Industrial Management Systems 2016: Vulnerability and Accessibility

Automated process control systems (ACS TP, ICS) are used everywhere today - from smart homes to nuclear power plants. However, the complex organization of such systems, the requirement of process continuity, and the ability to access process control systems via the universal Internet make them easily vulnerable to hacker attacks.
At the same time, the number of vulnerable ICS components does not decrease from year to year. Almost half of the vulnerabilities identified in 2015 have a high degree of risk, with the largest number of vulnerabilities found in the products of the most famous manufacturers. In particular, ACS TP everywhere uses dictionary passwords and default passwords, which makes it easy to access them and take control.
Such findings are contained in Positive Technologies' research, which analyzes data on the vulnerabilities of ICS for the period from 2012 to 2015, as well as data on the availability of ICS components via the Internet in 2015. Below are the main results of this study.
Research Methodology
The study was based on information from publicly available sources, such as vulnerability knowledge bases (ICS-CERT, NVD, CVE, Siemens Product CERT, Positive Research Center), manufacturer notifications, exploit collections, reports of scientific conferences, publications on specialized websites and on blogs. We determined the degree of risk of vulnerability of ICS components based on the CVSS value of the second version.
Data collection on the availability of ICS components on the Internet was carried out by scanning the ports of resources available on the Internet using public search engines: Google, Shodan, Censys. After collecting the data, an additional analysis was carried out for the relationship with the industrial control system. Positive Technologies experts have compiled a database of process control identifiers, consisting of approximately 800 entries, which allows us to make a conclusion on the basis of the banner about the product used and its manufacturer.
results
The study examined the vulnerabilities of components of about 500 manufacturers of automated control systems. As a result, 743 vulnerabilities were identified in the ICS. In 2015, Positive Technologies experts independently discovered 7 new vulnerabilities (two of them have a high degree of risk), detailed information about which was sent to the manufacturer.
Recall that according to our previous study, “ Industrial Systems Safety in Figures”, From 2009 to 2012, the number of detected vulnerabilities in ICS increased by 20 times (from 9 to 192). In recent years (2012–2015), the number of vulnerabilities detected annually remains stable (about 200). This can be explained by the increased interest of equipment manufacturers in the timely identification and elimination of vulnerabilities and interaction with researchers.
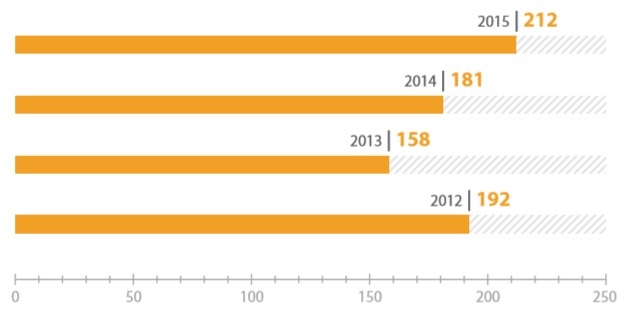
The total number of vulnerabilities detected in ICS components.
The leaders in the rating of the most vulnerable ICS components are Siemens, Schneider Electric and Advantech. However, the number of vulnerabilities detected depends on the prevalence of the product and on whether the manufacturer adheres to a responsible disclosure policy. As a result, this rating does not directly indicate the security of specific decisions of a particular manufacturer.
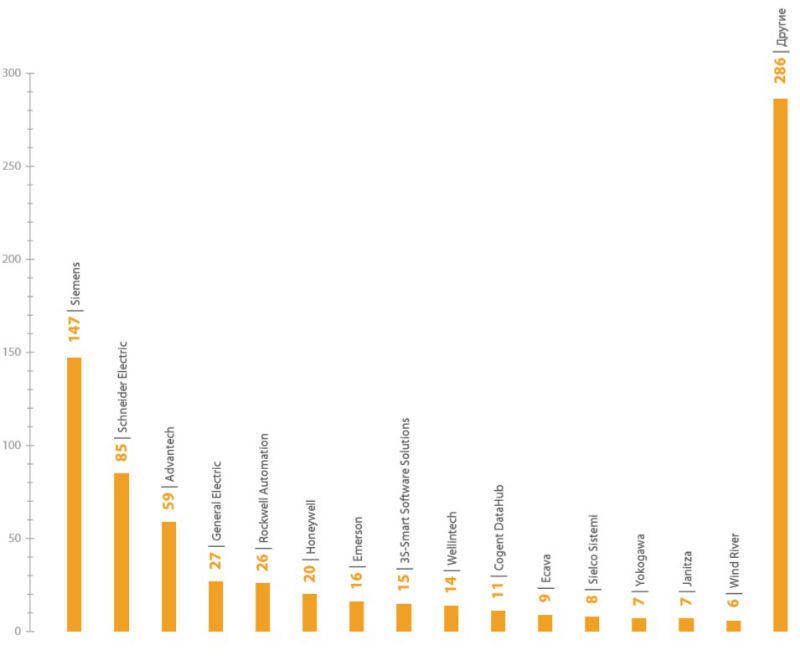
The number of vulnerabilities in ICS components of various manufacturers
The largest number of vulnerabilities were detected in SCADA components and programmable logic controllers , industrial network devices and engineering software, as well as in components of human-machine interfaces and remote access and control terminals, which corresponds to the previous report for 2012.
The main share of vulnerabilities is high and medium (47% each)degree of risk. At the same time, if we evaluate the level of vulnerability of vulnerabilities based on the possibility of realizing the main threats to information security (violation of confidentiality, integrity and availability), then more than half of the identified vulnerabilities have a high metric for such an important indicator as violation of accessibility . Together with the possibility of remote exploitation of vulnerabilities and weak authentication mechanisms, this significantly increases the risk of attacks on automated process control systems.
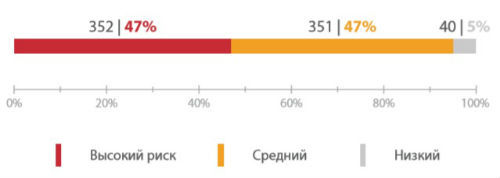
Distribution of vulnerabilities by risk
Since data on the process of eliminating vulnerabilities are not published, the study used data obtained by Positive Technologies experts directly from manufacturers. Detailed information on identified vulnerabilities that have already been fixed by manufacturers is presented on the company's website . According to 2015 data, only 14% of vulnerabilities were fixed within three months , 34% were eliminated for more than three months, and the remaining 52% of errors were either not fixed at all, or the manufacturer did not report the time of elimination.
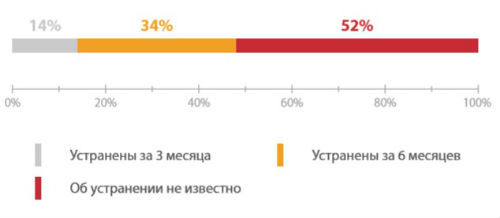
Percentage of fixed vulnerabilities in ICS components
However, only 5% of known vulnerabilities currently have published exploits. This indicator significantly decreased compared to 2012: then it was possible to find exploits for 35% of vulnerabilities.
The largest number of vulnerabilities relate to such types as denial of service ( DoS ), remote code execution ( Code Execution ) and buffer overflow ( Overflow ). The exploitation of such vulnerabilities by an attacker can lead to a failure in the operation of any equipment or to its unauthorized operation, which, given the requirements for the regular operation of automated process control systems, is unacceptable.
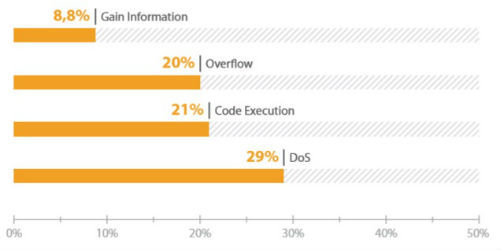
Common types of components vulnerabilities APCS
As of March 2016 found 158,087ICS components available on the Internet. The largest number of ICS components is available via HTTP, Fox, Modbus and BACnet , and in most cases a dictionary password is used for authorization in such systems.
The largest number of ICS components available was found in the USA (43%), Germany (12%), France, Italy and Canada (about 5% each). The low number of process control systems found in Asia is associated with the use of local and little-known solutions on the world market. Russia ranks 31st with 600 available components (this is less than 1% of the total number of components found).

The number of ICS components available on the Internet (by country)
By the prevalence of ICS components, Honeywell companies are leaders (17%) ,SMA Solar Technology (11%) , Beck IPC (7%) . The most common components on the Internet are building automation systems from Tridium (25,264) , part of the Honeywell group of companies, as well as energy monitoring and control systems, including those based on solar technology from SMA Solar Technology (17,275) .
The study also found automated systems that control the production processes of various enterprises, transport and water supply. In many cases, an attacker does not need to have any special knowledge in order to gain access to them: among the ICS components found on the Internet, only two-thirds canconditionally called protected .
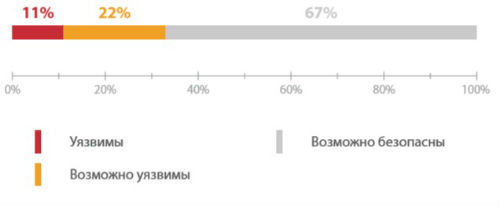
The proportion of vulnerable and safe ICS components available via the Internet
The data obtained indicate the absence of adequate protection for ICS from cyber attacks in 2016. Even minimal preventive measures, such as using complex passwords and disconnecting ICS components from the Internet, will significantly reduce the likelihood of attacks carrying significant consequences.
The full text of the research “ ICS Safety in Figures - 2016” can be found at www.ptsecurity.ru/research/analytics
