Tails OS or how to protect yourself online
· Tails
First of all, you should get acquainted with the main character of this article. Without this OS, one could not try to discover the door to the world of anonymity. Tails are used more than 20,000 times a day, journalists and human rights activists use Tails to condemn the wrongdoings of governments and corporations.
TheAmnesicIncognitoLiveSystem is an operating system that you can run on almost any computer from a USB drive or DVD.
This OS aims to preserve your privacy and anonymity will help you use the Internet anonymously and circumvent censorship - all connections are forced to go through the TOR network, as well as leave no traces on the computer that you use and use the latest cryptographic tools to encrypt your files, email, instant messaging and hiding all files and directories on electronic media.
· Installing Tails
Well, let's start the installation of this miracle. We need one USB 8GB (min.), Etcher program and half an hour of time.
First of all, go here and download the image directly. In my case, this is version 3.12, then we download the Etcher program to install our OS from the official site, and then proceed to the installation. The interface of this program is intuitive: you can select an OS image, a USB flash drive and press start. The process takes about 5 minutes. After the image is loaded without disconnecting the USB, restart the computer, go to the BIOS and select the USB flash drive as the boot device. Next, boot from it.
· Presetting Tails
Now you will see the Greeting menu, it will meet you every time you log in and I advise you to always apply the following settings. It is required to enter additional settings, we set an administrator password there, a MAC address spoofing, a connection via Tor and bridges.
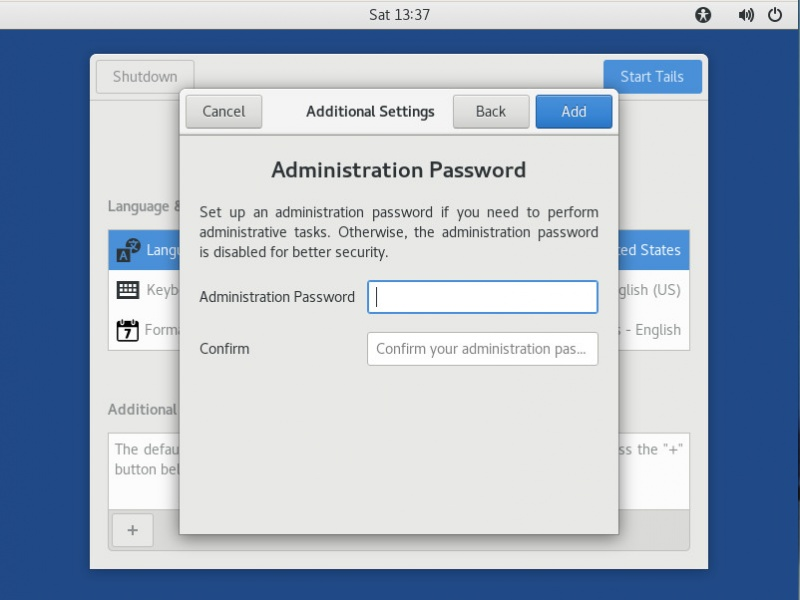
And again we need the tab "applications". Go to the folder TAILS and Configure persistent volume.
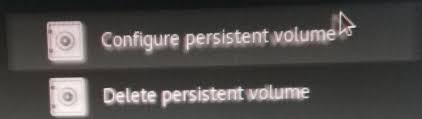
We entered the Persistent Wizard. First, set the password, you will need to enter it every time Tails is turned on, after you see a number of options with options - the files and settings that should be saved, put the bird on the desired one.
· Saving files and settings Persistent Volume
Before pumping the Tails you need to learn how to save the results of your improvements. Tails is not designed to keep installed programs, settings and files when it is turned off. But the developers made it possible to save certain data in the persistent section that we created earlier. For example, to install any program you need to go to the Synaptic package manager, specify a new program repository and select the one you need. And just to save some files move them to Home / Persistent.
So despite the fact that the session itself is not saved when the computer is turned off, the APT packages (settings, browser extensions, etc.) will remain in the persistent section with the correct settings. This makes it possible to deploy all necessary programs during the operating system boot process.
· Data Protection in Persistent Volume
Persistent Volume is encrypted by default, but there is one problem - you can decrypt anything but not find it. So that our persistent section could not be detected, we use something better than the developers recommend.
The hidden section is not very convenient to use, so only if you need to install this program, if you do not need TrueCrypt skip this item.
So, the Tails developers advise using Cryptsetup, but the section created by this tool is hidden quite well. Why create such a section if it can be found, so we will use TrueCrypt , the section created by this tool cannot be found. PS Despite the fact that the TrueCrypt project was closed in 2014, it suits us, as there were people who continued to develop.
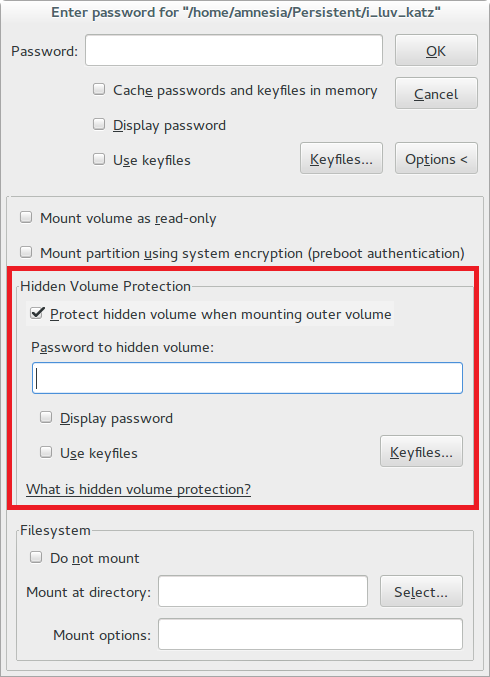
The TrueCrypt section is hidden so that the OS will not find it until you enter the correct password.
Therefore, while writing files to our hidden section may be damaged.
In order not to damage the dogs in the hidden section, you need to tick the creation, as in the screenshot below.
· TOR Browser
This browser is known to everyone who is interested in Internet security and whoever has ever tried to bypass various locks, be it rutracker, or any other blocked services.
The first tab we need is Browser Privacy. Let's put always to work in the private viewing mode, protection against tracking - always, fake and deceptive content - we include everything.
Now click on TorButton, this button to the left of the search bar. Here we choose the maximum level of protection.
The strongest browser defender is, of course, “Add-ons”, they will protect you from being tracked while surfing the Internet, malicious sites will be blocked. Some of them are already installed in the TOR in advance by the developers, but they do not provide full protection
Disconnect - Confidential Advertising Blocker: Blocks google analytics trackers / Yandex statistics, etc. - The main means of tracking your history of visiting sites, location and many other data.
Adblock Plus - Blocks trackers, mining, ads, etc.
User-Agent Switcher - Automatically changes your fingerprint on your computer \ browser.
Man in the Middle - Protects against Internet traffic interception \ MITM attacks. This extension can be hidden from the extension panel.
Disable WebRTC - The WebRTC protocol provides real ip, TOR network and other data, even if you use other security features, so disable this protocol.
Now you should configure these extensions.
NoScript - this extension must be configured depending on the level of protection you want to have. But it is important to remember that if you check the boxes everywhere, most sites will not work correctly.
Https Everywhere - click on the button of this add-on and put a tick in both items.
AdBlock Plus - Go to the settings and in the "third-party filters" it is desirable to select additional databases.
User-Agent Switcher - Here we choose a spread of 25%, and all UserAgents.
· Attached
Well, you are protected from tracking and you can start surfing the Internet with peace of mind, but in Tails there is also software already bundled with the OS, and I will tell about it
· Communication
For communication, Tails are equipped with Pidgin, OnionShare and Thunderbird. We will deal with everything in order. Pidgin acts as a chat client with an installed add-on for encrypting messages, OnionShare helps you share files, and Thunderbird for email.
· Encryption and privacy
Since this OS is focused on anonymity and security, the development team has invested a lot of interesting tools for anonymization. For example, the MAT program, it erases file metadata that can reveal a lot of personal information about the creator. As I said earlier, there are many such programs in Tails so that you can view their list on the developer’s website or explore them yourself
· Other useful software
The creators did not stint on the software useful to any user: LibreOffice, Gimp and Inkscape, pdf-redact-tools and some others.
· Instead of conclusion
Now you have learned about real security on the Internet whose name is Tails, here I did not tell about all the features of this live OS, but only did a brief overview with the installation.
Install, use, learn.
