Microsoft added another exploit protection feature in Windows 10
This is about the same Windows 10 Insider Preview Build 14316, which we mentioned several times in previous posts on the Ubuntu Linux subsystem. In the new build of Windows 10, the changes did not bypass the kernel. Microsoft added a new kernel object there called RegistryTransaction with the corresponding API functions for working with it like [NtCommit / NtCreate / NtOpen / NtRollback] RegistryTransaction . As it’s not hard to guess, we are talking about atomic operations with registry data.

Another improvement was the appearance of a long-awaited feature called Win32k syscalls filteringat the core level of Windows. Since it is still in pre-build of Windows 10, not much is known about it. Its main purpose is that it will completely close the sandbox for the processes of the respective applications, such as browsers, and will remove the issue of exploiting LPE vulnerabilities in win32k.sys for them. Today, such vulnerabilities are the main opportunity for an exploit to gain maximum SYSTEM privileges when entering a system through a web browser.
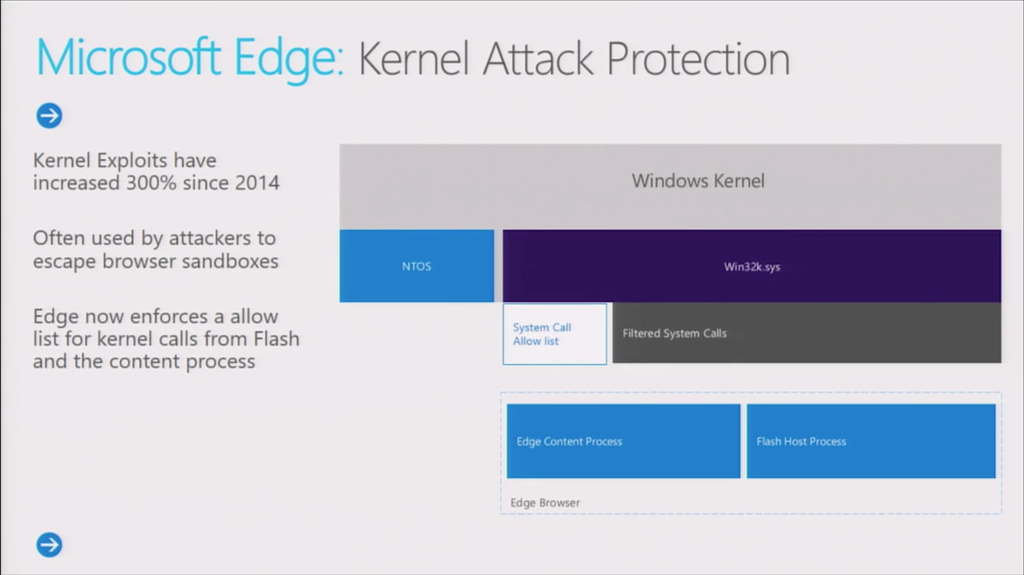
Fig. The general scheme of Win32k syscalls filtering using the example of the AppContainer-sandboxed Edge web browser, which can completely close the AppContainer from external influences.
It is worth noting that the authors of the Google Chrome web browser last year addedit has a function that protects sandboxed processes (renderer processes in Google terminology) from the harmful effects of win32k.sys. Since Chrome delegates work with graphics and windows to the main parent process, child sandboxed processes are completely freed from the need for GUI operations, such as rendering windows and other GUIs. Previously, the web browser setting -enable_win32k_renderer_lockdown was used for this .
Disabling win32k.sys completely is a sufficient security measure only for a web browser such as Chrome, which has a well-defined model for distributing functions between the parent and renderer processes (GUI functions do not overlap with sandboxed). Microsoft offers a more flexible way functionWin32k syscalls filtering ( PsAttributeWin32kFilter ) will help to selectively filter those functions that the process does not need, for example, Edge, and leave only the most necessary.
The Win32k syscalls filtering feature seamlessly complements another Windows 10 security feature that Microsoft first added to protect against LPE exploits. We are talking about the Block Untrusted Fonts function , which also appeared in EMET (see kernel32! SetProcessMitigationPolicy with the argument ProcessFontDisablePolicy ).
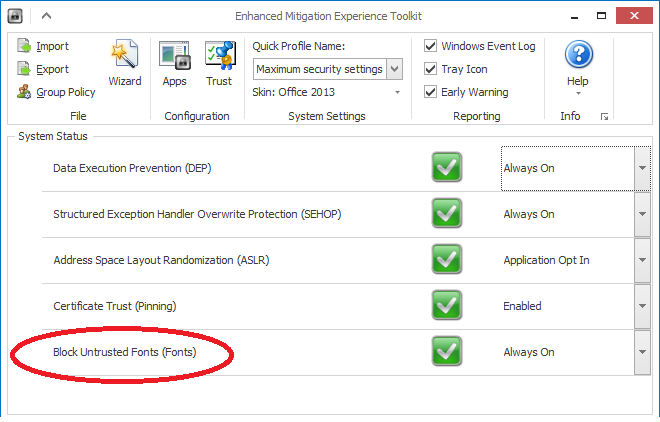
Fig. EMET Enables Enabling Block Untrusted Fontsfor the selected process, thus blocking the other attack surface with LPE-exploits that use specially crafted font files to exploit vulnerabilities in Win32k.sys.
Microsoft is known for its careful approach to exploit protection features that are integrated into Windows. DEP, SEHOP, ASLR, IE11-EPM, IE11-64bit_tabs, HEASLR consistently appeared there. The free EMET tool allowed forcing the inclusion of such settings for processes. At the same time, only with Windows 10 Microsoft began to take the above steps to close the vulnerabilities that are used by LPE exploits.
We wrote earlierand about the new Edge web browser in Windows 10, in which Microsoft abandoned all outdated technologies such as COM or ActiveX, which were used to inject their code into the web browser with malware (the same thing will happen to Flash Player). It also closed other possible places of injection (injection) of malicious code into the run-time running process, and also uses the AppContainer and 64-bit tabs by default. Using the Win32k syscalls filtering function will make this web browser even more secure.

Another improvement was the appearance of a long-awaited feature called Win32k syscalls filteringat the core level of Windows. Since it is still in pre-build of Windows 10, not much is known about it. Its main purpose is that it will completely close the sandbox for the processes of the respective applications, such as browsers, and will remove the issue of exploiting LPE vulnerabilities in win32k.sys for them. Today, such vulnerabilities are the main opportunity for an exploit to gain maximum SYSTEM privileges when entering a system through a web browser.

Fig. The general scheme of Win32k syscalls filtering using the example of the AppContainer-sandboxed Edge web browser, which can completely close the AppContainer from external influences.
It is worth noting that the authors of the Google Chrome web browser last year addedit has a function that protects sandboxed processes (renderer processes in Google terminology) from the harmful effects of win32k.sys. Since Chrome delegates work with graphics and windows to the main parent process, child sandboxed processes are completely freed from the need for GUI operations, such as rendering windows and other GUIs. Previously, the web browser setting -enable_win32k_renderer_lockdown was used for this .
Disabling win32k.sys completely is a sufficient security measure only for a web browser such as Chrome, which has a well-defined model for distributing functions between the parent and renderer processes (GUI functions do not overlap with sandboxed). Microsoft offers a more flexible way functionWin32k syscalls filtering ( PsAttributeWin32kFilter ) will help to selectively filter those functions that the process does not need, for example, Edge, and leave only the most necessary.
The Win32k syscalls filtering feature seamlessly complements another Windows 10 security feature that Microsoft first added to protect against LPE exploits. We are talking about the Block Untrusted Fonts function , which also appeared in EMET (see kernel32! SetProcessMitigationPolicy with the argument ProcessFontDisablePolicy ).

Fig. EMET Enables Enabling Block Untrusted Fontsfor the selected process, thus blocking the other attack surface with LPE-exploits that use specially crafted font files to exploit vulnerabilities in Win32k.sys.
Microsoft is known for its careful approach to exploit protection features that are integrated into Windows. DEP, SEHOP, ASLR, IE11-EPM, IE11-64bit_tabs, HEASLR consistently appeared there. The free EMET tool allowed forcing the inclusion of such settings for processes. At the same time, only with Windows 10 Microsoft began to take the above steps to close the vulnerabilities that are used by LPE exploits.
We wrote earlierand about the new Edge web browser in Windows 10, in which Microsoft abandoned all outdated technologies such as COM or ActiveX, which were used to inject their code into the web browser with malware (the same thing will happen to Flash Player). It also closed other possible places of injection (injection) of malicious code into the run-time running process, and also uses the AppContainer and 64-bit tabs by default. Using the Win32k syscalls filtering function will make this web browser even more secure.
