The hacker Alexei, who protects MikroTik routers without the permission of the owners, has become famous
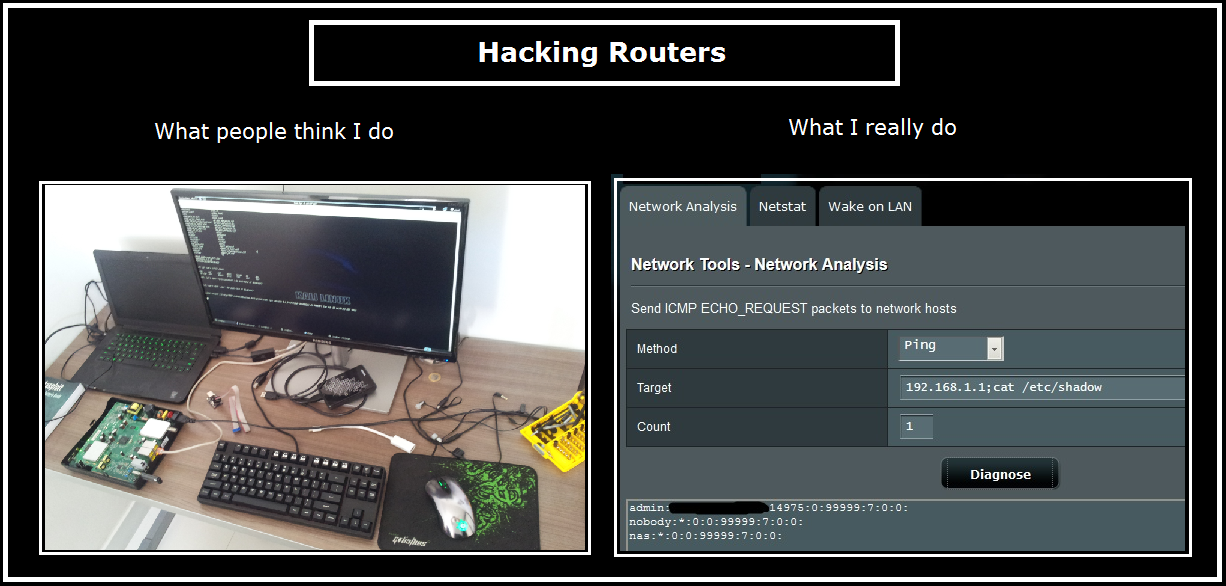
On Habré they spoke in detail about the vulnerability CVE-2018-14847 , which affects about 370 thousand MikroTik routers around the world (including 40 thousand in Russia) . In short, the vulnerability in MikroTik RouterOS allows without special authorization to read remotely any file from the router, including poorly protected access passwords. Although the patch was released very promptly in April, many router owners do not follow the updates. As a result, their devices remain vulnerable and are included in the IoT botnets that are used by attackers. Over the past few months, several cases have been recorded when through vulnerable MikroTik routers installed Coinhive scripts for mining in a browser
and set up a DNS redirect to malicious sites . The situation worsened on October 5, when a new exploit of By The Way for CVE-2018-14847 was released.
But not all hackers are ready to take advantage of users' nonchalance and make money on it. Some are trying to help. The other day, the popular western publication ZDNet talked about the "mysterious Russian-speaking hacker" who "breaks into routers and patches them without user permission." In fact, we are talking about the habrayuzer LMonoceros , which can now be considered a celebrity.
In his last article, Alexey said that he gets access to routers and makes changes to their settings to prevent further abuse.
Alexey works as a server administrator. Technically, his noble work falls under several articles of the criminal code, so it would be prudent to maintain anonymity. But judging by this, he is not too keen on this: according to ZDNet , the specialist “boasted of his hobby on the Russian blog platform”. It’s easy to guess that we are talking about the article “Why Mikrotik for hackers and how I hid 100 thousand RouterOS from a botnet” , which LMonoceros published on Habré on September 27, 2018.
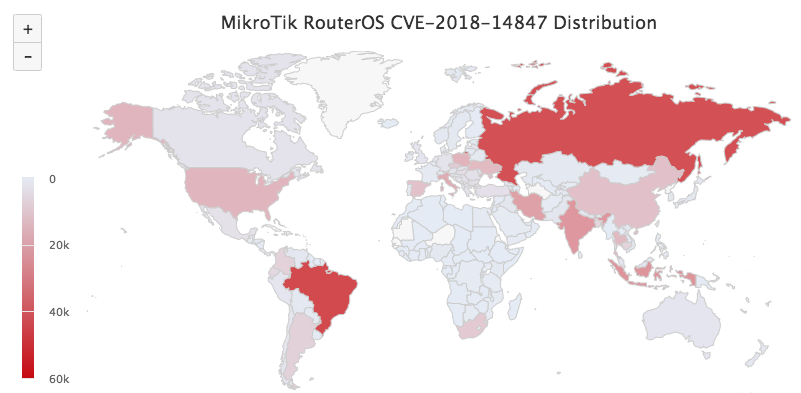
Distribution map of vulnerable devices as of September 2018, Illustration: Kaspersky Lab
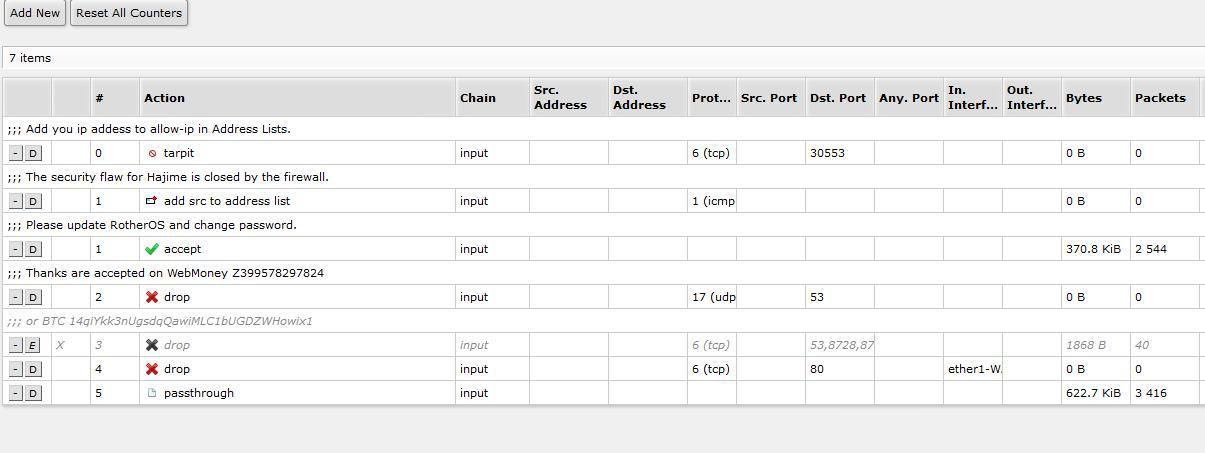
Alexey says that by now he has already patched 100 thousand vulnerable routers. “I added firewall rules that blocked access to the router not from the local network,” he wrote. “In the comments I wrote information about the vulnerability and left the address of the telegram channel @router_os , where you can ask questions.” The instruction on setup of a firewall was also earlier published on Habré . Apparently, this editing of configs , about which the admin complained, was made by another well-wisher. He does not write the address of the telegram channel, but indicates the wallet number. Note that today (October 15, 2018) there are already 1080 participants on the RouterOs Security channel. Every day they discuss the situation with the vulnerabilities of Mikrotiks.
MikroTik is one of the most popular router brands to date. More than two million MikroTik routers operate worldwide. According to some researchers, now more than 420 thousand of them are involved in IoT botnets and participate in mining.
Despite configuring the firewall for more than 100,000 users, Alexei says that only 50 people contacted via Telegram. Some said thank you, but most were outraged.
Alexey’s technically illegal activities are worthy of respect, but he’s not the first to act just as noble, reminds ZDNet . For example, in 2014, a hacker gained access to thousands of ASUS routersand posted text alerts on computers with shared folders that were behind these routers, warning users to close the vulnerability.
At the end of 2015, the White Team hacker group released a Linux.Wifatch malware that closed the security holes of various Linux-based routers. At some point, the White Team botnet became so big that it started fighting the botnet of the infamous group Lizard Squad for the title of the largest botnet on the Internet.
Finally, most recently, in 2018, an unknown hacker renamed tens of thousands of MikroTik and Ubiquiti routers to attract the attention of owners to update their devices. The devices are named like “HACKED FTP server”, “HACKED-ROUTER-HELP-SOS-WAS-MFWORM-INFECTED” and “HACKED-ROUTER-HELP-SOS-HAD-DEFAULT-PASSWORD”.
Despite the efforts of noble hackers, the security situation of IoT devices remains deplorable. But it’s nice to realize that thanks to its useful activity, the Russian specialist LMonoceros has now truly become famous.
New Year's ACTION GlobalSign: 50% DISCOUNT on Wildcard certificates.

