Replace Two-Factor Authentication
Introduction
2014 can be safely called the year of hacked accounts. According to the Identity Theft Resource Center , data has been stolen more often than ever since 2005.
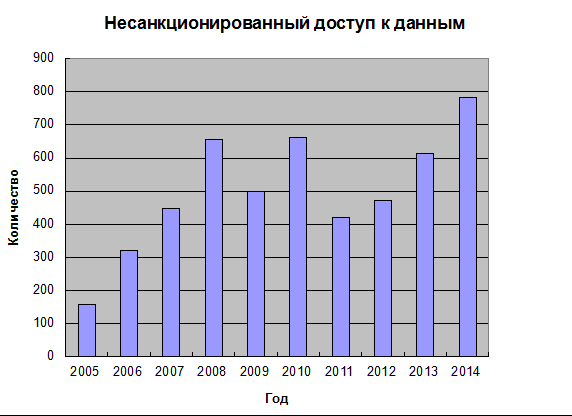
Also according to Have I been pwned? more than 175 million accounts were stolen. And it’s one thing when absolutely all the data leaked and completely different when only user accounts leaked. It is the latter that will be discussed in this publication.
Two-factor authentication
Two-factor authentication is essentially an industry standard that prevents the use of account leaks, since an attacker will not be able to log in as a stolen user without a second authentication. It also negates password cracking, eliminates the need for captcha and makes some other things nicer depending on the application.
There are several known ways to implement two-factor authentication:
- Physical token.
- SMS gateway.
- Authenticator application.
Physical token
Pros:
- Very safe. If the authenticator is compromised, we will know about it instantly, because it must be stolen.
Minuses:
- Costs money.
- You need to have authentication with you if necessary.
- If you have B2C, you absolutely can’t give out a token to everyone.
SMS gateway
Pros:
- Safely.
Minuses:
- We do not control it. Absolutely. We don’t know what is going on inside, we don’t know what is happening with our database of numbers, we don’t know if a valid SMS was sent. What will happen when the service drops?
- Cost. I took prices with Clickatell . On average, sending one SMS costs $ 0.03. If you send 100 thousand messages a month, it will cost you $ 3,000 a month (~ 180 thousand rubles) or 36 thousand dollars a year (~ 2 million rubles). But what if you are a little larger? And 1 million messages are sent per month? It will cost you 30 thousand dollars a month (360 thousand per year). But what if you have grown to the size of hoo? And 10 million messages are sent per month? Then be so kind as to lay out 300 thousand dollars a month or 3 600 000 dollars a year (~ 216 million rubles). This is bad. If you put money out of your pocket, you could buy something interesting on it. If this is investor’s money, then you could use it to develop the project, new servers, increase salaries and other useful things.
- Your user should always have a phone with an authorized SIM card. All sorts of trouble ensues if the user changes the SIM card or loses the phone, or the battery runs out on it.
Authenticator application
Pros:
- Safely.
- We are in full control of it.
Minuses:
- Sometimes the total cost of developing and maintaining such an application is more expensive than using an SMS gateway.
- Your user always needs to have an authorized device with him.
3rd party authenticator application
For example, Google Authenticator or Microsoft Authenticator.
Pros:
- Safely.
Minuses:
- We do not control it and do not know what is happening inside.
- What will happen to this application tomorrow? Would they kill him as unnecessary?
- Your user always needs to have an authorized device with him. At the same time, it must support a third-party authenticator.
Another authentication (the Sign)
I called her the Sign. The user does not need anything at all except his email and access to mail with him.
It looks like this:
- User enters email in our service.
- We add it to the database if it was not there.
- We send the user a letter with the generated authorization link and code, if authorization is in the application.
- The user logs in using the link or using the code.
- ...
- Profit!
Process Diagram:

Pros:
- Safely.
- The user does not need to think about the password or give us access to his social network profile or not. If we first made a landing to check the popularity of the idea, then then it will not be difficult for us to send authorization links to the user and not fool them with authorization.
- We fully control and monitor the entire process.
- The cost of the solution is extremely low.
- It works on any device.
- The user does not need an authorized device at all, only access to mail.
- Work it out once and forget it. Engage in support only. But you already support the service of sending email messages in your project, right?
- In order to enter the code in the application, you need to make as much effort as with SMS.
Minuses:
- The user needs access to the email account.
Conclusion
This process is still a concept and is not used in live applications. He is not tested by time. Since exactly one head came up with it. It is not tested by criticism. But I did not find possible attacks and generally significant minuses. Therefore, he submitted for public discussion. I would like to understand whether the use of such authorization restricts anything other than the fact that it is not widely used.
