Private messages from 81,000 Facebook accounts put up for sale
Browser extensions - the main channel of confidential information leaks
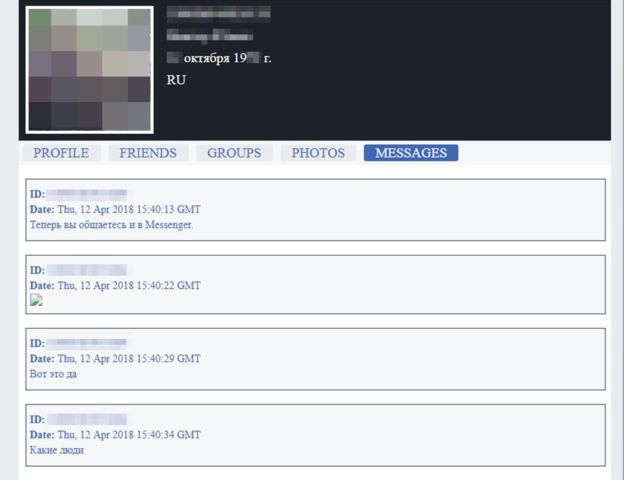
Of the world's largest social network, another data leak occurred. This time, not only the basic information about users has flowed away, but the most “secret” on Facebook - private messages of at least 81,000 users, mostly from Russia and Ukraine. The archive is up for sale, and the evidence was published by the BBC Russian service.
According to experts, private information obtained using malicious browser extensions. But the attackers claim that they have personal messages of 120 million people, including 2.7 million Russians. This is a small fraction of 2 billion active Facebook users.
Facebook commented that the hacking of internal networks is not fixed and the security of systems is not compromised. If the information was copied through extraneous extensions, then there really wasn’t any hacking. But the fact remains a fact: the real private messages in the archive are exposed to the public.
Hackers offer access to personal messages on 8 publy for one account. However, at the moment their ads are deleted.
For the first time the archive appeared on one of the English-language forums in September, the user published the ad under the nickname FBSaler. “We sell the personal information of Facebook users. There are 120 million accounts in our database, ”he wrote, although there are reasons to be skeptical about this figure.
More than 81,000 profiles were presented as samples. Cybersecurity company Digital Shadows has examined the product and confirmed the authenticity of the message. The Russian BBC service contacted five Russian Facebook users, whose personal messages are for sale. Those confirmed that the messages really belong to them.
Personal messages on the social network rarely contain any information that is valuable to outsiders. This is usually innocent chatter between relatives or friends. For example, in this case, the attackers to attract attention published several conversations. One of them included photographs from a recent vacation, the other - a conversation about a recent Depeche Mode concert, and the third - complaints about a son-in-law. There was also intimate correspondence between lovers.
Nevertheless, it should be understood that “personal” messages on Facebook or in any instant messenger are by no means private in the absence of end-to-end encryption. And even in this case, the text of the decrypted message on the screen can be read by malware, if it is previously installed on the computer. This is where the browser extension was made, but other programs can take screenshots and register all keystrokes from any programs on a computer or smartphone, so even strong encryption will not help here.
Experts reported that there are still 176,000 accounts in the sample, but some of this information, including email addresses and phone numbers, could be obtained in open form from users who did not hide the display of this data in their profile.
Extensions - the weak point of browsers
“We contacted the creators of the browsers to make sure that the known malicious extensions are no longer available for uploading to their extension directories,” said Facebook executive director Guy Rosen.
Obviously, browser extensions are becoming one of the main channels of leakage of confidential information from social networks.
Malware is often distributed along with innocent mobile applications or browser extensions. These can be shopping assistants, bookmarks, mini-puzzle games. Such extensions are offered for various browsers, including Chrome, Opera and Firefox.
According to Facebook, in this case, one of these extensions quietly tracked the activity of victims on the Facebook platform - and sent personal data and private conversations to hackers. Facebook didn’t name the specific expansion that caused the leak. Obviously, Facebook is not to blame for this, but users themselves should be more careful with installing third-party extensions.
Partially blamed for the hacking lies on Google, which allowed a malicious extension to the extension directory of the most popular Chrome browser. This is not a new problem: the catalog is periodically cleaned from such extensions. For example, last year several extensions were removed from there , posing as AdBlock Plus ad blocker, one of which had over 40,000 downloads. Malicious applications are also successfulOvercome the protection of the Google Play catalog .

Sometimes users report frauds for months, but Google responds with a delay.
How to solve the problem of malicious extensions?
It is clear that the user can optionally install any extension into his browser, not even from the official catalog, but from an external source. But it is believed that browser developers should be more attentive to the problem of malicious extensions. For example, they can enter the following mandatory requirements for installing an extension in a browser:
- Each extension must explicitly declare the URLs with which it intends to interact.
- Each extension should provide a diagram of any data that it intends to send from the browser.
- The browser locally logs all these communications.
- The browser blocks everything that does not correspond to the strict values of the specified policy.
You can also enter additional measures to limit the transfer of information from the browser.
