New Android 7 Security Features
 Google has already released Android 7. In the near future, owners of various devices running Android will receive a firmware update. One of the first to receive the new version is users of branded devices Google Nexus 6P, 5X, 6, 9, Google Pixel C, Nexus Player, Android One. Since Google distributes Android updates in waves, not all users of these devices will be able to quickly receive the update. Android 7 will also be able to get the flagship device models of such vendors as Samsung (Galaxy S6 and S7), HTC (HTC 10, One A9 and One M9), Sony (Xperia Z3 +, Xperia Z4 Tablet, Xperia Z5, Xperia X), LG (V20 ), Huawei. The new version of Android has a number of serious new security features (security features), some of which we wrote in previous posts. The first was dedicatedDirect Boot, which makes it easier for device owners to work with encryption. The second contained information about the security improvements to the Linux kernel on which Android is based.
Google has already released Android 7. In the near future, owners of various devices running Android will receive a firmware update. One of the first to receive the new version is users of branded devices Google Nexus 6P, 5X, 6, 9, Google Pixel C, Nexus Player, Android One. Since Google distributes Android updates in waves, not all users of these devices will be able to quickly receive the update. Android 7 will also be able to get the flagship device models of such vendors as Samsung (Galaxy S6 and S7), HTC (HTC 10, One A9 and One M9), Sony (Xperia Z3 +, Xperia Z4 Tablet, Xperia Z5, Xperia X), LG (V20 ), Huawei. The new version of Android has a number of serious new security features (security features), some of which we wrote in previous posts. The first was dedicatedDirect Boot, which makes it easier for device owners to work with encryption. The second contained information about the security improvements to the Linux kernel on which Android is based.The Direct Boot function is responsible for the timely preparation of the execution of Android system files on an encrypted device. Since previous versions of Android used the Full Disc Encryption (FDE) encryption method, i.e., encrypting the entire device’s memory, the bootloader needed to know the device unlock code to decrypt the system files (Android uses the device unlock code as a component of the encryption key). In this scheme, the user had to enter the unlock code twice after rebooting the device: the first time to unlock the system files, and the second to unlock the device itself.
Direct Boot owes its implementation to the fact that Android 7 has switched from using FDE encryption to per-file encryption, i.e., each individual file. This encryption scheme has long been used in iOS.
Under the hood, file-based encryption enables this improved user experience. With this new encryption scheme, the system storage area, as well as each user profile storage area, are all encrypted separately. Unlike with full-disk encryption, where all data was encrypted as a single unit, per-profile-based encryption enables the system to reboot normally into a functional state using just device keys. Essential apps can opt-in to run in a limited state after reboot, and when you enter your lock screen credential, these apps then get access your user data to provide full functionality.
Source
Another security improvement concerns a notorious system service called MediaServer. This component works with elevated rights and is responsible for playing various multimedia content. Vulnerabilities in it were regularly closed in the Android security updates that we wrote about on the blog. A security feature called overflow sanitization helps close the whole class of Android vulnerabilities that were discovered in the libstagefright library. This library uses MediaServer. Another MediaServer security improvement concerns the operation of the entire multimedia stack of components, each of which is now in isolation from its own sandbox environment.
First, by incorporating integer overflow sanitization, part of Clang's Undefined Behavior Sanitizer, we prevent an entire class of vulnerabilities, which comprise the majority of reported libstagefright bugs. As soon as an integer overflow is detected, we shut down the process so an attack is stopped. Second, we've modularized the media stack to put different components into individual sandboxes and tightened the privileges of each sandbox to have the minimum privileges required to perform its job. With this containment technique, a compromise in many parts of the stack grants the attacker access to significantly fewer permissions and significantly reduced exposed kernel attack surface.
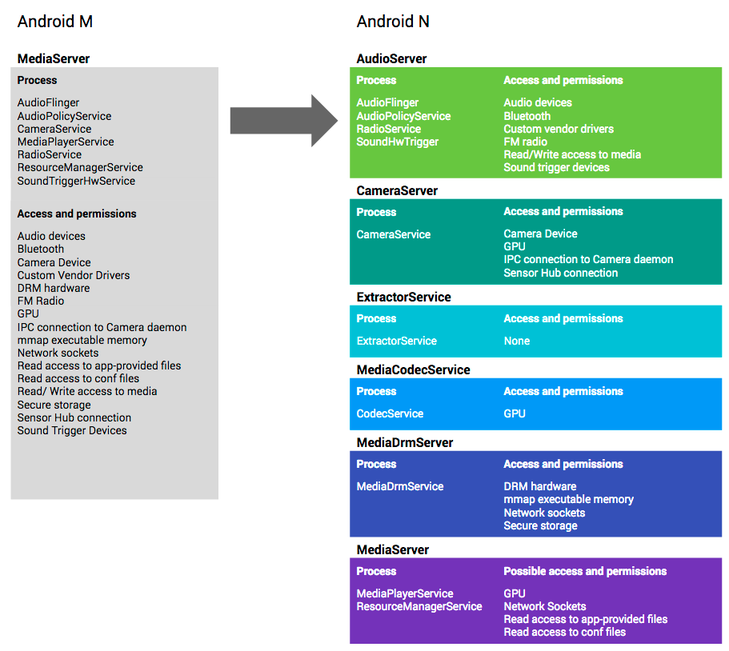
Fig. In Android 7, the MediaServer service is divided into various subsystems (multimedia stack) that work with limited rights and in a limited environment (sandbox). It can be seen that the new system of assigning rights to services is much more effective from the point of view of security, since it allows you to set the application only the rights it needs. In the new version, the libstagefright library functions in the MediaCodecService service, which has minimal system rights. Thus, exploitation of vulnerabilities in this component for Android 7 will not bring attackers any results.
The new Verified Boot function strictly controls the integrity of the bootloader, preventing the device from booting if it is compromised. The sandbox mechanism of the Linux kernel, known as seccomp, has also been improved.. In addition, SELinux security subsystem configuration settings have been improved . Both of these measures completely close the security mechanism of sandbox applications, as well as reduce the risk of successful exploitation of other attack methods used by exploits.
We wrote about security improvements to the Android kernel earlier. They include the implementation of DEP for kernel mode virtual memory (Kernel DEP), a function of type SMAP that allows you to block access to user virtual memory pages for kernel mode code. Several new features relate to the technique known as Attack Surface Reduction (ASR), it can significantly reduce the success of exploiting a whole class of vulnerabilities. As part of the ASR. Android 7 supports removing default debugging access for the device, and also prevents applications from using certain commands using the ioctl function .
The mechanism for updating Android 7 "over the air" (OTA update) has also become improved. Now the size of updates has become more compact, and installation time has been significantly reduced. The reduction in installation time is also due to the fact that the new version will not have the “application preparation” phase, which took the most time during the installation process of updates in previous versions of Android.

be secure.
