PentestBox - portable assembly of popular security utilities

To date, the most popular penetration testing distributions are * nix-like distributions: Kali Linux , BlackArch Linux, Pentoo, Whonix, and many others. They can be used both in a virtual environment, and as a live system or even be installed as a desktop OS.
Until recently, Windows users were deprived (we don’t take virtual machines into account) of such assemblies until a magic box appeared - PentestBox .
PentestBox is not like other security distributions that run on virtual machines. The idea of its creation was visited by the author Aditya Agrawal after studying statistics - more than 50% of users who downloaded distributions used Windows:
- Samurai Web Testing Framework - 66% of those who downloaded.
- Santoku Linux - 60% of the downloads.
- Parrot OS - 59% of the downloads.
What makes PentestBox different?
Simple to use. Download 2.5 gigabytes from the site, unpack and everything is ready to use. Not as resource intensive as a virtual machine instance. There are no dependencies, all utilities, standard commands - everything is installed. Also, the Mozilla Firefox browser is installed with the most popular add-ons for auditing web applications .
PentestBox is quite easy to customize - add the utilities you need to the python / ruby / executable file and write aliases. Updates will not be any difficulties either. The interface is designed as a command line with a "classic" green font on a black background, old school.
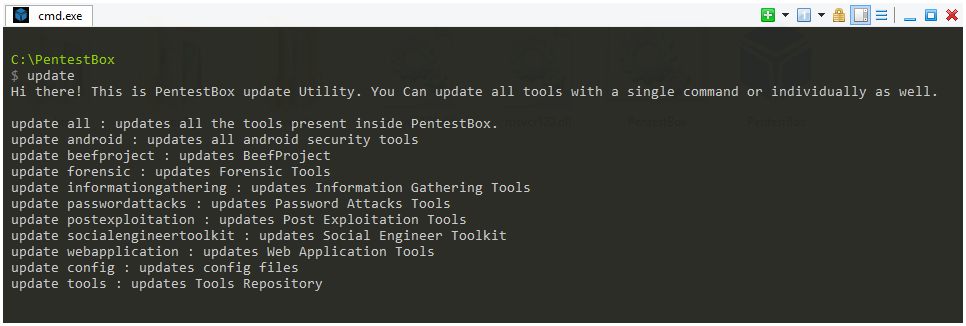
PentestBox contains a fairly large number of popular utilities that facilitate the penetration testing process. Utilities are divided into groups that facilitate their search and use - from information gathering and intelligence, web scanners, bruteforce utilities to utilities for analyzing Android applications and Wi-Fi.
The assembly does not contain one of the main "harvesters" used by security experts and hackers - the Metasploit framework. The author points out that for the installation, and so on, there is a completely working Windows version of this product that perfectly fulfills its purpose in its native form.
On the author’s website, the utilities are presented in sections, there are overlapping positions, so I arranged the utilities, classifying them according to the method of use / impact. Some utilities on the original site contain incorrect links / descriptions, keep this in mind.

Collection and analysis of information
This section contains utilities for preliminary exploration of the target.
dirs3arch - bruteforce (dictionary search) directories and file names.
nikto is a utility for finding and exploiting known vulnerabilities and incorrect web server configuration.
DirBuster is a multi- threaded directory and file scanner.
Angry IP Scanner is an easy-to-use IP / port scanner.
dnsrecon - a utility that facilitates the collection of information about the DNS of the investigated system.
Instarecon - automation of preliminary reconnaissance of the investigated server - dns zones, whois, shodan and google requests to search for possible targets for an attack.
Knock - search for possible subdomains in the dictionary.
Nmap- network mapper, the most powerful port scanner. Many modes and use cases. The legend of hack software.
SnmpWalk - Search and identify SNMP devices.
SSLyze - Identify SSL configuration errors.
SSLScan - the durability of the SSL / TLS algorithms used.
Subbrute - search for possible subdomains in the dictionary and using open DNS resolvers.
Tekdefense-Automater - collection of information about URL / IP address.
The Harvester - a utility for collecting information from the attacked site: email, employee names, hidden resources.

Web Application Audit
This section contains almost all existing popular (open source) utilities for researching vulnerabilities in web applications.
Burp Suite is one of the most popular vulnerability analysis tools for web applications. It consists of several modules that complement each other. Convenient utility for automation in "manual" research.
Commix is a simple python utility for exploiting command injection attacks.
dirs3arch - bruteforce (dictionary search) directories and file names.
fimap - search and exploitation of Local File Include / Remote File Include vulnerabilities. May use google dork.
Golismero is a web application testing framework.
Ironwasp- A framework for searching for vulnerabilities, privilege escalation. Contains a module for attacking the web interfaces of WiFi routers.
jSQL is a lightweight utility for operating sql-injection.
PadBuster is a utility for operating Padding Oracle Attack .
SqlMap - Swiss Army knife for sql-injection exploitation.
Vega - a platform for testing the security of web applications, there is a GUI.
Wpscan is one of the most popular tools for finding vulnerabilities in WordPress sites.
Xenotix XSS - a framework for exploiting XSS vulnerabilities.
Yasuo is a small ruby script for exploiting vulnerabilities in the server platform.
Zaproxy- Zed Attack Proxy is one of the most popular tools for auditing web applications.
Beef Project is a powerful utility for executing various attacks exploiting XSS vulnerabilities.

Password Utilities
Here are collected popular utilities for selecting passwords for online services and means for decrypting (selecting) hashes.
CryptoHaze is a fast utility based on CUDA and OpenCL technologies for selecting MD5, SHA1, LM, NTLM hashes.
Findmyhash is a utility for finding hashes using several online services.
HashIdentifier - a utility for determining the type of hash.
Hashcat is one of the fastest utilities (CPU) for password selection from a hash.
John the Ripper is one of the most famous multi-platform password cracking tools.
Patator is a popular tool for password selection for ftp / ssh / mysql / http and many others.
RainbowCrack - a utility for selecting passwords withrainbow tables .
THC Hydra is one of the oldest and most efficient password cracking utilities ftp / ssh / mysql / http and many others.
Android security
Several utilities and frameworks for analyzing applications of one of the most popular mobile OSs.
Androguard - a utility for analyzing malware applications.
Androwarn is a utility for detecting potentially malicious application behavior.
ApkTool - analysis of encrypted resources, rebuilding, debugger.
dex2jar - converter .dex> .class
drozer - one of the most popular frameworks for searching vulnerabilities in Android applications and devices.
Introspy is a utility for analyzing and identifying potential vulnerabilities.
JD-GUI - GUI utility for analyzing java source .class files.
Pidcat is a utility for analyzing and ranking log files.
JadIs a console utility for extracting source code from .class files.
Smali / Baksmali is a tool for analyzing and working with dalvik instances.
Stress testing
Utilities impact on attacked applications and devices.
Doona is a utility for checking applications for buffer overflows.
Termineter is a framework for testing measuring instruments operating under the C1218 and C1219 protocols.
THC-SSL-DOS is a utility for testing server configuration for SSL renegotiation .

Forensic
Utilities for collecting "digital evidence", forensic analysis, collecting evidence.
Autopsy - a framework for extracting deleted files, web surfing, etc.
Bulk Extractor - scanning and analyzing files, folders, building histograms from the received data.
CapTipper - detection of malicious HTTP traffic, analysis of .pcap files.
DumpZilla is a utility for extracting information from Firefox, Iceweasel and Seamonkey browsers.
Loki - a utility for detecting the presence of the so-called digital weapons and malicious code distributed during APT ( targeted attacks ).
PDF tools - search and identification of suspicious objects in PDF documents, analysis of PDF elements.
PeePDF - analysis of objects, elements and streams contained in PDF files.
Origami is a utility for analyzing and working with infected pdfs (used for drive-by attacks).
pype32 , pyew , pedump - utilities for working with PE / PE + files.
RAT Decoders - extracting configuration data from popular remote control systems (here in the context of backdoors).
rekall is a utility for extracting and analyzing information from RAM.
Volatility is a powerful framework for collecting and analyzing artifacts extracted from RAM.

Wifi
Utilities for attacking wireless networks. (Carrying out such attacks in a Win environment is rather doubtful, substantial dances with a tambourine may be required, I warned you :)
Aircrack-ng is a package of utilities for monitoring, analyzing and attacking wireless networks surrounding you.
Wifi Honey - a utility for creating Rogue AP - fake access points .
Miscellaneous
Everything else is in this section, mainly for local attacks.
SET - Social Engineer Toolkit, a platform for conducting sociotechnical attack methods.
SSlStrip - proxy server for downgrade and interception of HTTPS traffic.
Responder - a fake server for intercepting HTTP / SMB / MSSQL / FTP / LDAP authorizations.
UrlCrazy is a phishing attack tool.
Wireshark is a powerful traffic analyzer (sniffer).
LaZagne is a utility for extracting locally stored passwords - from browsers, ftp clients, WiFi and more.
JavaSnoop is a utility for testing Java applications.
OLLY Debugger- Win32 debugger with a huge number of necessary functions, plugins and settings.
Radare2 - a set of utilities for working with binary data, reversing.
DNSChef - DNS proxy for intercepting and filtering requests.
Ettercap is a network sniffer with the ability to attack changes to ARP table entries.
Conclusion
The project is very promising in view of the ability to add your own modules and a good initial set of opensource / free tools. You can work quite comfortably in this ecosystem - there is an atom, vim, a browser, most linux commands work. If it is too redundant for you, you can customize it to your liking, leaving and adding only the tools you need that you can always have on hand, for example, on a USB flash drive.
