Conference DEFCON 22. GTVHacker Group. Breaking it all: 20 devices in 45 minutes. Part 2
- Transfer
Conference DEFCON 22. GTVHacker Group. Breaking it all: 20 devices in 45 minutes. Part 1
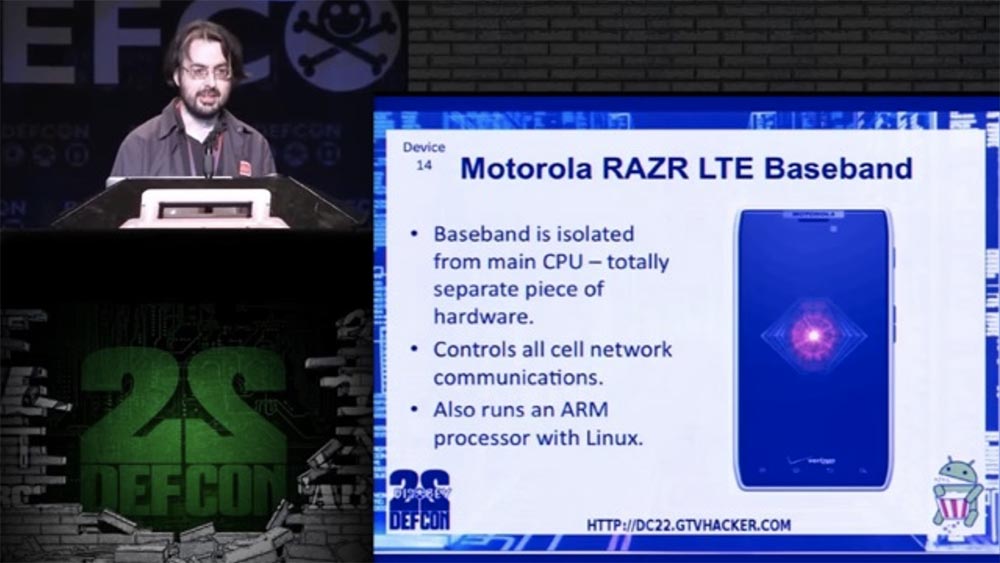
Mike Baker: The following, the 14th device to which we got root access, is the Motorola RAZR LTE Baseband smartphone. I'm not going to talk about Android, it is already “rooted”. This phone is special because it uses Baseband, a separate signal processor isolated from the main processor. This is a completely separate piece of smartphone hardware.
Communication between Android and Baseband is through a USB network connection. Baseband listens to the internal USB network port, has limited access to the shell through port 3023 and runs the diagnostic script through port 3002 as root.
If you look at the script, you can see that using AWK, the command busybox is launched:
That is, the file name is transmitted via the AWK script. This means that using the file name we can inject into the shell. For rutting the shell, we use the file name containing:
This allows you to enter into the system any command and run it with root-rights.
The next hacked device at number 15 was the PogoPlug Mobile mobile storage, which serves as a personal cloud storage. It is used to transfer content from your mobile device to anywhere, connecting to your home network and sharing files over the Internet.

The cost of this device is less than $ 10. You can connect a USB drive or an SD card to it and it will automatically upload information to the cloud. It is based on the Marvell Feroceon processor and is managed by Linux 2.6.31.8.
There are 4 traditional UART contacts on the PCB, which gives us access to the bootloader and the root shell, but we can also implement the command line using a web page.
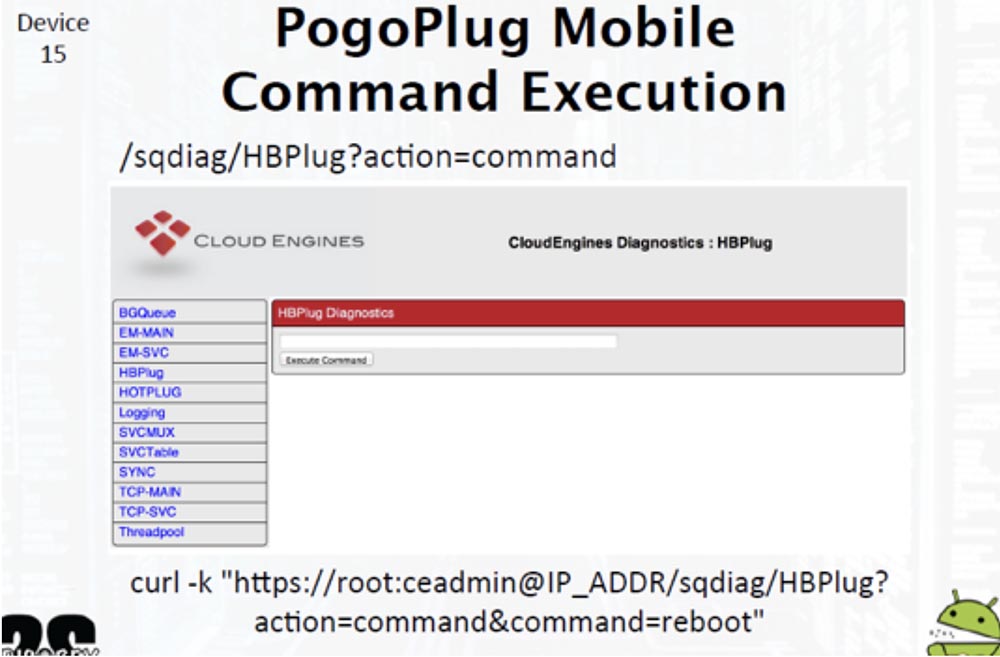
Using this interface allows you to enter arbitrary commands and run them on behalf of the superuser with root-rights.
The next exhibit # 16 is the Netgear Push2TV set-top box (PTV3000). It uses open technology Miracast, supported by Google, which is found in some models of smartphones and tablets with Android and Intel WiDi technology.

On the printed circuit board of this wireless receiver, there are UART pins through which you can connect to the device, then press the space bar during the bootup, thereby interrupting the U-boot operation, and run your own commands for Linux. You can not mess with the bootloader and use the Root console, which is active for 2-3 seconds after the download. It is also possible to implement commands via the web interface via the device name, while the command will be executed on behalf of the superuser with root privileges. An SPI Flash memory chip containing U-boot commands can be reflashed to launch your custom bootloader.
Device 17 is a VOIP Ooma Telo router running the OpenWRT OS and equipped with an ARM processor.

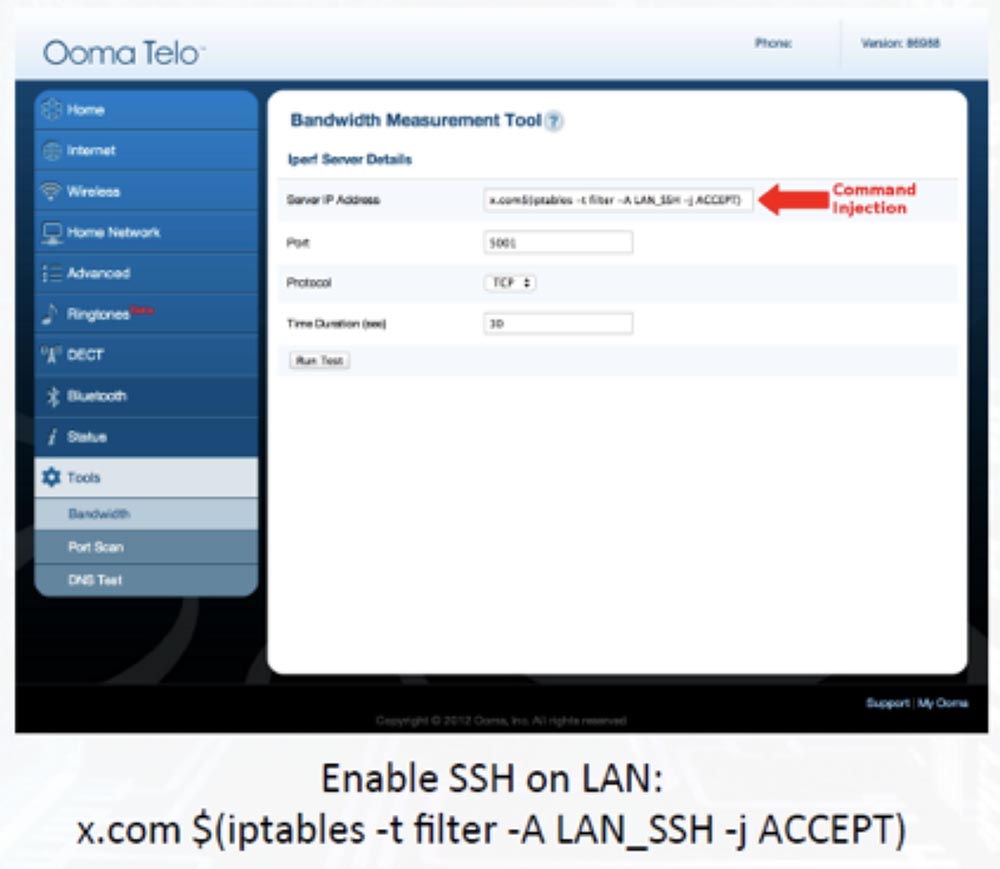
The UART is here again, which uses console input, but we are considering command injections. There is also an SSH port that works by default as a firewall, so we first need to implement a command that will change the rules of this firewall. We did this through a web interface to be able to subsequently enter any command. Interestingly, the default password for root access was "! Ooma123", so hacking it was not difficult. As soon as we entered, we immediately "reset" the password file and started hacking. By default, SSH is only available over the LAN.
The next slide shows the Olo Olo web interface, the arrow shows the line where we entered the command. The ability to adjust the rules of the IP address tables gives access to SSH, where you can use the password provided.
Device 18 is a streaming multimedia player Netgear NTV200-100NAS based on Adobe Flash, priced from 10 to $ 30, which plays SWF files.
It is equipped with a Wi-Fi module, a Broadcom SOC processor with an encrypted and signed firmware update.
Everything is signed on the PCB, so finding the UART was not difficult. But let's talk about command-line injection via the web interface, as updates and applications are downloaded to this player via an unencrypted HTTPS connection. This is a very bad idea, because unlike encrypted updates, applications can be freely downloaded and installed. Therefore, when installing the application, it becomes possible to use a man-in-the-middle attack:

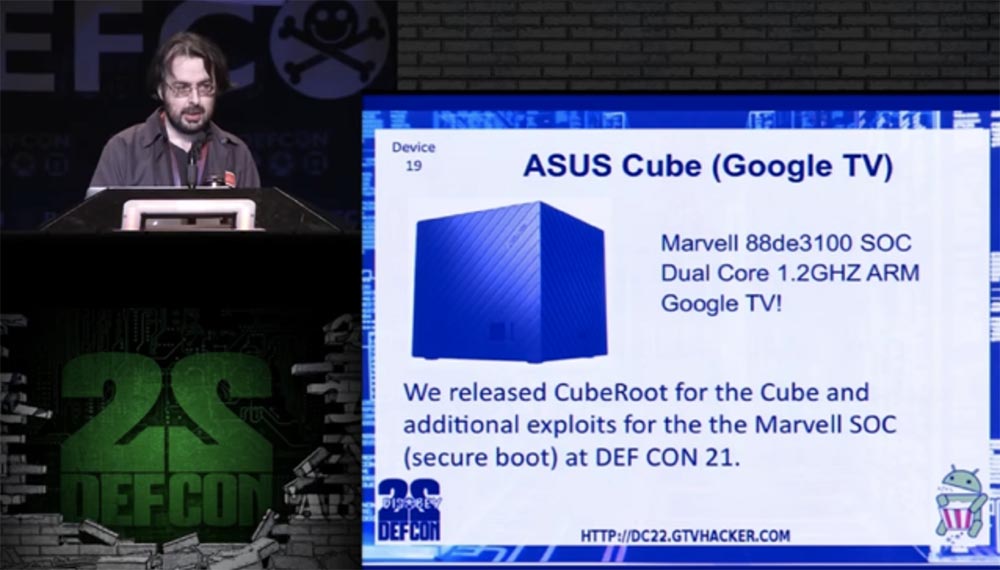
So, move on. Device number 19 is the ASUS Cube, the “bridge” between the Internet and streaming video, a set-top box that enables the large-scale operation of the Google TV hardware and software platform. It is equipped with a 1.2 GHz dual-core Marvell 88de3100 SOC processor. At the DefCon 21 conference, we already presented an additional CubeRoot exploit for this device, which was designed to control the processor in safe mode.
We had an application available on the Play Store, unfortunately Google removed it, they do not like these applications. Let's talk about how we get back to this cube again. Multimedia applications built into it allow you to mount the SMB network protocol for remote access to files, in this case they allow sharing Windows files without any restrictions. The procedure for obtaining root-rights is as follows:
At this point, I hand over to Amir.
Amir Etemadi: thanks, Mike!
Let's continue our fun and consider some more interesting devices. I want to tell you about a baby monitor - a baby's activity monitor called Summer Baby Zoom WiFi.
This device allows you to watch children using a video camera and transfer the image to your smartphone via Wi-Fi. He has his own compact monitor with a speaker and a display that allows you to remotely control the camera over the radio channel. On the market, it is positioned as "protected". This is the 20th device we hacked.

Having disassembled it, we, as usual, first of all began to search for the UART and made out contacts, which were quite difficult to connect to. How we managed to do this, we can tell after the presentation, and now we will look at the mistakes that the developers of this device made when creating it.

The first mistake is to have a hard-coded username and password on the device, which uses a binary file to communicate with the web interface. This is just a terrible practice. From a security point of view, you should not have hard-coded credentials on every single device.
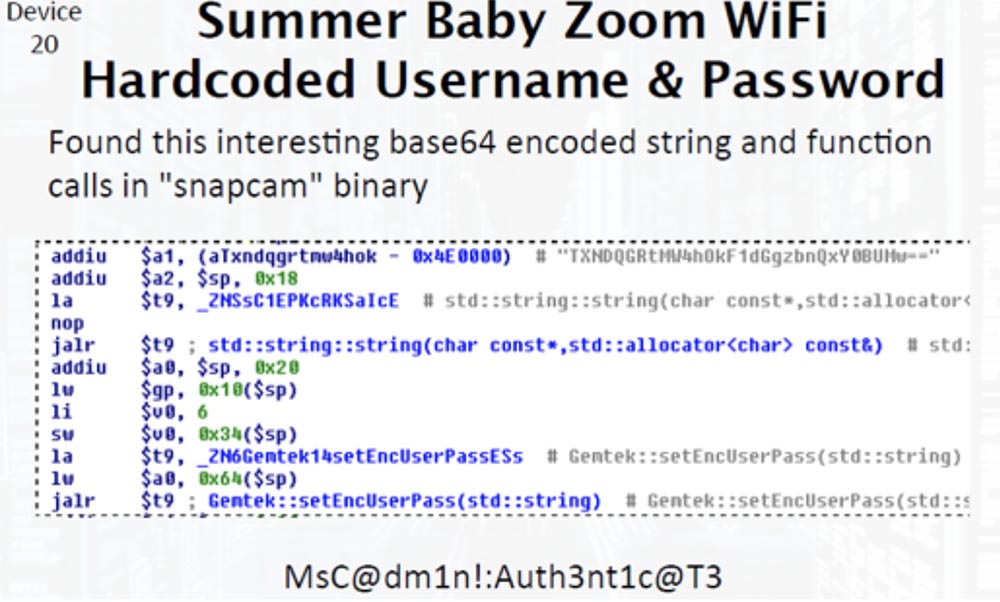
We found an interesting encrypted string and system calls in a binary “snapcam” file that contained authentication data. Next, we moved on to parsing hard-coded data.
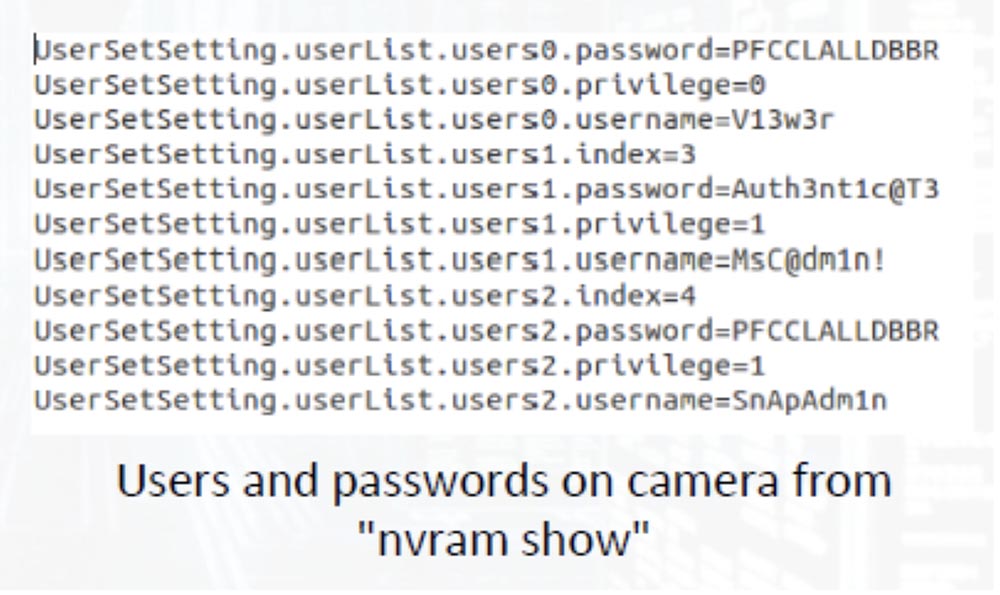
Having performed the “nvram show” system call from the command line, we received a list of 3 users and their passwords. Two users had passwords that were different for each camera, and provided different user rights.
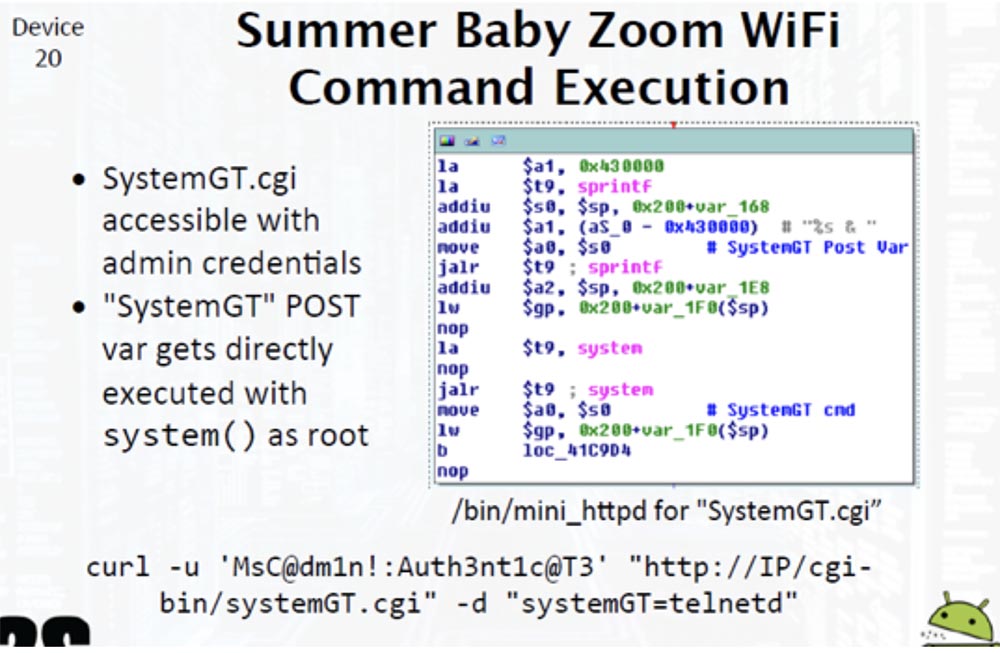
Next, we found the SystemGT.cgi system configuration file, access to which was provided using admin privileges, and which was directly executed using the system () operator on behalf of the superuser. We entered the command line shown at the bottom of the next slide and got access to the Telnet server with root privileges.
Remember that in most cases, when the device is not password protected, you can enter the shell by simply typing an expression of the type l / bin / login on the command line.
In many cases, you can use the / bin / sh command, and if someone enters the device in the normal way, the attacker immediately throws it into the shell. Therefore, do not allow people to connect to your device, keep it safe.
So, since this is DefCon 22, why don’t we tell us about hacking 22 devices in 45 minutes? Therefore, we will continue the presentation with two more devices.

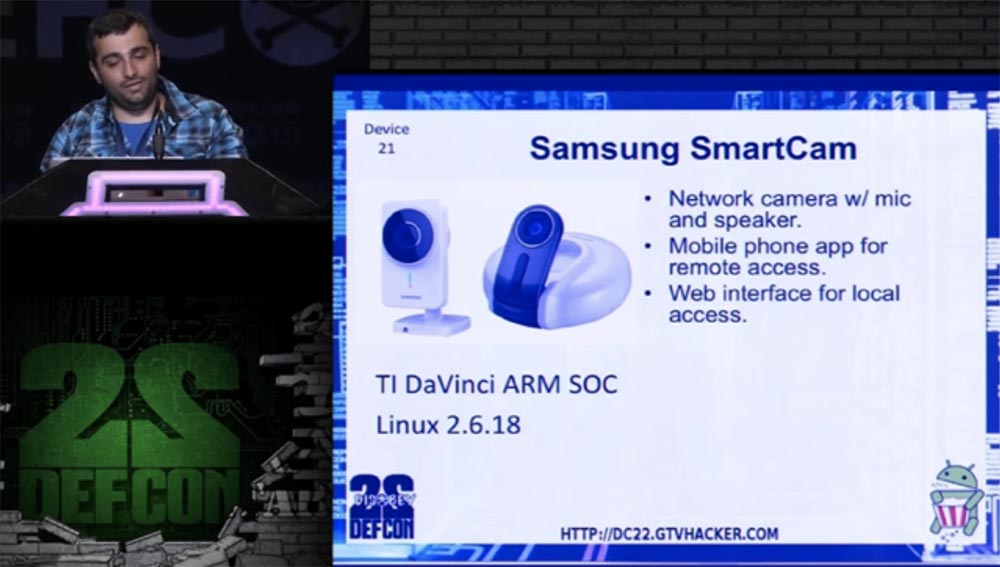
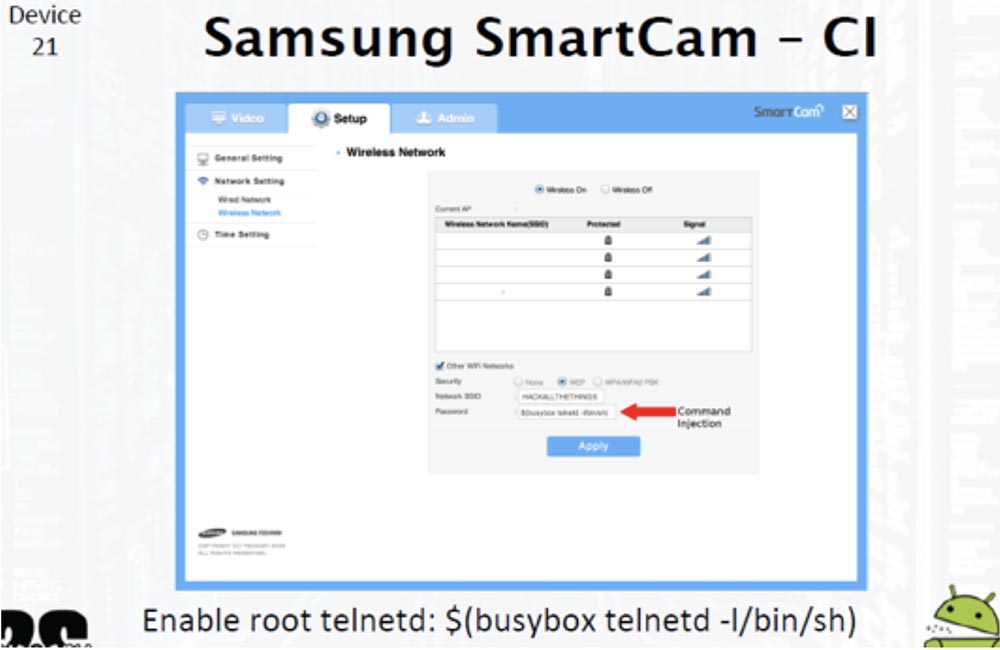
Let's move on to the next item on our list — this is the Samsung SmartCam standalone webcam with a microphone and speaker. It can be controlled using a mobile application, and uses a web interface for local access. The camera is equipped with a TI DaVinci ARM SOC processor and runs under Linux 2.6.18. Structurally, this device is very similar to the summer baby Zoom WiFi baby monitor, but it does not change its position to track an object.
On the printed circuit board is a classic UART adapter with the contacts of the receiver, transmitter, ground and power. Below is a block of contacts to configure the connection. Here, only the Console Logging method is used, which displays debug information in the console, hiding it from the user.
Interestingly, we discovered this by looking at how logins are processed and how the original administrator password is created when the device is first configured. With this setting, you are prompted to set your own administrator password. The disadvantage is that the device does not check if the password is already configured, so you can call the script to change the existing password to the administrator password. Thus, it is possible to reset the device administrator password without knowing the user's password. Access to the command line is possible only via LAN.
The WEP encryption key is not checked for shell commands and placed in a configuration file, from where it can be pulled out and used to enter commands through the console. In this case, you must disconnect the network cable if the camera is already connected to the network via Wi-Fi, because if you change the WEP key, when the camera is connected via Wi-Fi, the device may disconnect you and you will lose access to it.
If the camera is connected to a Wi-Fi network, it can be hacked without physical contact with the device, after which the web interface starts working with root-rights.
Thus, the injection of the superuser command is made by changing the WEP-key of access to the Wi-Fi network. To connect to the Telnet network, just enter the $ command (busybox telnetd - l / bin / sh)
The most interesting of all the considered devices seemed to us device number 22, because it provides a large field of activity for hackers. This device is called Wink Hub, and I like it more than others, mainly because it has a large range of peripheral devices.
This thing controls all wireless "smart" home devices using a mobile application, which allows you to abandon individual control panels. Wink Hub has a Wi-Fi, Bluetooth, Zwawe and Zigbee module, as well as an excellent product of the RF Toolkit developers.
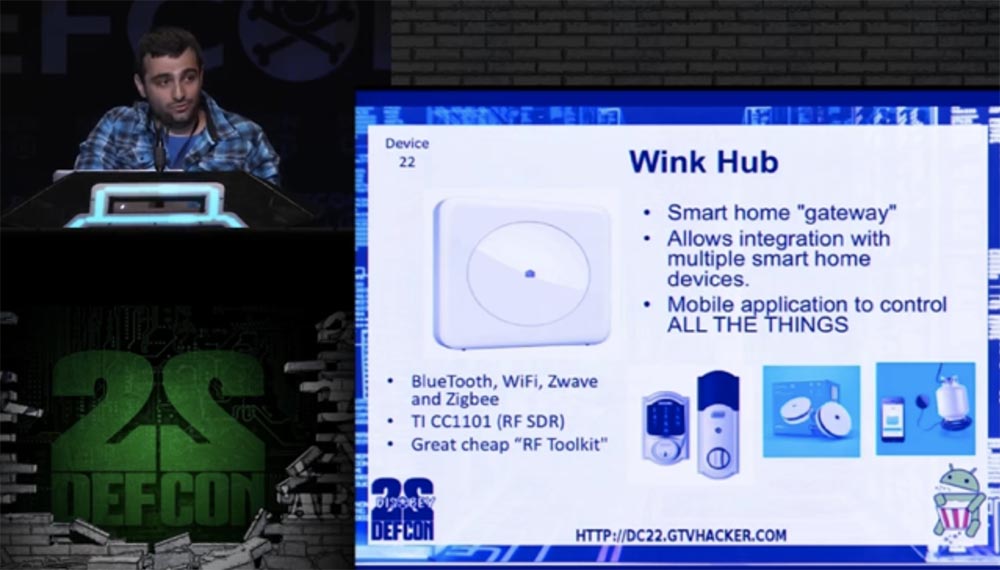
This is a software toolkit for any hacker, as through it the interaction of peripheral devices. Wink Hub is essentially a home gateway that integrates devices with already configured APIs, which has all the communication methods, it even has its own set of devices, ranging from a gas leak detector to sensors for humidity, temperature, lighting and motion detection. It also manages smart locks and obtains information on the status of all monitored devices.
The next slide shows a board that looks quite nice.

So, this is a board, it is really beautiful.
Everything is signed here, and what else is nice about this device is that it costs less than $ 50, and there is a suggestion that if you buy peripherals, you can get Wink Hub for free. Therefore, if you are interested in RF devices, this is a really cool board.
On it are separate chips for each type of connected devices that it supports. So this device has a command line injection error. If you do not understand PHP, there is a sudo command that allows you to run programs with administrator privileges without entering the superuser password.
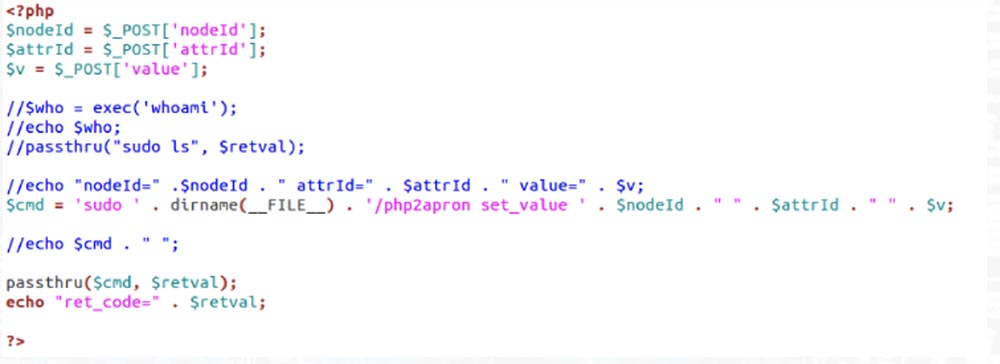
This command gives the node ID of the node the node ID of the ID attribute value by the POST variables. So take this team into service, and when you return home, buy yourself this device and have fun with it as you wish.
Well, now we will show you what you have been waiting for! A video recording of the hacking demonstration of all 22 devices will take place under a real hacker rep. For this, we invited our friend, rapper Ned from Dual Core! Let's welcome him and the song "All these things"!
We have almost a hundred different UART adapters here, and Сhromecast CDs, and while you watch the video and enjoy the rap, we'll go to the gym and give it all to you.
Dual Core:great guys i'm trying to catch my breath ... my name is ned, i'm a rapper in dual core, you may have heard our songs like “drink everything and break everything”. Have any of you cracked cars? Fine!
I want to present you a book of my friend, this is a hacker’s guide for hacking cars, you can download it for free, buy it on Amazon, I have a few pieces with me that I will distribute. So, rap music ... if I don’t get enough breath, I can die!
So where is my DJ? Press the spacebar and start the video so that I can start!
On the screen begins the demonstration of hacking devices, which were discussed in this presentation. The phrase “not every geek with Commodore 64 can crack NASA” sounds, then the music track is started, under which Ned plays rap “Drink all the booze” like this:
I tell you to drink all the drinks, the
guys so quickly hacked all the things
that you they didn’t even have time to count them;
disaster recovery requires even more fists,
put your bytes on it all,
my C64 will blow everything up in orbit, the
perfect boom will break all the chains,
optimize the process time
to avoid a sentence, you just need a stream,
you just need a stream,
engine size not having t value
there are mines in the command line,
and before they see me,
break the captcha, finish the chapter,
drink all the drinks,
take this bike, which is red,
it still winks at me,
drink all the booze, drink all the alcohol,
I wait until my Blackberry dies
To replace it with the Raspberry Pi,
neutralize any threat for the Red Skull,
killed virus writers climbed the VX7,
which records our live data,
hello to you, ciphers and device drivers,
where we will get, before they launch the format,
Mike wants to get your Internet wi-Fi,
it took vzlomat Pineapple 5,
you are ready to crack all things?
Yes, you are ready to hack all things!
like this, sir, we drink all the drinks,
we drink everything,
you know that there will be safety rules,
but first we drink all the drinks, and then we hack them, it's
all about the system or the firmware,
what you pray for regardless of the service,
re-encode and connect to the Internet,
gathering it yourself, it will be spoiled by pirates
clapping the attack above the cloud,
but we will return to the subway,
where there is no mass control, go
down the Tor nodes around the world,
hack the device traffic online,
call the state - hunt for us,
my Konrad Zuse is a trigger-debugger,
I need a plan that th works,
I want to see how everything burns,
and now it's your turn,
drink all the drinks, yes,
drink all the drinks, this fight is a game,
this horror still winks at me,
so eat all the food and drink all the drinks!
I thank the guys from GTVHacker!

Amir Etemadi: I find it hard to believe that we had a Dual Core visiting! He did it without any conditions, without any payment, he is just a great guy! Yes, I was also out of breath. We have absolutely no time, so if you have questions, we are ready to answer them after the conference.
We provide links to our resources here, welcome to the GTV Hacker channel and thank you all, we love you!
Presentation Slides: DC22.GTVHacker.com
WIKI:www.GTVHacker.com
Forum: forum.GTVHacker.com
Blog: blog.GTVHacker.com
IRC: irc.freenode.net #GTVHacker
Twitter: @GTVHacker
Mike Baker: The following, the 14th device to which we got root access, is the Motorola RAZR LTE Baseband smartphone. I'm not going to talk about Android, it is already “rooted”. This phone is special because it uses Baseband, a separate signal processor isolated from the main processor. This is a completely separate piece of smartphone hardware.

Communication between Android and Baseband is through a USB network connection. Baseband listens to the internal USB network port, has limited access to the shell through port 3023 and runs the diagnostic script through port 3002 as root.
If you look at the script, you can see that using AWK, the command busybox is launched:
busybox awk '{print+substr(" ' "$ {outFilePath}" ' ",0,1)}’That is, the file name is transmitted via the AWK script. This means that using the file name we can inject into the shell. For rutting the shell, we use the file name containing:
x",0,1);system("…");("This allows you to enter into the system any command and run it with root-rights.
The next hacked device at number 15 was the PogoPlug Mobile mobile storage, which serves as a personal cloud storage. It is used to transfer content from your mobile device to anywhere, connecting to your home network and sharing files over the Internet.

The cost of this device is less than $ 10. You can connect a USB drive or an SD card to it and it will automatically upload information to the cloud. It is based on the Marvell Feroceon processor and is managed by Linux 2.6.31.8.
There are 4 traditional UART contacts on the PCB, which gives us access to the bootloader and the root shell, but we can also implement the command line using a web page.

Using this interface allows you to enter arbitrary commands and run them on behalf of the superuser with root-rights.
The next exhibit # 16 is the Netgear Push2TV set-top box (PTV3000). It uses open technology Miracast, supported by Google, which is found in some models of smartphones and tablets with Android and Intel WiDi technology.

On the printed circuit board of this wireless receiver, there are UART pins through which you can connect to the device, then press the space bar during the bootup, thereby interrupting the U-boot operation, and run your own commands for Linux. You can not mess with the bootloader and use the Root console, which is active for 2-3 seconds after the download. It is also possible to implement commands via the web interface via the device name, while the command will be executed on behalf of the superuser with root privileges. An SPI Flash memory chip containing U-boot commands can be reflashed to launch your custom bootloader.
Device 17 is a VOIP Ooma Telo router running the OpenWRT OS and equipped with an ARM processor.

The UART is here again, which uses console input, but we are considering command injections. There is also an SSH port that works by default as a firewall, so we first need to implement a command that will change the rules of this firewall. We did this through a web interface to be able to subsequently enter any command. Interestingly, the default password for root access was "! Ooma123", so hacking it was not difficult. As soon as we entered, we immediately "reset" the password file and started hacking. By default, SSH is only available over the LAN.
The next slide shows the Olo Olo web interface, the arrow shows the line where we entered the command. The ability to adjust the rules of the IP address tables gives access to SSH, where you can use the password provided.

Device 18 is a streaming multimedia player Netgear NTV200-100NAS based on Adobe Flash, priced from 10 to $ 30, which plays SWF files.
It is equipped with a Wi-Fi module, a Broadcom SOC processor with an encrypted and signed firmware update.
Everything is signed on the PCB, so finding the UART was not difficult. But let's talk about command-line injection via the web interface, as updates and applications are downloaded to this player via an unencrypted HTTPS connection. This is a very bad idea, because unlike encrypted updates, applications can be freely downloaded and installed. Therefore, when installing the application, it becomes possible to use a man-in-the-middle attack:
- we create a copy of the application;
- insert the symlink malicious soft link into it;
- repack the application and place it on the local host;
- run the application;
- we modify it again by adding a shell script during operation that contains a symlink inside to call Telnet;
- run the application again, reboot, and now we have permanent root access!

So, move on. Device number 19 is the ASUS Cube, the “bridge” between the Internet and streaming video, a set-top box that enables the large-scale operation of the Google TV hardware and software platform. It is equipped with a 1.2 GHz dual-core Marvell 88de3100 SOC processor. At the DefCon 21 conference, we already presented an additional CubeRoot exploit for this device, which was designed to control the processor in safe mode.

We had an application available on the Play Store, unfortunately Google removed it, they do not like these applications. Let's talk about how we get back to this cube again. Multimedia applications built into it allow you to mount the SMB network protocol for remote access to files, in this case they allow sharing Windows files without any restrictions. The procedure for obtaining root-rights is as follows:
- creating an SMB share using a superuser binary;
- use of the media application to connect to SMB share;
- adding it to Cube, launching the superuser binary file, getting root-rights!
- Remounting the system, installing SuperSu and full control over the capabilities of the device.
At this point, I hand over to Amir.
Amir Etemadi: thanks, Mike!
Let's continue our fun and consider some more interesting devices. I want to tell you about a baby monitor - a baby's activity monitor called Summer Baby Zoom WiFi.
This device allows you to watch children using a video camera and transfer the image to your smartphone via Wi-Fi. He has his own compact monitor with a speaker and a display that allows you to remotely control the camera over the radio channel. On the market, it is positioned as "protected". This is the 20th device we hacked.

Having disassembled it, we, as usual, first of all began to search for the UART and made out contacts, which were quite difficult to connect to. How we managed to do this, we can tell after the presentation, and now we will look at the mistakes that the developers of this device made when creating it.

The first mistake is to have a hard-coded username and password on the device, which uses a binary file to communicate with the web interface. This is just a terrible practice. From a security point of view, you should not have hard-coded credentials on every single device.

We found an interesting encrypted string and system calls in a binary “snapcam” file that contained authentication data. Next, we moved on to parsing hard-coded data.
Having performed the “nvram show” system call from the command line, we received a list of 3 users and their passwords. Two users had passwords that were different for each camera, and provided different user rights.

Next, we found the SystemGT.cgi system configuration file, access to which was provided using admin privileges, and which was directly executed using the system () operator on behalf of the superuser. We entered the command line shown at the bottom of the next slide and got access to the Telnet server with root privileges.

Remember that in most cases, when the device is not password protected, you can enter the shell by simply typing an expression of the type l / bin / login on the command line.
In many cases, you can use the / bin / sh command, and if someone enters the device in the normal way, the attacker immediately throws it into the shell. Therefore, do not allow people to connect to your device, keep it safe.
So, since this is DefCon 22, why don’t we tell us about hacking 22 devices in 45 minutes? Therefore, we will continue the presentation with two more devices.

Let's move on to the next item on our list — this is the Samsung SmartCam standalone webcam with a microphone and speaker. It can be controlled using a mobile application, and uses a web interface for local access. The camera is equipped with a TI DaVinci ARM SOC processor and runs under Linux 2.6.18. Structurally, this device is very similar to the summer baby Zoom WiFi baby monitor, but it does not change its position to track an object.

On the printed circuit board is a classic UART adapter with the contacts of the receiver, transmitter, ground and power. Below is a block of contacts to configure the connection. Here, only the Console Logging method is used, which displays debug information in the console, hiding it from the user.
Interestingly, we discovered this by looking at how logins are processed and how the original administrator password is created when the device is first configured. With this setting, you are prompted to set your own administrator password. The disadvantage is that the device does not check if the password is already configured, so you can call the script to change the existing password to the administrator password. Thus, it is possible to reset the device administrator password without knowing the user's password. Access to the command line is possible only via LAN.
The WEP encryption key is not checked for shell commands and placed in a configuration file, from where it can be pulled out and used to enter commands through the console. In this case, you must disconnect the network cable if the camera is already connected to the network via Wi-Fi, because if you change the WEP key, when the camera is connected via Wi-Fi, the device may disconnect you and you will lose access to it.
If the camera is connected to a Wi-Fi network, it can be hacked without physical contact with the device, after which the web interface starts working with root-rights.
Thus, the injection of the superuser command is made by changing the WEP-key of access to the Wi-Fi network. To connect to the Telnet network, just enter the $ command (busybox telnetd - l / bin / sh)

The most interesting of all the considered devices seemed to us device number 22, because it provides a large field of activity for hackers. This device is called Wink Hub, and I like it more than others, mainly because it has a large range of peripheral devices.
This thing controls all wireless "smart" home devices using a mobile application, which allows you to abandon individual control panels. Wink Hub has a Wi-Fi, Bluetooth, Zwawe and Zigbee module, as well as an excellent product of the RF Toolkit developers.

This is a software toolkit for any hacker, as through it the interaction of peripheral devices. Wink Hub is essentially a home gateway that integrates devices with already configured APIs, which has all the communication methods, it even has its own set of devices, ranging from a gas leak detector to sensors for humidity, temperature, lighting and motion detection. It also manages smart locks and obtains information on the status of all monitored devices.
The next slide shows a board that looks quite nice.

So, this is a board, it is really beautiful.
Everything is signed here, and what else is nice about this device is that it costs less than $ 50, and there is a suggestion that if you buy peripherals, you can get Wink Hub for free. Therefore, if you are interested in RF devices, this is a really cool board.
On it are separate chips for each type of connected devices that it supports. So this device has a command line injection error. If you do not understand PHP, there is a sudo command that allows you to run programs with administrator privileges without entering the superuser password.

This command gives the node ID of the node the node ID of the ID attribute value by the POST variables. So take this team into service, and when you return home, buy yourself this device and have fun with it as you wish.
Well, now we will show you what you have been waiting for! A video recording of the hacking demonstration of all 22 devices will take place under a real hacker rep. For this, we invited our friend, rapper Ned from Dual Core! Let's welcome him and the song "All these things"!
We have almost a hundred different UART adapters here, and Сhromecast CDs, and while you watch the video and enjoy the rap, we'll go to the gym and give it all to you.
Dual Core:great guys i'm trying to catch my breath ... my name is ned, i'm a rapper in dual core, you may have heard our songs like “drink everything and break everything”. Have any of you cracked cars? Fine!
I want to present you a book of my friend, this is a hacker’s guide for hacking cars, you can download it for free, buy it on Amazon, I have a few pieces with me that I will distribute. So, rap music ... if I don’t get enough breath, I can die!
So where is my DJ? Press the spacebar and start the video so that I can start!

On the screen begins the demonstration of hacking devices, which were discussed in this presentation. The phrase “not every geek with Commodore 64 can crack NASA” sounds, then the music track is started, under which Ned plays rap “Drink all the booze” like this:
I tell you to drink all the drinks, the
guys so quickly hacked all the things
that you they didn’t even have time to count them;
disaster recovery requires even more fists,
put your bytes on it all,
my C64 will blow everything up in orbit, the
perfect boom will break all the chains,
optimize the process time
to avoid a sentence, you just need a stream,
you just need a stream,
engine size not having t value
there are mines in the command line,
and before they see me,
break the captcha, finish the chapter,
drink all the drinks,
take this bike, which is red,
it still winks at me,
drink all the booze, drink all the alcohol,
I wait until my Blackberry dies
To replace it with the Raspberry Pi,
neutralize any threat for the Red Skull,
killed virus writers climbed the VX7,
which records our live data,
hello to you, ciphers and device drivers,
where we will get, before they launch the format,
Mike wants to get your Internet wi-Fi,
it took vzlomat Pineapple 5,
you are ready to crack all things?
Yes, you are ready to hack all things!
like this, sir, we drink all the drinks,
we drink everything,
you know that there will be safety rules,
but first we drink all the drinks, and then we hack them, it's

all about the system or the firmware,
what you pray for regardless of the service,
re-encode and connect to the Internet,
gathering it yourself, it will be spoiled by pirates
clapping the attack above the cloud,
but we will return to the subway,
where there is no mass control, go
down the Tor nodes around the world,
hack the device traffic online,
call the state - hunt for us,
my Konrad Zuse is a trigger-debugger,
I need a plan that th works,
I want to see how everything burns,
and now it's your turn,
drink all the drinks, yes,
drink all the drinks, this fight is a game,
this horror still winks at me,
so eat all the food and drink all the drinks!
I thank the guys from GTVHacker!

Amir Etemadi: I find it hard to believe that we had a Dual Core visiting! He did it without any conditions, without any payment, he is just a great guy! Yes, I was also out of breath. We have absolutely no time, so if you have questions, we are ready to answer them after the conference.
We provide links to our resources here, welcome to the GTV Hacker channel and thank you all, we love you!
Presentation Slides: DC22.GTVHacker.com
WIKI:www.GTVHacker.com
Forum: forum.GTVHacker.com
Blog: blog.GTVHacker.com
IRC: irc.freenode.net #GTVHacker
Twitter: @GTVHacker
