Vulnerabilities of public terminals: how to crack a bike rental and clinic
This year Moscow was swept by a real bike fever. The number of bike rental stations was increased from 79 to 150, and 90 thousand people used the rental services. While two-wheeled friends are resting on their winter holidays, we’ll talk about the vulnerabilities of terminals for paying for bicycle rents, which compromised the security of personal data and electronic wallets of users, and also made us think about a new paradigm of attacks on corporate networks.

Payment and information terminals today operate on the streets, in shopping centers, at airports, in clinics, in the subway. Most of these devices run on Windows, in the mode of the so-called kiosk, which allows you to run on your computer one main full-screen application specified by the administrator. The functionality of the terminal expands significantly if you exit the kiosk mode in the operating system.
An application sometimes crashes on its own due to program errors and memory leaks, but there are also ways to minimize it on purpose. The oldest way is to perform a long press on the terminal screen until a context menu appears that emulates a right-click. Further penetration scenario is browser dependent. For example, you can get to the control panel from the Google Chrome context menu using the “Save As” command and the help section icon.
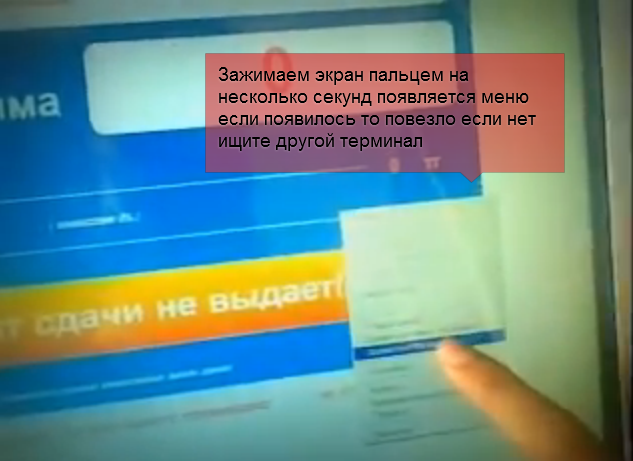
In some cases, an effective attack vector was a simple palpation of the screen in the lower left corner, allowing you to get to the taskbar and the Start menu, or simultaneously pressing several areas of the screen to minimize the main application.

To date, some of these loopholes are closed. But not all! Let's look at the situation from the perspective of a programmer. What can he lose sight of?
The developer will necessarily test the interactive parts of his full-screen application and check the data entered by the user so that the user does not have the opportunity to click something and “fall through” the operating system. But applications have become more complex, they use various technologies, including third-party code or widgets from other companies.
The application in the bicycle parking terminal is beautifully designed, the input of characters is tested ... But there was one bad “but” in it. In addition to the user registration form, the interface also has a help section with a map. It has a lot of useful information: where is this terminal and other bicycle parking lots, how to get to the nearest cafes, cinemas and other "points of interest". The map is based on the standard Google widget. There the error hid.
If you look closely, in the lower right part of the widget you can see the links “Report a problem”, “Confidentiality” and “Terms of use”. Click on any of them - and the standard Internet Explorer window appears.
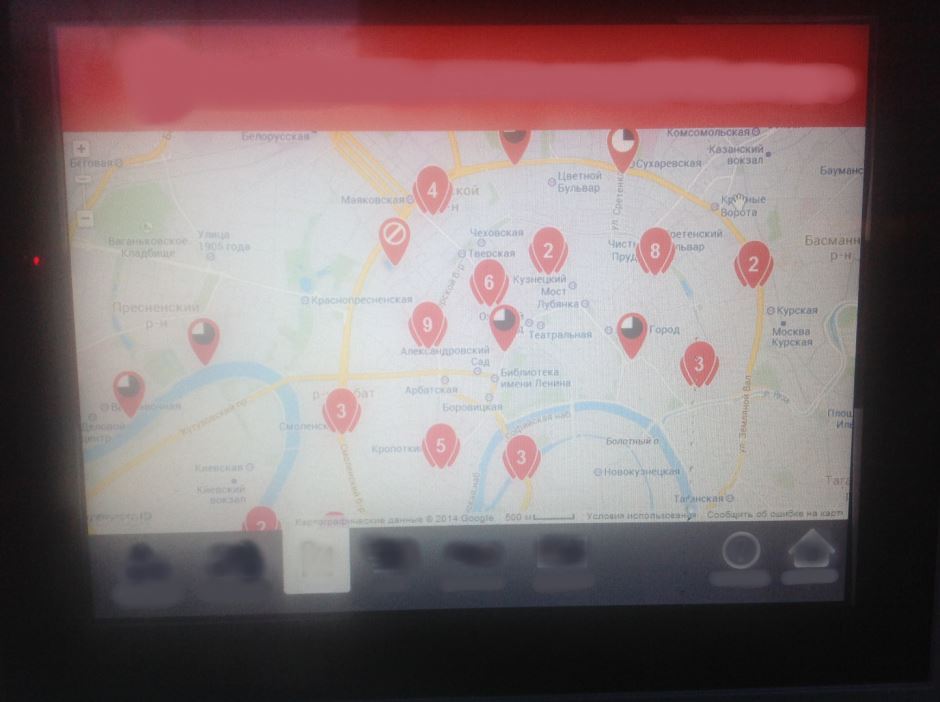
The browser window could be opened in a different way: by clicking the "Details" button when choosing the location of certain objects.

Half the job done.
The help section in Internet Explorer allows you to get to all elements and system programs of the OS. A little street magic, and we find ourselves in the "Accessibility Center" control panel, where we launch the on-screen keyboard. You can also directly get to the keyboard: go to "Explorer" by sequentially choosing Internet Explorer browser properties - the "General" tab, the "Options", "View Objects" buttons - and clicking on the Osk.exe application in the C: \ Windows \ System32 folder. Armed with a virtual keyboard, type cmd.exe and run the command line, where using the WHOAMI command we check the status in the system. We had administrator rights, so you can put on raspberry pants and host.


Full access to the Internet in the terminal was available, despite strict recommendations on restricting access to an external network for such devices. The intruder could go to the same exploit-db, download malicious applications to the device’s hard drive and run them, and also extract the administrator password using well-known password cracking programs (mimikatz, WCE, Fgdump, pwdump). It is worth adding that different bike parks with high probability could have the same administrator passwords.
What else could a cyber burglar do? Replace files in the system directory, elevate privileges, dump user data. Explicit flaws in the configuration left the intruder with space for completely dizzying maneuvers. Build a botnet, a mining pool, a cozy banner network with its own ads on the basis of the captured terminals ... In addition to the usual interception of entered personal data using a keylogger, an attacker could send a parking application to himself over the network, make changes to it (for example, add a field with the request to specify three-digit code CVV / CVV2) and set back. Users are unlikely, s immediately suspected anything, only a bike ride would have cost them dearly ...
In addition to friendly cartography, many terminals print checks, tickets, and this can also be used to penetrate the system. For example, in one of the organizations, when issuing an electronic queue ticket, a Windows interface with a print window appears momentarily. Under certain conditions, it will not be difficult to click on a printer, followed by access to the control panel. A similar window may appear if the built-in printer runs out of paper, the ink in the cartridge is dry, or the terminal itself solves Fermat's theorem and therefore works very slowly.

Over the past year, the author of this article and his colleagues have been faced with the unsafe work of e-government information, information kiosks at one of the Russian airports, aircraft entertainment systems , automated process control system (SCADA) remote terminals, and they also launched Angry Birds at an ATM. Recently, Russian clinics are actively equipped with terminals in which anyone can make an appointment with a doctor. Without proper attention to the safety of terminals, we run the risk of witnessing massive leaks of information, which already constitute a medical secret.

And these are the flowers! A distinctive feature of public terminals is that they are often connected to the same internal network and are trusted for the central server. In this case, the terminal administrator can have access to the internal resources of the parent company with important confidential data. Does a hacker need to break through firewalls and attack prevention systems if you can find an information kiosk on a quiet street with hippo-sized vulnerabilities and direct access to the main office server?
Imagine a modern high-tech airline, information kiosks which are located at various airports. Having gained full access to the terminal and cracked the server responsible for such devices (lack of a patch, vulnerability in the data exchange protocol), the attacker will check whether this server has a second interface connected to the airline’s internal network and there are ways to get into it. There are several ways to corporate secrets - VPN access, the same administrator passwords for terminal servers and the internal network, vulnerabilities in the mail web application for sending statistics or error reports.
The main trouble of public terminals with touch screens is minimizing the main application and getting the intruder into the Windows interface. Developers need to block pop-up menus with a long press on the screen (as when right-clicking) and exclude the call to the print window, from where you can enter the Windows control panel. We also recommend using embedded OS builds, which are devoid of a number of security flaws in standard versions - in particular, they do not use the desktop (but still, however, they do not protect against opening the same IE).
The mandatory minimum of events includes checking all links of a full-screen application and third-party widgets. If a new browser window opens when you go to the web address, you should disable this feature by editing the widget code and deleting the links. The main terminal application should always be on top of all Windows windows: various utilities (for example, Window On Top) can help.
From other wishes: unique passwords on different terminals, ordinary user privileges for the standard operating mode of the device, and a limited list of addresses when accessing an external network.
PS Incorrect configuration settings were professionally and promptly eliminated by the developers, and payment terminals of the Moscow city bike rental, according to a statementrepresentatives of the Moscow City Hall, continue their work in the winter.
PPS Thank you Denis Makrushin for help in conducting the study.
Author: Stanislav Merzlyakov

Payment and information terminals today operate on the streets, in shopping centers, at airports, in clinics, in the subway. Most of these devices run on Windows, in the mode of the so-called kiosk, which allows you to run on your computer one main full-screen application specified by the administrator. The functionality of the terminal expands significantly if you exit the kiosk mode in the operating system.
An application sometimes crashes on its own due to program errors and memory leaks, but there are also ways to minimize it on purpose. The oldest way is to perform a long press on the terminal screen until a context menu appears that emulates a right-click. Further penetration scenario is browser dependent. For example, you can get to the control panel from the Google Chrome context menu using the “Save As” command and the help section icon.

In some cases, an effective attack vector was a simple palpation of the screen in the lower left corner, allowing you to get to the taskbar and the Start menu, or simultaneously pressing several areas of the screen to minimize the main application.

To date, some of these loopholes are closed. But not all! Let's look at the situation from the perspective of a programmer. What can he lose sight of?
The developer will necessarily test the interactive parts of his full-screen application and check the data entered by the user so that the user does not have the opportunity to click something and “fall through” the operating system. But applications have become more complex, they use various technologies, including third-party code or widgets from other companies.
Bike Attack
The application in the bicycle parking terminal is beautifully designed, the input of characters is tested ... But there was one bad “but” in it. In addition to the user registration form, the interface also has a help section with a map. It has a lot of useful information: where is this terminal and other bicycle parking lots, how to get to the nearest cafes, cinemas and other "points of interest". The map is based on the standard Google widget. There the error hid.
If you look closely, in the lower right part of the widget you can see the links “Report a problem”, “Confidentiality” and “Terms of use”. Click on any of them - and the standard Internet Explorer window appears.

The browser window could be opened in a different way: by clicking the "Details" button when choosing the location of certain objects.

Half the job done.
The help section in Internet Explorer allows you to get to all elements and system programs of the OS. A little street magic, and we find ourselves in the "Accessibility Center" control panel, where we launch the on-screen keyboard. You can also directly get to the keyboard: go to "Explorer" by sequentially choosing Internet Explorer browser properties - the "General" tab, the "Options", "View Objects" buttons - and clicking on the Osk.exe application in the C: \ Windows \ System32 folder. Armed with a virtual keyboard, type cmd.exe and run the command line, where using the WHOAMI command we check the status in the system. We had administrator rights, so you can put on raspberry pants and host.


Operation scenarios
Full access to the Internet in the terminal was available, despite strict recommendations on restricting access to an external network for such devices. The intruder could go to the same exploit-db, download malicious applications to the device’s hard drive and run them, and also extract the administrator password using well-known password cracking programs (mimikatz, WCE, Fgdump, pwdump). It is worth adding that different bike parks with high probability could have the same administrator passwords.
What else could a cyber burglar do? Replace files in the system directory, elevate privileges, dump user data. Explicit flaws in the configuration left the intruder with space for completely dizzying maneuvers. Build a botnet, a mining pool, a cozy banner network with its own ads on the basis of the captured terminals ... In addition to the usual interception of entered personal data using a keylogger, an attacker could send a parking application to himself over the network, make changes to it (for example, add a field with the request to specify three-digit code CVV / CVV2) and set back. Users are unlikely, s immediately suspected anything, only a bike ride would have cost them dearly ...
Sly window print
In addition to friendly cartography, many terminals print checks, tickets, and this can also be used to penetrate the system. For example, in one of the organizations, when issuing an electronic queue ticket, a Windows interface with a print window appears momentarily. Under certain conditions, it will not be difficult to click on a printer, followed by access to the control panel. A similar window may appear if the built-in printer runs out of paper, the ink in the cartridge is dry, or the terminal itself solves Fermat's theorem and therefore works very slowly.


And if you dig deeper
Over the past year, the author of this article and his colleagues have been faced with the unsafe work of e-government information, information kiosks at one of the Russian airports, aircraft entertainment systems , automated process control system (SCADA) remote terminals, and they also launched Angry Birds at an ATM. Recently, Russian clinics are actively equipped with terminals in which anyone can make an appointment with a doctor. Without proper attention to the safety of terminals, we run the risk of witnessing massive leaks of information, which already constitute a medical secret.

And these are the flowers! A distinctive feature of public terminals is that they are often connected to the same internal network and are trusted for the central server. In this case, the terminal administrator can have access to the internal resources of the parent company with important confidential data. Does a hacker need to break through firewalls and attack prevention systems if you can find an information kiosk on a quiet street with hippo-sized vulnerabilities and direct access to the main office server?
Imagine a modern high-tech airline, information kiosks which are located at various airports. Having gained full access to the terminal and cracked the server responsible for such devices (lack of a patch, vulnerability in the data exchange protocol), the attacker will check whether this server has a second interface connected to the airline’s internal network and there are ways to get into it. There are several ways to corporate secrets - VPN access, the same administrator passwords for terminal servers and the internal network, vulnerabilities in the mail web application for sending statistics or error reports.
What to do
The main trouble of public terminals with touch screens is minimizing the main application and getting the intruder into the Windows interface. Developers need to block pop-up menus with a long press on the screen (as when right-clicking) and exclude the call to the print window, from where you can enter the Windows control panel. We also recommend using embedded OS builds, which are devoid of a number of security flaws in standard versions - in particular, they do not use the desktop (but still, however, they do not protect against opening the same IE).
The mandatory minimum of events includes checking all links of a full-screen application and third-party widgets. If a new browser window opens when you go to the web address, you should disable this feature by editing the widget code and deleting the links. The main terminal application should always be on top of all Windows windows: various utilities (for example, Window On Top) can help.
From other wishes: unique passwords on different terminals, ordinary user privileges for the standard operating mode of the device, and a limited list of addresses when accessing an external network.
PS Incorrect configuration settings were professionally and promptly eliminated by the developers, and payment terminals of the Moscow city bike rental, according to a statementrepresentatives of the Moscow City Hall, continue their work in the winter.
PPS Thank you Denis Makrushin for help in conducting the study.
Author: Stanislav Merzlyakov
