SMS virus for Android OS or “Hello :) You have a photo ...”

* Original picture, impudently pulled from apk resources
[approx. apk - application installation file extension on the Android OS]
Introduction
Unexpectedly, in the middle of the day, an old SMS comes to my old Sony Ericsson K320i:
hi [smiley] to you photo https: // m ** o * an.ru / oujr / 380688086 * 6 *
The sender was a person with whom I haven’t been talking for some time. After watching the test message and dismissing the phone with the words "Another spam", I further plunged into work.
Everything would be fine, but after a couple of minutes a similar message arrived on the second phone (Samsung Galaxy Gio). The sender number was the same.
After 2 hours, a friend called and asked for advice. He received a similar SMS from his boss. Reassuring him with the phrase: “Do not follow the link and you will be happy”, I decided that I needed to understand the situation.
Arrangements
1) It is technically correct to call this “malware” not a virus, but a trojan . The author deliberately went to this trick to simplify. I apologize in advance for this.
2) The author in this article tried to put himself in the place of an ordinary user, to experience and experience everything that he is experiencing. Therefore, specialized technical means are not used, and primitive methods are chosen.
2) The author in this article tried to put himself in the place of an ordinary user, to experience and experience everything that he is experiencing. Therefore, specialized technical means are not used, and primitive methods are chosen.
1. Preparation
Having searched the Internet on a surface, it was found that the link in the SMS message is nothing more than the address for downloading the apk file. And the apk file is the Trojan.SMSSend virus, which infects mobile devices running Android. The main tasks of this “malware” are to take control of a device and use it for its own purposes: blocking outgoing calls, sending messages “with greetings,” and other minor tricks.
Having followed the link from the browser, I safely received the answer “403 Forbidden”.
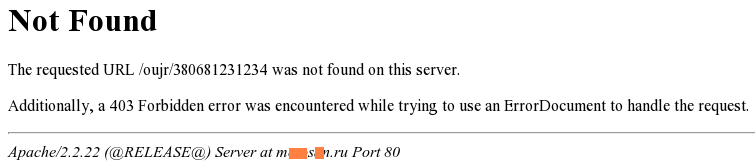
Clearly, it means there is a filter by browser. Well, I will check "on cats", as they say.
Without thinking twice, I decided to “put my Samsung Galaxy Tab 2 tablet on the altar of science”. After making a backup, with a clear conscience, I clicked on the “General Reset” button. Just in case, I was convinced that there was no money on the sim card and started installation.
2. Installation
I go to the settings, in the menu item "Unknown devices", uncheck the box "Allow installation of applications from sources other than the Play Store."
Following the link from the SMS message, I received a browser warning of the following nature: I
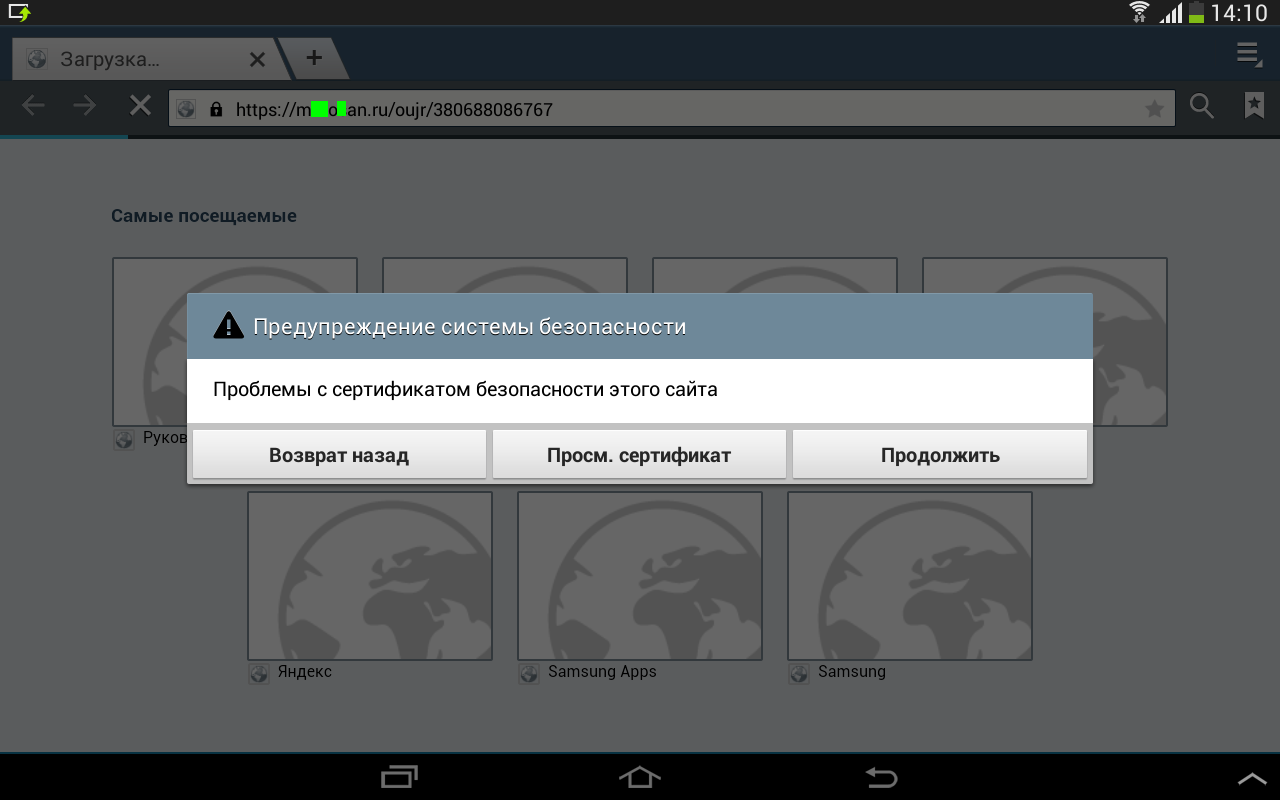
agree and click the "Continue" button. The application F0T0_ALB0M.apk was downloaded:
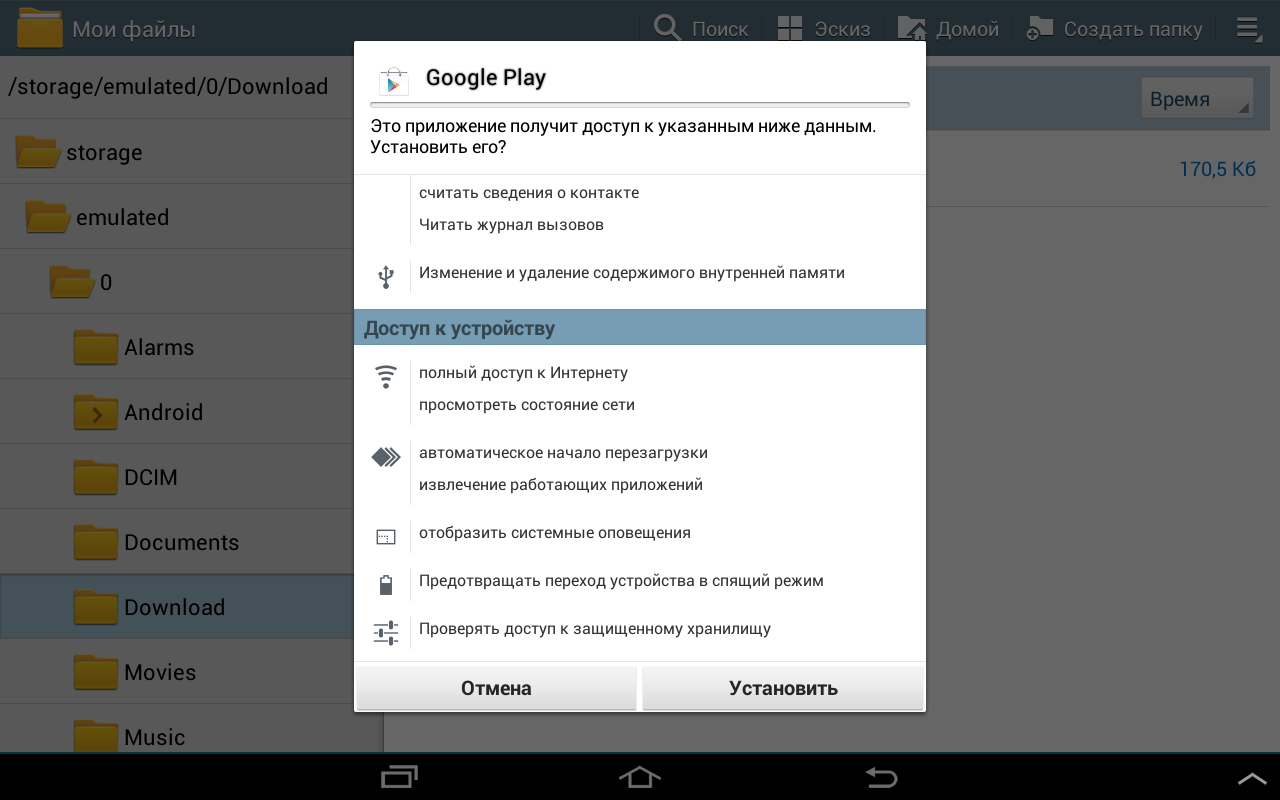
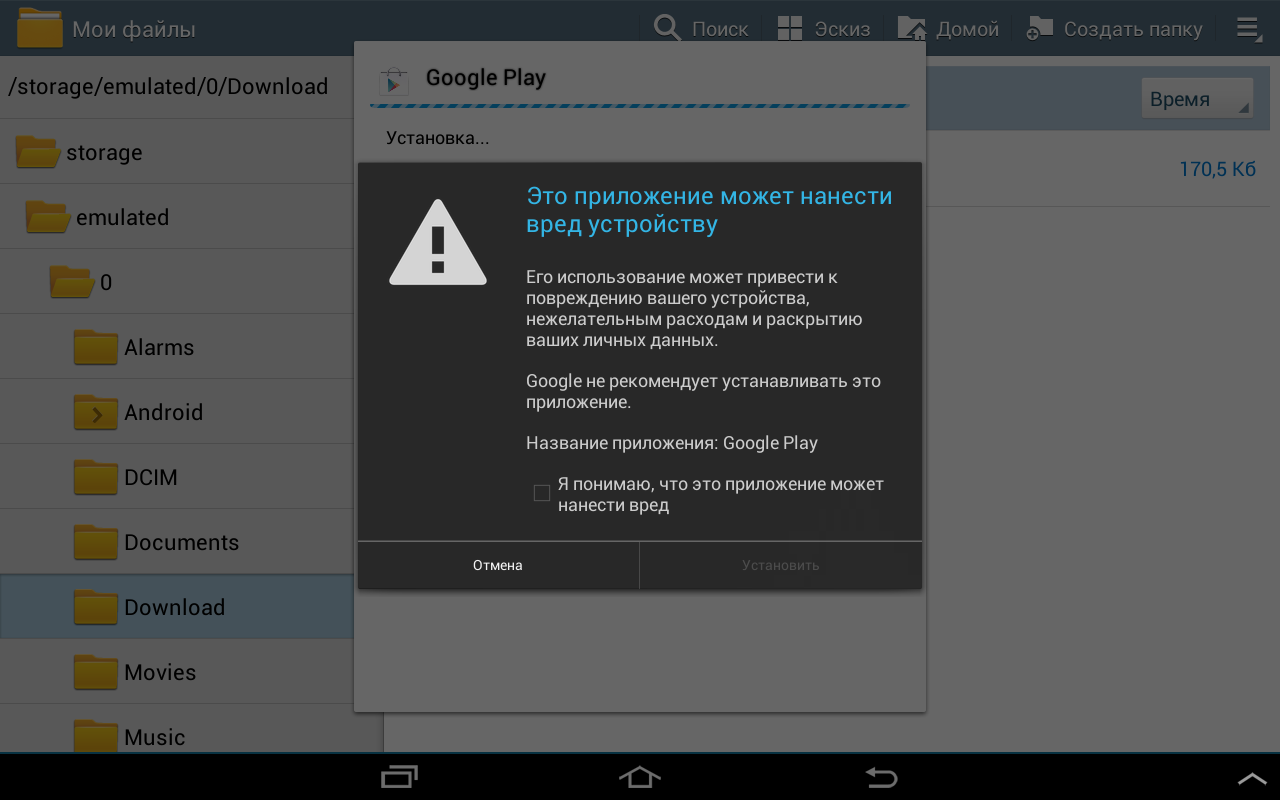
Installing. Terrified by the number of permission (s). The operating system kindly warns:
This application may harm the device.But I’m not looking for easy ways, therefore, “reluctantly,” I check the box “I understand that this application can be harmful.”
Installation process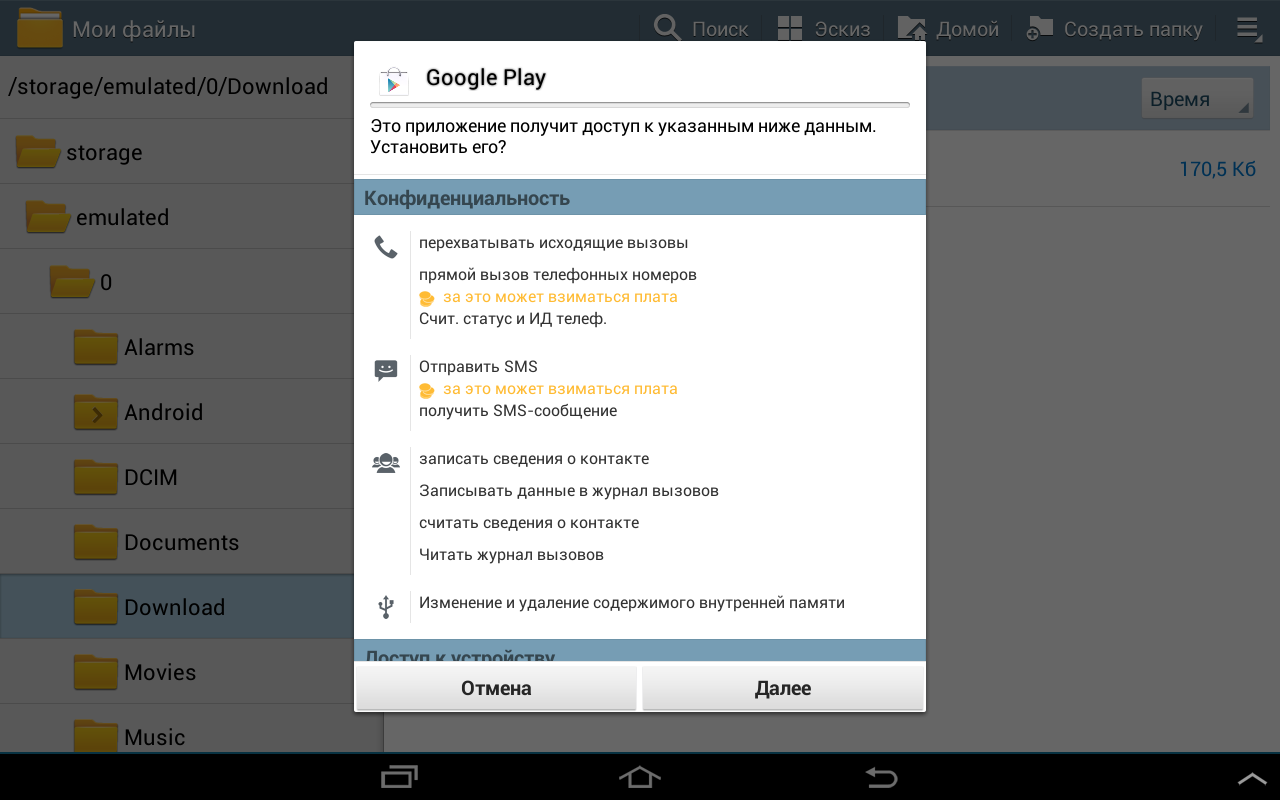





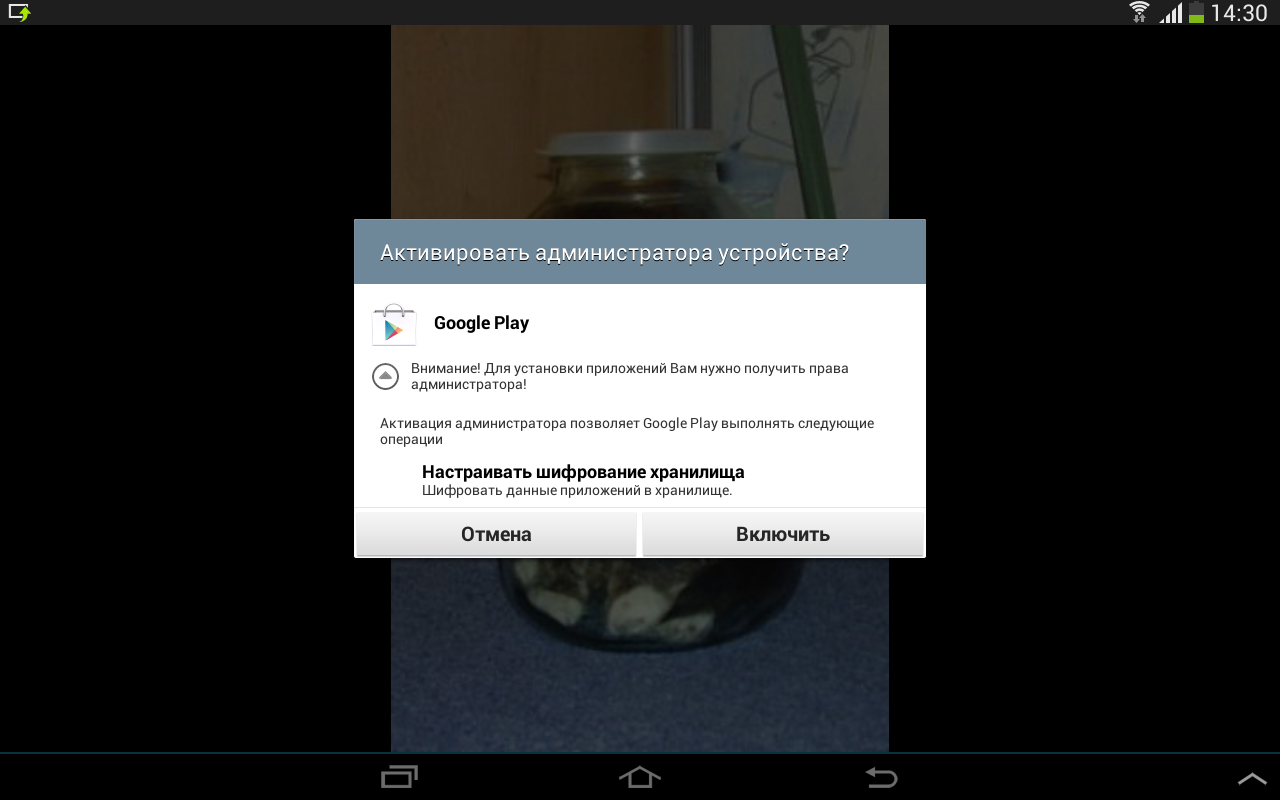
When an application asks for administrator rights, I understand that this is the last step. I click "Cancel", but the dialog appears again. Eh, I wasn’t, I will go to the end, and I click “Enable”.
3. Virus application
The application itself consists of one activity-picture with a doomed kitten. Probably in this way the developer tried to joke.

At this point, I’ll get ahead a bit (see section 6) and give the AndroidManifest.xml code for a better understanding of the article.
AndroidManifest.xml
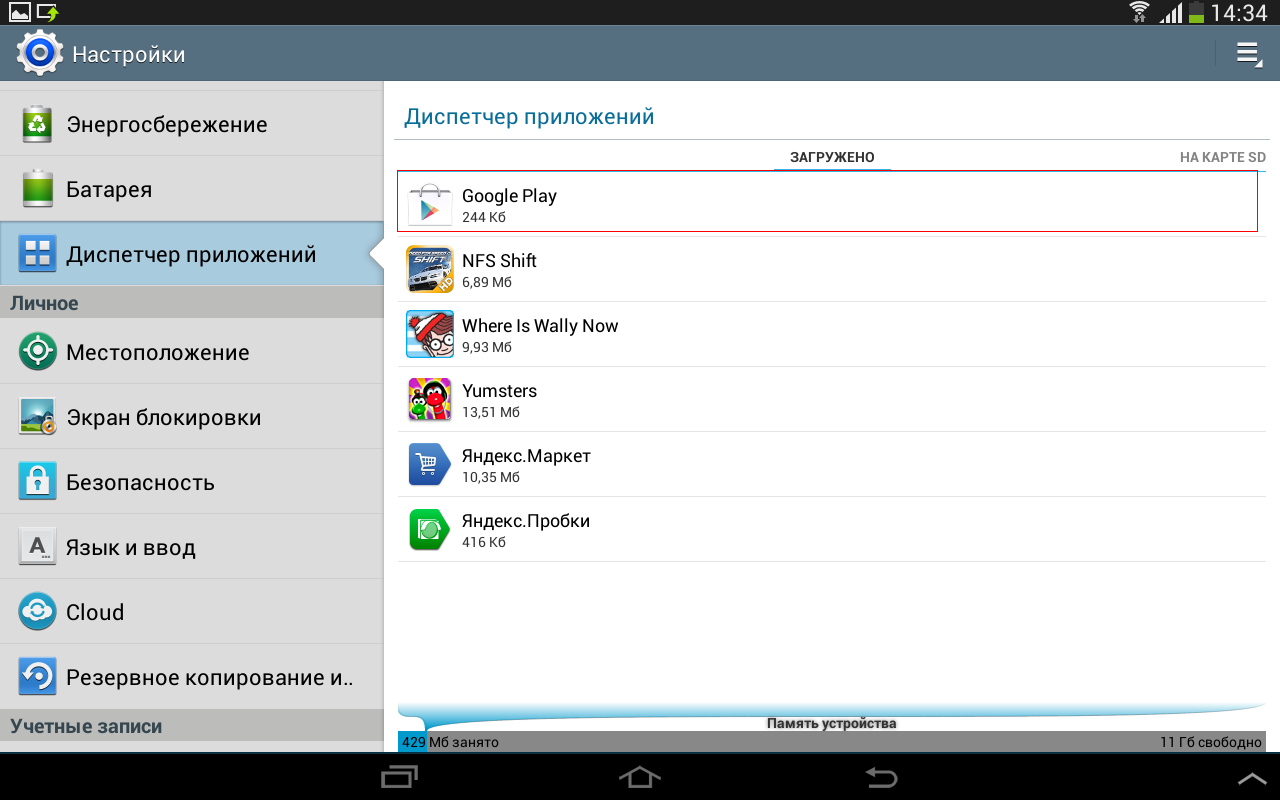
In the application manager, our "malware" is proudly called "Google Play."
4. Removal?
Safely infecting the device, I proceed to the treatment phase. First I try to uninstall the application. I go to the "Application Manager" and see that all the buttons are locked.
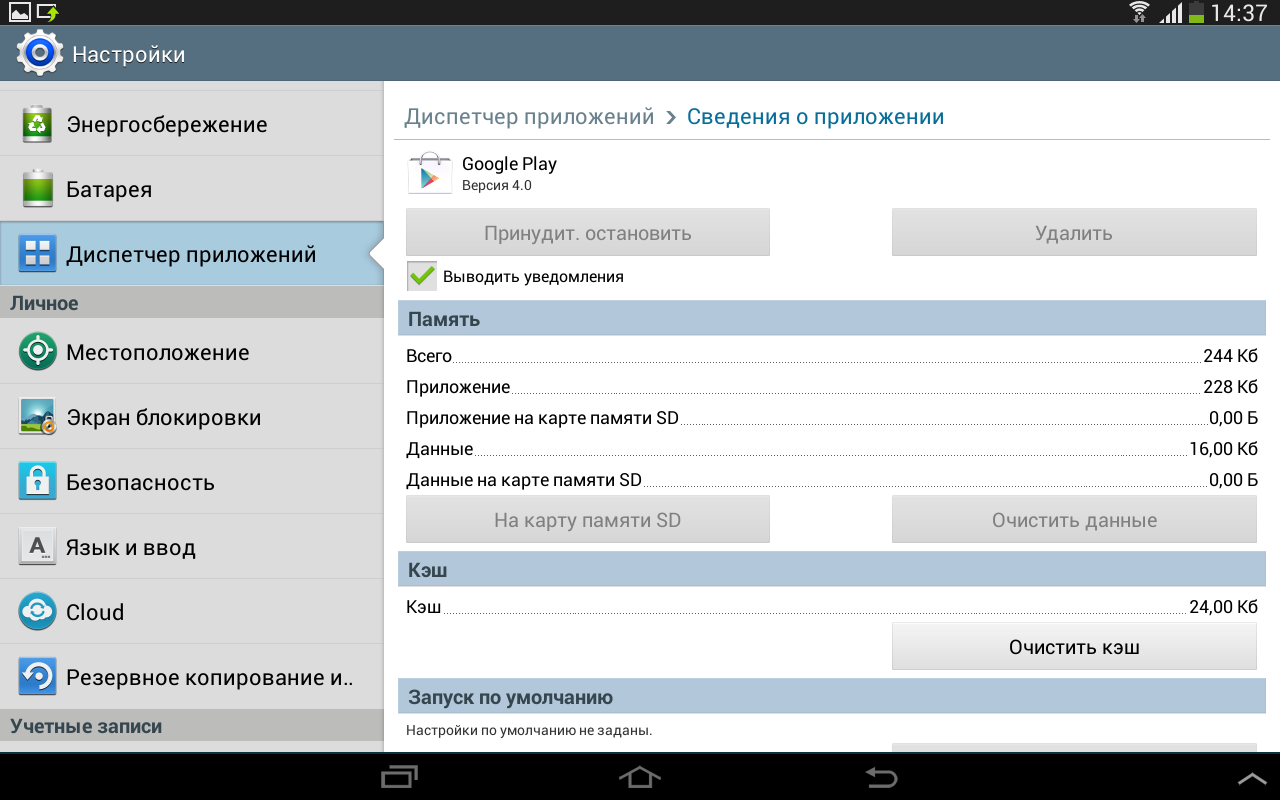
It’s clear, that means the application has administrator rights and it won’t be so easy to delete it. It doesn’t matter, now I’ll remove them. I go to the menu item "Security" -> "Device Administrators" and uncheck the box next to the application.
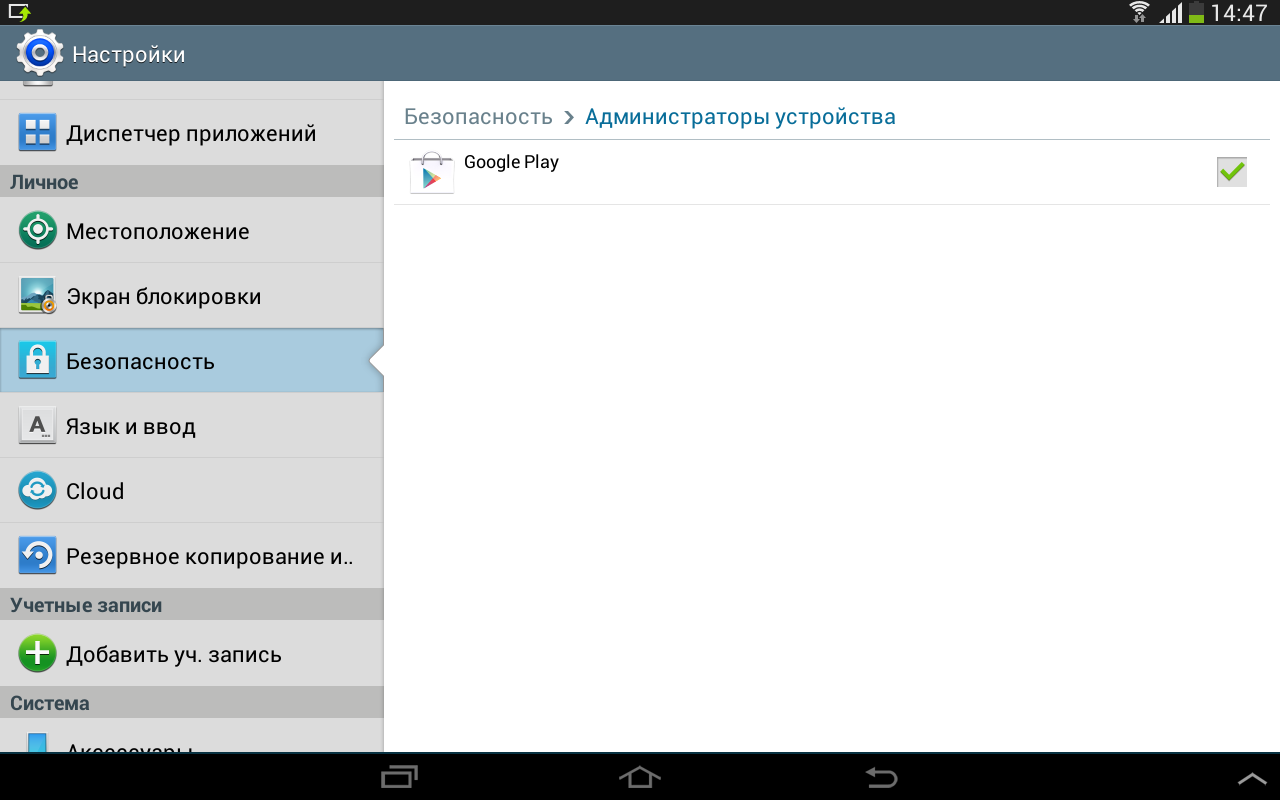
But, no, it wasn’t here. The device safely switches to the WiFi control settings and freezes. I had to “beat" the settings window.
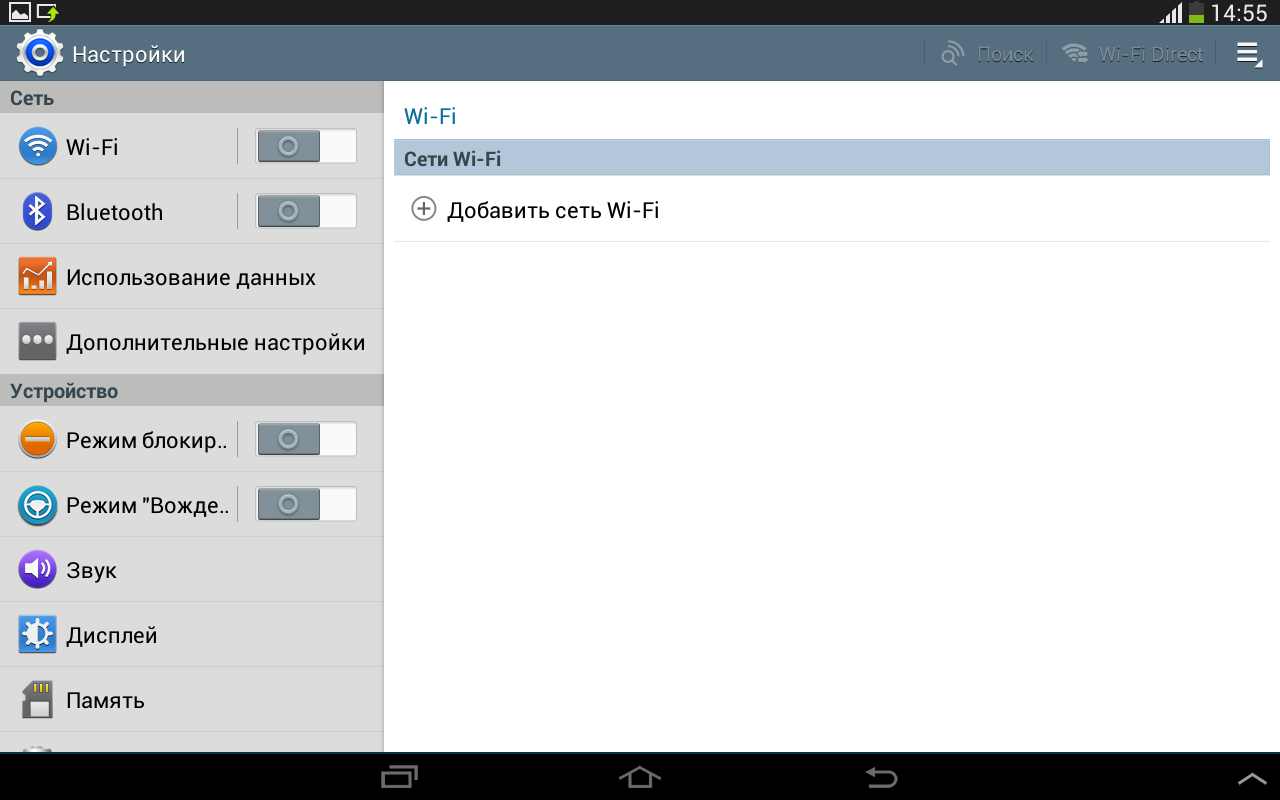
Then I wanted to solve the problem “in the bud,” so to speak, and take advantage of the general reset of the system. Well, yes, it’s easy for me to choose this option - my personal data is stored in backup.
But what about ordinary users? Which "suddenly" your favorite phone is infected with a virus. After all, they won’t even make an outgoing call to a familiar “tyco programmer”. In general, cheating is, I will not do so.
Bottom line: it was not possible to neutralize the threat with regular means. We connect the "heavy artillery."
Note for companies
In subsequent sections, a description of the actions associated with the use of free versions of the products of some companies is used. The purpose of the story is not complaints about companies or the services they provide.
5. Dr Web vs virus
Mindful of the good curing utility “Dr.Web CureIt!”, I decided to fight the malware using an analogue for Android. I go to the official website and download the free version of Dr.Web for Android Light 9 antivirus.
Install, update signatures via WiFi.
I run a quick check - nothing.
I run a full scan - nothing too.
Check progress
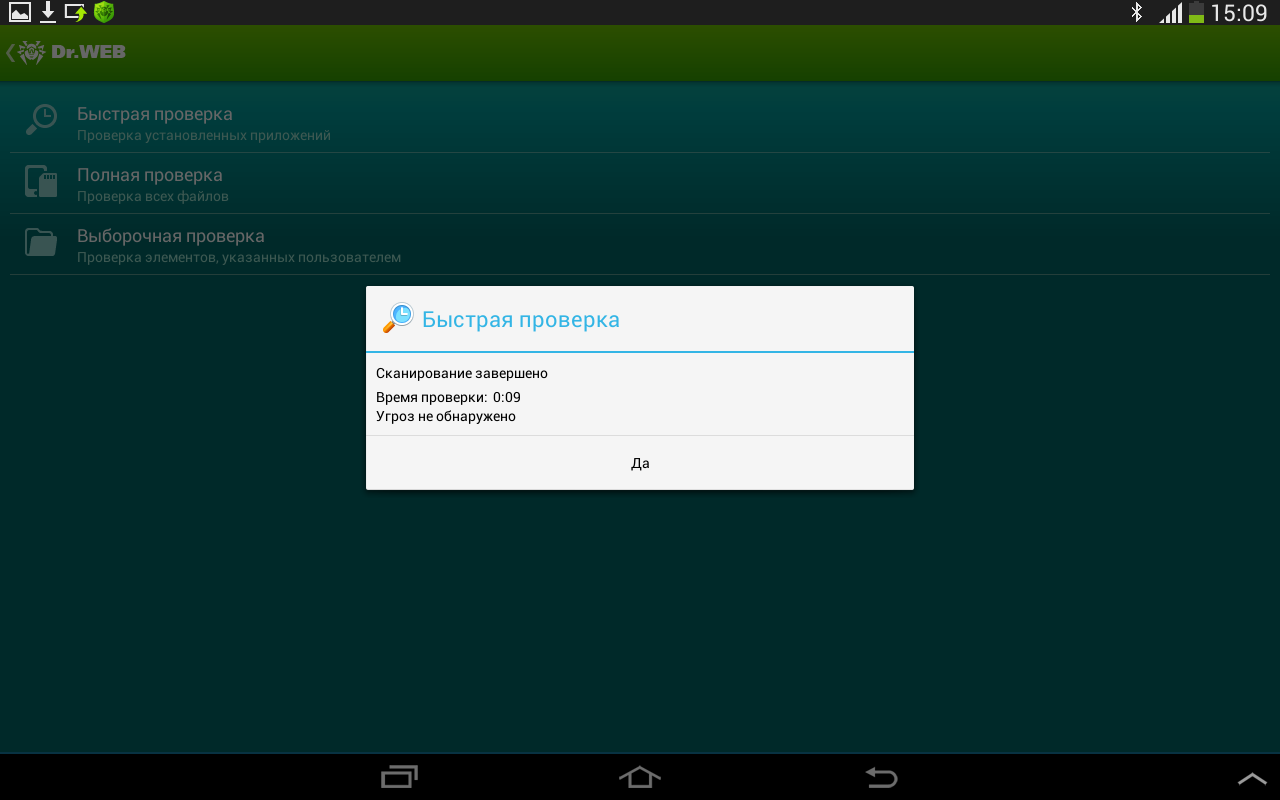
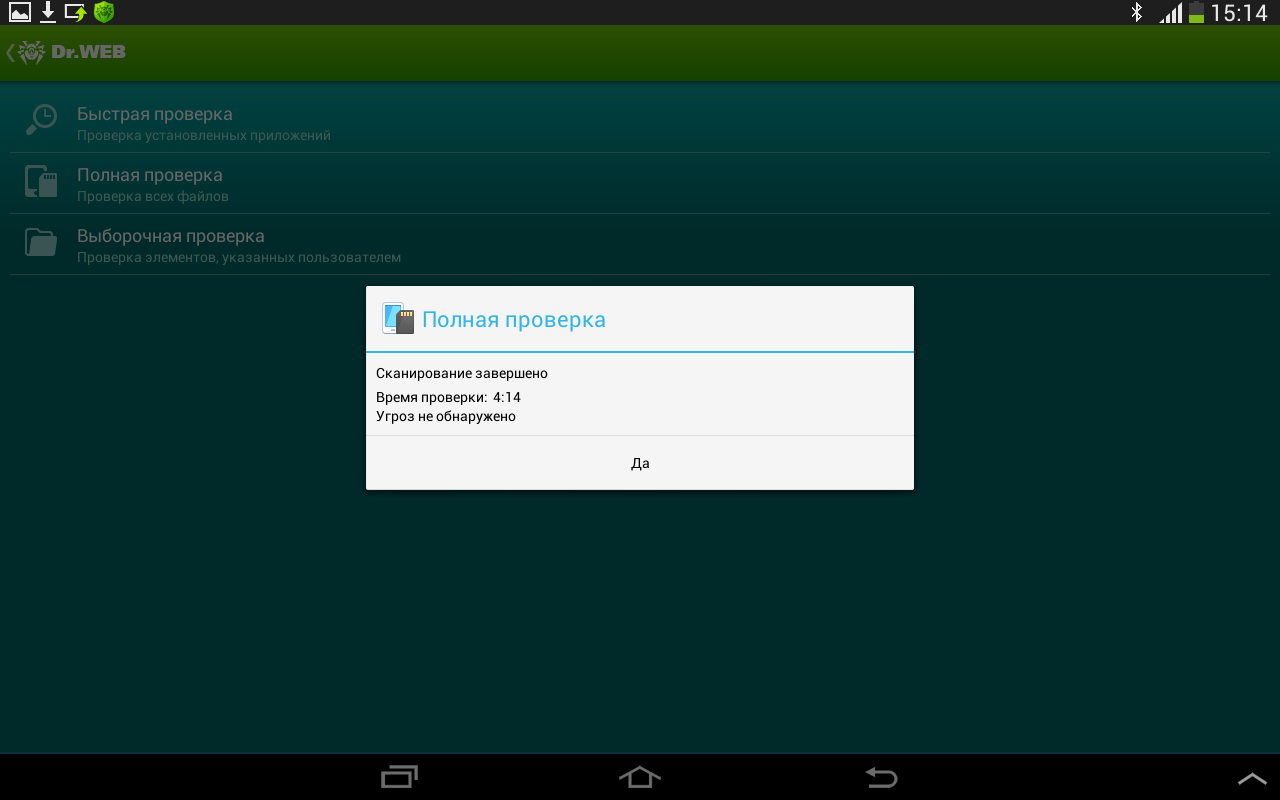



I am disappointed! Sighing sadly, I delete the antivirus program.
UPD from 09/06/14. At the moment, the antivirus program successfully identifies this malware under the Android.SmsBot.origin.165 detection. The deletion algorithm is the same as when using Avast (see below).
5. Avast against the virus
Opinion of the author
I never really liked the antivirus of this company. Especially after the story of deleting the tcp / ip protocol file in Windows XP . But what the "devil does not joke", we establish.
Download and install the version of "Avast-Mobile-Security-v3-0-7700".
At startup, an express scan is launched, which does not find any viruses in the system.
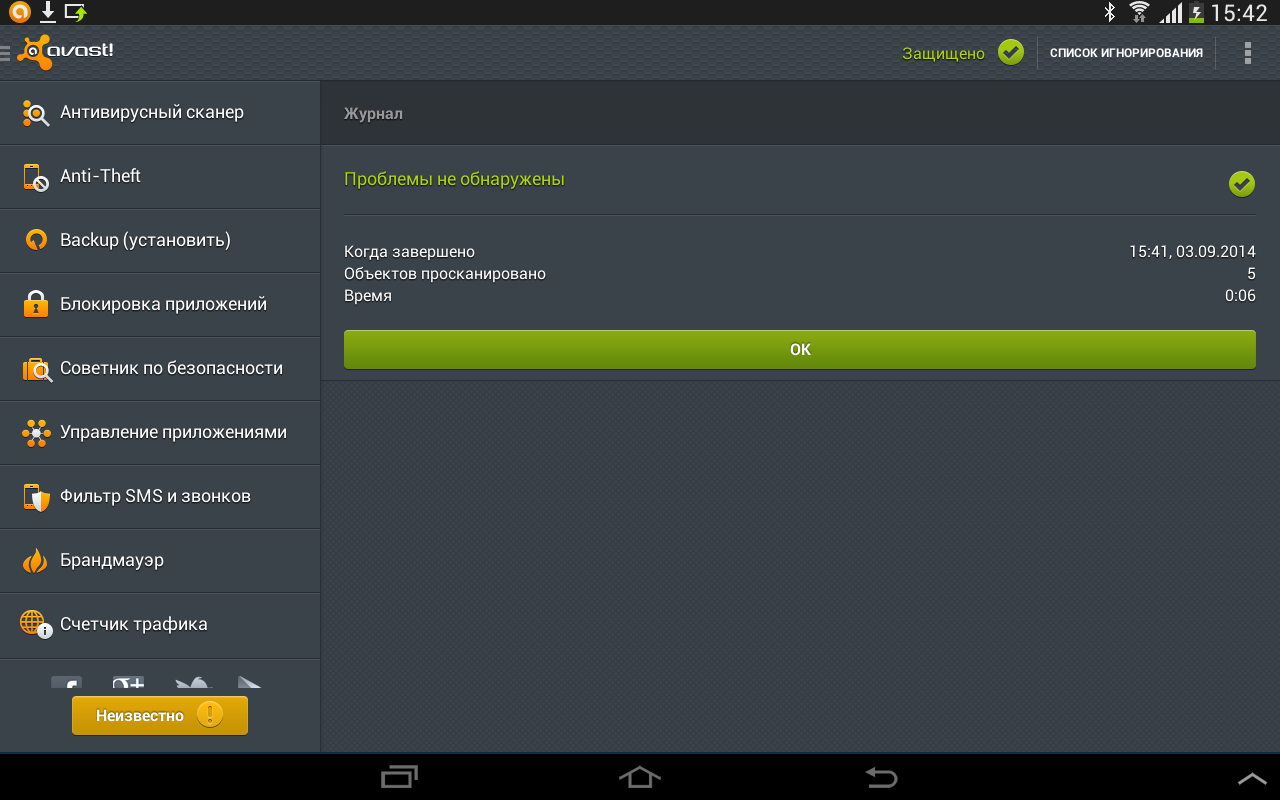
Well, okay, the brain prompted another idea: there is some menu item "Application Management", and what if ...
Yes, the list of applications in the system really loaded.

There is no “Delete” item. Therefore, I try to stop the application. It has stopped.
I wait 2-3 seconds, the application is back in operation.
Okay, I’ll try the other way. I run a forced system check. O_o, malware detected. Click “Repair All” [approx. somehow it sounds like Darth Vader or the Daleks]. Avast reports that it cannot delete the application, but you must first take away administrator rights from the application. A system dialog appears:
Delete all data from the device and restore the factory settings? Click “Yes” if you agree, or “No” to cancel
And immediately, on top of this dialog box, the "ill-fated" wi-fi settings window opens. I click "Return", the settings open again. Well, at least the settings window does not freeze.
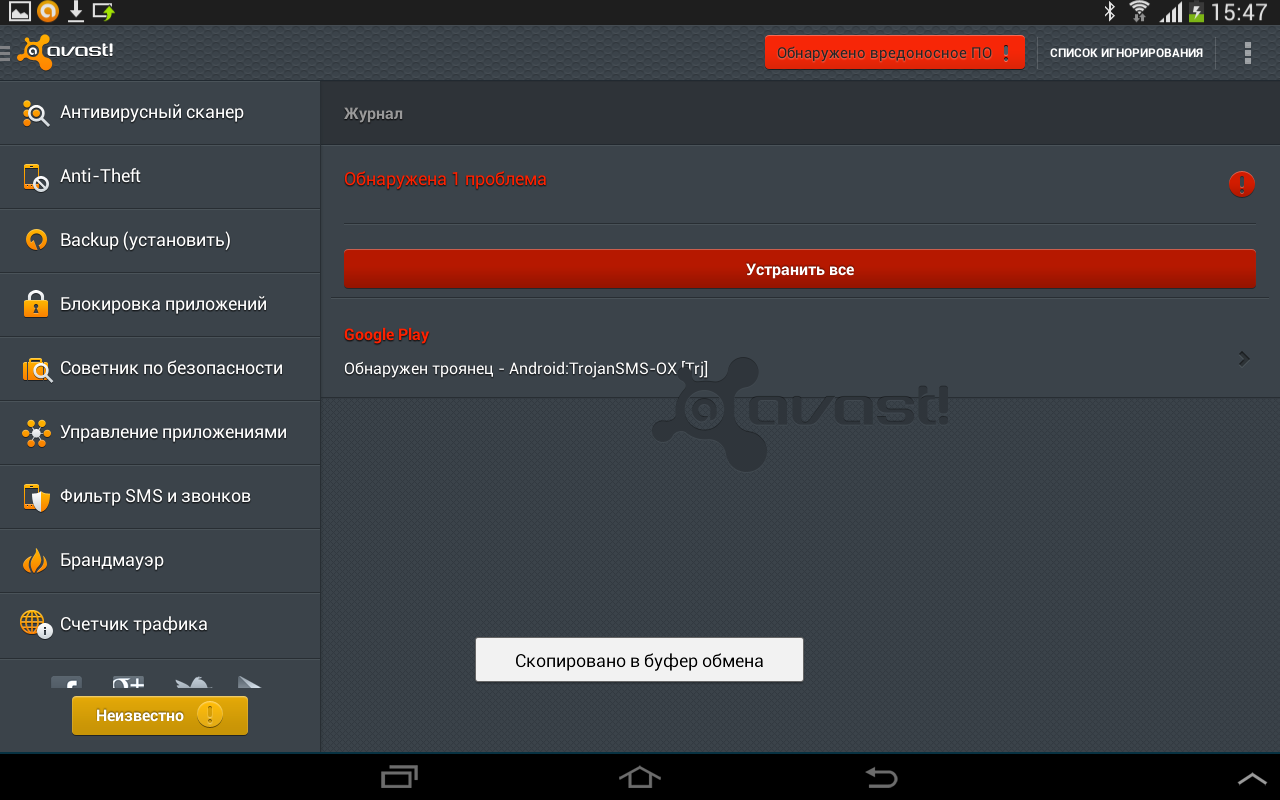
Again on the cheating path they push me. We will look for another solution ...
6. Reverse engineering
Let's look at the source code of the application, the benefit on Android is not such a big problem. A lot of interesting things ...
For example, in the SystemService class, the url of the site lamour.byethost5.com (design studio) is specified.
But most of all I liked the AdminReceiver class, which is the descendant of the DeviceAdminReceiver system class.
In this class, there is an overridden onDisableRequested method that fires when administrator privileges are disabled for this application. It is impossible to completely lock the buttons in the system dialog, therefore the virus developer went to the trick, he changed the message text to “Delete all data from the device and restore factory settings?” Click “Yes” if you agree, or “No” to cancel ”and generously covered the intrusive settings window from above.
Bingo. So now I can safely click "Delete" in this dialog box and the tablet will be "healthy."
Afterword
Thus, having repeated step 5 of this publication (without stopping at the last step), the virus version 4.0 (according to the manifest file) was defeated.
Why couldn’t it be possible to directly remove the checkmark from admin settings for the application, but only using Avast? Most likely, there is another trap with an overridden method.
conclusions
Virus developers are finding new loopholes.
But, one way or another, the browser and the operating system have become better at protecting users.
I needed to press 2 confirmations and put a tick in the settings “Unknown devices”.
Be healthy, you and your devices!
