Eat breakfast yourself, share your work with the "cloud"

How Zyxel Cloud helps the local gateway to repel threats.
Speaking of security (and not only in IT) it is customary to frighten the consumer.
“Here come the evil hackers and hack the network. Therefore, it is necessary, it is necessary, it is necessary ... and further a long list of everything that needs to be bought, set up to order, spend, and, most importantly, allocate a lot of money for this.
Terrible stories about mysterious kidnappings of “client bases” that caused the complete collapse of the company are walking on the Internet.
In fact, buying someone else's customer database is only one of the additional opportunities to improve the business, but not a panacea for poor revenue. This opportunity still needs to be able to realize with profit for themselves.
But at the same time, there are real threats that any organization, any person can face.
What can happen?
First, any hacking, even a simple disfigurement of the site - is a blow to reputation. There is a well-founded opinion that if an organization's IT infrastructure is easily cracked, and the leadership “doesn’t lead to the ear and does not blink an eye,” it means something is wrong with this organization as a whole .... With some reservations, something similar can be said about careless people who do not think about security problems.
It is especially unpleasant when, using your name, incomprehensible people come to your partners and try to put on their own bad deeds.
Because when the fraud is revealed, it will be not some hidden enemies that will be suspected, but you, first of all. The simplest thing is to blame one of the injured parties for the crime whose honest name was used.
Even with the use of official sources of information there are plenty of opportunities for fraud, and if an attacker gains access to internal documents, bills and so on - then expect trouble.
Secondly, security breaches are the banal theft of money from accounts (including from employees' salary cards). There is nothing to comment on.
Thirdly, it is a simple attempt to eliminate competitors.
The above was an example of copying the client base.
But it can be much worse when it intercepts not customers, but suppliers.
Because there can be a lot of customers, and sometimes established supply relations - sometimes “once and twice”.
Of course, invading from the outside is not the only danger. Offended employees are capable of causing no less harm than external intruders. However, poor network protection can provide invaluable assistance to both internal and external "personalities" in their insidious designs.
What will the "cloud" help?
In our troubled world, the number of all defense mechanisms is growing and replenishing in proportion to the number of emerging threats. Of course, to ensure all this, more and more power is required.
As usual, there are various ways to implement.
The simplest option is to limit yourself to the local gateway.
The essence of this approach is to perform all operations strictly on the local protection device - the gateway, router, server, and so on.
Of course, it will have to be strengthened all the time, including upgrading the hardware. And one day it will have to be replaced.
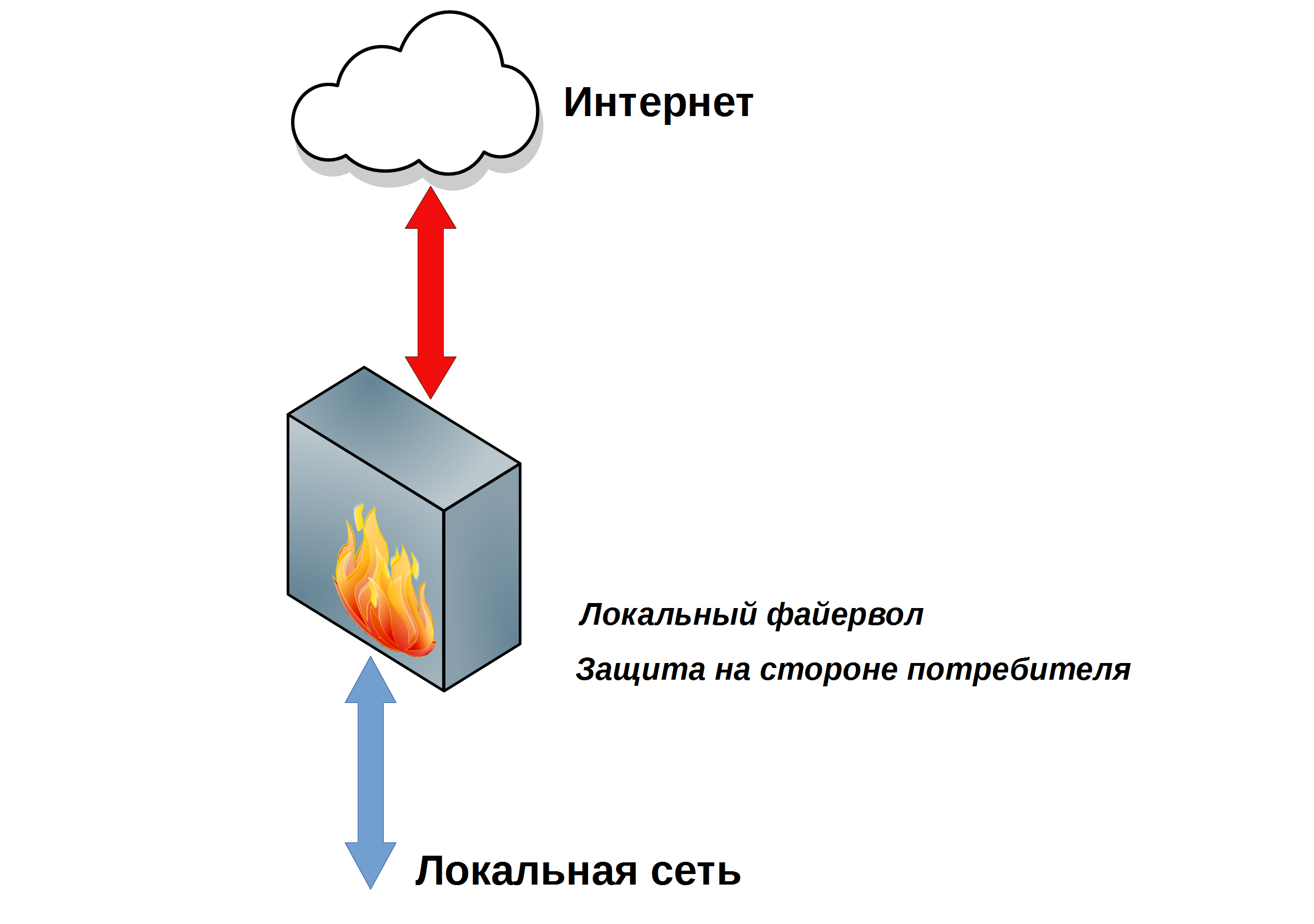
Figure 1. Local Network Security.
When all the protections are concentrated on the local device, it only looks like that every little thing is under vigilant supervision.
As it turns out, not everything is under control. The biggest problem is that it is impossible to accurately predict the emergence of new threats, and therefore it is impossible to plan the schedule and costs for updating.
To end up with outdated equipment that no longer meets new requirements is a very real prospect.
And here another interesting moment arises - it is necessary to upgrade or replace all (!) Gateways in the network. If 90% of the equipment is ready to cope with the increased load, and 10% is not ready, it means that this protection system is simply not ready for new threats, regardless of percentage ratios.
And can make all the protection to external resources?
Such a model of protection exists for a long time. For example, some Internet service providers offer a traffic inspection service.

Figure 2. Protection on the ISP side.
With this approach, there is one indisputable advantage: “give and forget” and in parallel with this there are many shortcomings: for example, the price, the means and level of protection used, the overall performance of the system (“The Internet suddenly began to slow down”) and so on may not be enough.
And thanks to this drawback, “give and forget” does not work. It is necessary to “give away” and something else to constantly control, write applications, etc.
But the biggest trouble that sometimes arises is the poor management of external services. For example, an antivirus on the provider’s gateway has blocked the necessary and useful file. Interaction "by phone call" or by writing tearful letters by e-mail: "Please be kind, return me the sent file" - this is not suitable for normal work.
Accordingly, the provider must provide a convenient tool for the full management of the service, which should work exclusively reliably. But the understanding of the "completeness", "convenience" and "reliability" of the supplier and the consumer of the service may differ significantly.
For the same reason, the use of other services "from the provider," for example, blocking unwanted resources, may not be suitable for everyone.
But regardless of the facilities provided, the protection of the organization’s network on the provider’s side is somehow in the hands of others and depends on many factors, including the good faith and qualifications of the specific person who will do it.
And then an interesting idea arises:
“Is it possible to leave practically the entire set of protection functions behind, giving away the most costly operations?” And at the same time get rid of the notorious "human factor" by maximally automating all the processes? "
The cloud solution comes to the rescue.
Let's try to split our protection system into separate functions, while either leaving them on the local device or sending them to external resource - in the "cloud".

Figure 3. Protection with no cloud support.
For example, for detailed scanning of a file for a malicious component, additional hardware resources are required. Therefore, it would be wiser to give the suspicious file to the "cloud" for review.
At the same time, the “cloud” test result can be saved and reused. If the checksum at the next request for the same file is the same, then the verdict is made without the cost of verification.
Pay attention: all (!) Necessary controls are on the local device and, as they say, always at hand. Only automated verification processes are transferred to the “cloud”. It is worth noting that the whole procedure of such interaction has been reconciled and tested many times.
In this case, anonymity is higher than when checking with the provider. It looks like this: a file comes into the “cloud” and or even a piece of the file without any “readable” data from the point of view of the person. The cipher is used, according to which the system itself determines where the file came from, and what to do with it.
With the cloud verification system, the local device is always in touch with an external service and gets access to the latest signatures, algorithms and other tools to protect the network.
Turnkey solution - Zyxel ZyWALL ATP200 firewall with cloud security services.
In fact, it is quite simple in terms of a device that can install and configure any sysadmin.
Figure 4. Web-based interface for configuring the Zyxel ZyWALL ATP200 firewall with cloud security services.
Consider some of the technical details of the solution based on the Zyxel ZyWALL ATP200 firewall in combination with the Zyxel Cloud cloud security service.
Zyxel Cloud cloud intelligence identifies unknown files on all ZyWALL ATP firewalls that are used throughout the world, and stores all the information about each new threat detected.
It organizes the results in the Cloud Threat Database and sends daily to all ATP updates.
With each attack, the database accumulates more and more useful information about potential threats, which increases the level of protection, including the ability to analyze traffic for potential threats.
In this way cloud learning takes place and Zyxel Cloud is constantly adapting to new attacks.
To apply the knowledge gained together with the Zyxel ZyWALL ATP200 in combination with the Zyxel Cloud comes a whole set of powerful tools, in particular, multi-level protection Multi-Layer Protection. The following services and features are available:
- Malware Blocker - in addition to traditional protection in streaming antivirus mode, this module is synchronized daily with the Cloud Threat Database, so protection against malicious code in ATP is not limited only to the local level, but through global exchange through the cloud provides comprehensive protection at the global level;
- Application Security - includes Application Patrol and Email Security features that not only block cyber attacks, but also provide customizable controls to optimize application traffic and block unwanted applications;
- Intrusion Prevention (IDP) - performs in-depth checks to block weaknesses in the protection of the application and using these weaknesses of attacks, ensuring complete security;
- Sandboxing — an isolated environment in the cloud where suspicious files are placed to identify new types of malicious code, which greatly enhances protection against zero-day attacks;
- Web-Security - includes the functions of Botnet Filter and Content Filter, which ensure the verification of both URL and IP addresses using the categories of addresses that are synchronized with the cloud, which can evolve with the growth of the cloud base;
- Geo Enforcer - can restrict access from those countries where threats most often occur, and find out the geographical address of the initiator or potential victim of the attack by converting GeoIP IP addresses to physical addresses;
- SecuReporter - performs a comprehensive analysis of logs with data correlation and provides reports on parameters specified by users. This is a necessary tool for service providers.
Of course, in a short article it is impossible to describe all the many useful functions that have appeared in the arsenal to protect the network thanks to the Zyxel Cloud.
In the next article on this topic, we will describe in more detail about each of the used protection methods. One thing is clear - at the initial stage, ordinary “cloudless” means protect the perimeter of the network fairly well, but with increasing requirements, “cloud” resources significantly expand security capabilities.
Sources
[1] A page on the Zyxel website dedicated to the Zyxel ZyWALL ATP200 firewall with cloud security services.
[2] The article “Building an expanded anti-virus protection system for a small enterprise. Part 3 ".
