Mobile phones and total NSA surveillance: how it works
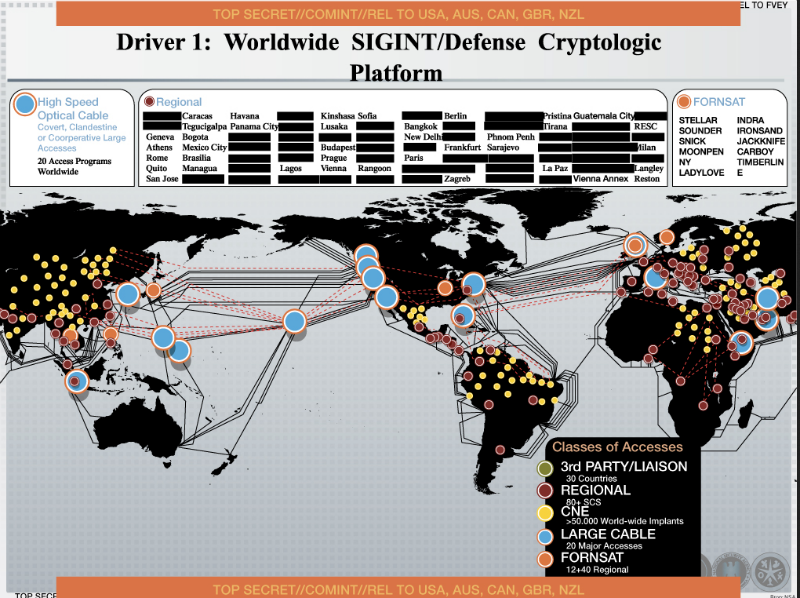
The name of Edward Snowden over the past two years regularly flashes in the news on the topic of information security. Thanks to the revelations of this former US intelligence officer, everyone has already heard that the National Security Agency (NSA) has the capabilities of total mobile surveillance of citizens. But how exactly this surveillance is arranged, few people know. In this review, we have gathered some details about the technologies that NSA uses - and not only that.
One of the first unpleasant news from Snowden was about undermining confidence in crypto protection technologies . As part of an NSA secret project called Bullrunit was possible to bypass many encryption systems - but not due to hacking, but due to the operation of bookmarks specially left by manufacturers at the request of the NSA. And in some cases, vendors are simply required to hand over encryption keys to the agency. Thus, many safety standards that were considered reliable and applied in large business and government organizations were discredited .

The other day, the development of this story appeared in the media - some details of the AuroraGold operationin which the NSA monitored telecom employees reading their electronic correspondence and internal documents. Already in May 2012, the NSA thus collected technical data on 70% of mobile networks around the world. The GSM Association, an international organization of telecoms, where recommendations on new communication standards are being developed, also came under the wiretap. The purpose of the AuroraGold operation is the same as that of the Bullrun project: implement bookmarks or learn about vulnerabilities that will help bypass the A5 / 3 encryption algorithm and other new protection technologies. Judging by documents from the Snowden archive, the NSA’s first attempts to crack the G4 were successful in 2010 - that is, even before this “safe” standard became widespread.
Another vector of NSA attacks is mobile OS and applications.. As it turned out, the special service has access to a lot of data on smartphones: lists of contacts and calls of subscribers, as well as their SMS and GPS data. For this, teams of hackers were assembled at the NSA, each of which was involved in hacking one of the popular OS. The publication of the German magazine Spiegel emphasizes that Blackberry was one of the first to be hacked, although traditionally it was considered more secure than iOS and Android.
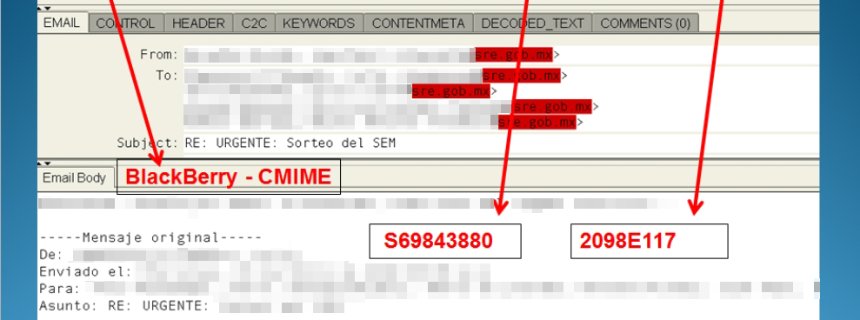
And of course, wiretapping capabilities have expanded significantly thanks to the development of the mobile application market . Many of them regularly transfer a significant amount of user data to third parties. Thus, for eavesdropping it is not necessary to crack the OS - it is enough to convince the user to install a “useful” mobile application.
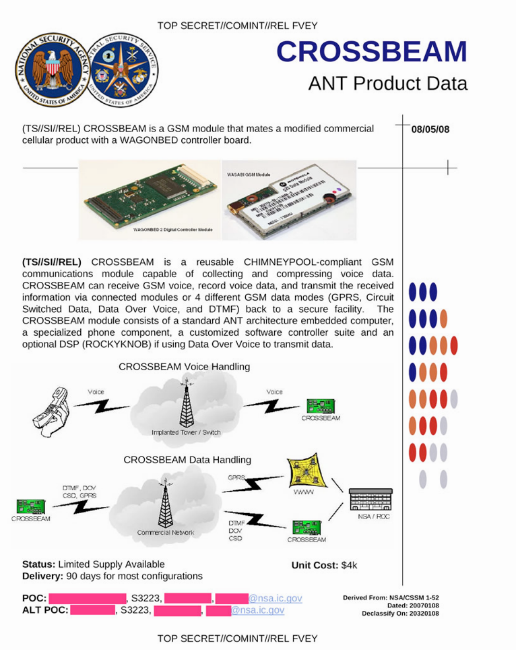
But even more opportunities for surveillance were found in the mobile networks themselves . The documents of Snowden found a description of the NSA spy directory - the Ant project , which has solutions for manipulating mobile networks for all occasions. It is not necessary to intercept data through vulnerable software - you can set bookmarks at the stage of manufacturing communication devices. For example, a compromised radio module for a phone:
Another option is fake base stations, with which you can intercept subscriber traffic and manipulate data on his phone:

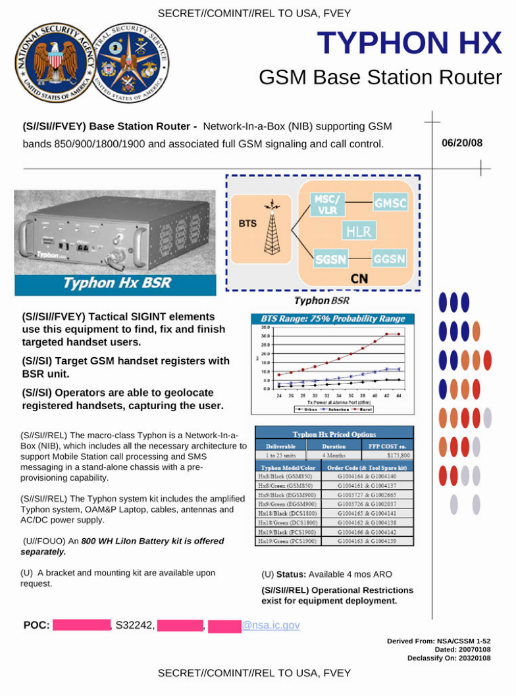
Or an entire cellular network in one box:
There is also a spectrum analyzer based on a Motorola L9 mobile phone , which allows you to record a radio spectrum for further analysis:

Location using a cellular network is pretty rough. There is a separate portable tool in place to accurately search for a victim:

Of course, the mere existence of such a catalog of devices does not mean that someone is already using them for total surveillance. However, after the publication of the catalog, evidence of practical application began to appear.
In September 2014, a suspicious IZD-Tower rooftop was discovered opposite the UNO-city complex (Vienna International Center). The box is fenced by a solid metal fence, under the supervision of 10 cameras. Most likely, this is a fake base station of a mobile network.

Vienna is the third UN resident city (after New York and Geneva), and OPEC and OSCE headquarters are located there. The NSA’s interest in the place where dignitaries of most countries gather is quite understandable. And here is the estimated coverage area of this station:
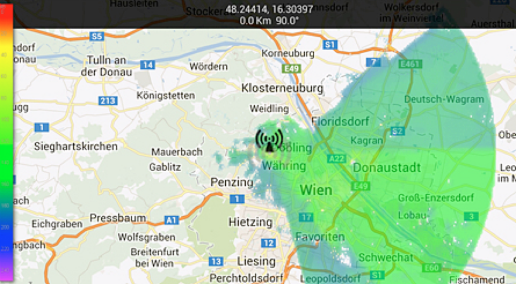
Such base stations can intercept IMSI (the so-called IMSI-catcher), and then track the victim’s location through the SS7 network. Once you have tracked the victim’s IMSI, you can track its movement around the world until the user changes the SIM card. We have already talked about such attacks in more detail here .
Snowden's documents suggest that the Vienna station (Vienna-Annex) is only part of the SIGINT global tracking network. Further, you can already search the list of countries and cities mentioned in these documents. Here is a photo of a similar structure found on a rooftop in Rome:

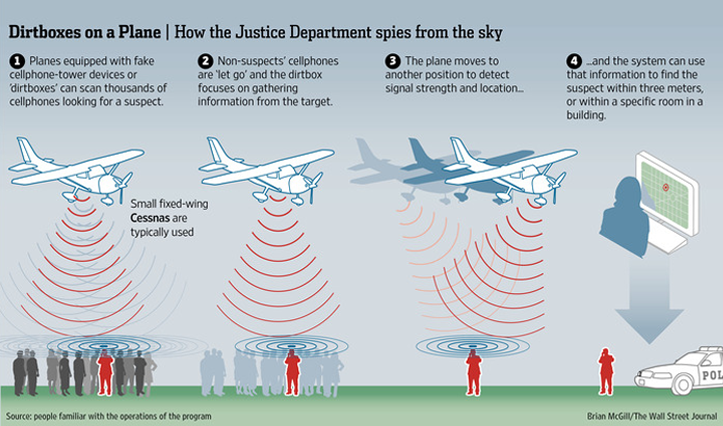
By the way, American intelligence agencies are not limited to stationary tracking systems. They have long been using StingRay interceptor stations on special vehicles that can drive to a given target. And in November, the Wall Street Journal reported that the US Department of Justice is using Cessna aircraft with fake base stations to intercept user data:
Who is to blame and what to do?
First of all, it should be noted that despite the loud headlines, the described technologies are now available not only to the special services. In fact, wiretapping of mobile networks and protection against it has become a new high-tech market. And as in any market, new, cheaper solutions are constantly appearing here.
In August 2014, Popular Science magazine talked about how a group of ESD America security experts are promoting their own development - the “highly protected” Android-based CryptoPhone 500 smartphone. Since there are already several similar products on the market, the developers used a non-banal advertising move. Using their advanced smartphone, they found 17 fake base stations in the US that forcibly disable data encryption:
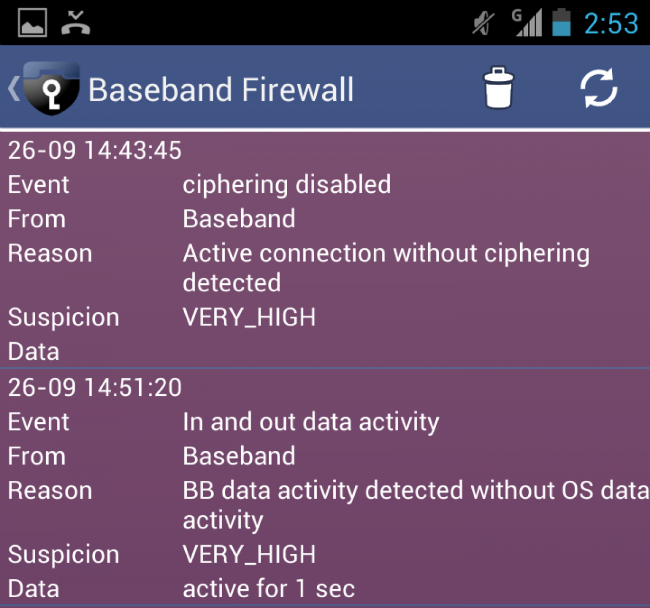
One such wiretapping station was discovered near a large casino in Las Vegas, and several more - near the US military bases. Who, except the NSA, can use such a technique? Yes, anyone. True, commercial complexes are expensive - more than $ 100 thousand. However, you can significantly reduce the cost of the solution if you use free software to create your own base station.
How to escape from this? One of the options already mentioned above is a “secure” smartphone. However, the pleasure is not cheap: CryptoPhone costs $ 3,500. For this money, the client receives the "closure" of a number of attack vectors, which appeared above in our list. In particular, there is monitoring of known vulnerabilities of Android OS, monitoring of suspicious activity of mobile applications, and even monitoring of a baseband processor: this feature allows you to determine the connection of a fake base station-interceptor, which is not noticed by ordinary smartphones.
It’s more difficult to protect yourself from fake base stations with a regular phone, but you can still do something. UMTS (G3) networks use mutual authentication of a mobile station in a cellular network and a cellular network in a mobile station. Therefore, one of the signs of wiretapping is the forced switching from the G4 and G3 modes to the less secure G2 mode. If the user disables the 2G mode in advance, this will complicate the task for the attacker to intercept the radio broadcast. Some mobile phone models allow you to switch the type of network you are using:
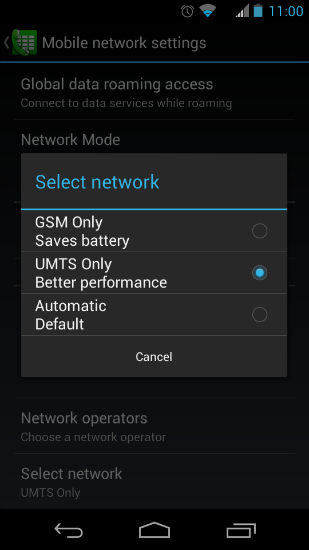
Also, many Android phones have a service menu called up by the command * # * # 4636 # * # *, where you can select the type of network. True, such a solution is fraught with increased battery consumption, as well as loss of communication in the absence of 3G network coverage.
Fake base stations allow you to intercept any data transmitted through the cellular network - however, this requires the physical presence of the subscriber in the coverage area of the base station. Therefore, attacks on the SS7 network can be considered a more advanced tracking method , allowing you to intercept the subscriber’s data, as well as his location, from anywhere in the world. Here, too, there are commercial solutions: in one of our previous posts we talked about the SkyLock system of the American company Verint, which allows you to track any subscribers around the world.
How can you prevent wiretapping in this case? Since the attacks are based on legitimate messages of the SS7 signaling network, rough filtering of these messages can have a negative impact on the entire service. According to the experience of Positive Technologies experts, adequate protection against attacks on SS7 should be a set of measures on the operator’s side, including SS7 traffic monitoring and “smart” filtering control, which allows you to block only attack and fraud attempts. You can read more about how this is implemented on the basis of our products in the article “ Security of mobile communication networks based on SS7 ”.
