A formalized method for the analysis and analysis of normative and methodological documents, as well as the synthesis of local acts based on them

It so happened that I participated in the development of the direction of personal data at the very beginning of the appearance of the FSTEC documents on their protection. In this regard, I had to shovel a huge amount of various regulatory documents. A little later, work happened on organizing the processing of personal data - I had to create a fairly voluminous directory for operator’s employees who were not familiar with the requirements of the law. After radical changes to the law were made, this handbook was revised, and in order to convey the experience of such work, I created a formalized method for analyzing regulatory documents. About it further and will be discussed.
Methodology
The technique takes only one A4 sheet, but requires some explanation. I proceeded from the principle of special attention to the psychological state of a person who parses a document. Unfortunately, this work is cognitive - it requires a state of flow . When reading a normative act (hereinafter - ON, by which I will mean any normative, legal, methodological document) it is often difficult to keep thoughts on the text, wading through its legal and punctuation jungle. Therefore, it is better to adhere to the rule that any text search should be associated with one “concept” for one reading of the text (this is from the category: underline all letters “O” in “War and Peace”, cross out all letters “A” and circle in the circle all the letters "E").
Document Analysis (AT)
On the first three points of the methodology. These steps are necessary in order not to do "unnecessary" work. Suppose, if you need to draw up an employment contract, it makes no sense to read the code of criminal procedure. There is one remark - it is necessary to carefully read the scope of federal laws. Very often it turns out that the same concepts in different laws have different meanings - depending on the sphere in question (context).
Example:
Federal Law of July 27, 2006 No. 152-ФЗ “On Personal Data”
Article 11. Biometric personal data
1. Information that characterizes the physiological and biological characteristics of a person, on the basis of which it is possible to establish his personality (biometric personal data) and which are used by the operator to the establishment of the identity of the subject of personal data may be processed only with the written consent of the subject of personal data, with the exception of cases provided for in paragraph 2 of this article.
and
Federal Law of December 3, 2008 No. 242-ФЗ “On State Genomic Registration in the Russian Federation”
Article 1. Basic Concepts
3) genomic information - personal data, including encoded information about certain fragments of deoxyribonucleic acid of an individual or an unidentified corpse that do not characterize their physiological characteristics;
in this example, “personal data” in the concept of 242-ФЗ are not “biometric personal data” in the concept of 152-ФЗ.
Article 11. Biometric personal data
1. Information that characterizes the physiological and biological characteristics of a person, on the basis of which it is possible to establish his personality (biometric personal data) and which are used by the operator to the establishment of the identity of the subject of personal data may be processed only with the written consent of the subject of personal data, with the exception of cases provided for in paragraph 2 of this article.
and
Federal Law of December 3, 2008 No. 242-ФЗ “On State Genomic Registration in the Russian Federation”
Article 1. Basic Concepts
3) genomic information - personal data, including encoded information about certain fragments of deoxyribonucleic acid of an individual or an unidentified corpse that do not characterize their physiological characteristics;
in this example, “personal data” in the concept of 242-ФЗ are not “biometric personal data” in the concept of 152-ФЗ.
For 5-7 points, it is better to see:

Order of the FSTEC No. 17 (the “correct” arrangement of blocks is marked with a green border, and the “wrong” one is marked with red).
This is a general view of gluing placement:

Law No. 149-ФЗ “On Information, Information Technologies and Information Protection” “before” and “after” 23 points of the methodology (it is clear that colored pencils, crayons and a whole bunch of disassembled documents are in the cabinet: personal data and education).
Points 8 and 9 are mechanical work that just needs to be carefully performed and double-checked.
Paragraphs 8 through 15 are the “inclusion” of the maximum possible number of cognitive processes for storing information: its “convolution” and analysis.
At point 10, a trap from our legislators may lie in wait if we try to delve into the structure of NA: often the semantic blocks are in different parts of the law, and then at step 12 we can get a “mosaic”. In the case of fulfillment of paragraph 15 from the point of view of the subject, such a “mosaic” will always be obtained (various issues relating, for example, to the personal data operator, will be scattered throughout the text - in duties, terms, rights, etc.).
16 point - allows you to penetrate very deeply and visualize all the subtleties of ON. Its peculiarity is that color separation is not used at this step (visually contrasting colors are few, for the same reason you should not paint adjacent blocks with non-contrasting colors - it is better to alternate them: warm-cold).
Paragraphs 17 through 21 are necessary for visualizing the place of NA in the system of regulatory acts, and paragraph 20 is also to determine the list of local acts that should be developed in the organization.
Paragraphs 22 to 26 make sense only in cases where the disassembled AT is necessary for the current work.
Three examples of performing the described actions:
FSTEC Order No. 21.

Order of the FSTEC No. 31 (the annex with the tables is glued separately, aside)

Composite document (Decree of the Government of the Russian Federation No. 1119, Order of the Federal Security Service of the Russian Federation No. 378 and Order of the FSTEC No. 17). All classifications and determination of requirements are carried out sequentially from left to right: the presence of NDV, the level of security, the requirements for the regime, the class group of the crypto facility, the exact class of the crypto facility, the GIS class and its refinement by the security level of the PD are determined.

FSTEC Order No. 21.

Order of the FSTEC No. 31 (the annex with the tables is glued separately, aside)

Composite document (Decree of the Government of the Russian Federation No. 1119, Order of the Federal Security Service of the Russian Federation No. 378 and Order of the FSTEC No. 17). All classifications and determination of requirements are carried out sequentially from left to right: the presence of NDV, the level of security, the requirements for the regime, the class group of the crypto facility, the exact class of the crypto facility, the GIS class and its refinement by the security level of the PD are determined.
Document Synthesis (LA)
When developing an aircraft, a standard method for developing content and filling it is essentially described. Separately, it makes sense to note 3 and 5 points.
In paragraph 3, in the absence of any textual “content” for the document being created, it makes sense to refer to analogues of NA / LA in another area of law, using article 6 of the Civil Code of the Russian Federation.
Civil Code of the Russian Federation:
Article 6. Application of civil legislation by analogy
1. In cases where the relations provided for in paragraphs 1 and 2 of Article 2 of this Code are not directly regulated by law or by agreement of the parties and there is no custom applicable to them, such relations, if this does not contradict their substance, shall be applied civil law governing similar relationships (analogy to the law).
2. If it is impossible to use an analogy of the law, the rights and obligations of the parties are determined on the basis of the general principles and the meaning of civil law (analogy of law) and the requirements of good faith, reasonableness and justice.
1. In cases where the relations provided for in paragraphs 1 and 2 of Article 2 of this Code are not directly regulated by law or by agreement of the parties and there is no custom applicable to them, such relations, if this does not contradict their substance, shall be applied civil law governing similar relationships (analogy to the law).
2. If it is impossible to use an analogy of the law, the rights and obligations of the parties are determined on the basis of the general principles and the meaning of civil law (analogy of law) and the requirements of good faith, reasonableness and justice.
Paragraph 5 mentions the “canonical form of the text”. This is not a generally accepted concept taken from the remarkable, but difficult to read book of Yu. V. Kurnosov and Konotopova P.Yu. “Analytics: methodology, technology and organization of informational and analytical work” (for more details about it, see the 3rd paragraph from the bottom of the 335th page and further, RUSAKI publication, 2004).
Examples of “synthesis”:
• Rules for the processing of personal data for a state organization (the 15th parsing point is clearly presented here - the items are grouped not according to the text of the law, but by subjects, types of relationships, terms, etc.);
• Consent to the processing of personal data , which takes into account all references to it in the text of the law (may differ from the latest version of the law);
•The personal data subject’s request to the personal data operator (contains “a little more” than the subject has the right to request, but since the operators have not read the law in most of their cases, this makes an indelible impression on them and, usually, they agree to resolve the issue with the subject by the world without scolding and scandals).
Another example - the Rules themselves have already been drawn (not in the form of an intelligence card, but in the form of an algorithm - a mind-map degenerates into it, if everything is logically built):
A complete sequence of all steps to organize the processing and security of personal data in the organization.
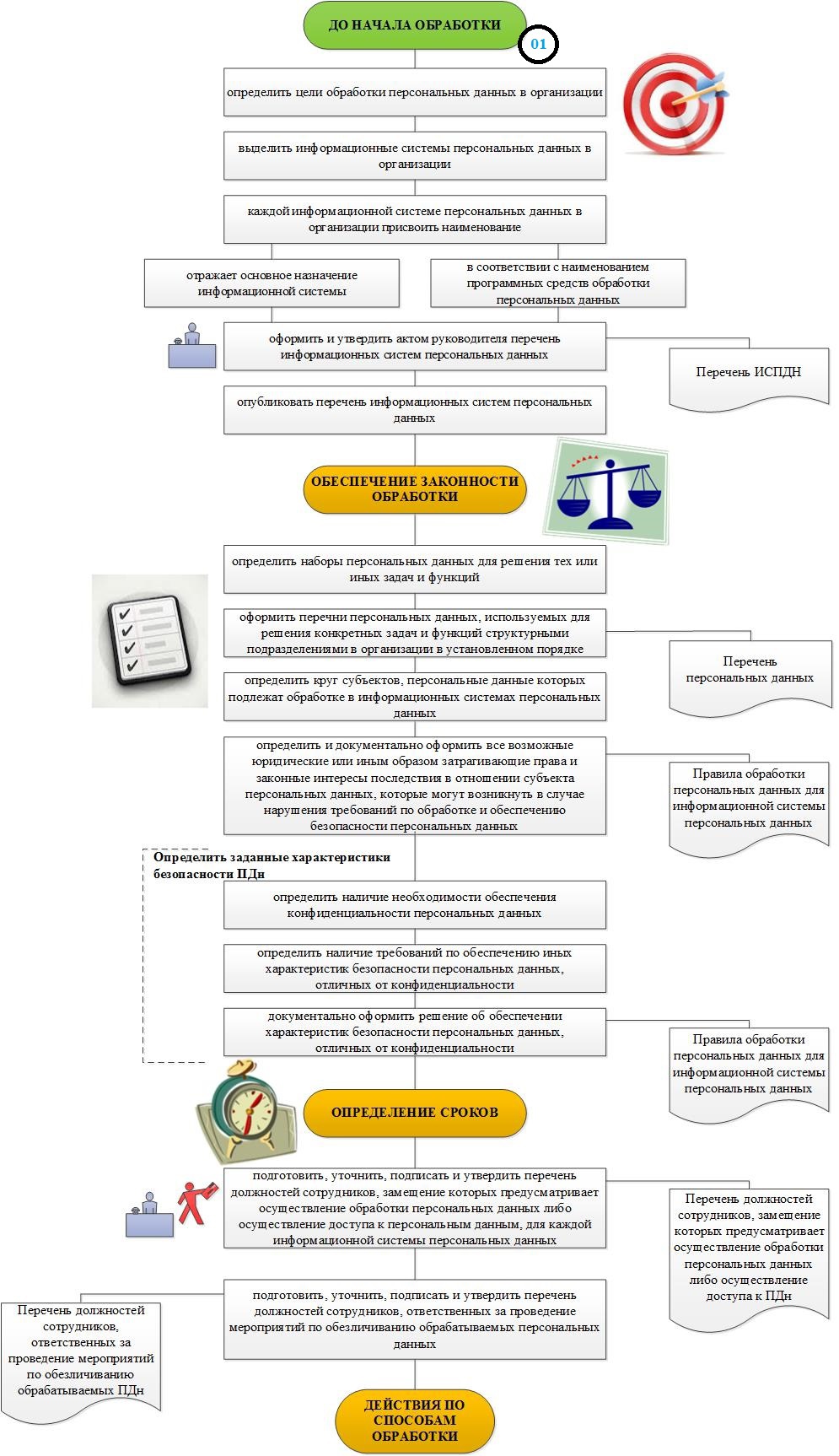
The algorithm of step 1 is the preparation for the processing of personal data in the organization.
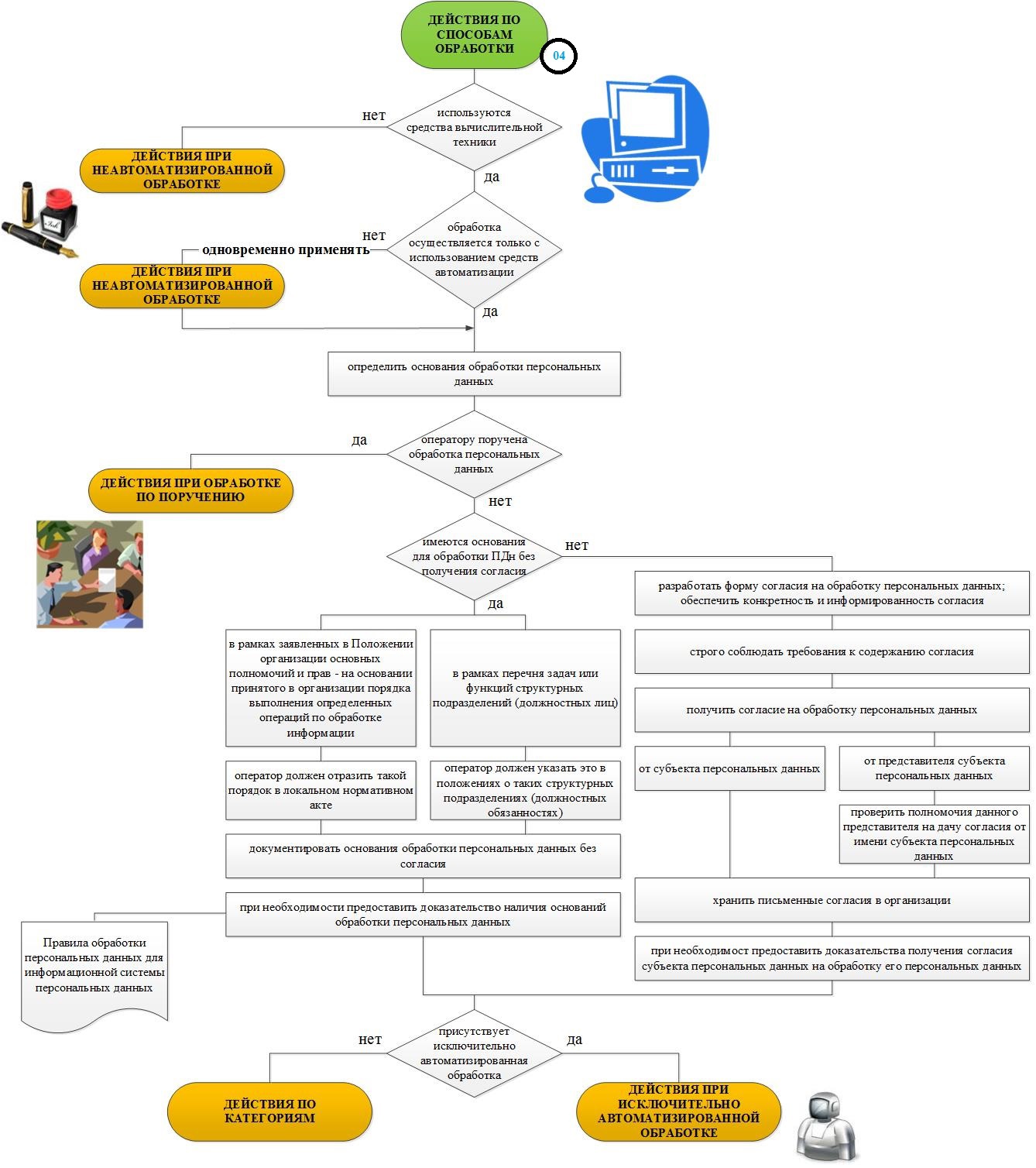
The 4-step algorithm is the necessary actions of the operator to process personal data in the organization, depending on the processing method.
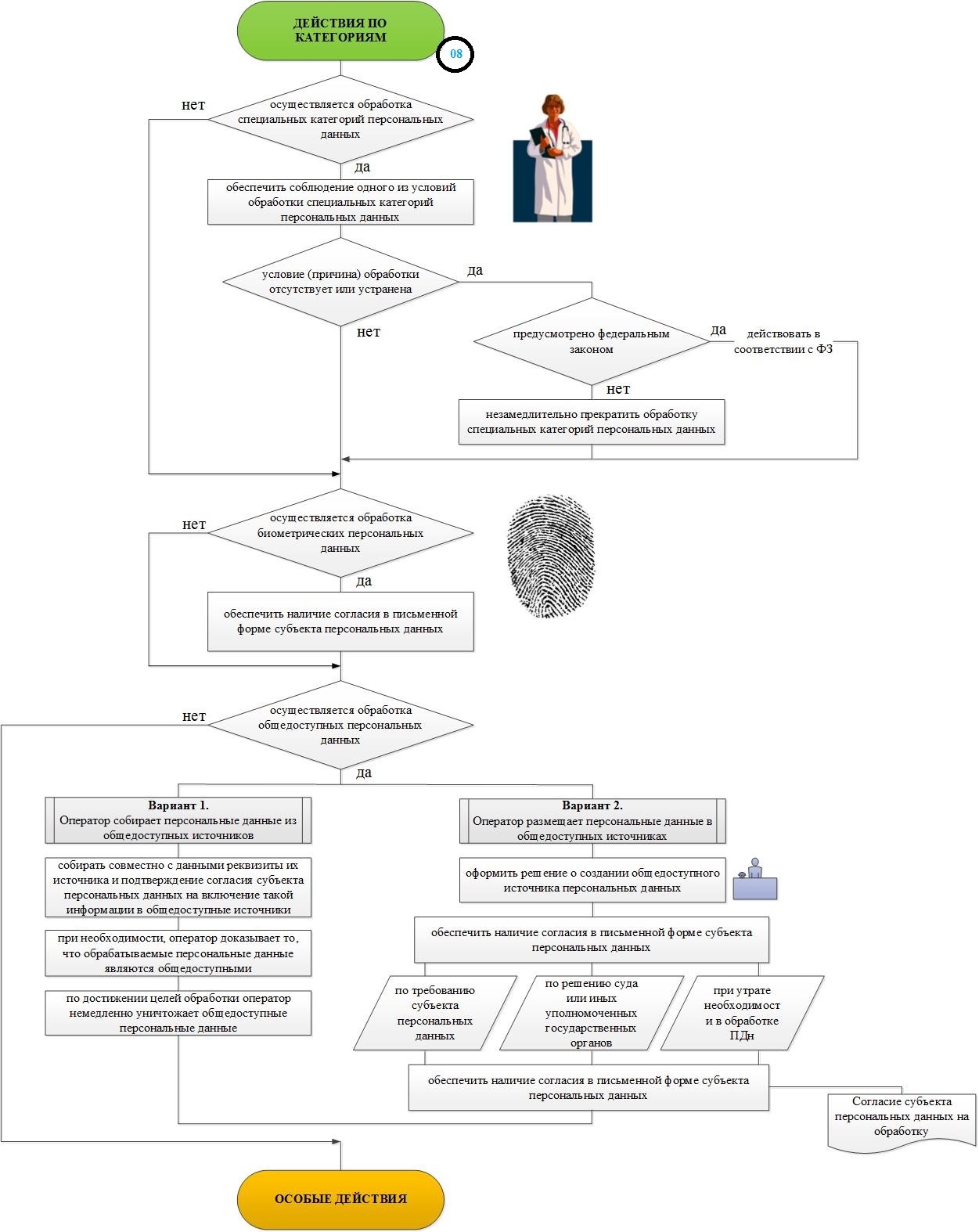
Algorithm 8 of the step - the necessary actions of the operator to process personal data in the organization, depending on the category of processed personal data.

A complete sequence of all steps to organize the processing and security of personal data in the organization.

The algorithm of step 1 is the preparation for the processing of personal data in the organization.

The 4-step algorithm is the necessary actions of the operator to process personal data in the organization, depending on the processing method.

Algorithm 8 of the step - the necessary actions of the operator to process personal data in the organization, depending on the category of processed personal data.
Conclusion
In conclusion, I remind you that it is very difficult to challenge the “literal reading” of what is written in regulatory enactments, so I urge you to read / write documents this way.
And, of course, this technique with some modifications can be used not only for parsing normative documents, but also for analyzing any literature (primarily educational) and synthesizing various reports, analytical notes, term papers and dissertations.
And the last, in order to use the described technique quickly, without hesitation, just by looking at the document, you need to “train” quite a lot, as in any business in which a person wants to become a professional or achieve noticeable results.
My personal email
My personal e-mail for questions, comments and suggestions xanton@list.ru
