Street Fighter V computer game driver disables the built-in Windows protection mechanism
Drivers for computer games that are used to protect the integrity of game files, as well as the legitimacy of these players are not uncommon. Earlier, several reviews of the most famous such drivers were published, for example, nProtect GameGuard and Blizzard Lockdown . Such drivers can take advantage of intercepting API calls at the Windows kernel level, constantly scanning the virtual address space of processes, monitoring access to the registry, etc.

A few days ago, Capcom notifiedits users about updating the anti-hack driver (Capcom.sys), which is used to monitor the integrity of game files and prevents possible memory compromise of the game process in order to prevent cheating. However, users in this update had an unpleasant surprise in one of the driver functions. It allows you to disable the protective measure of the SMEP kernel and execute code according to the pointer obtained from user mode.
SMEP (Supervisor Mode Execution Prevention) is already a fairly well-known measure that has been written aboutsome reviews. It requires support both from the microprocessor and from the OS (Windows 8+). SMEP is used to block the user-mode code execution operation (Ring 3) in kernel mode (RIng 0). No matter how strange it looks (kernel mode code is the most privileged and has the ability to access all memory in the system), SMEP is a good measure to block the activity of LPE exploits, which often transfer control to a code block located in the user part of the virtual address space .
Windows drivers are organized in such a way that to interact with the client from Ring 3, a special interface is used called IOCTL. The driver registers a special handler in the Windows kernel, which can be used from user mode by the well-known API function DeviceIoControl . When using this API, the application passes the driver the code of the required function, the set of arguments, and indicates the input and output memory buffers for passing arguments and obtaining the result.
New Capcom.sys update usesIOCTL interface and two functions with codes 0xAA012044, 0xAA013044. The peculiarity of these functions is that they allow the user-mode client to execute code in kernel mode using the pointer received from there, and before that it disables SMEP. After the function is executed, the SMEP is switched back on by setting the corresponding bit of the CR4 register. Obviously, disabling is used to execute code in kernel mode from user mode.
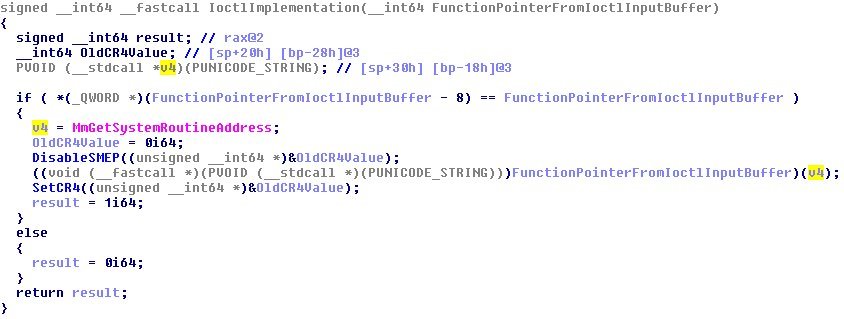
Fig. Capcom.sys function that executes the function specified in the IOCTL request with SMEP disabled.
Obviously, since the driver of the computer game is digitally signed and provides such a potentially dangerous interface for access from user mode, it creates a backdoor in the system. Third-party code can use this driver to execute its code in Ring 0.
Capcom has already released a game update to close this vulnerability.

A few days ago, Capcom notifiedits users about updating the anti-hack driver (Capcom.sys), which is used to monitor the integrity of game files and prevents possible memory compromise of the game process in order to prevent cheating. However, users in this update had an unpleasant surprise in one of the driver functions. It allows you to disable the protective measure of the SMEP kernel and execute code according to the pointer obtained from user mode.
SMEP (Supervisor Mode Execution Prevention) is already a fairly well-known measure that has been written aboutsome reviews. It requires support both from the microprocessor and from the OS (Windows 8+). SMEP is used to block the user-mode code execution operation (Ring 3) in kernel mode (RIng 0). No matter how strange it looks (kernel mode code is the most privileged and has the ability to access all memory in the system), SMEP is a good measure to block the activity of LPE exploits, which often transfer control to a code block located in the user part of the virtual address space .
Windows drivers are organized in such a way that to interact with the client from Ring 3, a special interface is used called IOCTL. The driver registers a special handler in the Windows kernel, which can be used from user mode by the well-known API function DeviceIoControl . When using this API, the application passes the driver the code of the required function, the set of arguments, and indicates the input and output memory buffers for passing arguments and obtaining the result.
New Capcom.sys update usesIOCTL interface and two functions with codes 0xAA012044, 0xAA013044. The peculiarity of these functions is that they allow the user-mode client to execute code in kernel mode using the pointer received from there, and before that it disables SMEP. After the function is executed, the SMEP is switched back on by setting the corresponding bit of the CR4 register. Obviously, disabling is used to execute code in kernel mode from user mode.

Fig. Capcom.sys function that executes the function specified in the IOCTL request with SMEP disabled.
Obviously, since the driver of the computer game is digitally signed and provides such a potentially dangerous interface for access from user mode, it creates a backdoor in the system. Third-party code can use this driver to execute its code in Ring 0.
Capcom has already released a game update to close this vulnerability.
We are in the process of rolling back the security measures added to the PC version of Street Fighter V. After the rollback process to the PC version, all new content from the September update will still be available to players. We apologize for the inconvenience and will have an update on the time-frame for the PC rollback solution soon.
