Conference DEFCON 16. How can I get hold of you? Let me list the ways. Part 2
- Transfer
Conference DEFCON 16. How can I get hold of you? Let me list the ways. Part 1
And now I will show you a video that explains why I hate Bluetooth headsets.
In the video, the girl is talking to a guy.
D: what are you doing tonight?
P: nothing!
D: do you want to go to the party with me?
P: Yes, I want to!
D: and before that we can come to me ...
P: it sounds amazing!
D: wait! (answers the phone)
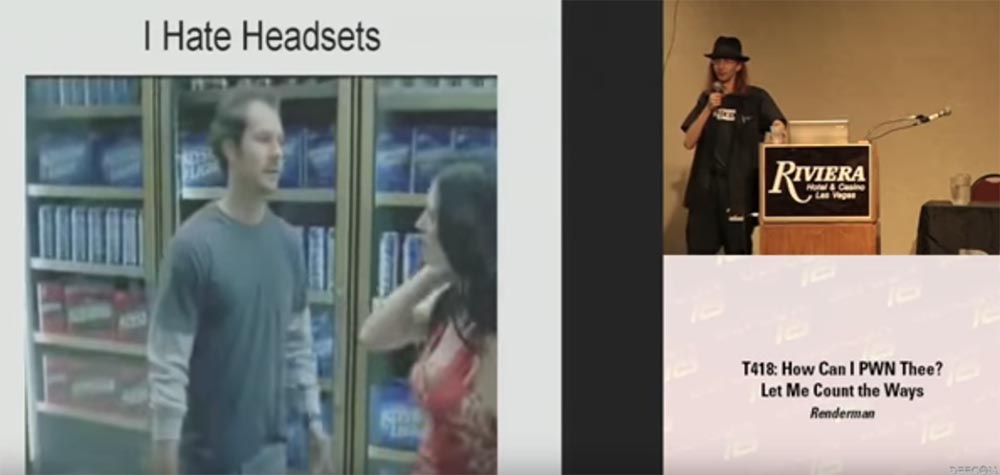
How many times have you had in your life when a phone call sounds at the most inopportune moment? That's why I don't hate these things.
So let's start a new section. I try to stay serious, although I called him "Taking Bob's Wife." Having rummaged well on Bob’s phone, we are making a discovery: there must be something inaccessible through a wireless connection on the phone, I think you will agree with that. These are special SMS messages with a header of 5 or 6 digits, after studying which, you come to the conclusion that they are addressed to Bob's wife.
Now we know the code, we know his wife's phone number ... who the hell thought that would be a good idea?

The inscription on the slide: "Toy." The inscription on the photo: "Just imagine ... a secret mischief that can be shared ... tease me, please excite, control ...".
And here is the “toy” itself - a Bluetooth vibrator! I warned that I was trying to stay serious. So, this is a vibrator that responds to special SMS messages when paired with a compatible phone. Each letter in the text causes a certain reaction of the vibrator, any symbol that you enter from the phone gives the vibrator a different movement. You can force the vibrator to perform hundreds of different movements in response to the characters you enter. This piece is produced by thetoy.co.uk.

But discarding the insinuations like “Penetration test”, “Hacking a device without a trojan”, “Extend a hand and touch”, “Do you hear me now?” Or “I can't wait until the site has a poll on this topic” to the side and try to be serious.
If you don’t even consider the teledildonics (technology of sex at a distance) to be a relevant area of research and start to google to find examples of such devices, I note that all of them also need to ensure security, but no one has done a security review of such devices. So attention, this is a new area of research (laughter in the audience)!
In any case, this bluetooth vibrator is a really bad idea of using wireless technology for completely stupid things. But there are serious consequences.
Would rape be considered if someone else sent these messages instead of Bob? “Dear, thank you for sending me this message 7-30! “But I did not send you any message!” This may cause a trial in the near future, and if this happens, it will cause many questions to anyone.
Another question: can non-printing characters lead to potentially dangerous actions of this device? Well, for example, it starts to behave incorrectly or gets stuck ...
It sounds ridiculous, but it is serious enough, because theoretically with the help of such a vibrator you can hurt someone. “To hurt someone with an SMS” sounds awful enough.
I will answer the question - I do not have such a device, my wife helps me with a lot of different projects, but does not want to participate in such research. But if someone doesn't mind 300 bucks, he can buy this thing, bring it to DefCon next year, put it on the table and give people the opportunity to do something with it. Present the announcement of the presentation: “Next weekend, you will be shown a bluetooth vibrator hacking!”
Consider how to prevent the threat of using Bluetooth:

Now let's talk about the keys of Bob. He has a pass card to enter the office. She is tied to his badge - ID. He wears it without removing it all the time. You’ve seen Johnny Long’s low-tech hacking presentation, this is a really good story about hacking without the use of technology. He talked about how easy it is to take photographs of the identity cards of people who hang out on their laces, and then he makes his own card with his photo.
Cards-passes of the new model are encrypted, but most of the passes used are not encrypted. The device asks for the number, you provide it, and the system lets you inside. There is a special program cq.cx for cloning proxy cards, and you can make your own map for further use for your own purposes. Jonathan developed this wonderful device, version 1 is shown on the slide, but, in my opinion, there is a 3rd version.

You simply press a button on the map, it reads the code, press another button, and it gives the read information. So I just go up to the CEO or another person who has access to the whole building, for example, to the cleaner, and say: “hey, how are you? You really do a great job with your work! ”And shake hands with him. During this time, you are copying his card, and now the CEO must explain why he was looking at research and development data and confidential files at 3 am, because all audit logs will point to his own electronic key, which is still in his pocket. .
Traditional mechanical keys are also vulnerable. If you wear them in a bundle on a belt, they hang out there and ring, they can also be photographed. Then you can view all the grooves and grooves, and then purchase an exact duplicate of such a key through the Diebold online store. Even on this small photo you can see all the details of the key. It is a common practice when an office orders all the equipment, cabinets, drawers, mini-bars from the same manufacturer, and the same keys are used everywhere.
In this small video, you see how the key that one guy took during an equipment audit at a university perfectly opens the lock on his home mini-bar. The next day, he returned with another key, click - and everything was ready, the lock opened. Such is democracy!
Consider Bob's passport. RFID tags in the passports of the new sample can be read very easily. How many of you have such a new passport with this little shiny label on the cover? A few people, alright. Encryption of these tags is not too serious.

Each country has its own rules for controlling such passports, but it usually happens that you come to the border guard, he passes your passport through a device that reads the string under your photo. This provides the information they need to generate a key that allows you to unlock and download the content of the RFID tag. It contains quite a lot of information, for example, your date of birth. There is a fairly limited place to place the key, especially if you know your goal, that is, where the date of birth is located approximately and the sequence of other data in this line. So you can try to guess the key, knowing where it is located approximately.
Not only in the United States, but also in other countries, people are able to crack these tags literally with the help of an envelope that is mailed, simply based on data written outside the envelope, and information to Google.
In the United States, when an e-tagged passport was identified, people were asked to comment on this situation, and the result was interesting: about 2,000 comments said that it was a bad idea, and only 2 people wrote that it was a good idea. The solution that was offered to calm these disappointed people was to use a thin layer of foil. They were going to literally build a protective “foil cap” for the passport, that is, to place foil liners on the front and back of the cover to prevent unauthorized reading of the RFID tag until the passport was opened and presented for control.
This small video shows what happens with such a passport - you are trying to close it, but it springs up and opens again. This disclosure of about 1 inch is enough to read these tags - you can see the numbers appearing on the monitor screen. So a passport with foil liners is not able to protect itself from being read, especially if it is in a free pocket or a wide wallet.
From the audience here they suggest that you can use a condom for a passport - perhaps this is a good idea to protect it.
This vulnerability was most well demonstrated in the UK this Wednesday — they were able to clone a chip from an English passport, put it in another passport, and went through border control with this passport. And this passport was recognized as authentic. So it’s easy to replace a child's photo in a passport with a photo of Bin Laden and it will work.
Such dangers have not arisen today, I have been talking about them for a couple of years, but people do not understand this. I believe that it is necessary to teach the rules of safety of sellers who travel abroad. Now one of the most common fears is that if you are American and travel abroad and you have an American passport, they will steal it from you. If someone clones your passport and before you return to the country, then you and your current passport will be delayed when you return to your homeland and probably will not believe that you have nothing to do with it, because someone has cloned your passport.
Bob has different responsibilities. He works at trade fairs and presents his products, because the success of his work directly depends on how profitable he is to demonstrate the functionality of his widgets to a potential buyer. He tells how neat, shiny and how much they can do.
But what happens if your widgets start executing unauthorized unencrypted commands?
You know, I was a little upset when I saw the icons with the image of the guns of TV-B-Gone here in Vegas. This video shows Gizmodo speaking at a CES 2008 conference last January, and I do not advise trying to repeat this extreme example at home.
The video shows how in the halls of the conference all monitors located on the walls, in the hall, at the reception are turned off, the image disappears and they go out. The following shows how monitors are remotely turned off, on which performances are shown and a presentation is made.
Last January, the MakeMagazine portal provided the guys at CES with a bunch of TV-B-Gone pistols that could remotely and quietly turn off any television receiver. We can only regret these guys from Motorola, whose performance was interrupted in a similar way. Such a gun can ruin any presentation by simply not allowing our Bob to demonstrate his product.


I do not admire people who are doing such things, because these unfortunate guys are sitting there, showing off their goods, trying to earn a living. So it's not at all cool to deprive them of work in this way. But the wall of screens - it looked cool!
I mean, you don't have to be a complete jerk when you demonstrate hacker devices, just to get attention.
A couple of years ago at the Shmoocon conference, I found myself in an interesting position. They sold USB hubs, they had LEDs inside, and they lit up when they connected the hubs to a computer.

The sellers had a whole bunch of such devices, they connected them to each other in the form of "daisies" and wanted to show how they all sparkle, so they needed to connect them to some kind of computer. There was a demo notebook on which the password stood. I will tell you that the hacker this time was in the right place, at the right time and with the right tool. I missed waiting for registration and just stood next to these guys. I fished out a USB flash drive from my pocket and told these guys: “Look what I have with me!”. They inserted it into a laptop, pulled it out, inserted it again — it was useless. I said that I do not remember all the passwords by heart, but I will try to do something.
I did not want to do this imperceptibly, I wanted to attract more attention. I decided, like a complete moron, to publicly crack passwords, and I ran a script that scrolled through a projector that was standing next to the table and transmitting the image to the big screen behind us. Then I got up on a chair and made an announcement, they say, ladies and gentlemen, you are at a security conference, this means ensuring security not only for network ports, but also for USB ports, and went on to explain what I just did.
The most interesting was the fact that there was a woman who worked at one of the stands. It was a new job for her, and there was another guy with her who was out for lunch at that time. It turns out that before the start of the action he explained all day to her that this is a hacker conference, there are a lot of hackers here, so you don’t need to connect anything that requires you to enter your password, be very careful with these guys, because it’s unknown who is watching and listening. Therefore, she behaved like a paranoid in relation to her laptop and did not do anything, except for checking e-mail, any actions requiring the transfer of a password. As it turned out, I was showing my “work” on this particular guy’s laptop. When he returned from dinner, this woman began to convince him that she did not reveal any passwords, and I had to prove that I did it myself.
So, we proved that Bob was completely "fucked":
Do you have any suggestions? I know that now Blackberry is becoming more and more popular - a platform for mobile devices with enhanced security. Its developers have done a solid job of maintaining the relative security of Bluetooth devices in their own network.
How many of you have seen people turn into heaps of seething mucus on the floor during large outages or similar failures trying to access email through their Blackberry devices? Unfortunately, people are becoming increasingly dependent on technology.
I wonder what you are doing to teach your staff and responsible people mobile security rules, what are you doing to teach them to keep their devices safe? What are you doing to help them learn to help themselves?
It may be worth considering the use of wireless microphones for presentations or broadband jammers that can suppress unwanted digital communications and control signals — GSM, Wi-Fi and Bluetooth. It is possible that such devices will provide some confidentiality of communication.
As I have already said, people use wireless communication where it cannot be used, for example, in medical equipment, and this is scary.
If you have any questions, send me an email at render@renderlab.net. Thank you so much Robert T Firefly from New York for the illustrations of Bob. I suggest you also buy WPA cracking kits, 9 DVDs, they cost 50 bucks each. So I can recoup my expenses for a trip here, and besides, I don’t want to drag them back home.
Thank you so much!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
And now I will show you a video that explains why I hate Bluetooth headsets.
In the video, the girl is talking to a guy.
D: what are you doing tonight?
P: nothing!
D: do you want to go to the party with me?
P: Yes, I want to!
D: and before that we can come to me ...
P: it sounds amazing!
D: wait! (answers the phone)

How many times have you had in your life when a phone call sounds at the most inopportune moment? That's why I don't hate these things.
So let's start a new section. I try to stay serious, although I called him "Taking Bob's Wife." Having rummaged well on Bob’s phone, we are making a discovery: there must be something inaccessible through a wireless connection on the phone, I think you will agree with that. These are special SMS messages with a header of 5 or 6 digits, after studying which, you come to the conclusion that they are addressed to Bob's wife.
Now we know the code, we know his wife's phone number ... who the hell thought that would be a good idea?

The inscription on the slide: "Toy." The inscription on the photo: "Just imagine ... a secret mischief that can be shared ... tease me, please excite, control ...".
And here is the “toy” itself - a Bluetooth vibrator! I warned that I was trying to stay serious. So, this is a vibrator that responds to special SMS messages when paired with a compatible phone. Each letter in the text causes a certain reaction of the vibrator, any symbol that you enter from the phone gives the vibrator a different movement. You can force the vibrator to perform hundreds of different movements in response to the characters you enter. This piece is produced by thetoy.co.uk.

But discarding the insinuations like “Penetration test”, “Hacking a device without a trojan”, “Extend a hand and touch”, “Do you hear me now?” Or “I can't wait until the site has a poll on this topic” to the side and try to be serious.
If you don’t even consider the teledildonics (technology of sex at a distance) to be a relevant area of research and start to google to find examples of such devices, I note that all of them also need to ensure security, but no one has done a security review of such devices. So attention, this is a new area of research (laughter in the audience)!
In any case, this bluetooth vibrator is a really bad idea of using wireless technology for completely stupid things. But there are serious consequences.
Would rape be considered if someone else sent these messages instead of Bob? “Dear, thank you for sending me this message 7-30! “But I did not send you any message!” This may cause a trial in the near future, and if this happens, it will cause many questions to anyone.

Another question: can non-printing characters lead to potentially dangerous actions of this device? Well, for example, it starts to behave incorrectly or gets stuck ...
It sounds ridiculous, but it is serious enough, because theoretically with the help of such a vibrator you can hurt someone. “To hurt someone with an SMS” sounds awful enough.
I will answer the question - I do not have such a device, my wife helps me with a lot of different projects, but does not want to participate in such research. But if someone doesn't mind 300 bucks, he can buy this thing, bring it to DefCon next year, put it on the table and give people the opportunity to do something with it. Present the announcement of the presentation: “Next weekend, you will be shown a bluetooth vibrator hacking!”
Consider how to prevent the threat of using Bluetooth:
- Turn off the bluetooth itself or at least the automatic search mode for the device to connect. It saves a great battery, because my phone works without recharging for 8 hours, and if you turn off the bluetooth, it will work for several days;
- change the default pin code. Some models of headsets can be connected to a computer via USB and using a small program to change the pin code;
- if possible, limit the number of simultaneously connected devices,
use prompts to determine the name of the device you are connecting to. - If your phone asks for permission to pair with some device, do not automatically agree, but check every request;
- unplug the headset if you are not using it. So you will get rid of this stupid blue light that hurts the eyes;
- Consider ensuring the safety of your devices and assess the consequences of using bluetooth, remember a hacker who is bored and who wants to hack you.

Now let's talk about the keys of Bob. He has a pass card to enter the office. She is tied to his badge - ID. He wears it without removing it all the time. You’ve seen Johnny Long’s low-tech hacking presentation, this is a really good story about hacking without the use of technology. He talked about how easy it is to take photographs of the identity cards of people who hang out on their laces, and then he makes his own card with his photo.
Cards-passes of the new model are encrypted, but most of the passes used are not encrypted. The device asks for the number, you provide it, and the system lets you inside. There is a special program cq.cx for cloning proxy cards, and you can make your own map for further use for your own purposes. Jonathan developed this wonderful device, version 1 is shown on the slide, but, in my opinion, there is a 3rd version.

You simply press a button on the map, it reads the code, press another button, and it gives the read information. So I just go up to the CEO or another person who has access to the whole building, for example, to the cleaner, and say: “hey, how are you? You really do a great job with your work! ”And shake hands with him. During this time, you are copying his card, and now the CEO must explain why he was looking at research and development data and confidential files at 3 am, because all audit logs will point to his own electronic key, which is still in his pocket. .
Traditional mechanical keys are also vulnerable. If you wear them in a bundle on a belt, they hang out there and ring, they can also be photographed. Then you can view all the grooves and grooves, and then purchase an exact duplicate of such a key through the Diebold online store. Even on this small photo you can see all the details of the key. It is a common practice when an office orders all the equipment, cabinets, drawers, mini-bars from the same manufacturer, and the same keys are used everywhere.
In this small video, you see how the key that one guy took during an equipment audit at a university perfectly opens the lock on his home mini-bar. The next day, he returned with another key, click - and everything was ready, the lock opened. Such is democracy!
Consider Bob's passport. RFID tags in the passports of the new sample can be read very easily. How many of you have such a new passport with this little shiny label on the cover? A few people, alright. Encryption of these tags is not too serious.

Each country has its own rules for controlling such passports, but it usually happens that you come to the border guard, he passes your passport through a device that reads the string under your photo. This provides the information they need to generate a key that allows you to unlock and download the content of the RFID tag. It contains quite a lot of information, for example, your date of birth. There is a fairly limited place to place the key, especially if you know your goal, that is, where the date of birth is located approximately and the sequence of other data in this line. So you can try to guess the key, knowing where it is located approximately.
Not only in the United States, but also in other countries, people are able to crack these tags literally with the help of an envelope that is mailed, simply based on data written outside the envelope, and information to Google.
In the United States, when an e-tagged passport was identified, people were asked to comment on this situation, and the result was interesting: about 2,000 comments said that it was a bad idea, and only 2 people wrote that it was a good idea. The solution that was offered to calm these disappointed people was to use a thin layer of foil. They were going to literally build a protective “foil cap” for the passport, that is, to place foil liners on the front and back of the cover to prevent unauthorized reading of the RFID tag until the passport was opened and presented for control.
This small video shows what happens with such a passport - you are trying to close it, but it springs up and opens again. This disclosure of about 1 inch is enough to read these tags - you can see the numbers appearing on the monitor screen. So a passport with foil liners is not able to protect itself from being read, especially if it is in a free pocket or a wide wallet.
From the audience here they suggest that you can use a condom for a passport - perhaps this is a good idea to protect it.
This vulnerability was most well demonstrated in the UK this Wednesday — they were able to clone a chip from an English passport, put it in another passport, and went through border control with this passport. And this passport was recognized as authentic. So it’s easy to replace a child's photo in a passport with a photo of Bin Laden and it will work.
Such dangers have not arisen today, I have been talking about them for a couple of years, but people do not understand this. I believe that it is necessary to teach the rules of safety of sellers who travel abroad. Now one of the most common fears is that if you are American and travel abroad and you have an American passport, they will steal it from you. If someone clones your passport and before you return to the country, then you and your current passport will be delayed when you return to your homeland and probably will not believe that you have nothing to do with it, because someone has cloned your passport.
Bob has different responsibilities. He works at trade fairs and presents his products, because the success of his work directly depends on how profitable he is to demonstrate the functionality of his widgets to a potential buyer. He tells how neat, shiny and how much they can do.

But what happens if your widgets start executing unauthorized unencrypted commands?
You know, I was a little upset when I saw the icons with the image of the guns of TV-B-Gone here in Vegas. This video shows Gizmodo speaking at a CES 2008 conference last January, and I do not advise trying to repeat this extreme example at home.
The video shows how in the halls of the conference all monitors located on the walls, in the hall, at the reception are turned off, the image disappears and they go out. The following shows how monitors are remotely turned off, on which performances are shown and a presentation is made.
Last January, the MakeMagazine portal provided the guys at CES with a bunch of TV-B-Gone pistols that could remotely and quietly turn off any television receiver. We can only regret these guys from Motorola, whose performance was interrupted in a similar way. Such a gun can ruin any presentation by simply not allowing our Bob to demonstrate his product.



I do not admire people who are doing such things, because these unfortunate guys are sitting there, showing off their goods, trying to earn a living. So it's not at all cool to deprive them of work in this way. But the wall of screens - it looked cool!
I mean, you don't have to be a complete jerk when you demonstrate hacker devices, just to get attention.
A couple of years ago at the Shmoocon conference, I found myself in an interesting position. They sold USB hubs, they had LEDs inside, and they lit up when they connected the hubs to a computer.

The sellers had a whole bunch of such devices, they connected them to each other in the form of "daisies" and wanted to show how they all sparkle, so they needed to connect them to some kind of computer. There was a demo notebook on which the password stood. I will tell you that the hacker this time was in the right place, at the right time and with the right tool. I missed waiting for registration and just stood next to these guys. I fished out a USB flash drive from my pocket and told these guys: “Look what I have with me!”. They inserted it into a laptop, pulled it out, inserted it again — it was useless. I said that I do not remember all the passwords by heart, but I will try to do something.
I did not want to do this imperceptibly, I wanted to attract more attention. I decided, like a complete moron, to publicly crack passwords, and I ran a script that scrolled through a projector that was standing next to the table and transmitting the image to the big screen behind us. Then I got up on a chair and made an announcement, they say, ladies and gentlemen, you are at a security conference, this means ensuring security not only for network ports, but also for USB ports, and went on to explain what I just did.
The most interesting was the fact that there was a woman who worked at one of the stands. It was a new job for her, and there was another guy with her who was out for lunch at that time. It turns out that before the start of the action he explained all day to her that this is a hacker conference, there are a lot of hackers here, so you don’t need to connect anything that requires you to enter your password, be very careful with these guys, because it’s unknown who is watching and listening. Therefore, she behaved like a paranoid in relation to her laptop and did not do anything, except for checking e-mail, any actions requiring the transfer of a password. As it turned out, I was showing my “work” on this particular guy’s laptop. When he returned from dinner, this woman began to convince him that she did not reveal any passwords, and I had to prove that I did it myself.
So, we proved that Bob was completely "fucked":
- took possession of his laptop;
- took possession of his data;
- took possession of his cell phone;
- took possession of his wife!
- took possession of his keys;
- seized his presentation materials;
- seized his ability to work.
Do you have any suggestions? I know that now Blackberry is becoming more and more popular - a platform for mobile devices with enhanced security. Its developers have done a solid job of maintaining the relative security of Bluetooth devices in their own network.
How many of you have seen people turn into heaps of seething mucus on the floor during large outages or similar failures trying to access email through their Blackberry devices? Unfortunately, people are becoming increasingly dependent on technology.
I wonder what you are doing to teach your staff and responsible people mobile security rules, what are you doing to teach them to keep their devices safe? What are you doing to help them learn to help themselves?
It may be worth considering the use of wireless microphones for presentations or broadband jammers that can suppress unwanted digital communications and control signals — GSM, Wi-Fi and Bluetooth. It is possible that such devices will provide some confidentiality of communication.
As I have already said, people use wireless communication where it cannot be used, for example, in medical equipment, and this is scary.
If you have any questions, send me an email at render@renderlab.net. Thank you so much Robert T Firefly from New York for the illustrations of Bob. I suggest you also buy WPA cracking kits, 9 DVDs, they cost 50 bucks each. So I can recoup my expenses for a trip here, and besides, I don’t want to drag them back home.
Thank you so much!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
