Site Security Audit - Identifying Risks and Threats

Site security audit (checking the site for vulnerabilities) is a series of procedures aimed at ensuring the stable operation of a web resource, data security and reducing risks.
It's no secret that the economic situation is now dictating new rules, including in the competition. If before the “war of technologies”, cyber espionage and destructive actions were mainly the lot of large corporations or entire states, now these methods are quite successfully used in small and medium-sized businesses.
We’ll leave the sites of offline companies aside, and today we’ll talk about commercial websites whose main income is related to Internet activities.
Site Security Audit- This is a set of works to identify errors in the site code and server software that the attackers who have taken advantage of can attack and hack the site.
The motivation used by attackers can be different - this is bragging, and the search for benefits both for yourself and working on an “order”.
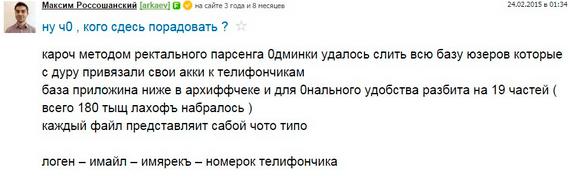
Of the latest “high-profile” examples - hacking freelance exchanges FL.ru habrahabr.ru/post/251487
screenshot of a cracker message on behalf of one of the administrators
Here the resource has clearly suffered reputational damage, user loyalty is reduced. It may be difficult to attract new users: www.google.ru/search?ie=UTF-8&hl=en&q=FL.ru
As a result of GOOGLE search results at the request of FL.RU, the second is the topic on Habré about draining the user base.
What would the security audit of the FL.RU exchange give - the selection of passwords for the accounts of resource administrators would help to identify these accounts. Additional recommendations and rules for their implementation would help to avoid such an annoying oversight. The lack of restriction of access to critical functionality (user accounts) from an untrusted IP address only aggravated the situation.
Reputational risks of hacking a company's website will naturally affect the company's profitability. But there is also a direct threat of theft of data of value to the company. The company's website related to online activities - online store, electronic exchange and so on. - the main tool for making a profit - often contains a database of customers, all the more valuable if the service involves long-term work with the client, repeated purchases, etc.
Also, the manipulation of payment data, fraudulent transactions in the systems of input / output of funds or payment systems can cause great damage to the company.
Attackers attacking a site can be conditionally divided into two types:
1. We take everything that lies badly.
Attackers of this kind try to gain access to a large number of sites, use primitive techniques, "make noise in the logs." Typically, these kinds of subjects scan the site (s) with popular vulnerability scanners or look for vulnerable CMS for a specific exploit. They may be interested in both the user base and the banal iframe on the so-called. exploit-pack.
the search for accomplices to commit an offense under article 273 of the Criminal Code
A timely security audit of web applications will help to identify vulnerable components and problem areas of the site. Recommendations will help you be prepared to repel hacker attacks.
2. We attack a specific target.
Attackers of this kind are usually motivated to obtain certain data or destroy it:
ads on “hacker” forums
In this case, the attacker will not limit himself to passive methods - most likely he will attack the site until he gets the desired result, using all possible combinations of attack vectors.
A comprehensive security audit, which usually includes the following actions, can help significantly increase site security.
- Search for vulnerabilities in server components;
- Search for vulnerabilities in the web environment of the server;
- Check for remote execution of arbitrary code;
- Check for injections (code injection);
- Attempts to bypass the web resource authentication system;
- Checking the web resource for the presence of "XSS" / "CSRF" vulnerabilities;
- Attempts to intercept privileged accounts (or sessions of such accounts);
- Attempts to make Remote File Inclusion / Local File Inclusion;
- Search for components with known vulnerabilities;
- Check for redirection to other sites and open redirects;
- Scan directories and files using brute force and “google hack”;
- Analysis of search forms, registration forms, authorization forms, etc .;
- Checking the resource for the possibility of openly receiving confidential and secret information;
- Attacks of the class "race condition";
- Embedding XML Entities
- Password selection.
Site security audit is a proactive measure that allows you to get an adequate assessment of the security of a company's resource, complete information about the vulnerabilities found, possible attack scenarios and recommendations for their elimination. This, in fact, is not an event, but an ongoing process to ensure the safety of the business processes of the company’s site, preserve business reputation, economic growth and business development.
Do not wait until your site is attacked by cybercriminals - order a comprehensive security audit of the site from professionals.
Be secure!