Company network and MitM. Part 1
Intercept confidential information? Get unauthorized access to various applications and systems? Disrupt normal operation? All this and more are carried out by attacks like Man in the Middle.
Today we begin a series of articles devoted to man-in-the-middle attacks (and a number of related ones) on typical protocols and transmission channels found in almost any company. To begin, consider the basic levels: physical and channel.
Interested? Welcome under cat.
Man in the Middle (aka “man in the middle” attack, also known as “mediator attack”) is generally a type of attack aimed at breaching confidentiality and, in some cases, integrity of information. It is possible to describe schematically the “typical” attack as follows:

The main lines in the figure are both orange and red lines. Orange - the estimated data path, red - the actual. The transmission medium or protocol in this case is unimportant. Alice can be, for example, a Wi-Fi client, and Bob can be a Wi-Fi access point. Anyway, there is always a third party that performs any actions with the transmitted information.
Why did we miss the transmission channel? Because all levels of the OSI network model are subject to such an attack in one way or another. Further we will confirm it.
Let us proceed to consider the attack from the first and second levels of OSI - physical and channel.
Copper
Let's start with the simplest thing - picking data from a twisted pair. This is not exactly MitM, this is classic sniffing, but in this case it is a “prerequisite” for more serious attacks. In fact, to remove data from a twisted pair, say, 100Base-T, it is enough to have just an extra router on which to install any DD-WRT / OpenWRT or any other analogue. Some time ago, a similar thing was mentioned here .
A more reliable way is to use special devices. But he has flaws:
Everything leads to the fact that such sniffing may not bring the desired results to the attacker. A more “flexible” connection is required, that is, “embedding” into the data line. For example, like this, a little brazenly:

This method has many disadvantages. For example, it is easy to detect it in the presence of various means of protection or suspicious eyes suspicious of the emergence of something new in the workplace. But he has an advantage: full control and the possibility of modifying the transmitted data. Let's model attack in real life. It will take 2 things: my working machine, on which this text is written, my laptop with Archon board, although any Linux distribution should come up. The connections “my working machine” - “laptop” and “laptop” - “local network” will be made over a cable, for which a USB network adapter is connected to the laptop. We will use brctl to configure the bridge , although this functionality is declared even by NetworkManager .
Configure the bridge:
If you want to get an IP address at the same time, you just need to set some dhclient on br0, or set up a static IP with your hands (# ip ad add XXXX / X dev br0).
So, the bridge interface is created on the laptop, a computer is connected to the USB interface, the main interface goes to the local area network. Run any software to intercept the traffic (for convenience, use Wireshark to GUI) and observe the following: Figure 1. Wireshark in As you can see, here the entire dump car traffic to the address 192.168.139.206 (for the test, I created a test network). In the current configuration (without MAC-pinning
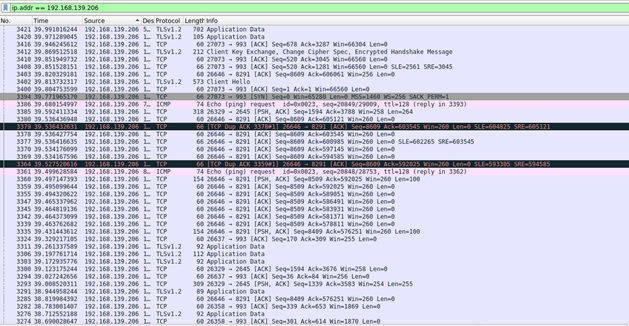
, for example) no one will ever notice my online presence. This attack allows you to get a lot of information, including logins / passwords, for example, for the site diary.ru : Figure 2. Ooops In fact, everything is a little more complicated. diary.ru is one of the rare sites that do not redirect the user to encrypted HTTPS. Dealing with HTTPS is harder than open traffic. And most of the traffic I caught is encrypted, which is actually good for the user, but not very good for me at the moment. How to protect yourself? There are several options, each with its own characteristics:

The question arises: what to do if the computer you want to access is, for example, indoors, and the cable is under cameras or hidden? Nothing complicated, just resort to the simplest spoofing attacks. When requesting the MAC address of a specific node, the attacking node starts “spamming” the network with ARP packets, in which its MAC is specified as the required address, thereby causing the attacker to connect to our host.
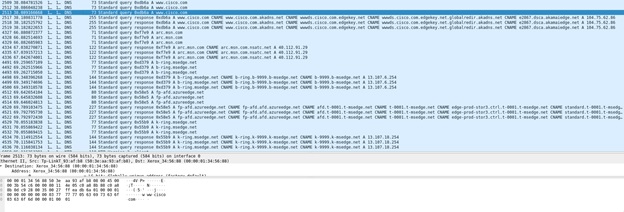
You must first select a target. In my case it will be my colleague. Now use the very ancient, but quite workable ettercap. We will determine the IP address of a colleague in any way, further we will designate the target of the attack. For example, I want to find out which DNS my colleague was looking for. After that in ettercap I drive in 2 IP addresses: the address of the DNS server and, in fact, the address of the victim. And ... Figure 3. We catch DNS queries It is clear that my colleague is looking for information on the Cisco website, and at the same time his system sends "service" requests to identify various MS sites. There is some good news. A large list of equipment supports protection against ARP-spoofing, which can negate such attacks. And if the company uses SOC or SIEM, then you can try to find the attacker in hot pursuit. Optics Fiber-optic communication lines are another, extremely common communication channel in any company. What's up with MitM protection?
The situation is twofold. If we take the simplest cable without special protective reinforced shells, then for the simplest sniffing it is enough to bend it. A special device hangs on a bend. Part of the light goes beyond the cable to our device, from which we collect the entire dump.
It is good that most of the traffic is still encrypted. What to do if not? In fact, it is difficult to defend. The easiest way to isolate optics in such a way as to get close to it was difficult. Another way is to use a more expensive “protected” cable, which includes special protection measures that allow you to detect a broken cable sheath. But with proper skill, you can connect to it, and re-laying the cable is often an extremely unpleasant affair. An effective way is to use special equipment that will respond to changes in the signal level when a fiber bend appears. The price of the issue is high. Well, perhaps the best solution is to use encryption of the transmitted traffic.
If we want to somehow influence traffic, then everything is more complicated. The most effective way is a tie-in, in which special equipment is built in the middle. The disadvantage of this method is that we need for some time (rather large) to cut the cable with all the ensuing consequences, which can confuse the security men in the company. But if successful, we will, in most cases, be able to influence a large amount of traffic, since fiber is rarely laid up to the users computer. Most often, this is a data transmission channel, for example, between separate branches of companies.
An article covering a slightly larger number of fiber connection options is also available here .
And what about Wi-Fi?
And all the same and even easier! Consider for starters WPA2-PSK (connection by password). For the “secrecy” of the attack, it is important to fulfill one requirement: you need to know the real password, this will allow the devices on which the automatic connection to the network is configured to connect to the “malicious” network without any problems. So, we raise a Wi-Fi access point with an identical password and wait for connections. If you don’t want to wait, you can start sending out deauth packets, which will force users to disconnect from current access points, and for some of them, for which the malicious access point will be more powerful, force them to connect to you. To create a point, I used hostapd- the most powerful tool for creating various networks in various configurations. I connected the Wi-Fi interface to the br0 bridge so that users would not notice something amiss and could continue to work with services within the local network. We are waiting for some time and enjoy the results. Figure 4. We look at the iPhone dump of WPA2 Enterprise (with authentication through an external service, for example, RADIUS) from a security point of view is much better. If classic PSK may not even have access to the company's local network (for example, if the network is guest), then for Enterprise to work it is necessary to have access to an authentication server, which can use the same Windows NPS . In addition, a certificate with a private key is required for the access point to work.

which get quite problematic. You can, of course, release a self-signed one, but this can cause some problems, because in an ideal world the client device should verify this certificate. In general, it is possible to set up a similar access point and make clients connect to it, but with great reservations. Most likely, the attacker will still be able to catch.
How to protect a Wi-Fi network? Use WPA2 Enterprise (preferably with certificates) and configure client devices to check the certificate of the access point, then it will be much more difficult to emulate the Evil Twin access point. Be careful in setting up the authentication server. If it is permissible, use the capabilities of the existing equipment, for example, the Cisco Wireless Intrusion Prevention System, the essence of which in this case is to search for malicious access points and prevent different clients from connecting to them.
Let's summarize a little. As you can see, in one form or another, the most common data transmission channels are subject to MitM attacks. How to protect yourself?
But what if the attacker is a "trusted" person? An employee of the company who has legitimate access to the local network, but who has sabotage thoughts? What can he do to analyze encrypted traffic and, most importantly, how can you protect yourself from this? We will tell about this in the following articles, again returning to our DNS queries and to HTTPS traffic.

Today we begin a series of articles devoted to man-in-the-middle attacks (and a number of related ones) on typical protocols and transmission channels found in almost any company. To begin, consider the basic levels: physical and channel.
Interested? Welcome under cat.
Some theory
Man in the Middle (aka “man in the middle” attack, also known as “mediator attack”) is generally a type of attack aimed at breaching confidentiality and, in some cases, integrity of information. It is possible to describe schematically the “typical” attack as follows:

The main lines in the figure are both orange and red lines. Orange - the estimated data path, red - the actual. The transmission medium or protocol in this case is unimportant. Alice can be, for example, a Wi-Fi client, and Bob can be a Wi-Fi access point. Anyway, there is always a third party that performs any actions with the transmitted information.
Why did we miss the transmission channel? Because all levels of the OSI network model are subject to such an attack in one way or another. Further we will confirm it.
Let us proceed to consider the attack from the first and second levels of OSI - physical and channel.
Practice
Copper
Let's start with the simplest thing - picking data from a twisted pair. This is not exactly MitM, this is classic sniffing, but in this case it is a “prerequisite” for more serious attacks. In fact, to remove data from a twisted pair, say, 100Base-T, it is enough to have just an extra router on which to install any DD-WRT / OpenWRT or any other analogue. Some time ago, a similar thing was mentioned here .
A more reliable way is to use special devices. But he has flaws:
- With proper physical security (access control, video surveillance) and good awareness of employees about the actions, in case of the appearance of “suspicious” items, the risk of detecting such devices is extremely high.
- The attacker gains access only to the data that goes on the cable to which he connected. If the cable is connected to the guard’s booth, then most likely the offender will be able to watch images from a number of cameras and periodic Youtube sessions, but not financial data from SAP.
- Third, and most important is traffic encryption. In fact, now almost any server, any service works through TLS or uses any analog to encrypt the transmitted data. Without a key, we will not decrypt the transferred data. And in the case of using TLS 1.3 or TLS 1.2 on Diffie-Hellman algorithms, even this will not help.
Everything leads to the fact that such sniffing may not bring the desired results to the attacker. A more “flexible” connection is required, that is, “embedding” into the data line. For example, like this, a little brazenly:

This method has many disadvantages. For example, it is easy to detect it in the presence of various means of protection or suspicious eyes suspicious of the emergence of something new in the workplace. But he has an advantage: full control and the possibility of modifying the transmitted data. Let's model attack in real life. It will take 2 things: my working machine, on which this text is written, my laptop with Archon board, although any Linux distribution should come up. The connections “my working machine” - “laptop” and “laptop” - “local network” will be made over a cable, for which a USB network adapter is connected to the laptop. We will use brctl to configure the bridge , although this functionality is declared even by NetworkManager .
Configure the bridge:
# brctl addbr br0 // вместо br0 можем ввести любое удобное наименование# brctl addif br0 enp14s0 // здесь enp14s0 – мой внешний интерфейс, у вас, скорее всего, он будет называться иначе# brctl addif br0 enp0s20u4 // enp0s20u4 – интерфейс для подключения рабочего компьютераIf you want to get an IP address at the same time, you just need to set some dhclient on br0, or set up a static IP with your hands (# ip ad add XXXX / X dev br0).
So, the bridge interface is created on the laptop, a computer is connected to the USB interface, the main interface goes to the local area network. Run any software to intercept the traffic (for convenience, use Wireshark to GUI) and observe the following: Figure 1. Wireshark in As you can see, here the entire dump car traffic to the address 192.168.139.206 (for the test, I created a test network). In the current configuration (without MAC-pinning

, for example) no one will ever notice my online presence. This attack allows you to get a lot of information, including logins / passwords, for example, for the site diary.ru : Figure 2. Ooops In fact, everything is a little more complicated. diary.ru is one of the rare sites that do not redirect the user to encrypted HTTPS. Dealing with HTTPS is harder than open traffic. And most of the traffic I caught is encrypted, which is actually good for the user, but not very good for me at the moment. How to protect yourself? There are several options, each with its own characteristics:

- MAC-pinning does not help: MAC'i fake all and sundry. On the same Linux, you can use macchanger, and in Windows through the Device Manager;
- 802.1X authentication is a great thing. But there are a couple of nuances: in the mode of the simplest sniffing, it will not protect, since the attacker remains "invisible" to connect from the point of view of the switch, only the attacked device is connected to the network port. Another thing, in the case of the impact on traffic, the chance to reveal its presence is seriously increased, because now the network through the switch starts to emit traffic from you, to which various means of protection can react. Everything depends on the equipment used (SIEM or something similar) and the skills of the security men in the company;
- “User and entity behavior analytics” (UEBA) solutions will allow you to track something suspicious on the network. As in the case of 802.1X, with normal sniffing you remain invisible, but they will leave you behind when generating traffic. It is used not so often, and everything again depends on the skills of the security men.
The question arises: what to do if the computer you want to access is, for example, indoors, and the cable is under cameras or hidden? Nothing complicated, just resort to the simplest spoofing attacks. When requesting the MAC address of a specific node, the attacking node starts “spamming” the network with ARP packets, in which its MAC is specified as the required address, thereby causing the attacker to connect to our host.
You must first select a target. In my case it will be my colleague. Now use the very ancient, but quite workable ettercap. We will determine the IP address of a colleague in any way, further we will designate the target of the attack. For example, I want to find out which DNS my colleague was looking for. After that in ettercap I drive in 2 IP addresses: the address of the DNS server and, in fact, the address of the victim. And ... Figure 3. We catch DNS queries It is clear that my colleague is looking for information on the Cisco website, and at the same time his system sends "service" requests to identify various MS sites. There is some good news. A large list of equipment supports protection against ARP-spoofing, which can negate such attacks. And if the company uses SOC or SIEM, then you can try to find the attacker in hot pursuit. Optics Fiber-optic communication lines are another, extremely common communication channel in any company. What's up with MitM protection?

The situation is twofold. If we take the simplest cable without special protective reinforced shells, then for the simplest sniffing it is enough to bend it. A special device hangs on a bend. Part of the light goes beyond the cable to our device, from which we collect the entire dump.
It is good that most of the traffic is still encrypted. What to do if not? In fact, it is difficult to defend. The easiest way to isolate optics in such a way as to get close to it was difficult. Another way is to use a more expensive “protected” cable, which includes special protection measures that allow you to detect a broken cable sheath. But with proper skill, you can connect to it, and re-laying the cable is often an extremely unpleasant affair. An effective way is to use special equipment that will respond to changes in the signal level when a fiber bend appears. The price of the issue is high. Well, perhaps the best solution is to use encryption of the transmitted traffic.
If we want to somehow influence traffic, then everything is more complicated. The most effective way is a tie-in, in which special equipment is built in the middle. The disadvantage of this method is that we need for some time (rather large) to cut the cable with all the ensuing consequences, which can confuse the security men in the company. But if successful, we will, in most cases, be able to influence a large amount of traffic, since fiber is rarely laid up to the users computer. Most often, this is a data transmission channel, for example, between separate branches of companies.
An article covering a slightly larger number of fiber connection options is also available here .
And what about Wi-Fi?
And all the same and even easier! Consider for starters WPA2-PSK (connection by password). For the “secrecy” of the attack, it is important to fulfill one requirement: you need to know the real password, this will allow the devices on which the automatic connection to the network is configured to connect to the “malicious” network without any problems. So, we raise a Wi-Fi access point with an identical password and wait for connections. If you don’t want to wait, you can start sending out deauth packets, which will force users to disconnect from current access points, and for some of them, for which the malicious access point will be more powerful, force them to connect to you. To create a point, I used hostapd- the most powerful tool for creating various networks in various configurations. I connected the Wi-Fi interface to the br0 bridge so that users would not notice something amiss and could continue to work with services within the local network. We are waiting for some time and enjoy the results. Figure 4. We look at the iPhone dump of WPA2 Enterprise (with authentication through an external service, for example, RADIUS) from a security point of view is much better. If classic PSK may not even have access to the company's local network (for example, if the network is guest), then for Enterprise to work it is necessary to have access to an authentication server, which can use the same Windows NPS . In addition, a certificate with a private key is required for the access point to work.

which get quite problematic. You can, of course, release a self-signed one, but this can cause some problems, because in an ideal world the client device should verify this certificate. In general, it is possible to set up a similar access point and make clients connect to it, but with great reservations. Most likely, the attacker will still be able to catch.
How to protect a Wi-Fi network? Use WPA2 Enterprise (preferably with certificates) and configure client devices to check the certificate of the access point, then it will be much more difficult to emulate the Evil Twin access point. Be careful in setting up the authentication server. If it is permissible, use the capabilities of the existing equipment, for example, the Cisco Wireless Intrusion Prevention System, the essence of which in this case is to search for malicious access points and prevent different clients from connecting to them.
Instead of conclusion
Let's summarize a little. As you can see, in one form or another, the most common data transmission channels are subject to MitM attacks. How to protect yourself?
- use encryption; it is not so difficult and very effective;
- the introduction of any information systems (yes the same Wi-Fi) networks should not take place under the slogan “If only it worked!”, especially if really important information will circulate in the system, it is necessary to consider the process from the point of view of information security;
- use protective equipment or functional equipment used. Cisco WIPS, various IPS / IDS, UEBA, etc. This will allow if you do not stop the work of the attacker, then to detect it and take measures to catch the criminal.
But what if the attacker is a "trusted" person? An employee of the company who has legitimate access to the local network, but who has sabotage thoughts? What can he do to analyze encrypted traffic and, most importantly, how can you protect yourself from this? We will tell about this in the following articles, again returning to our DNS queries and to HTTPS traffic.
