. But in our case, the security zone operation mechanism described above works and there is an initiation of data flow from the zone with priority 100 (local) to the zone with priority 5 (untrust), so we need to configure the security policy (outbound security policy) to allow walking packages in both directions. In the case of an outgoing policy with respect to traffic in the direction LOCAL → UNTRUST, our device will create a new record in the session table after each initiation of a new session in this direction. The record will contain the outgoing (source) and destination (destination) IP addresses,
If the packets exchanged by the client from the LOCAL zone and the server in the Untrust zone correspond to entries in the session table, the firewall processes the packets based on the outgoing security policy without having to check the direction of the packet transfer again. That is, in our case, we should receive ICMP ECHO from the address 8.8.8.8.
We’ll configure the policy in the Policy section by clicking the Add button with the name policy_to_Inet:

After applying the policy, we ’ll verify its functionality by running ping on the address 8.8.8.8 of our device:
[USG6300]ping 8.8.8.8
PING 8.8.8.8: 56 data bytes, press CTRL_C to break
Reply from 8.8.8.8: bytes=56 Sequence=1 ttl=47 time=19 ms
Reply from 8.8.8.8: bytes=56 Sequence=2 ttl=47 time=21 ms
Reply from 8.8.8.8: bytes=56 Sequence=3 ttl=47 time=19 ms
Reply from 8.8.8.8: bytes=56 Sequence=4 ttl=47 time=20 ms
Reply from 8.8.8.8: bytes=56 Sequence=5 ttl=47 time=20 ms
--- 8.8.8.8 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 19/19/21 msIn the System → Update Center section, we will try to update the IPS and antivirus signatures by clicking Update immediately opposite, for example, Antivirus Signature Database:

After a while, in the Status column, we see that the database download failed because the domain name of the update server (sec.huawei .com) could not be resolved. Indeed, in order for the names to be resolved, it is necessary to register the DNS server in the Network -> DNS section by clicking the Add button:

After registering the DNS server, everything turned out:

After that, all signatures will be updated according to their time in the Scheduled Update Time section, in this case every day at 6:38 a.m.
Configuring NAT / PAT for LAN access to the Internet
Configure Internet access for the local network 192.168.200.0 / 24 (our zone trust) via PAT. Since in this case the traffic direction will be from a zone with a high priority (trust) towards a zone, a lower priority (untrust), you need to configure outbound policy security. The rule here is exactly the same as we already did for the local zone. You can configure a new rule, or, if all other parameters are the same, add another Source Zone to the already created policy_to_Inet, in our case trust:

In the Content Security section, add the default predefined profile in the Antivirus subsection and the strict profile in the Intrusion Preventions subsection.
After that, create a NAT policy for the trust zone to access the Internet, "masking" the external IP address:

After that, users from the network 192.168.200.0 / 24 will be able to access the Internet.
The basic configuration of Huawei USG can be considered complete. The VRP device software was upgraded to the latest version, SSH was configured for remote control via the command line, setting up signature updates via the Internet and users accessing the Internet from a trusted zone.
Once again, a very good setup guide is worth mentioning (the HUAWEI USG6000 & USG9500 V500R001C30SPC200 & NGFW Module V500R002C00SPC200 Product Documentation was used in this article). In addition to the described functions, I configured IPsec site-to-site tunnels, SSL VPN for connecting remote users, integration with Microsoft Active Directory for authorizing remote SSL-VPN users and Single Sign On for domain users (access to the Internet for domain users without additional authorization) and other.
I hope this article will be useful for those who consider UTM / NGFW / Firewall devices to replace similar devices of famous American vendors.
