We add an arbitrary phone in the personal account of the mobile operator Kyivstar (Ukraine)
I am a client of the Ukrainian mobile operator Kyivstar and a user of their web service my.kyivstar.ua . Like many other operators, Kyivstar offers a web version of your personal account, where you can view your account balance, call details, change the tariff, order or deactivate the service, etc.
They also recently launched a new version of their new account, new.kyivstar.ua . An interesting function appeared in it - adding another Kyivstar phone via SMS verification. I undertook to check it for vulnerabilities, since it actually gave the same access to the added phone as to my own, which did not make me very happy as a client.
The new site has the following interface for adding a phone:

Adding is done in 4 steps:
Entering a phone number

Selecting via SMS by joining (and sometimes even through the static password, but I do not see it)
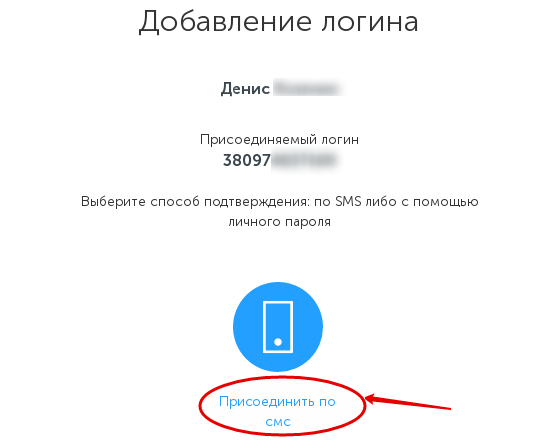
input received SMS.
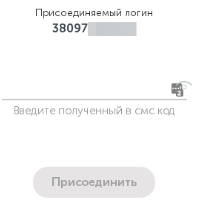
The confirmation.
These 4 steps are converted to a series of POST and GET requests. The last three queries in this series are responsible for adding the number after the passed OTP verification.
And I decided to check: what if you repeat these requests without those that are responsible for SMS verification.
Let us consider in more detail these last 3 queries.
They have the following appearance in the Google Chrome developer tool (Shift + Ctrl + I):
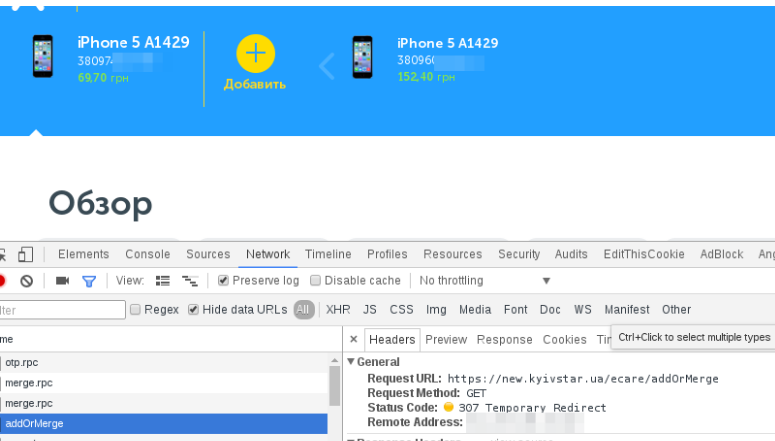
Merge.rpc requests are sent to account.kyivstar.ua/cas/merge/merge.rpc .
The contents of the first request:
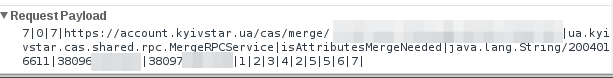
The request contains the number of the telephone to be added (097 ...) The
contents of the second request:
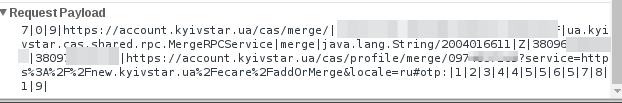
The third request to the address new.kyivstar.ua/ecare/addOrMerge is a GET request without parameters, confirming the previous two operations.
Next, I decided to replay these 3 requests, having previously deleted the phone I just added from my personal account.
For playback, I used the Postman application.
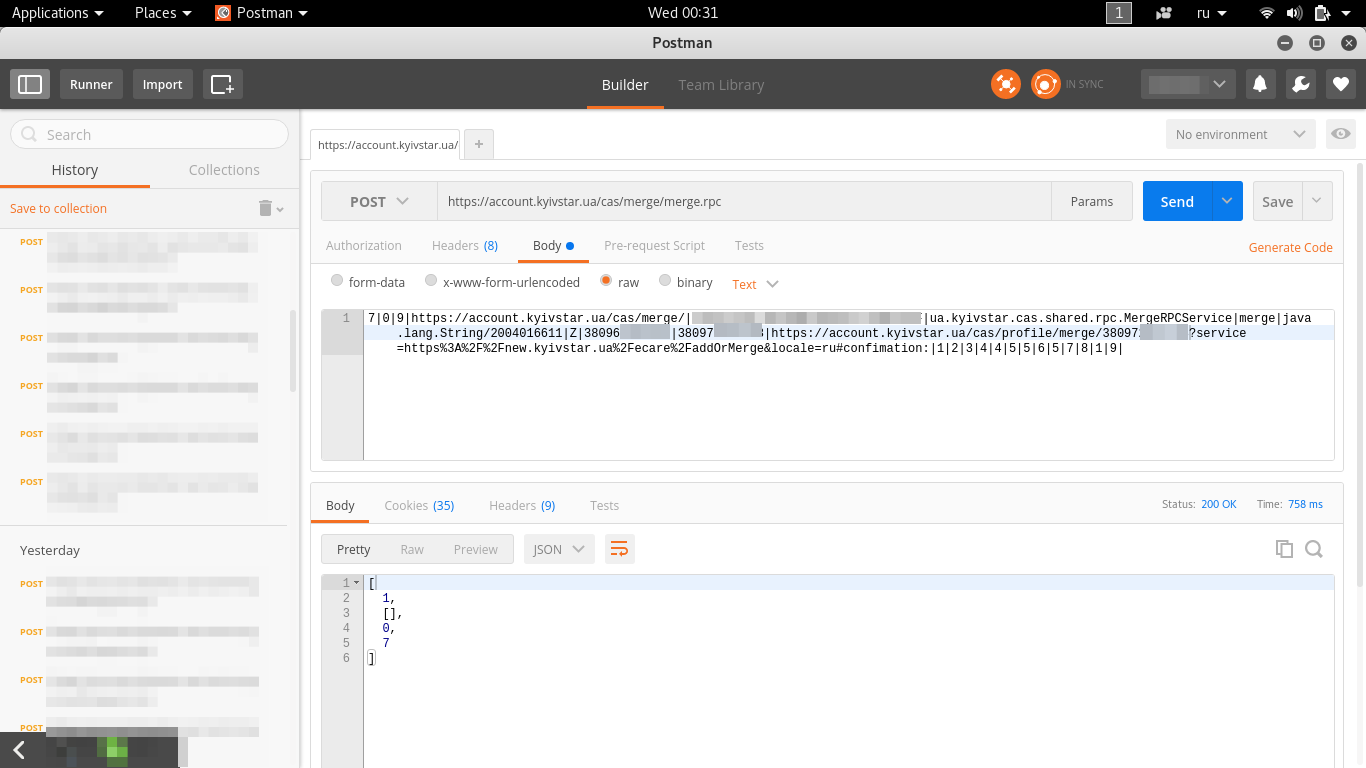
As expected, after updating the page, the phone was successfully added to your personal account.
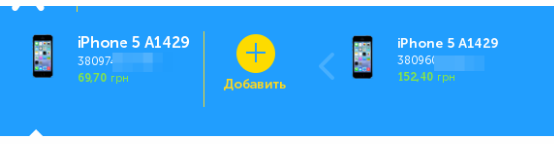
What we have.
We can add any phone number to our personal account without SMS verification and manage it as ours, namely:
You can’t imagine a better gift for scammers.
As expected, I immediately contacted Kyivstar customer support and asked for security contacts or a responsible employee of the development department to provide me with a detailed description of the essence of the vulnerability and how to reproduce it. As expected, I was refused my request and offered to send a description of the vulnerability either in chat, or through a universal form on the site.
Understanding what risks are possible if a detailed description of the vulnerability is available to any customer support employee, I still insisted on my request, but again without success. Realizing that there is no other way out, I issued detailed instructions for reproducing the vulnerability in a Google Docs file, wrapped it in a link through the clickmeter.com link tracking serviceand sent to the chat.
As I expected, my application caused a stir and increased interest among company employees, which was displayed in the analytics service clickmeter.com:
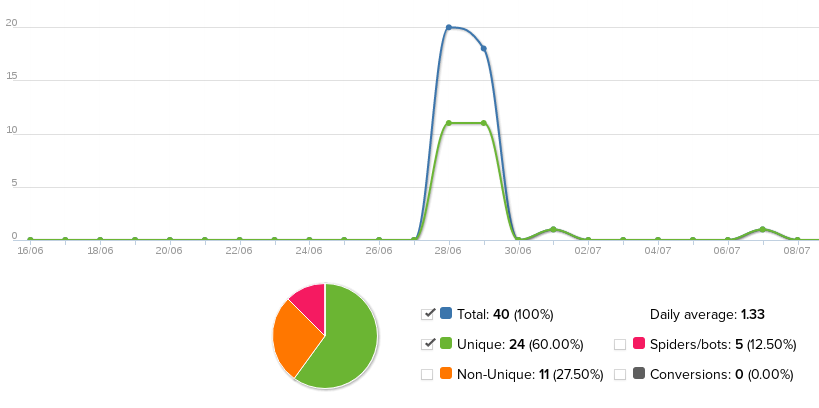
Application for 2 days was viewed by 22 unique users.
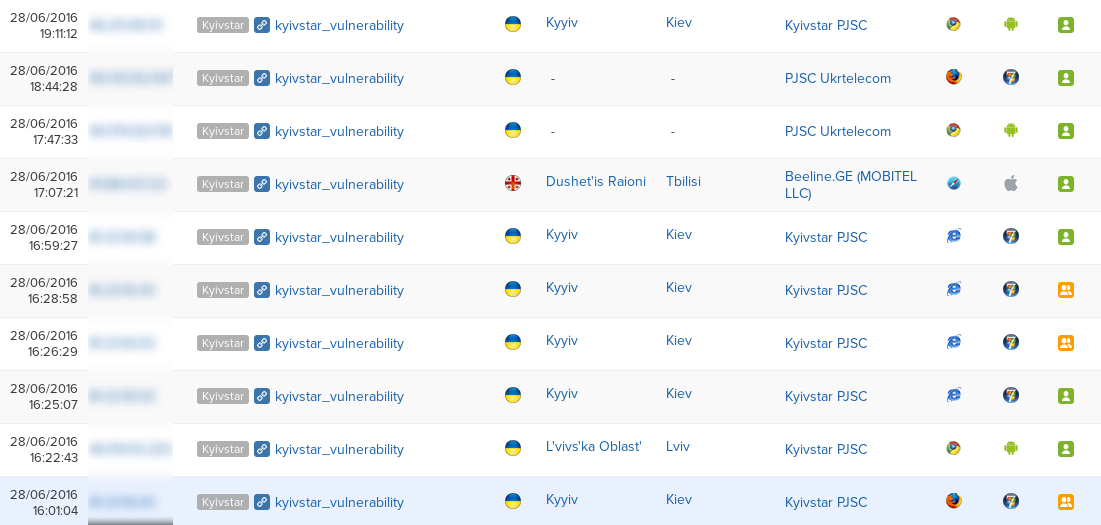
According to statistics, you can see that the link was viewed both from computers and from mobile devices. The geography of views was also not limited to the Kiev office, in the list Kiev, Lviv, Dnepropetrovsk, Tbilisi.
Analyzing the statistics, it becomes clear that the existing communication channel with the company is not intended for filing applications of this kind and can lead to information leakage and exploitation by third parties until the vulnerability is closed.
It is worth paying tribute to the company, the responsible employee contacted me on the second day, thanked and asked to remove the link from the public. Over the next few weeks, the vulnerability was closed, and I was contacted again and informed that the application was completed.
This story reminds us that we need to be more careful about information security issues in companies of such a scale as Kyivstar, create separate communication channels for this, access to which will be available only to authorized employees. Well, as well as the company's participation in bug-bounty programs or the creation of its own also has a positive effect on strengthening the security of services.
They also recently launched a new version of their new account, new.kyivstar.ua . An interesting function appeared in it - adding another Kyivstar phone via SMS verification. I undertook to check it for vulnerabilities, since it actually gave the same access to the added phone as to my own, which did not make me very happy as a client.
The new site has the following interface for adding a phone:

Adding is done in 4 steps:
Entering a phone number

Selecting via SMS by joining (and sometimes even through the static password, but I do not see it)

input received SMS.

The confirmation.
These 4 steps are converted to a series of POST and GET requests. The last three queries in this series are responsible for adding the number after the passed OTP verification.
And I decided to check: what if you repeat these requests without those that are responsible for SMS verification.
Let us consider in more detail these last 3 queries.
They have the following appearance in the Google Chrome developer tool (Shift + Ctrl + I):

Merge.rpc requests are sent to account.kyivstar.ua/cas/merge/merge.rpc .
The contents of the first request:

The request contains the number of the telephone to be added (097 ...) The
contents of the second request:

The third request to the address new.kyivstar.ua/ecare/addOrMerge is a GET request without parameters, confirming the previous two operations.
Next, I decided to replay these 3 requests, having previously deleted the phone I just added from my personal account.
For playback, I used the Postman application.

As expected, after updating the page, the phone was successfully added to your personal account.

What we have.
We can add any phone number to our personal account without SMS verification and manage it as ours, namely:
- view balance and call details
- view the PUK1 code and the serial number of the SIM card, which allows you to replace the SIM card yourself
- add new services and change the tariff plan
- and most importantly - transfer money from phone to phone
You can’t imagine a better gift for scammers.
As expected, I immediately contacted Kyivstar customer support and asked for security contacts or a responsible employee of the development department to provide me with a detailed description of the essence of the vulnerability and how to reproduce it. As expected, I was refused my request and offered to send a description of the vulnerability either in chat, or through a universal form on the site.
Understanding what risks are possible if a detailed description of the vulnerability is available to any customer support employee, I still insisted on my request, but again without success. Realizing that there is no other way out, I issued detailed instructions for reproducing the vulnerability in a Google Docs file, wrapped it in a link through the clickmeter.com link tracking serviceand sent to the chat.
As I expected, my application caused a stir and increased interest among company employees, which was displayed in the analytics service clickmeter.com:

Application for 2 days was viewed by 22 unique users.

According to statistics, you can see that the link was viewed both from computers and from mobile devices. The geography of views was also not limited to the Kiev office, in the list Kiev, Lviv, Dnepropetrovsk, Tbilisi.
Analyzing the statistics, it becomes clear that the existing communication channel with the company is not intended for filing applications of this kind and can lead to information leakage and exploitation by third parties until the vulnerability is closed.
It is worth paying tribute to the company, the responsible employee contacted me on the second day, thanked and asked to remove the link from the public. Over the next few weeks, the vulnerability was closed, and I was contacted again and informed that the application was completed.
This story reminds us that we need to be more careful about information security issues in companies of such a scale as Kyivstar, create separate communication channels for this, access to which will be available only to authorized employees. Well, as well as the company's participation in bug-bounty programs or the creation of its own also has a positive effect on strengthening the security of services.
