Marshmallow Everyone should do it. Add SDK 23 support to our applications
- Tutorial
 I was lucky to become a Google Developer Expert Android in Russia , and therefore I doubly worry that not all of you have prepared for the release in advance. Now we will try to jump onto a sailing ship with marshmallows.
I was lucky to become a Google Developer Expert Android in Russia , and therefore I doubly worry that not all of you have prepared for the release in advance. Now we will try to jump onto a sailing ship with marshmallows. You can not read, but just see my report on the past DroidCon .
But especially for those who like to read habr more than watching youtube - welcome to cat. There we will go through the checklist of actions that everyone should definitely do in their application, and then look at the new features for developers in sdk 23.
Important Notice
All of the following applies only to applications with targetSdk = 23 and higher! I’ll be ready to discuss how applications with older sdk on marshmallows will behave in the comments.
Doze Mode, App Standby, and Runtime Permissions
Unfortunately, the length of the article was not able to accommodate these three major changes in Android Marshmallow. Please read about them in a separate article .
Autobackup
Now Android applications every night, while the device is charging, will merge all the settings into the user Drive. Rather, those that we allow.
What for?
When buying a new one, the user immediately restores not only all applications from Google Play, but also their settings.
What is bad for us?
Account data and GCM keys fly off to the cloud and to new devices from shared preferences (pushies stop working). It must be prevented!
By default, all folders of our application and all SharedPreferences will be backed up. They do not save only:
- paths on the SD card that are not in android / data / ...
- getCacheDir ()
- getCodeCacheDir ()
- getNoBackupFilesDir ()
The last daddy was created just for this purpose.
To prevent some files from being backup, we’ll write such an xml, where we list all the data that we don’t want to be backed up:
<android:fullBackupContent="@xml/mybackupscheme"><full-backup-content><excludedomain=
["file" | "database" | "sharedpref"| "external" | "root"] path="string”>
</full-backup-content>
To determine the opposite, only those files that we want to upload to the cloud:
<android:fullBackupContent="@xml/mybackupscheme"><full-backup-content><includedomain=
["file" | "database" | "sharedpref"| "external" | "root"] path="string”>
</full-backup-content>
If the backup doesn’t need any data to be restored, we can do this trick: in the Application successor class, redefine the onRestoreFinished () method and delete undesirable restored records in it.
! Remove Google Cloud Messages keys from backup!
Learn more: developer.android.com/intl/en/training/backup/autosyncapi.html
Example: developer.android.com/intl/en/samples/AutoBackupForApps/index.html
Deprecated
If you are still using the Apache Http client and completely refuse to switch to modern analogs, for example, OkHttp , then you urgently need to add to build.gradle :
android {
useLibrary 'org.apache.http.legacy'
}
Now they cut OpenSSL from sdk: libcrypto.so and libssl.so are replaced by BoringSSL.
If you suddenly did not know until today about Notification.Builder , but used notification.setLatestEventInfo () to generate notifications , that's enough, it has been deleted. Read at least my article , and preferably the official docks , how to create and update notifications correctly.
Adoptable storage
Now the user can format the sd-card, turning it into an almost internal encrypted storage. And thus, the system will transfer and install applications to the new storage. How does this threaten us?
If we do not use standard methods and constants in the application to get the paths ( getFilesDir () , getCacheDir () , etc.), and we hardcode the paths to the internal storage, then after moving the files to the card, the mount point will change, and all our carefully registered paths will no longer be valid.
Read more: developer.android.com/intl/en/about/versions/marshmallow/android-6.0.html#adoptable-storage
Small but important additions
Access to the poppy addresses of devices in the district is now possible only when scanning using WifiManager.getScanResults () methods BluetoothLeScanner.startScan () and with requested permissions ACCESS_FINE_LOCATION or ACCESS_COARSE_LOCATION . But the WifiInfo.getMacAddress () and BluetoothAdapter.getAddress () methods will always return a dummy 02: 00: 00: 00: 00: 00 . This is done in order to increase user security. It’s a pity that not everyone will upgrade to marshmallow, and custom firmware is unlikely to preserve this limitation.
From Android, Keystore provider dropped support for DSA encryption.
Now WifiConfiguration statesobjects, our applications can only change if they themselves have created them.
The camera has a good change in working with access to the service. If the application has gone into the background, and another application, on the contrary, has come to the fore, then it will be given priority, and the first will lose the service. And yet, now you can use from different applications simultaneously access to different cameras of the device.
ART changes
- Now the processing of rights to newInstance () is correctly implemented .
- The dynamic linker now understands the differences between the soname of the library and its path, and a search has also appeared on soname .
- The dlopen (3) RTLD_LOCAL flag was repaired .
New Android Features
The mandatory changes to our application are over. Let's move on to the main features that the new SDK provides us with.
App linking
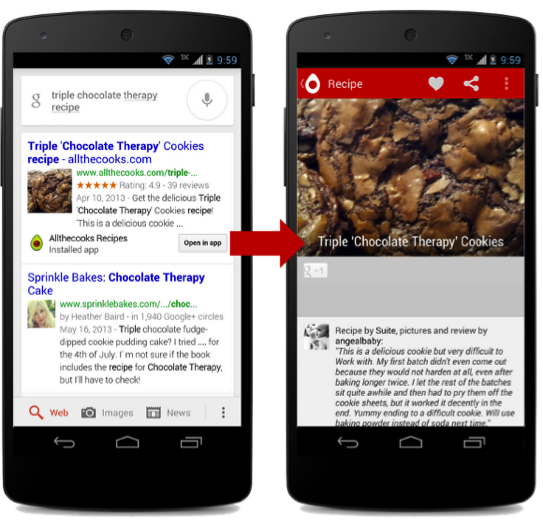
Many developers embed url filters in their applications so that the user is prompted to open a specific url using the application. Now there is an opportunity to deprive other developers of the ability to handle the url of your site. Suppose if you are doing banking, then you definitely do not want other applications, except for the client application of your bank, to be opened by a user clicking on a link.
In the manifest you need to add this kind of filter:
<intent-filterandroid:autoVerify="true"><actionandroid:name="android.intent.action.VIEW" /><categoryandroid:name="android.intent.category.DEFAULT" /><categoryandroid:name="android.intent.category.BROWSABLE" /><dataandroid:scheme="http"android:host="www.android.com" /><dataandroid:scheme="https"android:host="www.android.com" /></intent-filter>And put JSON on your website (https://www.domain1.com/.well-known/assetlinks.json) by inserting sha256 from the keystor with which the application is signed.
[{
"relation": ["delegate_permission/common.handle_all_urls"],
"target": {
"namespace": "android_app",
"package_name": "com.example",
"sha256_cert_fingerprints":
["14:6D:E9:83:C5:73:06:50:D8:EE:B9:95:2F:34:FC:64:16:A0:83:42:E6:1D:BE:A8:8A:04:96:B2:3F:CF:44:E5"]
}
}]
The only thing worth remembering: if your application is not installed, the "open with" dialog box pops up and the attacker application can open.
Read more: developer.android.com/intl/en/training/app-links/index.html
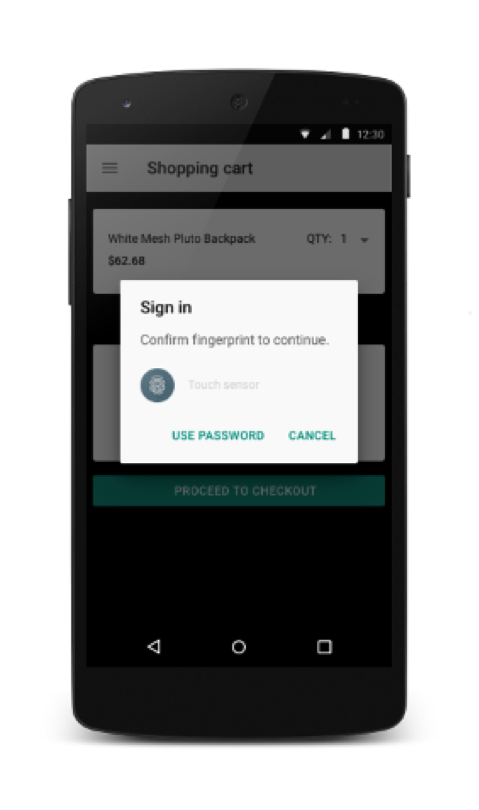
Fingerprint API
Finally, Android has native support for fingerprint sensors. Now, using the android.hardware.fingerprint.FingerprintManager class, we check for the presence of the isHardwareDetected () sensor in the device , request USE_FINGERPRINT permission , and if the user has the hasEnrolledFingerprints () fingers rolled back , we show the standard authentication dialog using authentificate () fingerprint .
More details .
An example .

Confirm Credentials
Now we have the opportunity to double-check that the device is now in the hands of its owner, showing the unlock screen before an important action in the application, for example, when trying to open the folder "/ Rest in Adler 2007 /".
More details .
An example .
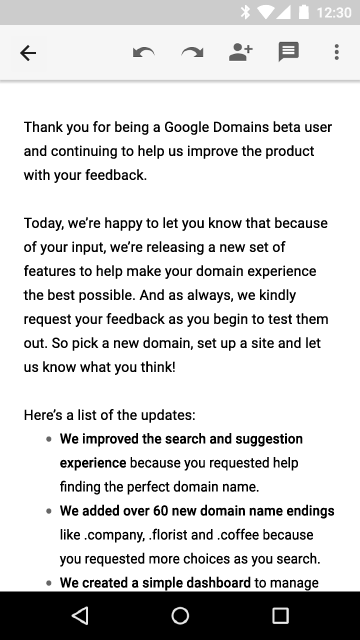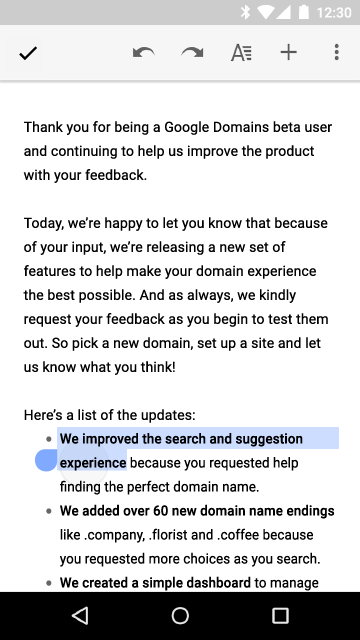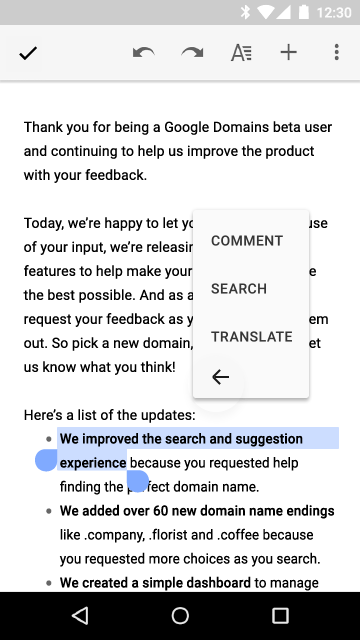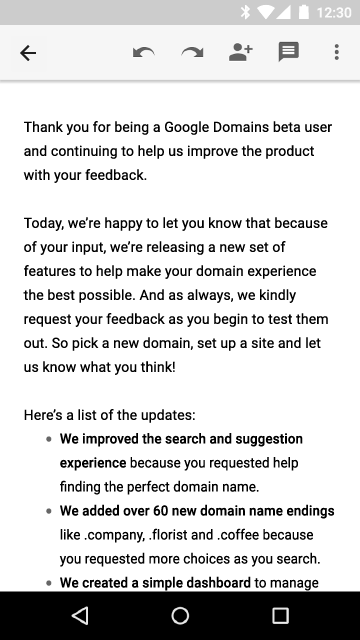
Text selection
Now the context menu for actions with selected text appears directly next to the carriage, to add our actions we can also use the menu described in menu.xml and add it using the startActionMode method (Callback, ActionMode.TYPE_FLOATING) .
More details .
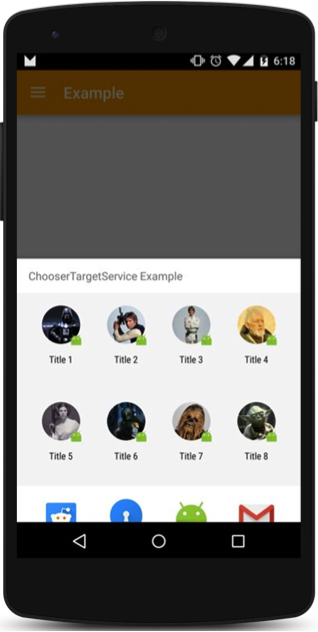
Direct share
An important addition to Marshmallow is the ability to add up to eight different objects to a standard sharing dialog for one application:
The main thing is not to clutter up the dialogue with useless sharing options. Try not to abuse.
Learn more: developer.android.com/intl/en/about/versions/marshmallow/android-6.0.html#direct-share
Example: developer.android.com/intl/en/samples/DirectShare/index.html
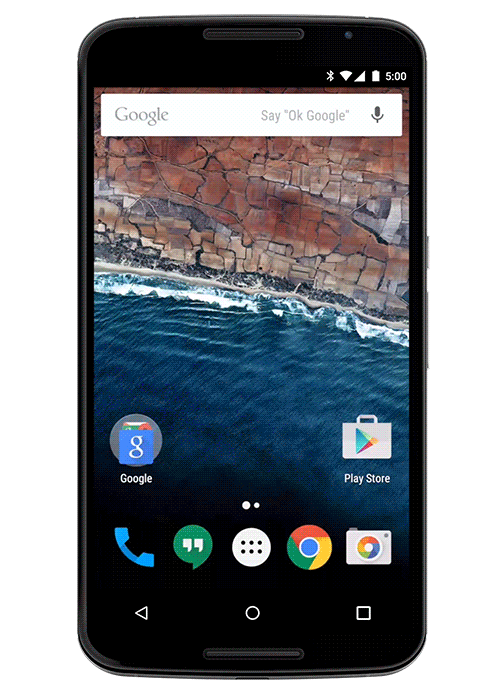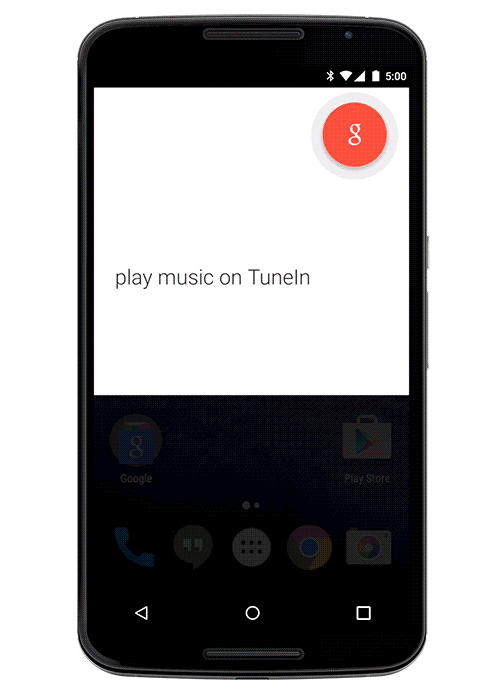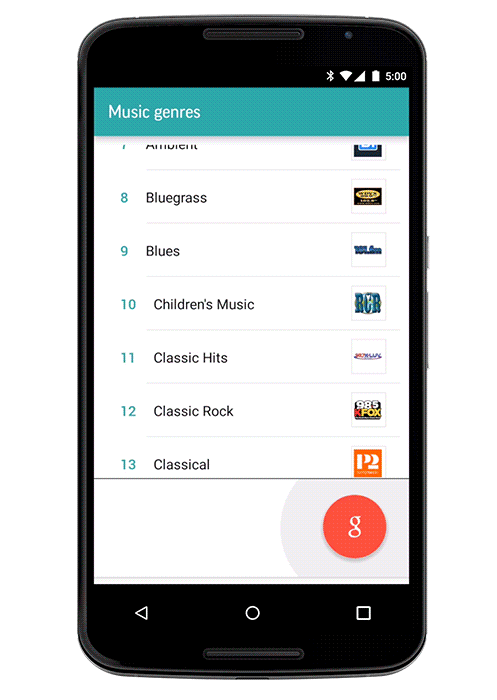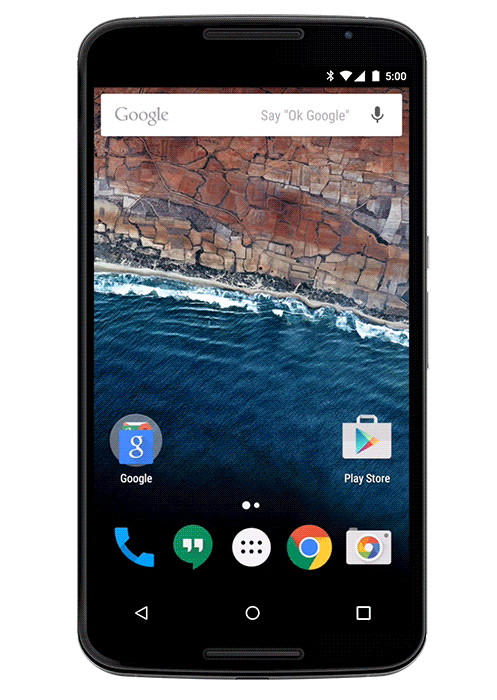
Voice interaction
An important, but not so detailed lighted chip, in contrast to the "Now on tap" . Our application, being launched from Google Now, can conduct a dialogue with the user using the android.app.VoiceInteractor class .
Learn more at developers.google.com/voice-actions/interaction/voice-interactions .
The list does not end there. Smaller innovations can be read here .
Be sure to go through all the points above. Check autobackup, doze mode and request all permissions. I will be happy to answer all questions in the comments.
