New backdoor of the TeleBots cyber group: the first proof of the link between Industroyer and NotPetya
A study of the new backdoor of the TeleBots cyber group behind the NotPetya epidemic revealed a significant similarity between the code and the main backdoor of Industroyer, which confirms the interconnection previously rumored.

Among the largest cyber incidents of recent years are attacks on Ukrainian energy enterprises and the epidemic of the NotPetya coder . In the post we will look at the relationship between these events.
The first in the history of massive power outages caused by cyber attacks occurred in December 2015, its cause is the BlackEnergy malware complex . ESET specialists monitored the activity of the ART group using BlackEnergy, both before and after this event. After the blackout of 2015, the group seems to have turned to active work with BlackEnergy and evolved into what we now call TeleBots .
Here it should be noted that, speaking of the ART group, we mean the general technical indicators: code similarity, common network (C & C) infrastructure, chains of execution of malicious programs, etc. As a rule, we do not directly participate in the investigation and identification of developers or operators. The term “ART group” is not clearly defined and is often used to characterize malware parameters. For these reasons, we refrain from assumptions about the source of attacks, national or state identity of the attackers.
In any case, we found a connection between the attacks of BlackEnergy (aimed at the Ukrainian energy companies, as well as other industries and high-ranking facilities) and the campaigns of the TeleBots group (mainly against the Ukrainian financial sector).
In June 2017, companies around the world suffered from Diskcoder.C wiper (better known as Petya / NotPetya) - the massive nature of the infection seems to have been a side effect. Studying the incident, we found out that companies infected with the backdoor of the TeleBots group became the “zero patient” of this epidemic as a result of the compromise of the popular MEDoc accounting software in Ukrainian companies.
The question is, what does Industroyer have to do with this story .- a complex malicious complex that caused the blackout in Kiev in December 2016. Immediately after the publication of the ESET report, some security companies and the media suggested that Industroyer also developed the BlackEnergy / TeleBots group (sometimes also called Sandworm). However, evidence to date has not been provided.
In April 2018, we recorded a new activity of the TeleBots group - an attempt to deploy a new Win32 / Exaramel backdoor . Our analysis showed that this backdoor is an improved version of the main backdoor of Industroyer - which was the first proof.

The Win32 / Exaramel backdoor is initially installed using a dropper. According to the dropper metadata, the backdoor is compiled into Microsoft Visual Studio just before being deployed to a particular compromised computer.
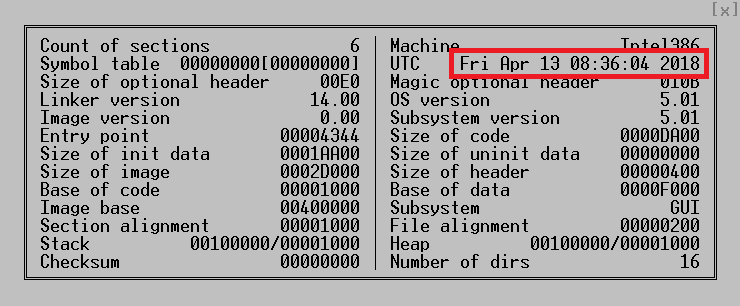
Figure 1. Win32 / Exaramel backdoor PE dropper timestamp
After execution, the dropper places the Win32 / Exaramel binary file in the Windows system directory and starts the Windows service with the name
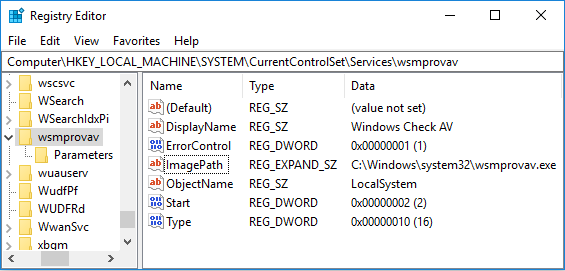
Figure 2. Windows service registry settings created by the Win32 / Exaramel backdoor
In addition, the dropper writes the backdoor configuration to the Windows registry in XML format.
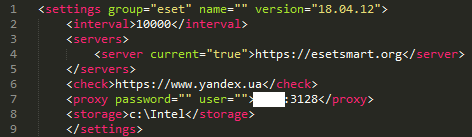
Figure 3. Win32 / Exaramel XML configuration
The configuration consists of several blocks:
- Interval - time in milliseconds, used for the Sleep function
- Servers - list of command servers (C & C)
- Check - web site used to determine whether the host has Internet access
- Proxy - proxy server in the host's network
- Storage - the path used to store files for exfiltration
As can be seen from the first configuration line, attackers group targets based on the antivirus products used. A similar approach is used in the Industroyer complex - in particular, some Industroyer backdoors were also disguised as antivirus related service (deployed under the name
Another interesting fact is that the backdoor uses C & C servers whose domain names mimic domains belonging to ESET. In addition to
After launching, the backdoor establishes a connection with the C & C server and receives commands for execution on the system. Below is a list of available commands:
- Starting the process
- Starting the process from a specific Windows user
- Writing data to a file at a specified path
- Copying a file to the storage subdirectory (Load file)
- Execute a shell command
- Execute a shell command from a specific Windows user
- Run VBS code using the
command loop code and the implementation of the first six commands in Win32 / Exaramel is very similar to the backdoor from the Industroyer software.

Figure 4. Comparison of decompiled Win32 / Exaramel backdoors (left) and Win32 / Industroyer (right)
Both families of malware use a report file to store the output of executed shell commands and running processes. In the case of the Win32 / Industroyer backdoor, the report file is stored in a temporary folder with a random name; in Win32 / Exaramel, the report file is called
To redirect standard output (stdout) and standard error (stderr) to the report file, both backdoors set the parameters

Figure 5. Comparing the Win32 / Exaramel and Win32 / Industroyer decompiled code, respectively.
If the malware operators want to exfiltrate the files from the victim's computer, it is enough to copy these files to the storage path subdirectory
The main difference between the backdoor Industroyer and the new backdoor TeleBots is that the latter uses the XML format for communication and configuration instead of the custom binary format.
Together with Exaramel, the TeleBots group uses some of the old tools, including a password theft tool (internal name is CredRaptor or PAI) and slightly modified Mimikatz.
The improved CredRaptor password theft tool, used only by this group since 2016, has been improved. Unlike previous versions, it collects saved passwords not only from browsers, but also from Outlook and a number of FTP clients. Below is a list of supported applications:
- BitKinex FTP
- BulletProof FTP Client
- Classic FTP
- CoffeeCup
- Core FTP
- Cryer WebSitePublisher
- CuteFTP
- FAR Manager
- FileZilla
- FlashFXP
- Frigate3
- FTP Commander
- FTP Explorer
- FTP Navigator
- Google Chrome
- Internet Explorer 7 - 11
- Mozilla Firefox
- Opera
- Outlook 2010, 2013, 2016
- SmartFTP
- SoftX FTP Client
- Total Commander
- TurboFTP
- Windows Vault
- WinSCP
- WS_FTP Client
Refinements allow attackers to collect data from webmaster accounts for websites and from servers in the internal infrastructure. Having access to such servers, you can install additional backdoors. Quite often, these servers have an operating system different from Windows, so attackers have to adapt backdoors.
During incident response activities, we discovered the TeleBots Linux backdoor — Linux / Exaramel.A .
The backdoor is written in the Go programming language and compiled as a 64-bit ELF binary file. Attackers can deploy the backdoor in the selected directory under any name.
If the backdoor is executed by attacking with the string 'none' as a command line argument, it tries to use persistence mechanisms to automatically start after a reboot. If the backdoor is not running as root, it uses the file
Depending on the result, the backdoor uses the following hard-coded locations to ensure persistence (hereinafter, Init system and its location):
sysvinit- /etc/init.d/syslogd
upstart - /etc/init/syslogd.conf
systemd - /etc/systemd/system/syslogd.service
During startup, the backdoor tries to open a configuration file that is stored in the same directory as the backdoor under the name
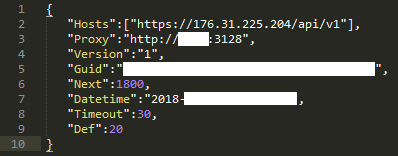
Figure 6. Decrypted Linux backdoor JSON configuration / Exaramel The
backdoor connects to a hard-coded C & C (default is 176.31.225 [.] 204 in the pattern we saw) or to the C & C server specified in the configuration file in value
App.Update- update to the new version of
App.Delete - self-
deletion from the App.SetProxy system - set proxy server settings in the
App.SetServer configuration - update the C & C server in the
App.SetTimeout configuration - set the timeout value (intervals between connections to the C & C server)
IO .WriteFile - download file from remote server
IO.ReadFile - upload file from local disk to C & C server
OS.ShellExecute - execute shell command
The discovery of Exaramel shows that the TeleBots group remains active in 2018, and the attackers continue to improve tactics and tools.
The significant similarity between the Win32 / Exaramel code and the Industroyer main backdoor is the first publicly presented evidence linking Industroyer with the TeleBots group and, therefore, with NotPetya and BlackEnergy cyber campaigns. Establishing a connection between the sources of cyber attacks, we should take into account the possibility of error or deliberate deception, but in this case we consider this unlikely.
It is worth noting that Win32 and Linux versions of Exaramel backdoor were found in an organization that is not relevant to the industry. ESET specialists reported the finding to the investigative authorities of Ukraine, due to which the attack was promptly localized and prevented.
ESET continues to monitor the activity of this cyber group.
Backdoor Win32 / Exaramel cybergroup TeleBots A tool to steal passwords Mimikatz Linux / Exaramel

Among the largest cyber incidents of recent years are attacks on Ukrainian energy enterprises and the epidemic of the NotPetya coder . In the post we will look at the relationship between these events.
The first in the history of massive power outages caused by cyber attacks occurred in December 2015, its cause is the BlackEnergy malware complex . ESET specialists monitored the activity of the ART group using BlackEnergy, both before and after this event. After the blackout of 2015, the group seems to have turned to active work with BlackEnergy and evolved into what we now call TeleBots .
Here it should be noted that, speaking of the ART group, we mean the general technical indicators: code similarity, common network (C & C) infrastructure, chains of execution of malicious programs, etc. As a rule, we do not directly participate in the investigation and identification of developers or operators. The term “ART group” is not clearly defined and is often used to characterize malware parameters. For these reasons, we refrain from assumptions about the source of attacks, national or state identity of the attackers.
In any case, we found a connection between the attacks of BlackEnergy (aimed at the Ukrainian energy companies, as well as other industries and high-ranking facilities) and the campaigns of the TeleBots group (mainly against the Ukrainian financial sector).
In June 2017, companies around the world suffered from Diskcoder.C wiper (better known as Petya / NotPetya) - the massive nature of the infection seems to have been a side effect. Studying the incident, we found out that companies infected with the backdoor of the TeleBots group became the “zero patient” of this epidemic as a result of the compromise of the popular MEDoc accounting software in Ukrainian companies.
The question is, what does Industroyer have to do with this story .- a complex malicious complex that caused the blackout in Kiev in December 2016. Immediately after the publication of the ESET report, some security companies and the media suggested that Industroyer also developed the BlackEnergy / TeleBots group (sometimes also called Sandworm). However, evidence to date has not been provided.
In April 2018, we recorded a new activity of the TeleBots group - an attempt to deploy a new Win32 / Exaramel backdoor . Our analysis showed that this backdoor is an improved version of the main backdoor of Industroyer - which was the first proof.

Win32 / Exaramel backdoor analysis
The Win32 / Exaramel backdoor is initially installed using a dropper. According to the dropper metadata, the backdoor is compiled into Microsoft Visual Studio just before being deployed to a particular compromised computer.

Figure 1. Win32 / Exaramel backdoor PE dropper timestamp
After execution, the dropper places the Win32 / Exaramel binary file in the Windows system directory and starts the Windows service with the name
wsmproav“Windows Check AV”. The file name and description of the Windows service is hard coded in the dropper. 
Figure 2. Windows service registry settings created by the Win32 / Exaramel backdoor
In addition, the dropper writes the backdoor configuration to the Windows registry in XML format.

Figure 3. Win32 / Exaramel XML configuration
The configuration consists of several blocks:
- Interval - time in milliseconds, used for the Sleep function
- Servers - list of command servers (C & C)
- Check - web site used to determine whether the host has Internet access
- Proxy - proxy server in the host's network
- Storage - the path used to store files for exfiltration
As can be seen from the first configuration line, attackers group targets based on the antivirus products used. A similar approach is used in the Industroyer complex - in particular, some Industroyer backdoors were also disguised as antivirus related service (deployed under the name
avtask.exe) and used the same approach to group formation. Another interesting fact is that the backdoor uses C & C servers whose domain names mimic domains belonging to ESET. In addition to
esetsmart[.]orgthe above configuration, we found a similar domain um10eset[.]netthat was used by the recently discovered Linux version of the TeleBots malware. It is important to note that these monitored offensive servers are not related to ESET's legitimate network infrastructure.. At present, we have not found that Exaramel uses domains that mimic the infrastructure of other information security companies. After launching, the backdoor establishes a connection with the C & C server and receives commands for execution on the system. Below is a list of available commands:
- Starting the process
- Starting the process from a specific Windows user
- Writing data to a file at a specified path
- Copying a file to the storage subdirectory (Load file)
- Execute a shell command
- Execute a shell command from a specific Windows user
- Run VBS code using the
MSScriptControl.ScriptControl.1command loop code and the implementation of the first six commands in Win32 / Exaramel is very similar to the backdoor from the Industroyer software.

Figure 4. Comparison of decompiled Win32 / Exaramel backdoors (left) and Win32 / Industroyer (right)
Both families of malware use a report file to store the output of executed shell commands and running processes. In the case of the Win32 / Industroyer backdoor, the report file is stored in a temporary folder with a random name; in Win32 / Exaramel, the report file is called
report.txt, and its path to the repository is specified in the backdoor configuration file. To redirect standard output (stdout) and standard error (stderr) to the report file, both backdoors set the parameters
hStdOutputand hStdErrorthe file descriptor of the report. This is another similarity between these malware families.
Figure 5. Comparing the Win32 / Exaramel and Win32 / Industroyer decompiled code, respectively.
If the malware operators want to exfiltrate the files from the victim's computer, it is enough to copy these files to the storage path subdirectory
dataspecified in the configuration. Before establishing a new connection with the C & C server, the backdoor will automatically compress and encrypt these files before sending them. The main difference between the backdoor Industroyer and the new backdoor TeleBots is that the latter uses the XML format for communication and configuration instead of the custom binary format.
Malicious password theft tools.
Together with Exaramel, the TeleBots group uses some of the old tools, including a password theft tool (internal name is CredRaptor or PAI) and slightly modified Mimikatz.
The improved CredRaptor password theft tool, used only by this group since 2016, has been improved. Unlike previous versions, it collects saved passwords not only from browsers, but also from Outlook and a number of FTP clients. Below is a list of supported applications:
- BitKinex FTP
- BulletProof FTP Client
- Classic FTP
- CoffeeCup
- Core FTP
- Cryer WebSitePublisher
- CuteFTP
- FAR Manager
- FileZilla
- FlashFXP
- Frigate3
- FTP Commander
- FTP Explorer
- FTP Navigator
- Google Chrome
- Internet Explorer 7 - 11
- Mozilla Firefox
- Opera
- Outlook 2010, 2013, 2016
- SmartFTP
- SoftX FTP Client
- Total Commander
- TurboFTP
- Windows Vault
- WinSCP
- WS_FTP Client
Refinements allow attackers to collect data from webmaster accounts for websites and from servers in the internal infrastructure. Having access to such servers, you can install additional backdoors. Quite often, these servers have an operating system different from Windows, so attackers have to adapt backdoors.
During incident response activities, we discovered the TeleBots Linux backdoor — Linux / Exaramel.A .
Linux / Exaramel backdoor analysis
The backdoor is written in the Go programming language and compiled as a 64-bit ELF binary file. Attackers can deploy the backdoor in the selected directory under any name.
If the backdoor is executed by attacking with the string 'none' as a command line argument, it tries to use persistence mechanisms to automatically start after a reboot. If the backdoor is not running as root, it uses the file
crontab. However, if it is running as root, it supports various Linux systems init. It determines which initsystem is currently used by executing the command: strings /sbin/init | awk 'match($0, /(upstart|systemd|sysvinit)/){ print substr($0, RSTART, RLENGTH);exit; }'Depending on the result, the backdoor uses the following hard-coded locations to ensure persistence (hereinafter, Init system and its location):
sysvinit- /etc/init.d/syslogd
upstart - /etc/init/syslogd.conf
systemd - /etc/systemd/system/syslogd.service
During startup, the backdoor tries to open a configuration file that is stored in the same directory as the backdoor under the name
config.json. If the configuration file does not exist, a new file is created. The configuration is encrypted using the key s0m3t3rr0r and the RC4 algorithm. 
Figure 6. Decrypted Linux backdoor JSON configuration / Exaramel The
backdoor connects to a hard-coded C & C (default is 176.31.225 [.] 204 in the pattern we saw) or to the C & C server specified in the configuration file in value
Hosts. Communications are carried out via HTTPS. The backdoor supports the following commands: App.Update- update to the new version of
App.Delete - self-
deletion from the App.SetProxy system - set proxy server settings in the
App.SetServer configuration - update the C & C server in the
App.SetTimeout configuration - set the timeout value (intervals between connections to the C & C server)
IO .WriteFile - download file from remote server
IO.ReadFile - upload file from local disk to C & C server
OS.ShellExecute - execute shell command
Conclusion
The discovery of Exaramel shows that the TeleBots group remains active in 2018, and the attackers continue to improve tactics and tools.
The significant similarity between the Win32 / Exaramel code and the Industroyer main backdoor is the first publicly presented evidence linking Industroyer with the TeleBots group and, therefore, with NotPetya and BlackEnergy cyber campaigns. Establishing a connection between the sources of cyber attacks, we should take into account the possibility of error or deliberate deception, but in this case we consider this unlikely.
It is worth noting that Win32 and Linux versions of Exaramel backdoor were found in an organization that is not relevant to the industry. ESET specialists reported the finding to the investigative authorities of Ukraine, due to which the attack was promptly localized and prevented.
ESET continues to monitor the activity of this cyber group.
Compromise Indicators (IoCs)
Detection by ESET products
Win32/Exaramel trojan
Win32/Agent.TCD trojan
Linux/Agent.EJ trojan
Linux/Exaramel.A trojan
Win32/PSW.Agent.OEP trojan
Win32/RiskWare.Mimikatz.Z application
Win64/Riskware.Mimikatz.AI applicationHashi SHA-1
Backdoor Win32 / Exaramel cybergroup TeleBots A tool to steal passwords Mimikatz Linux / Exaramel
65BC0FF4D4F2E20507874F59127A899C26294BC7
3120C94285D3F86A953685C189BADE7CB575091DF4C4123849FDA08D1268D45974C42DEB2AAE3377
970E8ACC97CE5A8140EE5F6304A1E7CB56FA3FB8
DDDF96F25B12143C7292899F9D5F42BB1D27CB20
64319D93B69145398F9866DA6DF55C00ED2F593E
1CF8277EE8BF255BB097D53B338FC18EF0CD0B42
488111E3EB62AF237C68479730B62DD3F52F8614458A6917300526CC73E510389770CFF6F51D53FC
CB8912227505EF8B8ECCF870656ED7B8CA1EB475F74EA45AD360C8EF8DB13F8E975A5E0D42E58732C & C Servers
um10eset[.]net (IP: 176.31.225.204)
esetsmart[.]org (IP: 5.133.8.46)