HackedSim. Call from any number - fiction or reality?
 An article about HackerSIM with an intriguing title and promising content appeared on the hub last week . The essence of the article was as follows: for a substantial amount an order of magnitude higher than the cost of a regular SIM card, some guys provide you with their SIM card, which allows you to "safely call from any number from any country with any voice to the selected numbers" (in quotation marks because that the aggregation of theses from the previously mentioned article is cited here). After looking at the comments, it turned out that there was a keen interest in this topic, but no one had an accurate understanding of how it works and whether it works at all.
An article about HackerSIM with an intriguing title and promising content appeared on the hub last week . The essence of the article was as follows: for a substantial amount an order of magnitude higher than the cost of a regular SIM card, some guys provide you with their SIM card, which allows you to "safely call from any number from any country with any voice to the selected numbers" (in quotation marks because that the aggregation of theses from the previously mentioned article is cited here). After looking at the comments, it turned out that there was a keen interest in this topic, but no one had an accurate understanding of how it works and whether it works at all. After a little thought with colleagues, we decided to tell how this service is feasible in real life.
Initially, we were skeptical about the content of the above article, obviously written by a layman in this field, so we decided to see what is on the Internet on this topic. Here are a few resources ( safecalls.ru , a video of work , another video ) that convinced us of the serviceability of the proposed service (only the declared call security remained in question, since we could not see it on the video, so its availability will be discussed further) . In addition, requirements were added, such as working with any mobile phones and smartphones, the absence of the need to install programs and having an Internet connection.
Service Description
We will try not to bore the reader with technical details and describe some processes at a rather abstract level. In case of interest in some unlit details, please write questions in the comments. We hope this complements the big picture.
Connection and network registration
When installing a new SIM card, the first thing the phone tries to connect to the home network. As it has already been written many times, the phone sorts the available frequencies by signal level in descending order and then tunes in to them in turn in search of their operator until this process is successful. The considered SIM card, as stated, works in any country of the world, therefore, it is obvious that, as a rule, it does not work on the home network - the SIM card is roaming and uses base stations provided by other operators for communication. Only other operators “just like that” do not provide their equipment to “not” their customers, this only happens if roaming agreements are concluded between the operators.
However, firstly, the GSM association is trying to widely disseminate standardized roaming agreements, and secondly, no one has tested how this SIM card works in other countries. According to unverified data in the modern world, most often everyone has these agreements with everyone, but this is not important here, but the fact that the providers of such a service must have a licensed operator that provides them with SIM cards, and the operator has roaming agreements.
As was just what was said by default, your phone connects to the base station with the highest signal level. But in order to ensure security, namely, protection from IMSI Catchers, when using this SIM card, the connection is made to the second most powerful BTS (Base Transceiver Station). From a technical point of view, this can only be done at a very low level, because the baseband processor performs the entire logic of working with the radio channel (a modem is a separate device in your phone with its own architecture and OS). The Secret Life of SIM Cards Report Presented at Defcon 21, from it you can understand that the sim card also has its own OS and its own applications. At the same time, applications on the SIM card can display the simplest UI controls — for example, the “Live Balance” service is implemented that way, open urls, send sms, make calls, and receive notifications about the start / end of a call.
These applications are written in a greatly reduced version of the Java language and use the SIM Toolkit (STK) API for interaction. There is little documentation about the operation of Applets SIM and the baseband processor, but if the function of choosing the second most powerful base station works, then this can be implemented using the SIM Applet. This is really time-consuming and difficult work (maybe even impossible - we did not study the documentation for the interface provided by the baseband in detail), which can only be performed by a highly qualified specialist, but our opinion is that this function is not supported in these SIM cards, since for its execution it requires a lot of resources, and the result is not only dubious, but for the vast majority it is inconspicuous (not everyone can verify it). Therefore, most likely this is just a marketing ploy. Another argument in favor of the fact that this function is not implemented is that the written application needs to be "uploaded" to the SIM card. Naturally, this can be done not by anyone, but only by the holder of the OTA Install Key, which is unique for each SIM card.
In the presentation above, there is a slide with the Shadytel operator and the SIM card distributed by him with Ki, IMSI and OTA Install Key. We do not know whether it is licensed, but if it is, and the organizers of the Hacker SIM service use this or a similar operator, then the user of this SIM card should not sleep well, because while he is sleeping on his card, third parties can fill out the code with might and main ( because they know OTA Install Key).
As for the forced use of the A5 / 1 encryption algorithm for traffic between MS and BTS with the participation of this SIM card, this again refers us to the previous paragraph. The command to establish the encryption algorithm comes from the BTS MS in the Ciphering Mode Command message of the Radio Resource Management protocol (over LAPDm). Thus, the sim card needs to receive this package from the baseband and, in the case of an “inappropriate” algorithm, reject the command and terminate the connection. For all this, the baseband should provide a sim card with a very developed interface. And again, the problem arises of developing and installing the application on the SIM card (it is not even clear what is more difficult). In addition, another rhetorical question arises: why is only the A5 / 1 algorithm used? It’s clear that A5 / 1 is needed for compatibility with old equipment, but if the user's phone and operator’s equipment support A5 / 3, then why not use it, because it is, according to experts in the field of cryptography, safer? So most likely this feature is not implemented.
Making a call from any number
Now let's move on to the most interesting - what is shown in the video, confirmed by the comments on the article, and therefore implemented - by making calls from absolutely any numbers.
The idea of this technique is that for calling on telephone networks to identify the calling party (Caller), two identifiers are used simultaneously: the identifier of the number that is billed and the number that is displayed on the equipment of the party receiving the call (Callee).
Those who are interested in the details and details of this topic can familiarize themselves with it in more detail:
To begin with, it is important to understand that a regular telephone network actually consists of two. The first network is used to transmit user call traffic, the second is a packet-switched network, which is used to establish voice calls, complete them, support various other features, in particular caller id and special numbers starting from 800. This network is a general channel alarm system No. 7 (Signal System 7, SS7). Initially, access to it had only switching nodes and databases of telecom operators. However, later access was partially expanded to PBX (private branch exchange - private corporate lines) to provide access to caller id and other SS7 features through ISDN PRI (the type of connection to ISDN and the cable used for it).
Obviously, with the ability to manipulate signal information in SS7, there are great opportunities for various tricks in the telephone network, including the substitution of the outgoing number. In order to understand how this is done, you need to consider the process of setting up a call on a regular telephone network. During the call, the switch on the calling side generates and sends two messages to the receiving switching equipment via the SS7 signaling channel. The first message is called IAM (Initial Address Message). It contains the number of the subscriber they are trying to reach, as well as a special ANI (Automated Number Identification) number according to the old terminology, or as it is now called CHARGED DN. This number is used to identify the caller and bill (billing). To manipulate them, as a rule, impossible. This number is generated and sent by the switching equipment of the servicing customer of the telecom operator. ANI or CHARGED DN is displayed when receiving a call from emergency services (i.e. the option to call the Ministry of Emergency Situations with a fake number disappears - they display ANI on the equipment, which in general can not be replaced) and can be received by private clients for incoming calls when using access to the telephone network using PRI or SIP.
The switching equipment of the receiving operator, in response to the first IAM message, generates a second one, which is called an INR (Information Request) and, in turn, also sends it via the SS7 signaling channel to the switching equipment of the subscriber who makes the call.
In response to this message, the switching equipment of the operator of the subscriber making the call generates a second INF message. It is this message that contains the very infamous CPN (Called Party Number) / Caller ID. This is the same number that is displayed on the phone screen when receiving an incoming call. In addition to the number itself, the message may contain a “privacy” flag, which instructs the receiving switching equipment not to issue the number to the end-user equipment. If the subscriber has activated a service that allows him to see all the numbers of incoming calls, then the number will most likely be displayed regardless of the privacy flag.
The following is a schematic depiction of the process of exchanging the described messages:
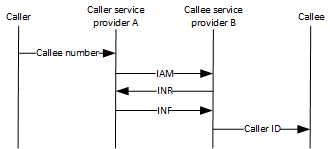
Caller ID can be changed by the switch, which is part of the PBX, and connected to the signaling channel through a PRI or SIP gateway.
It should be noted that CPN / Caller ID can be sent immediately in the first IAM message, in which case the INR request and the INF response are not made. However, this does not change the essence: there is a separate number for which an invoice is issued, and a separate number that is simply displayed on the screen of the telephone receiving the caller’s call.
Obviously, with the ability to manipulate signal information in SS7, there are great opportunities for various tricks in the telephone network, including the substitution of the outgoing number. In order to understand how this is done, you need to consider the process of setting up a call on a regular telephone network. During the call, the switch on the calling side generates and sends two messages to the receiving switching equipment via the SS7 signaling channel. The first message is called IAM (Initial Address Message). It contains the number of the subscriber they are trying to reach, as well as a special ANI (Automated Number Identification) number according to the old terminology, or as it is now called CHARGED DN. This number is used to identify the caller and bill (billing). To manipulate them, as a rule, impossible. This number is generated and sent by the switching equipment of the servicing customer of the telecom operator. ANI or CHARGED DN is displayed when receiving a call from emergency services (i.e. the option to call the Ministry of Emergency Situations with a fake number disappears - they display ANI on the equipment, which in general can not be replaced) and can be received by private clients for incoming calls when using access to the telephone network using PRI or SIP.
The switching equipment of the receiving operator, in response to the first IAM message, generates a second one, which is called an INR (Information Request) and, in turn, also sends it via the SS7 signaling channel to the switching equipment of the subscriber who makes the call.
In response to this message, the switching equipment of the operator of the subscriber making the call generates a second INF message. It is this message that contains the very infamous CPN (Called Party Number) / Caller ID. This is the same number that is displayed on the phone screen when receiving an incoming call. In addition to the number itself, the message may contain a “privacy” flag, which instructs the receiving switching equipment not to issue the number to the end-user equipment. If the subscriber has activated a service that allows him to see all the numbers of incoming calls, then the number will most likely be displayed regardless of the privacy flag.
The following is a schematic depiction of the process of exchanging the described messages:

Caller ID can be changed by the switch, which is part of the PBX, and connected to the signaling channel through a PRI or SIP gateway.
It should be noted that CPN / Caller ID can be sent immediately in the first IAM message, in which case the INR request and the INF response are not made. However, this does not change the essence: there is a separate number for which an invoice is issued, and a separate number that is simply displayed on the screen of the telephone receiving the caller’s call.
Acting on the first identifier (it is called ANI (Automated Number Identification) or CHARGED DN) is illegal and, as a rule, impossible. Manipulation of the second parameter (Caller ID) can be performed by any PBX (private branch exchange - private corporate lines) connected to ISDN. Thus, anyone with access to the telephone line via SIP or PRI can change the Caller ID to whatever they like without worrying about the consequences. ISDN telephony operators usually do not verify that the Caller ID is real. VoIP providers are even less likely to reduce the functionality of their clients.
It follows that the number displayed on the screen of the receiving side is very easy to change. It is also seen that anonymity is completely absent when making a call on a public telephone network. This is achieved due to ANI or CHARGED DN. It is on the basis of this number that the systems of investigative and search measures work, while Caller ID in such cases no longer interests anyone.
Practical guides on how to do this yourself can be found on request in the search engine “Caller ID spoofing”.
By the way, looking ahead, let's say that only calls have a Caller ID. When sending sms message with this field is not used. This explains the fact that the proposed SIM cards do not support sending SMS. Although this is presented on the site, as for "security purposes."
Installing PBX - in fact, a regular telephone network in the office - is not difficult, both financially and administratively. PBX, in turn, connects to the public telephone network using PRI (the provider extends the cable to your office), or using SIP no longer over the telephone cable, but over the available Internet channel. As a result of this event, your office is allocated a pool of city numbers from which you can call freely.
Summarizing what has just been said: to make a call from an arbitrary number, you just need to order from the ISDN telephone operator to provide you access to the telephone network via PRI or from the SIP telephone service provider via SIP, with the ability to manipulate some parameters of voice calls (in particular, Caller ID).
The official regulatory body of the FCC (Federal Communications Commission) in this regard is expressed as follows: “Telecommunications operators must provide the correct number for display to the end user, and if possible the name of the company making the call.” US operators are fined for providing false information. However, the situation when the Caller ID is changed by a non-operator is not regulated in any way even in the USA.
But, using this approach, you can call with an arbitrary number (as we found out by Caller ID) only from the phone of the organization that owns PBX, and providers of a random number service state and demonstrate in numerous videos that you can call with a given number from any mobile phone in the absence of the Internet and any third-party software.
The solution to this problem seems really interesting to us (one might even say hacker). The process of calling from a mobile phone to another with an arbitrary outgoing Caller ID is shown in the diagram:
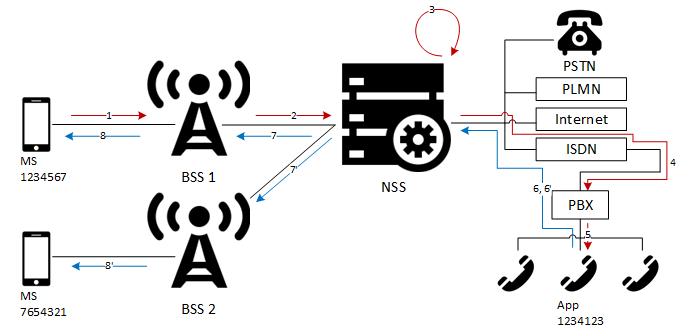
The diagram shows how the subscriber with number 1234567 (we will call him subscriber A) calls subscriber 7654321 (subscriber B) with an arbitrary number.
First of all, according to the instructions from one of the sites that provide the SIM card service with the ability to change the outgoing number, you must enter the USSD command of the type 150 * phone_number *, which subscriber A does.
The phone is connected to the network, it is in roaming, so the first two steps shown in the diagram are performed trivially, in full accordance with the GSM documentation. In the third step, the MSC (Mobile Switching Center), according to its routing tables, sends a request for HLR to the home operator of the SIM card and receives an indication of forwarding USSD to 1234123, which in turn is the organization’s office phone connected to PBX. The latter is connected to SS7 via a cable laid by the ISDN provider through the PRI ISDN. Thus, at the 4th step, the initial USSD command reaches the PBX distributors of this SIM card. This equipment probably runs specific software, which, upon this request, adds itself to the config rule for replacing the number from which the request came up with the number in the USSD command.
Then subscriber A makes a call to subscriber B. Steps 1-5 are repeated exactly and the call reaches the PBX, after which it “drops” subscriber A. The application on the PBX, in turn, using Caller ID spoofing to change the number, makes a call to subscribers A and B. The call reaches subscriber A and he is “shown” either a random number or a phone number connected to PBX, in parallel the call reaches subscriber B, he sees a fake phone number on the phone screen and picks up the phone. Next, the PBX simply “forwards” the traffic that is transmitted during the conversation of subscribers.
I would like to note that even though calls are established through a third-party PBX, this does not add anonymity, since this PBX can always be found physically - it is registered. And after that, the right people will surely find out who is calling and through it, compare the time of calls and receive data that is in no way inferior to the call detail that can be obtained from the operator in the event of a subscriber making a call from a regular SIM card.
Since it is claimed that all voice traffic passes through one PBX, it is easy to guess that it is there that the tonality of the voice of the subscriber changes. But this creates additional risks - since all calls pass through it, it is not difficult to record / save / analyze them there.
conclusions
In conclusion, I would like to express the opinion that a call from any number with a selected voice pitch - a thing that is undeniably cool for practical jokes and jokes - we are sure now to be able to make any reader if they wish, the security of conversations not exceeding the usual, and sometimes inferior to the default security in 2G networks (operators often use A5 / 3, we don’t even talk about 3G networks), lack of declared anonymity and protection from wiretapping, lack of support for SMS and the Internet, as well as the potential for collecting your goal cial traffic by third parties (after all, it is clear that they can not only change the tone of voice, but also parallel to store and analyze) - questionable service for a lot of money even taking into account the cost of roaming.
I would like to highlight the “hacker" idea of the developers who, using the opportunities provided by the operator, are absolutely legal (with the possible exception of selling SIM cards without documents) - and after all, the first thing that arose about the legality of this service is that they organized this service . But, unfortunately, this is the case when everything looks much more attractive than it really is.
It should be noted that the proposed implementation of this service with a high degree of probability coincides with that implemented by the people selling it. But at the same time, do not forget that we can be wrong. In order to dot all the “i”, you need to purchase this sim-card and explore how it works. But the cost of this event cools the research fervor.
