VariFlight ADS-B - Flightradar in Chinese
“Flightradar”, in some way, has become a household name, in effect replacing the concept of “a site where you can watch aircraft in real time” . Although in fact there are several such large sites, and smaller projects are even more, but it is often possible to see in the media news about an aviation event with the phrase “according to Flightradar website” and a screenshot from another resource.
On Habré there are a number of publications about radar sports, in which or in the comments to which not only the Flightradar is mentioned. In this publication I will talk about the Chinese service for tracking air traffic and its similar Chinese ADSB receiver, which they send out for free.

Radarspotting is quite an interesting activity to captivate a significant number of people. Several articles on Habré describe well the essence of the lesson:
The receiver receives, transmitted by airplanes, a signal at a frequency of 1090 MHz, decrypts and sends in some format. For example:
This activity is not only interesting, but has become the activity of several companies:
Few people think about what they do for a living and how services like Flightradar work. An example of this can be seen in ru.vikipedii " public web service, allowing real-time monitoring of the position of aircraft in the air ." The article itself and the title give a false impression of Flightradar as a kind of entertainment service.
In fact, having emerged in the early 2000s as a hobby, these companies quickly reached a payback period and each year increase revenue. For example, Flightaware, founded in 2005, became profitable already in 2006, earning more than $ 1M in the first 18 months, and showing an annual growth of 40-75%. According to some resources, the annual income of Flightaware exceeds $ 9M, and Flightradar - more than $ 2M.
If in Europe there is a Flightradar, in the USA - Flightaware, then in China there is a VariFlight. In the same way, the service, which sells flight statuses, statistical data and archives of flights, performs analysis and forecasting for customers - organizations and individual clients.
VariFlight own words:
Companies trade data, both their own and those received, for example, from the US Federal Aviation Administration. But the greatest profit can be obtained from its own receivers, the operation of which the company does not cost anything because they are installed by radarspot enthusiasts, you only need to spend money on manufacturing and shipping. Therefore, at some point companies began to sell and send their receivers for free. Free to where the company does not yet have coverage with its network of receivers and where there is no data.
The cost of the data justifies the “free” distribution of receivers (note the text below the table - the receiver remains in the ownership of Flightaware, formally rented out for free).
By 2015, Flightradar had more than 8,000 active receivers in the network, Flightaware had about 4,500. But Flightaware began distributing receivers two years before, and Flightradar had built its network for almost a decade by that time. At this time , Flightaware has more than 15,000 receivers. Flightaware receivers software is constantly being improved on this and FMSDATA, FMSWX.
Location map of receivers in March 2017:

Orange - for free distributed Flightaware receivers, white - homemade receivers, red - PlanePlotter paid program .
This coverage of the Flightaware receiver network in December 2015:

And in March 2017, the Flightaware receivers network (the current state at the offsite site ) provided such coverage:
It is not always possible to install receivers, so in 2018 the data of ground receivers are supplemented with data from the Iridium NEXT satellites - “For the first time, it will be possible to continuously track aircraft anywhere in the world . ”
Blue Gray - Iridium NEXT satellite data. Green and yellow (the latter is MLAT ) are ground receiver data.
The radius of the zone covered by one station is limited by the curvature of the Earth’s surface and the obstacles covering the horizon, and is no more than 450 km at best. And in the "usual case" about 150 km. With rare tropospheric passages for this radio frequency, it is possible to look beyond the horizon. An example of the zones of maximum coverage of stations broadcasting on Planeradar.ru:

Sharp peaks in reception diagrams are just isolated cases of reception at very large distances.

The animation below shows the need to send receivers. Outside the EU / US, this hobby is not very popular. There may be a reason for the cost of the hobby and this map indirectly indicates the level of welfare, technical education, population density in the region. Perhaps a matter of practical interest - users transmitting data from their receivers receive a free Flightaware corporate account , worth $ 90 per month.
And so the situation is outlined in general terms. The market for this service is growing, the market needs more data and VariFlight has also begun to deploy its network. In April 2018, the company VariFlight announced that it is looking for volunteers to host free equipment. An example of such a message in the post on Instagram .
And in August, I came across this offer for free to order a receiver via the link http://flightadsb.feeyo.com/index/adsb?lang=en . After studying the site, I noticed that the company is looking for voluntary network participants in countries near the borders of China. And having filled out the questionnaire, I did not particularly expect that the SFD is in the area of the company's interests.

In the application you need to indicate on the map the installation location ( Installation Location ), the antenna installation floor on the building ( Floor of Installation , for example, 7/9 - the 7th floor of a 9-storey building), the nearest airport code ( Airport code - I indicated the IATA code) and download photos of the horizon from the Installation Environment . The rest is almost identical to the order on Aliexpress, except for the items Title, Nationality, Occupation, Company. Filled in English with full name.
After a couple of weeks, checking the mail, I found two emails from ADSB 展示 系统 (Display system of ADS-B) stating that the application was approved almost immediately and that the parcel had been rushing to me for a long time, having already passed the customs at that time.

In the second letter were login, password and track number of the parcel. And also the instruction that I did not notice and read when ... you know yourself, when they usually read the instructions.
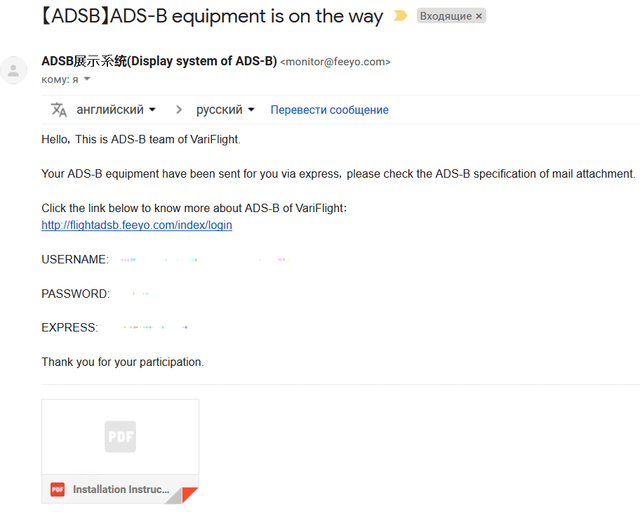
Login matched the name in the application, and the password is clearly sent the same to everyone. Therefore, we go and change the password immediately (and login if required).
In general, the phrase “This is some nonsense” from the Sudden-strike game has increasingly surfaced in my head, if anyone remembers how the Germans in the game with accent speak Russian. Sometimes quiet, sometimes loud.
By the way, the profile was the only page in English, then everything will be in Chinese. On Habré wtigga published an excellent article about the Chinese Internet "Chinese Internet and software: about sore" . I felt all the pain just now. If you have not read, then it's time to prepare.

The Google Chrome browser with the translation function will help work on the site, but many pages that were not always feasible for it.

Places will be funny phrases.

And so we log in with the data from the second email.

And go to the item Personal information . As it turned out, Google Chrome can not always translate the page or it does not succeed the first time and in this case, after a series of automatic translation attempts, I had to copy the text into Google Translate. Therefore, I post a hint for those who encounter the same problem.
The page has two tabs, the active of which is marked with a red line. At first you can not touch anything.
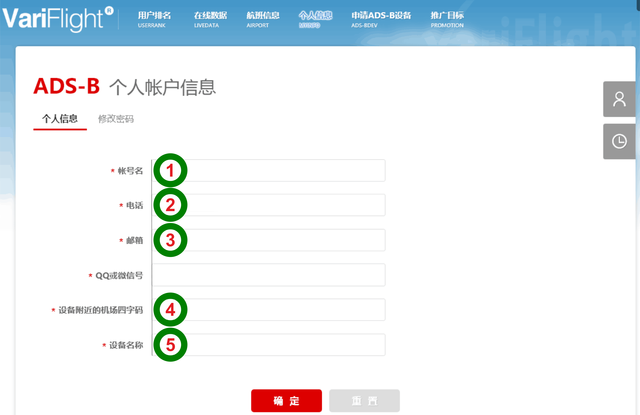
QQ item is a Chinese Tencent QQ messenger .
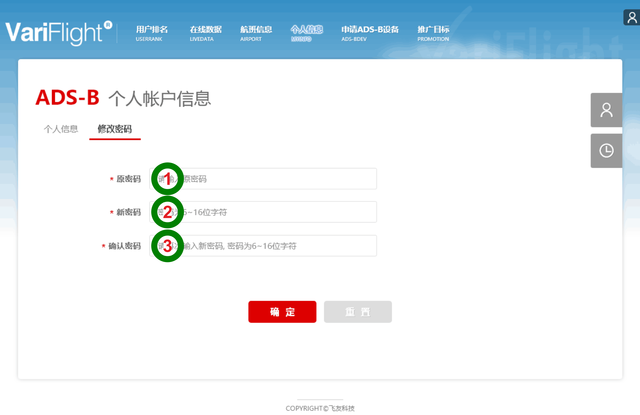
On the second tab, change password
With the exception of this, automatic translation almost always works. The site map design is very close to the Flightradar site and the “features” of the translation do not make it difficult to use.
A detailed examination of the service differs, for example, an interesting functionality that Flightaware does not have - a heat map , translated by Google Chrome as “thermal analysis”.

An interesting feature of some flights:

Probably there is no information about the airports of departure and landing of this flight.
By track number the parcel was sent on September 6 and received on September 18. The box has solid dimensions that surprised post office workers. On the way from the post office inside, something thundered, tinkled and rolled.

The open box was somewhat surprised by the lack of packaging materials.

For comparison, the box at the receiver Flightaware.

Surprisingly, the contents of the box did not suffer. Only on the antenna there was a scratch - the film was torn off.

The receiver itself has the inscription only two connectors - power and HDMI. In addition to two, all connectors are on one side. LAN, 2 USB ports, four-pin connector (assumption that this serial interface was confirmed by a dial tone on the BCM 14 (8 pin TXD / Transmit),
BCM 15 (10 pin RXD / Receive)), 5 volt power supply and SMA (female) antenna connector .

On the opposite side, behind the two holes in the housing, are green and red LEDs. And next to a sticker with the "serial number" of the receiver, recorded by hand. Also, the receiver has HDMI and microUSB.

The cover of the receiver has two ears for mounting on the wall, which positively distinguishes it from almost the same case of the Flightaware receiver, which the manufacturer provided for only four silicone feet at the bottom.

Test the ability to use these two ears for mounting the receiver:

Flightaware Flightfeeder upside down:

To compare receiver sizes:

The natural question is "what's inside?" Removing the cover, fastened with 4 screws, we see this layout.

The connectors are on a separate receiver board, made in the form of an expansion card for the Raspberry Pi 3 Model B V1.2.
For comparison, a photo Flightaware Flightfeeder (G6) without a cover. This generation of receivers sent out until about 2017. Built on RPi 2 Model B v.1.1 and mode-receiver-decoder mode-S Beast .

The reverse side of this design hid an unexpected element. Surprise is a massive radiator located on the bottom side of the board. The need for it is incomprehensible (after a week, I think this is a “tropical design.” In my conditions, the radiator is slightly warm).

Additionally, the expansion board is connected to the RPi with a four-wire connector with three wires soldered to test points PP27 (USB VCC), PP44 (USB D-),
PP45 (USB D +).

Those. nothing can be plugged into the top right USB connector. Therefore, in the photo of the case placed above, it can be seen that of the two paired USB connectors, the slot in the case is just opposite one that is closest to the LAN.

Flightaware did the same, soldering the receiver to the pins of one of the connectors.
Most of the expansion card takes a metal screen. Of the visible parts of the connectors on the same side, and on the opposite two indicators and some "coil" with taps. Reminds shunt with variable resistance. Perhaps 1div0 , the author of the article “Why bend tracks?” Knows what it is. During normal operation of the receiver, the green LED is on. In what cases it is lit red - I do not know. Not yet watched its inclusion.

On the side of the connectors there are power connectors and antennas, and a four-pin connector of unknown purpose.
All electronics are hidden under a large tin screen cover. Flightaware Flightfeeder receiver board is not shielded. At the Flightaware forum, the developers answered this question that the metal case of the receiver itself is sufficient to protect against external interference.
An attempt to look under the screen was a success from the second approach. The lid broke off and turned out ...

... as it turned out everything was in vain - the marking with chips was carefully cut down.

Looking ahead, I will say that it turned out to be an almost ordinary RTLSDR receiver - RTL2832U DVB-T (0bda: 2838), called “dongles”, “whistles”, and which are devoted to several articles on Habré that give an idea of these devices and how they have simplified and cheapened the implementation of the reception and processing of radio signals on computers. For example:
In the latter, the background is well described:
Unlike the "regular tuners" that I have, this instance of usb id 0bda: 2832 also has a 17-digit serial number.
Bus 001 Device 005: ID 0bda: 2832 Realtek Semiconductor Corp. RTL2832U DVB-T
Found Rafael Micro R820T tuner
Ie analogue to the “blue whistle” used to create homemade ADSB receivers. In the photo is the receiver on OrangePI.

Assembling the receiver back, set the radiator just in case. Bought specifically for the revision of routers and other home equipment.

Power supply 5V 2A. It looks more solid than the power supply for Flightaware Flightfeeder. But with a Chinese plug ... I tried to remember where my adapter was lying around.

In a box of white cardboard was such a pretty velvet bag.

"... in the chest - a hare, in a hare - a duck, in a duck - an egg, in an egg - a needle ..."

Inside was a puzzle of three adapters that solved the question "where is my adapter lying around."

A CA-23RP 2.5GHZ 400W Made in Japan lightning arrester appeared in a brown cardboard box. I am not aware of this configuration of other ADS-B receivers. Very reasonable for protection against small power accidents.

The indoor antenna is likely to test the receiver without installing an external antenna. Not suitable for practical use. But it is sold on Aliexpress / Ebay as an “ADS-B antenna”, but its present purpose is given on the inscription on a magnetic sole. I caught airplanes on this antenna no further than within a radius of 30-40 km.
Near adapter N (female) - SMA (male). Perhaps a gift in the event of a filter or low-noise amplifier.

Coaxial cable for antenna 5 meters with N and SMA connectors, and twisted pair 10 meters ("100% oxygen-free copper, blablabla").

Antenna cable marked KOPA PLESS RG400-KF MIL-C-17. Googling M17 / 128-RG400 RG-400 Double Braid Flexible Coaxial Cable with a different shell color:
It is very doubtful that these are characteristics of a Chinese cable. By the way, Flightaware bundled a lousy antenna cable, albeit an Italian one. Shortening the cable from the antenna to several tens of centimeters three times increased the number of received packets by the Flightaware receiver.

Outdoor antenna and its mounting to the mast.

Kuryez from the FlightFeeder ADS-B VariFlight group on Facebook:

The antenna is slightly smaller in diameter than Flightaware

Flightaware mast mount from duralumin

A gift with the symbolism of VariFlight. Judging by the inscriptions on the back - this label should cling to the luggage in case of loss at the airport, filling out contact details of the owner.


Turning on the power in principle did not change anything in the appearance of the device. Only LAN indicators were lit, the router has a new host name raspberrypi in the list of issued dhcp IP addresses. On HDMI, there was a normal RPi boot output and a login request.

And that's all. The expected web interface for such devices at IP: 8080 was unavailable. The port scan of the device found only port 22. Attempting to log in as the default user and password was sent far away to both the console and ssh:
The receiver turned on and off several times, remained for days on the assumption that it could download something at that time or try to reach servers in China. Neither the red nor the green indicator lights up.
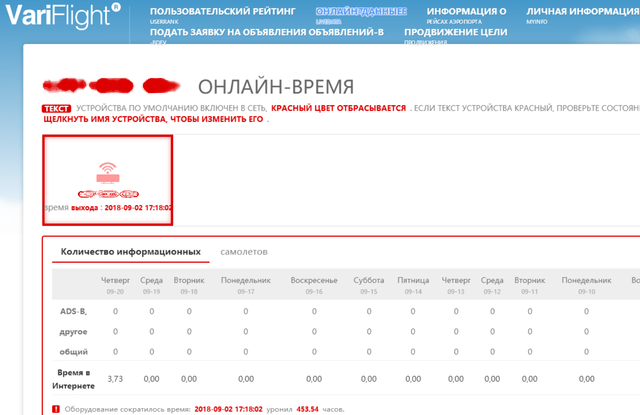
At this time, I went off-site looking for an FAQ, technical support or something else that could tell what this device should and should not do. I logged in for the first time, but this didn’t fundamentally change anything - there are no contact forms or feedback forms. The only thing that was found was that the receiver was tied to an account and had the status offline. I noticed that the system last saw it on the network on September 2 at 17.18 Beijing time, 4 days before being sent by mail. Those. He was checked and connected to the account.
After spending a couple of days in ferment on the sites of the Chinese Internet, which somehow linked to offsite or to which links from offsite were, and tired of their original design, I realized that there was no technical support for this product. And at that moment I remembered two emails from ADSB 展示 系统 (Display system of ADS-B).
“This is some kind of nonsense” - once again I heard a familiar voice with an accent in my head. My email to this address was turned back by PostMaster feeyo.com

And then the eye caught the attachment to the second letter, which had previously eluded the view (due to the unusual GMail design). This turned out to be a VariFlight ADS-B installation manual. It's time to find out how it was supposed to work.
Below is a translation of the instructions in 6 pages and two languages, most of which are occupied by illustrations.

The VariFlight ADS-B is equipment designed for civil aviation enthusiasts to track aircraft. The kit consists of an ADS-B receiver, power supply, patch cord (patch cord), antenna and cable for it.

The external antenna must be fixed on the outside of the building, as high as possible above the obstacles to the radio signal; installation on the roof is preferred. Otherwise, ADS-B signals will be absorbed by obstacles such as a wall or a building.

After installing the antenna, you need to connect the ADS-B receiver to the Internet by following these steps:

The Internet should connect automatically as soon as you complete these three steps above. Static IP is not supported, only DHCP.


Method one.
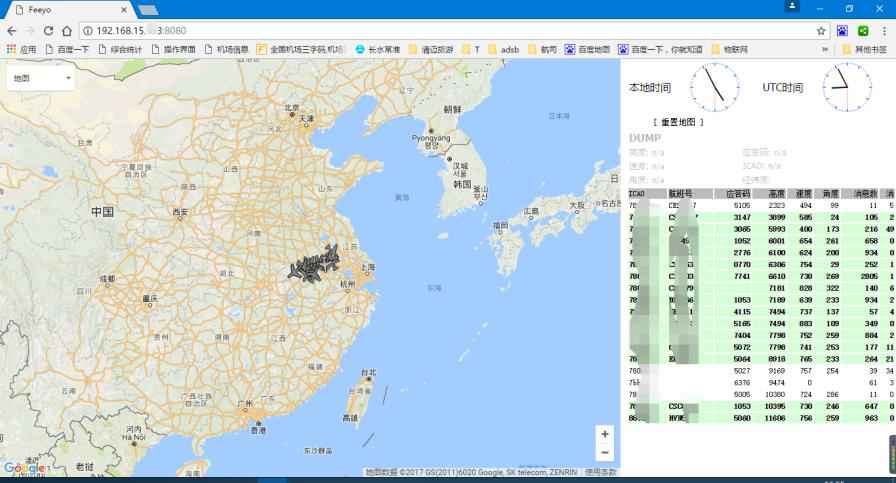
In the settings of your router, find the IP address of the ADS-B receiver and open http // XXX.XXX.XXX: 8080 in a web browser, where XXX.XXX.XXX is the internal IP address on your local network.
Method two
Open the link flightadsb.variflight.com in your web browser, log in, and click on the item Airport

Method three, only for Chinese volunteers
For Chinese users, we can use WeChat.
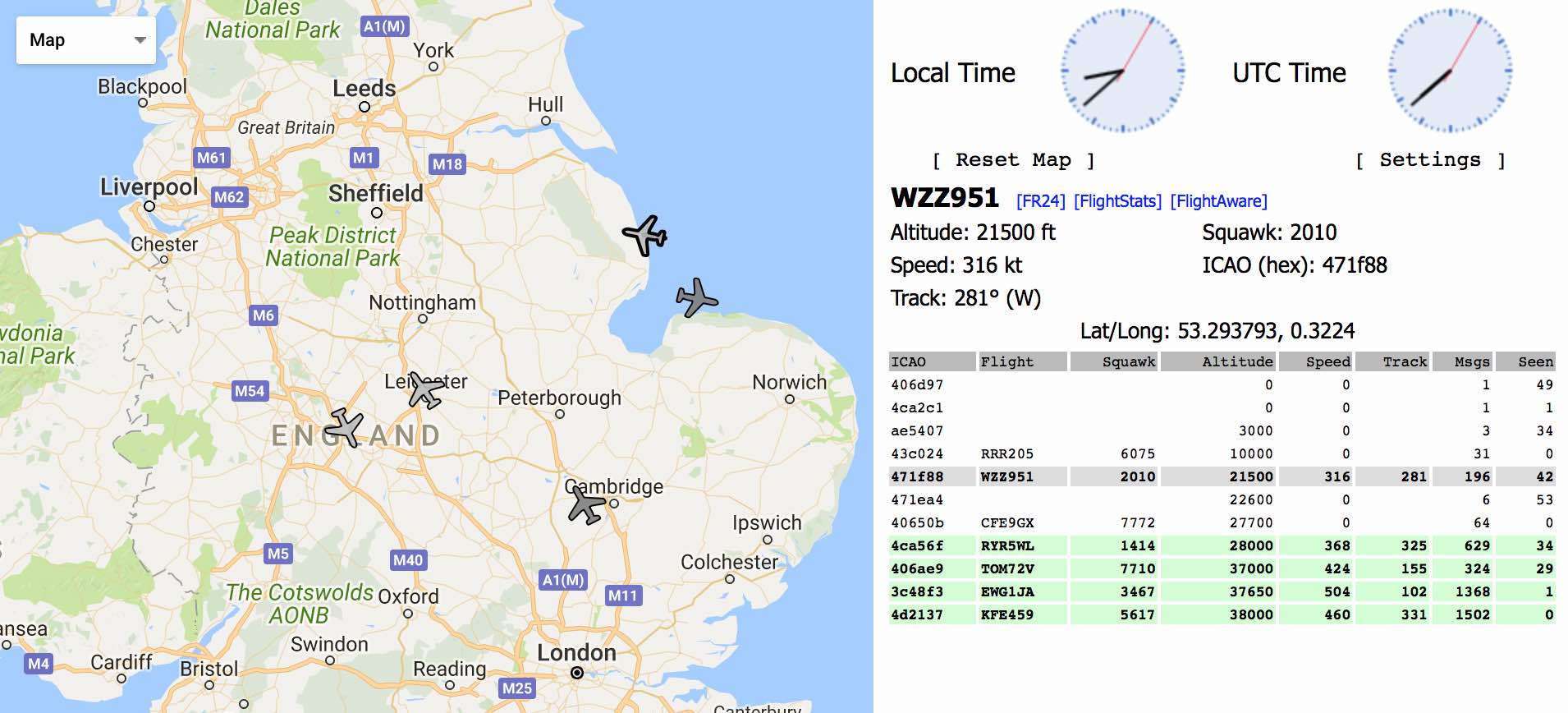
On this instruction over. In accordance with this instruction, the device works partially - it receives IP on the local network, but does not display the web interface, in which you can find out the dump1090 - Mode S decoder, created for RTLSDR dongles and used in similar devices.
Without working dump1090, no data will be sent to the server. It is strange that the device somehow worked when checking before sending. "This is some kind of nonsense." Since the Chinese are not interested in the device’s fate in any way, and I couldn’t find any signs of technical support, my conscience is completely clear if I try to repair it myself.
Having disassembled the receiver, immediately upon receipt, I made a microSD image in the state before the first power up and studied the contents a bit, immediately suspecting as the receiver sends data to the server - there were files and scripts with service addresses in / root /.
Instructions on changing the “forgotten password” with pictures can be found at this link .
I disassemble the receiver again. To get to the microSD you need to unscrew all the screws and pull out both the boards. Later on, while working with the receiver, I did not assemble it back into the case. I had to replace two microSD with different systems.
We take out the microSD from Rpi, make a backup copy on the computer, if not already done, and edit the file - cmdline.txt .
Add to the end of this line
We return the microSD back to RPi, connect the monitor and keyboard. Connect the power. When the lines stop running on the screen, press Enter. The console prompt appears, in which we type
The lines run again and again wait for them to stop running, then turn it off. We take out microSD from RPi. On the computer, edit or restore a backup copy of cmdline.txt - delete “init = / bin / sh”.
For the last time, we return microSD back to RPi. Turn on. Successfully log in with a new password. Enable ssh by typing raspi-config and selecting SSH from the menu.
Then, using the top command, I want to see what the receiver lives with and suddenly notice wget processes and ... dump-1090. Silent scene. I check in the web browser http // XXX.XXX.XXX: 8080 - there is an interface.
Not to say that it was unexpected, but definitely unusual. From the instructions I check Method Two - everything is fine there too: the receiver's icon turned green, and below there was a list of airplanes that he heard.
It would be possible to finish this, but first of all it would be inexcusable to use RPi3 for this. And secondly, if this device worked stably. For example, it disappeared from the list of IP addresses of the DHCP router, while it was available when accessing the previously received IP, and at the same time there was no image on HDMI. But the most important was the instability of the broadcast. According to statistics on the receiver page, it worked several hours a day. Sometimes a full day, sometimes several hours, sometimes zero hours. It took several days to study the system - not every software was installed. Chinese repositories ... The German voice finally convinced that it was necessary to make a healthy person's ADS-B receiver, and for this you need to roll up the PiAware image on another microSD. The original microSD is still useful to find out how it works.At least save files from / root. Preferably make an image.
PiAware - Linux software for transferring flight data to FlightAware. Contains fork dump1090-mutability. According to the developers, one of the differences is that it does not send packages to the FlightAware server if they do not differ from the first one. Those. if the plane did not change the speed, altitude, then this data should not be processed, and thus reduces the load on the server.
About two years ago, FlightAware began translating texts on the site into Russian. And much to create your own station PiAware can be found offsite . The essence of creating a station on RPi with RTLSDR comes down to writing to the microSD the finished image of PiAware on Raspbian Linux using Etcher. Further, before you insert the card in RPi and wait for the download, you need to make some changes. To enable SSH access, create an empty file with no extension called ssh in the boot partition. And in the piaware-config.txt file, you can make the necessary settings , for example, specify a static IP or enable WiFi and specify an SSID / password, provided that a supported USB WiFi adapter is connected. The same settings can be made from the console with the command piaware-config Setting_ Possible_values .
If you already have a Flightaware account, then in 5 minutes the station will become attached to the account by receiving a Unique Identifier. And the receiver will have its own statistics page.
By default, user PI has the password flightaware. It’s a good idea to change your password right away.
Tests in quotes, just impressions. Having two devices with almost the same software, you can evaluate their abilities.
I have a free Flightaware receiver and the first thing I experienced was a complete VariFlight antenna. I just replaced it with a Flightaware antenna. And while studying the VariFlight receiver, FlightFeeder statistics was collected on the Flightaware page. The conclusion is disappointing. Although the maximum range, nothing has changed, like FlightFeeder, in the direction of the line of sight, catching some at a distance of 400 km, but the statistics of aircraft per hour / day slipped by 2-3 times. Sure takes the board for 300+ kilometers, but sees a little less messages. What I do not know inside the case of the antenna itself is not collapsible.
A Flightaware antenna was connected to the VariFlight receiver and it showed statistics of the same order. And with a native antenna even lower.
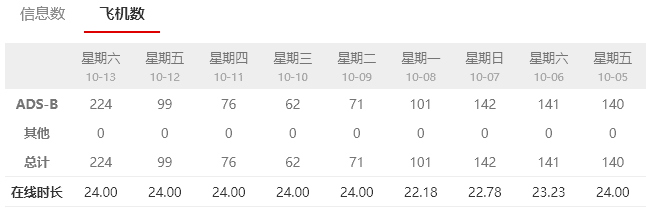
I decipher the statistics. Statistics from 10-05 to 10-07 is the VariFlight receiver with Flightaware antenna. 10-08 the complete antenna was connected and from 10-09 to 10-11 the statistics of the VariFlight kit. 10-12 The send_message.py script has been modified to collect data from Flightaware Flightfeeder. After that, data from it and 10-13 daily statistics based on Flightaware Flightfeeder data went to VariFlight. Further more, for example, for 10-18 - 396 flights, 814176 packages, for 10-19 - 471 flights, 860415 packages.
Let's estimate how the receiver VariFlight is subject to radio interference. To do this, we scan the 800 MHz-1200 MHz range and generate a heat map.
After half an hour (-e 30m), scanning stops and generate an image.
Reboot the device to restore the work of dump1090.
And copy the resulting image to a computer using (win) scp.
This is a fragment of a thermal scan map around 1090 MHz. Full image is available by click.

Bright yellow stripes is a mobile connection. Nothing out of the ordinary - he has no prefilters like the Flightfeeder, and he is greatly hampered by mobile stations. In this, it is absolutely the same as the simple “blue whistle” mentioned earlier. Manufacturing in the form of a special expansion card is possible; it makes some sense, for example, the role of “curved tracks” on this board is incomprehensible. Making a specialized board it would not be difficult to install both a low-noise amplifier and a SAW filter at 1090 MHz. Just looking at the scripts in the device, I had an idea why this was done - one script is called acars.py.

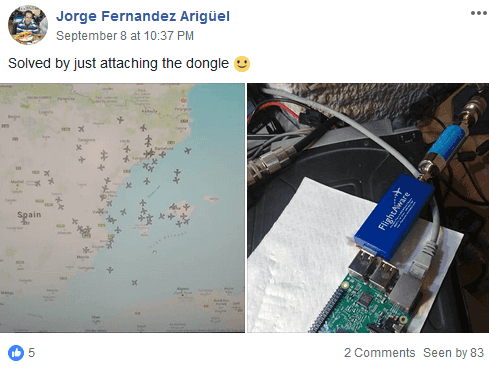
As far as the amplifier and filter would improve the characteristics of the receiver shows an example from the above-mentioned group on Facebook. One of the VariFlight Box users connected a specialized dongle from Flightaware instead of a regular receiver, which brought it to the top of the rating from about a thousand users (of course, the installation location and another antenna also affected).
FlightAware launches two dongle models — Pro Stick and Pro Stick Plus, which are still the same “blue whistle” but have a preamplifier, and the latter additionally has a SAW filter that eliminates unnecessary signals in areas with a lot of interference, for example in cities, as well as these models are equipped with an SMA antenna connector. These dongles are used in Flightaware Flightfeeder “orange” receivers.

The name of the script “acars.py” hints that the absence of any filters is not an error and economy. Address and reporting system of aviation communication(Eng. Aircraft Communications Addressing and Reporting System, ACARS) - a digital radio communication system used in aviation for the transmission of short messages between the aircraft and ground stations. The operating frequency for ACARS in Europe is 131.725 MHz. Therefore, the device can not have a filter only for 1090 MHz, otherwise it will not be able to receive a signal at 131 MHz. What is inside the antenna is unknown, I am not going to break it, but it is obvious that its “wide coverage” is also provided by the creators. Similarly, the method above generated a heat map in the range of 100 MHz-500 MHz. Fragment of the thermal scan map around 450 MHz. The full image is also available by click.

On the heat map are visible control panels, security sensors, wireless door bells, wireless weather station sensors, radio amateurs, FM radio stations, and so on and so forth.
For example, by setting rtl_433, you can see the data of the neighboring wireless sensors of weather stations and, if desired, use them as the author of this article .
And by running rtl_tcp, you can listen to radio amateurs and FM radio.

Interestingly, not all radio amateurs exactly hold the frequency. It was amusing to see how the radio amateurs rated the interlocutor as audible, and the frequency of one of the radio stations was somewhere off to the side.
But the Chinese receiver on the native system showed accuracy - 0 PPM. On the method of measuring PPM can be read on Habré in the article quwy "Once again on the reception of HF on RTL-SDR" . It is highly desirable to adjust the PPM for best reception. What the Chinese did. Piaware has a small error that can and should be removed by specifying the correct PPM value with the command sudo piaware-config rtlsdr-ppm <PPM value>.
As a result, we can say that the VariFlight receiver for iron is little better than what you can assemble yourself. This is a good base to start practicing this hobby (and showed tests of iron, it can be used for a wide range of other tasks. Especially since there are three free USB ports).
The unique disadvantage of an ADSB receiver is the software and the Chinese interface of the site. If nothing can be done with the Chinese website, then you can modify the software of the receiver itself. The easiest way is to install PiAware and set up distribution on VariFlight. Then you can set up distribution on Flightradar24 and get an account with special conditions there. An example of using an account with special features is access to the archived data of Flightaware (the crash of the An-148 Saratov Airlines).
Returning to the contents of the root directory. It can be found on github . The names of the files clearly hint at their functions.
From the last install.sh lines, you can see that cron adds two tasks — run task.sh every minute and synctime.sh every 6 days.
The script task.sh, run every minute by cron, checks and, if necessary, restarts dump1090, the send_message.py and get_ip.py scripts.
The get_message directory contains python scripts, one of which, send_message.py, sends data.
The init.sh script checks if there is an update and installs a new send_message.py
I especially do not understand the meaning of the network exchange performed by the script. A unique UUID is generated if it is missing. And there is a certain exchange with the addresses specified in the config.ini file. Probably this script is responsible for linking the translated data and IP to the account.
Noteworthy is the line "if request_json ['type'] == 'reboot': os.system ('/ sbin / reboot')".
Finally, the script sends the data.
I edited the serverHost = 'localhost' string, replacing 'localhost' with 'ff-1234' —the network name of my Flightaware Flightfeeder and rebooting the VariFlight receiver. After that, the data from the Flightfeeder went to VariFlight.
The remaining scripts are receiving ACARS messages. Perhaps the remnants of a functional or a function implemented in the future. Scripts work with /root/acarsdec-3.0/acarsdec, which is missing along this path. ACARSDEC is an ACARS SDR decoder that decodes messages, for example, at a frequency of 131.725 MHz. Apparently it is precisely based on the reception of this frequency, at the receiver input there are no filters at 1090 MHz.

The acars.sh script is similar in implementation to task.sh — it restarts acarsdec and the get_ip.py and acars.py scripts if it does not detect the required process.
At work, it looks like this:
From this it is clear that you can take data from PiAware almost without straining, in fact, only by transferring scripts to a new system. And if there is already an existing adsb-station - self-made, Flightradar24, Flightaware, then the existing receiver can be used at your discretion for other personal goals and tasks with a completely clear conscience.
We transfer the necessary files to the new system from the old one. Those. the contents of the root directory: the
directory get_message and files install.sh, synctime.sh, task.sh.
In the get_message directory:
and the UUID file is your VariFlight network ID.
If you want to start sharing data without having a VariFlight Feeder, then the first time you run the script, your UUID is generated. This file and the name of the nearest airport should be sent to chengyi (at) variflight.com to create your account on the service.
Further:
Edit the crontab in nano by inserting
Save the file by pressing [Ctrl + O] and close [Ctrl + X].
After rebooting, check the page with its statistics flightadsb.feeyo.com/user/rank.
In the fourth column should be a green inscription online. And in the Airport list, the taken airplanes (the third column - how many seconds ago the signal from the aircraft was received).
At this point, my draft “stuck” indefinitely, because here I wanted to write how to run on a router with an openwrt script and ModeSMixer to distribute data to services and thus turn off this receiver and use it for other purposes. But I do not yet have free time and I decided to publish it as it is. Maybe someone will want to order a free receiver and this article will be useful.
One receiver can distribute data to several services and is used for this program ModeSMixer.
ModeSMixer is a console application for combining and relaying streams with Mode-S data in various formats. Approximate use case:
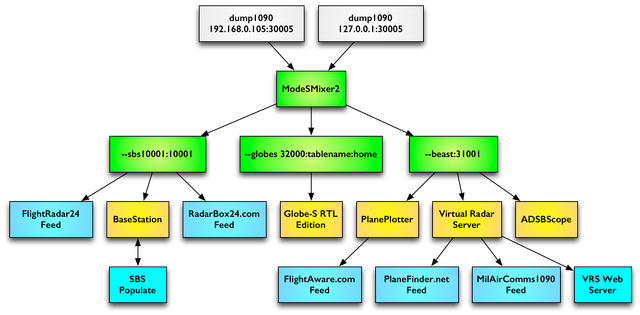
The program is designed to combine and retransmit different stream formats ModeS data. The program has no default settings. Everything is set by parameters.
The --inConnect parameter specifies the addresses and ports from which data is received. And the parameter --outServer defines the format and port for the relayed data. The example in the picture will look like this:
The --location parameter defines the latitude and longitude of the station installation location, and the --web parameter specifies the port on which the program’s web interface will work. More information about the program can be found here .
By setting up a distribution to several services, the station owner receives a special membership on each service and access to non-public information and the archive of flights for a certain period.
In the case of using PiAware, data is already being sent to FlightAware and all that remains is to collect this data using modesmixer2. And in the case of Variflight, you need to get data in BaseStation format on some free port, for example, 10001. The parameter will look like --outServer msg: 10001. If necessary, you can add port 10002 for the VirtualRadar program: --outServer beast: 10002
In order for it to start and restart automatically, you need to edit task.sh, adding:
Finally, edit the get_message / send_message.py script, specifying the new port with the data:
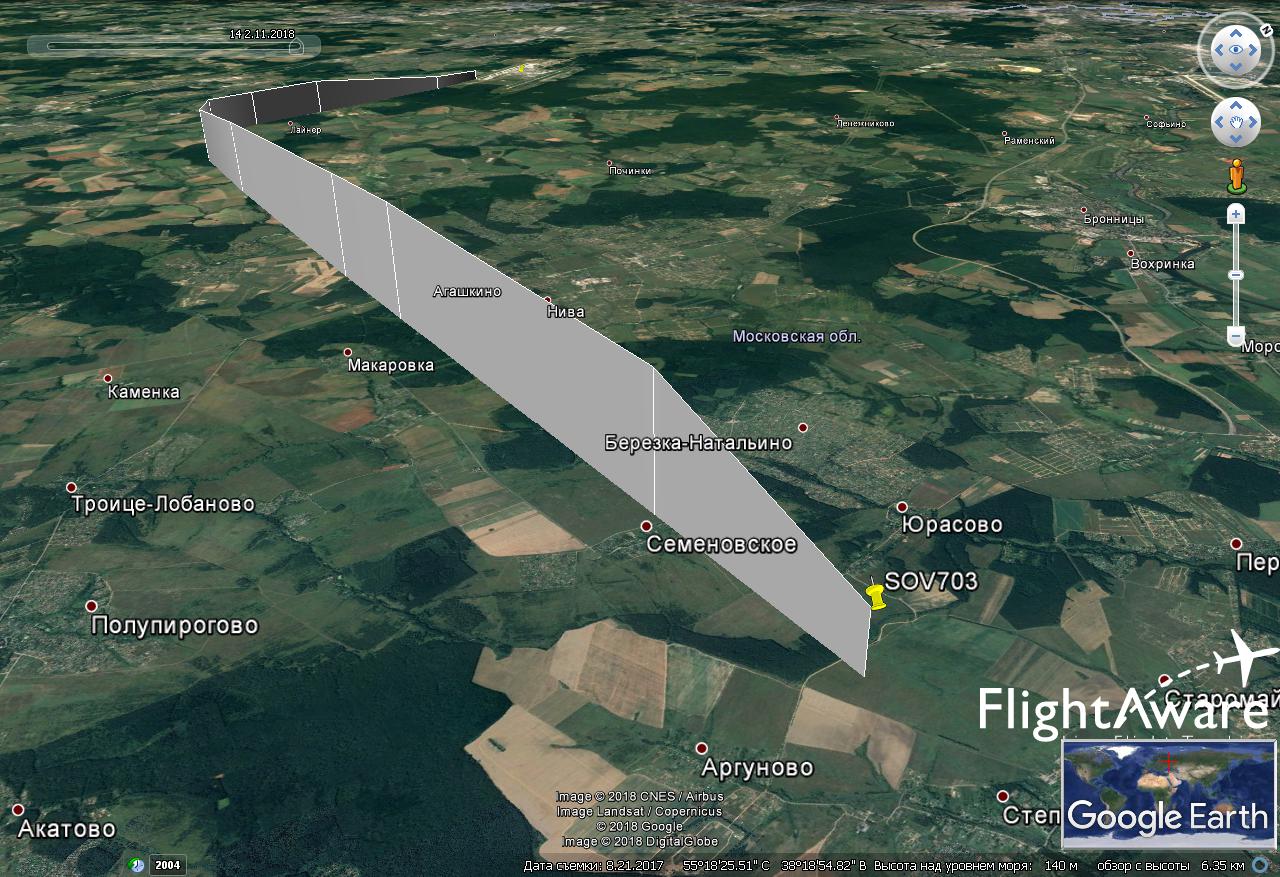
while this article was in draft, news from China appeared concerning these services. In November 2018, the Chinese authorities began to turn off the ADSB receivers of foreign services. This can be seen in the public statistics of Flightaware stations in China:

The news is that Chinese radarspotting enthusiasts said they received calls from representatives of the Chinese authorities and were visited by the police, who “very nice and polite” asked them to stop transmitting ADS-B data to overseas services that appear to "endanger China’s national security and sovereignty."
Some claimed that they were called, even if they did not receive the receiver from FlightRadar24 and FlightAware. These events caused a stir among enthusiasts, and many of them stopped transmitting ADS-B data. It is known that FlightRadar24 tried to anonymize the user stations in China. It is not clear how effective it is.
Chinese authorities notice in English:

“It threatens the national security and sovereignty of China” by the fact that such services make it possible to locate Chinese (American, European and others except the countries of the former USSR) military aircraft. For example, the weekly trajectory of the US strategic reconnaissance UAV over international waters at an altitude of 16 km:
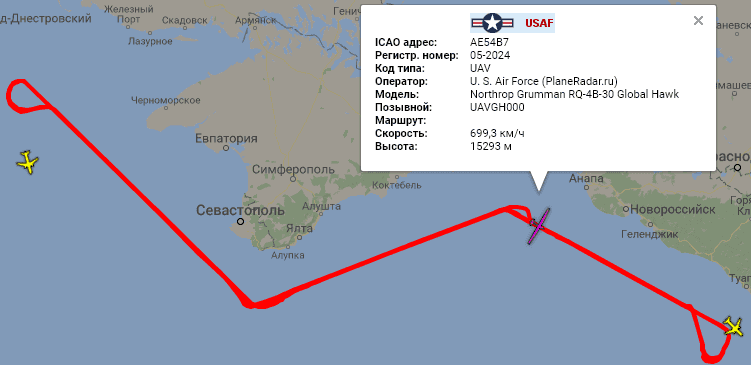
In the world there are two secondary radar systems from the United States and the USSR. Therefore, these receivers and services cannot show the location of most “Soviet” aircraft, helicopters, if they are not equipped with an “American” radar responder, which is necessary only for flying in airspace, for example, the United States or the EU. Therefore, it is possible to see something interesting in the territory of the Russian Federation in the border areas, preferably by the sea. For example, the above-mentioned American intelligence officer is remarkably visible from Krasnodar. Thanks to this coastal receiver placement, mentioned above, PlaneRadar service periodically gets into the news of the Russian media.
PS VariFlight ADS-B has launched an English version - flightadsb.variflight.com
On Habré there are a number of publications about radar sports, in which or in the comments to which not only the Flightradar is mentioned. In this publication I will talk about the Chinese service for tracking air traffic and its similar Chinese ADSB receiver, which they send out for free.

Radarspotting is quite an interesting activity to captivate a significant number of people. Several articles on Habré describe well the essence of the lesson:
- Plain and Radarspotting, or I am sick of aviation
- Step by step: Transmit data to flightradar24
- Flightradar24 - how does it work?
- How to keep track of identified flying objects with the Raspberry Pi
- Cheap and simple radarspot station
The receiver receives, transmitted by airplanes, a signal at a frequency of 1090 MHz, decrypts and sends in some format. For example:
{"updatetime":1537902225,"UTC Time":"2018-09-25 19:03:45","anum":"TCETM","fnum":"KKK6944","position":{"long":30.66455078125,"lat":39.351677},"height":10005.06,"speed":888.96,"angle":130},This activity is not only interesting, but has become the activity of several companies:
Few people think about what they do for a living and how services like Flightradar work. An example of this can be seen in ru.vikipedii " public web service, allowing real-time monitoring of the position of aircraft in the air ." The article itself and the title give a false impression of Flightradar as a kind of entertainment service.
In fact, having emerged in the early 2000s as a hobby, these companies quickly reached a payback period and each year increase revenue. For example, Flightaware, founded in 2005, became profitable already in 2006, earning more than $ 1M in the first 18 months, and showing an annual growth of 40-75%. According to some resources, the annual income of Flightaware exceeds $ 9M, and Flightradar - more than $ 2M.
If in Europe there is a Flightradar, in the USA - Flightaware, then in China there is a VariFlight. In the same way, the service, which sells flight statuses, statistical data and archives of flights, performs analysis and forecasting for customers - organizations and individual clients.
VariFlight own words:
<meta name="description" content="VariFlight занимает лидирующие позиции среди поставщиков информации о статусе полетов. Мы предоставляем статистические данные, информацию о рейсах в реальном времени, расписание полетов и др. Наши продукты и услуги, такие как Индекс Комфортности Полета, могут быть беспрепятственно интегрированы с деловыми системами и процессами.">
<meta name="keywords" content="расписание рейсов, онлайн табло аэропорт, домодедово расписание, аэропорт погода, задержка рейса, статус рейса, карта полетов, время вылета, отслеживание рейсов, шереметьево онлайн табло, самолеты онлайн, анализ данных, отслеживание самолетов, воздушный транспорт, аэропорт расписание">
<meta property="og:url" content="http://www.variflight.com/ru/">Companies trade data, both their own and those received, for example, from the US Federal Aviation Administration. But the greatest profit can be obtained from its own receivers, the operation of which the company does not cost anything because they are installed by radarspot enthusiasts, you only need to spend money on manufacturing and shipping. Therefore, at some point companies began to sell and send their receivers for free. Free to where the company does not yet have coverage with its network of receivers and where there is no data.
The cost of the data justifies the “free” distribution of receivers (note the text below the table - the receiver remains in the ownership of Flightaware, formally rented out for free).

By 2015, Flightradar had more than 8,000 active receivers in the network, Flightaware had about 4,500. But Flightaware began distributing receivers two years before, and Flightradar had built its network for almost a decade by that time. At this time , Flightaware has more than 15,000 receivers. Flightaware receivers software is constantly being improved on this and FMSDATA, FMSWX.
Location map of receivers in March 2017:

Orange - for free distributed Flightaware receivers, white - homemade receivers, red - PlanePlotter paid program .
This coverage of the Flightaware receiver network in December 2015:

And in March 2017, the Flightaware receivers network (the current state at the offsite site ) provided such coverage:

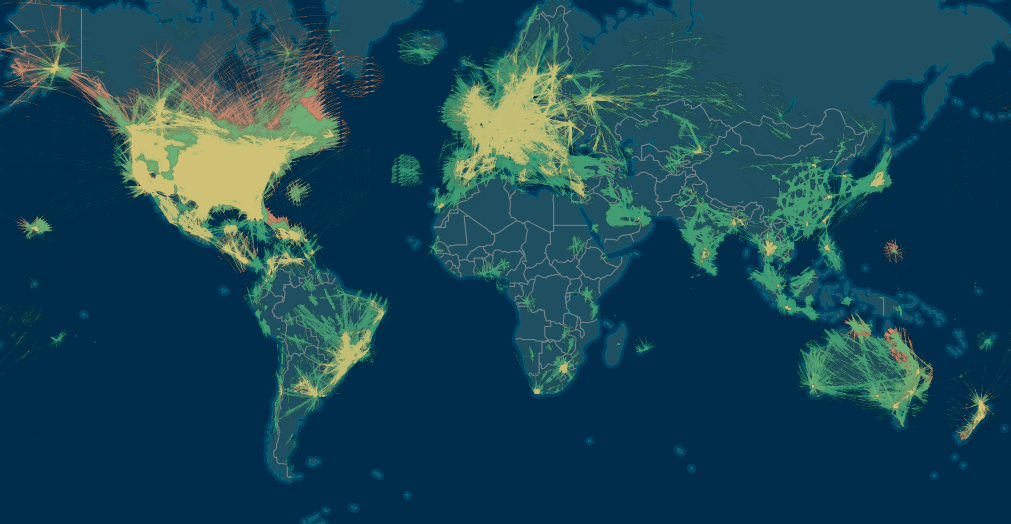
It is not always possible to install receivers, so in 2018 the data of ground receivers are supplemented with data from the Iridium NEXT satellites - “For the first time, it will be possible to continuously track aircraft anywhere in the world . ”

Blue Gray - Iridium NEXT satellite data. Green and yellow (the latter is MLAT ) are ground receiver data.
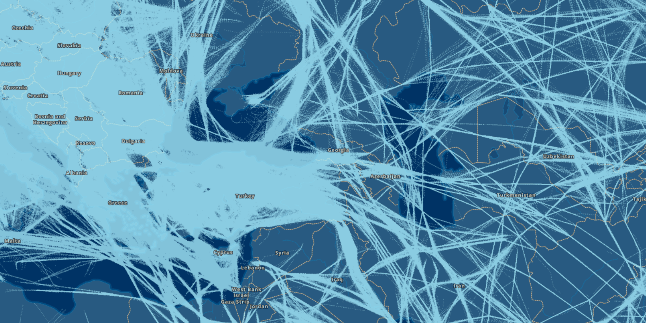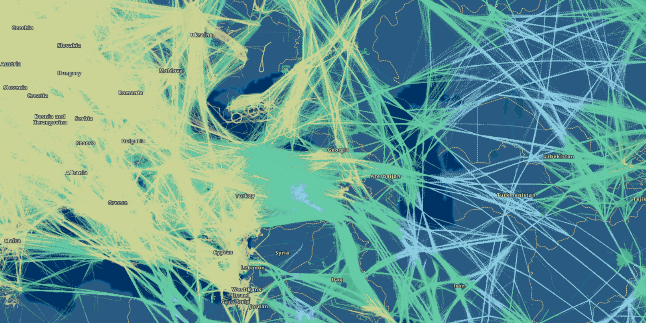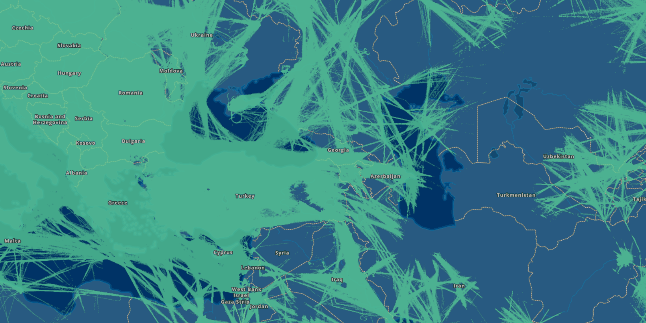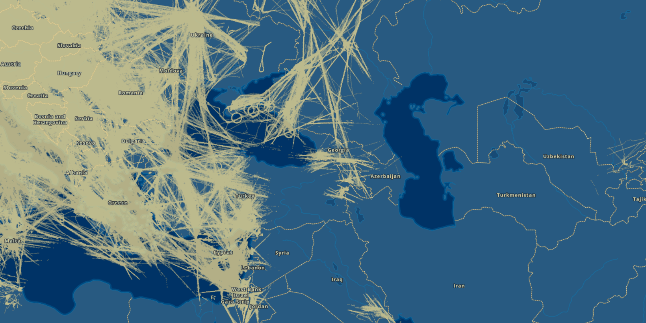
The radius of the zone covered by one station is limited by the curvature of the Earth’s surface and the obstacles covering the horizon, and is no more than 450 km at best. And in the "usual case" about 150 km. With rare tropospheric passages for this radio frequency, it is possible to look beyond the horizon. An example of the zones of maximum coverage of stations broadcasting on Planeradar.ru:

Sharp peaks in reception diagrams are just isolated cases of reception at very large distances.

The animation below shows the need to send receivers. Outside the EU / US, this hobby is not very popular. There may be a reason for the cost of the hobby and this map indirectly indicates the level of welfare, technical education, population density in the region. Perhaps a matter of practical interest - users transmitting data from their receivers receive a free Flightaware corporate account , worth $ 90 per month.

And so the situation is outlined in general terms. The market for this service is growing, the market needs more data and VariFlight has also begun to deploy its network. In April 2018, the company VariFlight announced that it is looking for volunteers to host free equipment. An example of such a message in the post on Instagram .
And in August, I came across this offer for free to order a receiver via the link http://flightadsb.feeyo.com/index/adsb?lang=en . After studying the site, I noticed that the company is looking for voluntary network participants in countries near the borders of China. And having filled out the questionnaire, I did not particularly expect that the SFD is in the area of the company's interests.

In the application you need to indicate on the map the installation location ( Installation Location ), the antenna installation floor on the building ( Floor of Installation , for example, 7/9 - the 7th floor of a 9-storey building), the nearest airport code ( Airport code - I indicated the IATA code) and download photos of the horizon from the Installation Environment . The rest is almost identical to the order on Aliexpress, except for the items Title, Nationality, Occupation, Company. Filled in English with full name.
After a couple of weeks, checking the mail, I found two emails from ADSB 展示 系统 (Display system of ADS-B) stating that the application was approved almost immediately and that the parcel had been rushing to me for a long time, having already passed the customs at that time.

In the second letter were login, password and track number of the parcel. And also the instruction that I did not notice and read when ... you know yourself, when they usually read the instructions.

Login matched the name in the application, and the password is clearly sent the same to everyone. Therefore, we go and change the password immediately (and login if required).
In general, the phrase “This is some nonsense” from the Sudden-strike game has increasingly surfaced in my head, if anyone remembers how the Germans in the game with accent speak Russian. Sometimes quiet, sometimes loud.
By the way, the profile was the only page in English, then everything will be in Chinese. On Habré wtigga published an excellent article about the Chinese Internet "Chinese Internet and software: about sore" . I felt all the pain just now. If you have not read, then it's time to prepare.

The Google Chrome browser with the translation function will help work on the site, but many pages that were not always feasible for it.

Places will be funny phrases.

And so we log in with the data from the second email.

And go to the item Personal information . As it turned out, Google Chrome can not always translate the page or it does not succeed the first time and in this case, after a series of automatic translation attempts, I had to copy the text into Google Translate. Therefore, I post a hint for those who encounter the same problem.
The page has two tabs, the active of which is marked with a red line. At first you can not touch anything.

- Full name
- Your phone number
- Your email
- Airport code
- Name of your ADSB receiver
QQ item is a Chinese Tencent QQ messenger .
On the second tab, change password

- Old Password
- New password
- Repeat new password
With the exception of this, automatic translation almost always works. The site map design is very close to the Flightradar site and the “features” of the translation do not make it difficult to use.

A detailed examination of the service differs, for example, an interesting functionality that Flightaware does not have - a heat map , translated by Google Chrome as “thermal analysis”.

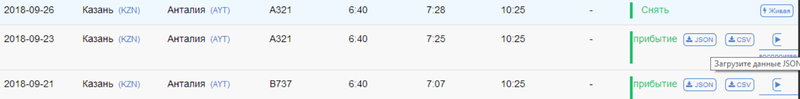
An interesting feature of some flights:

Probably there is no information about the airports of departure and landing of this flight.
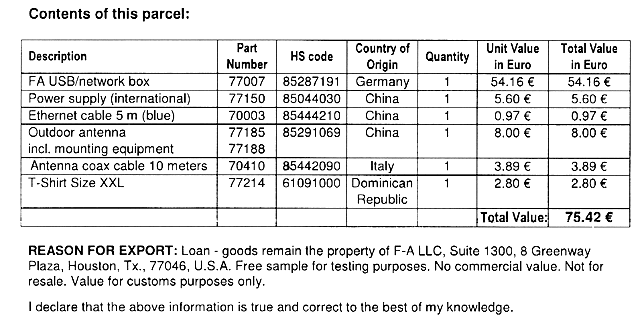
Package and receiver overview
By track number the parcel was sent on September 6 and received on September 18. The box has solid dimensions that surprised post office workers. On the way from the post office inside, something thundered, tinkled and rolled.

The open box was somewhat surprised by the lack of packaging materials.

For comparison, the box at the receiver Flightaware.

Surprisingly, the contents of the box did not suffer. Only on the antenna there was a scratch - the film was torn off.

The receiver itself has the inscription only two connectors - power and HDMI. In addition to two, all connectors are on one side. LAN, 2 USB ports, four-pin connector (assumption that this serial interface was confirmed by a dial tone on the BCM 14 (8 pin TXD / Transmit),
BCM 15 (10 pin RXD / Receive)), 5 volt power supply and SMA (female) antenna connector .

On the opposite side, behind the two holes in the housing, are green and red LEDs. And next to a sticker with the "serial number" of the receiver, recorded by hand. Also, the receiver has HDMI and microUSB.

The cover of the receiver has two ears for mounting on the wall, which positively distinguishes it from almost the same case of the Flightaware receiver, which the manufacturer provided for only four silicone feet at the bottom.

Test the ability to use these two ears for mounting the receiver:

Flightaware Flightfeeder upside down:

To compare receiver sizes:

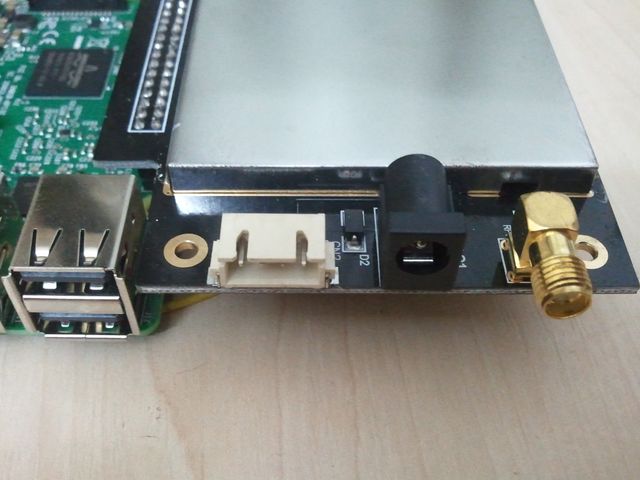
The natural question is "what's inside?" Removing the cover, fastened with 4 screws, we see this layout.

The connectors are on a separate receiver board, made in the form of an expansion card for the Raspberry Pi 3 Model B V1.2.
For comparison, a photo Flightaware Flightfeeder (G6) without a cover. This generation of receivers sent out until about 2017. Built on RPi 2 Model B v.1.1 and mode-receiver-decoder mode-S Beast .

The reverse side of this design hid an unexpected element. Surprise is a massive radiator located on the bottom side of the board. The need for it is incomprehensible (after a week, I think this is a “tropical design.” In my conditions, the radiator is slightly warm).

Additionally, the expansion board is connected to the RPi with a four-wire connector with three wires soldered to test points PP27 (USB VCC), PP44 (USB D-),
PP45 (USB D +).

Those. nothing can be plugged into the top right USB connector. Therefore, in the photo of the case placed above, it can be seen that of the two paired USB connectors, the slot in the case is just opposite one that is closest to the LAN.

Flightaware did the same, soldering the receiver to the pins of one of the connectors.
Most of the expansion card takes a metal screen. Of the visible parts of the connectors on the same side, and on the opposite two indicators and some "coil" with taps. Reminds shunt with variable resistance. Perhaps 1div0 , the author of the article “Why bend tracks?” Knows what it is. During normal operation of the receiver, the green LED is on. In what cases it is lit red - I do not know. Not yet watched its inclusion.

On the side of the connectors there are power connectors and antennas, and a four-pin connector of unknown purpose.
All electronics are hidden under a large tin screen cover. Flightaware Flightfeeder receiver board is not shielded. At the Flightaware forum, the developers answered this question that the metal case of the receiver itself is sufficient to protect against external interference.

An attempt to look under the screen was a success from the second approach. The lid broke off and turned out ...

... as it turned out everything was in vain - the marking with chips was carefully cut down.

Looking ahead, I will say that it turned out to be an almost ordinary RTLSDR receiver - RTL2832U DVB-T (0bda: 2838), called “dongles”, “whistles”, and which are devoted to several articles on Habré that give an idea of these devices and how they have simplified and cheapened the implementation of the reception and processing of radio signals on computers. For example:
- USB TV tuners on rtl2832 - or how to hear everything on the radio for 600 rubles
- Once again about receiving HF on RTL-SDR
In the latter, the background is well described:
The launch of the RTL2832U microcircuit for DVB-T digital television receivers did not promise any sensations, because Realtek was already somewhat late with its release. In 2010, a more progressive DVB-T2 standard was already being introduced with more efficient coding of information, therefore, the original novelty did not attract much attention. For two years, cheap USB tuners at its base were used for their intended purpose, until at the beginning of 2012 some technical information about the operating modes of this chip leaked. It turned out that for receiving analog (FM) and digital (DAB) radio in the VHF band, this chip uses the principle of software decoding of a previously digitized from the air frequency band. Those. roughly speaking, it digitizes the high-frequency signal from the antenna input, and filtering of a specific carrier and its detection (allocation of useful information) from the received digital stream is given to the central processor. Obviously, this was done for reasons of economy, just as at the time of the Dial-UP sunset, extremely cheap “soft modems” were widely distributed, which also represented only an advanced pair of DAC + ADC, and all signal processing was done by the CPU in thread with the highest priority.
Unlike the "regular tuners" that I have, this instance of usb id 0bda: 2832 also has a 17-digit serial number.
Bus 001 Device 005: ID 0bda: 2832 Realtek Semiconductor Corp. RTL2832U DVB-T
Found Rafael Micro R820T tuner
Ie analogue to the “blue whistle” used to create homemade ADSB receivers. In the photo is the receiver on OrangePI.

Assembling the receiver back, set the radiator just in case. Bought specifically for the revision of routers and other home equipment.

Power supply 5V 2A. It looks more solid than the power supply for Flightaware Flightfeeder. But with a Chinese plug ... I tried to remember where my adapter was lying around.

In a box of white cardboard was such a pretty velvet bag.

"... in the chest - a hare, in a hare - a duck, in a duck - an egg, in an egg - a needle ..."

Inside was a puzzle of three adapters that solved the question "where is my adapter lying around."

A CA-23RP 2.5GHZ 400W Made in Japan lightning arrester appeared in a brown cardboard box. I am not aware of this configuration of other ADS-B receivers. Very reasonable for protection against small power accidents.

The indoor antenna is likely to test the receiver without installing an external antenna. Not suitable for practical use. But it is sold on Aliexpress / Ebay as an “ADS-B antenna”, but its present purpose is given on the inscription on a magnetic sole. I caught airplanes on this antenna no further than within a radius of 30-40 km.
Near adapter N (female) - SMA (male). Perhaps a gift in the event of a filter or low-noise amplifier.

Coaxial cable for antenna 5 meters with N and SMA connectors, and twisted pair 10 meters ("100% oxygen-free copper, blablabla").

Antenna cable marked KOPA PLESS RG400-KF MIL-C-17. Googling M17 / 128-RG400 RG-400 Double Braid Flexible Coaxial Cable with a different shell color:
- Maximum operating frequency 6 GHz
- At a frequency of 1.20 GHz, the maximum attenuation is 0.54 dB / m
It is very doubtful that these are characteristics of a Chinese cable. By the way, Flightaware bundled a lousy antenna cable, albeit an Italian one. Shortening the cable from the antenna to several tens of centimeters three times increased the number of received packets by the Flightaware receiver.

Outdoor antenna and its mounting to the mast.

Kuryez from the FlightFeeder ADS-B VariFlight group on Facebook:

The antenna is slightly smaller in diameter than Flightaware

Flightaware mast mount from duralumin

A gift with the symbolism of VariFlight. Judging by the inscriptions on the back - this label should cling to the luggage in case of loss at the airport, filling out contact details of the owner.


First start
Turning on the power in principle did not change anything in the appearance of the device. Only LAN indicators were lit, the router has a new host name raspberrypi in the list of issued dhcp IP addresses. On HDMI, there was a normal RPi boot output and a login request.

And that's all. The expected web interface for such devices at IP: 8080 was unavailable. The port scan of the device found only port 22. Attempting to log in as the default user and password was sent far away to both the console and ssh:
login as: pi
pi@raspberrypi's password:
Access deniedThe receiver turned on and off several times, remained for days on the assumption that it could download something at that time or try to reach servers in China. Neither the red nor the green indicator lights up.
At this time, I went off-site looking for an FAQ, technical support or something else that could tell what this device should and should not do. I logged in for the first time, but this didn’t fundamentally change anything - there are no contact forms or feedback forms. The only thing that was found was that the receiver was tied to an account and had the status offline. I noticed that the system last saw it on the network on September 2 at 17.18 Beijing time, 4 days before being sent by mail. Those. He was checked and connected to the account.

After spending a couple of days in ferment on the sites of the Chinese Internet, which somehow linked to offsite or to which links from offsite were, and tired of their original design, I realized that there was no technical support for this product. And at that moment I remembered two emails from ADSB 展示 系统 (Display system of ADS-B).
“This is some kind of nonsense” - once again I heard a familiar voice with an accent in my head. My email to this address was turned back by PostMaster feeyo.com

And then the eye caught the attachment to the second letter, which had previously eluded the view (due to the unusual GMail design). This turned out to be a VariFlight ADS-B installation manual. It's time to find out how it was supposed to work.
Meet with 飞 常 准 ADS-B 设备 安装 说明
Below is a translation of the instructions in 6 pages and two languages, most of which are occupied by illustrations.
Installation instructions VariFlight ADS-B

Short description
The VariFlight ADS-B is equipment designed for civil aviation enthusiasts to track aircraft. The kit consists of an ADS-B receiver, power supply, patch cord (patch cord), antenna and cable for it.

Antenna installation site
The external antenna must be fixed on the outside of the building, as high as possible above the obstacles to the radio signal; installation on the roof is preferred. Otherwise, ADS-B signals will be absorbed by obstacles such as a wall or a building.

After installing the antenna, you need to connect the ADS-B receiver to the Internet by following these steps:
- Connect the antenna cable to the receiver.
- Insert one end of the patch cord into the router and the other end of the ADS-B receiver.
- Connect the power supply to the receiver.

The Internet should connect automatically as soon as you complete these three steps above. Static IP is not supported, only DHCP.
Complete equipment kit

An example using an indoor antenna

Three ways to find out if your ADS-B equipment is online or not
Method one.
In the settings of your router, find the IP address of the ADS-B receiver and open http // XXX.XXX.XXX: 8080 in a web browser, where XXX.XXX.XXX is the internal IP address on your local network.

Method two
Open the link flightadsb.variflight.com in your web browser, log in, and click on the item Airport

Method three, only for Chinese volunteers
For Chinese users, we can use WeChat.
On this instruction over. In accordance with this instruction, the device works partially - it receives IP on the local network, but does not display the web interface, in which you can find out the dump1090 - Mode S decoder, created for RTLSDR dongles and used in similar devices.

Without working dump1090, no data will be sent to the server. It is strange that the device somehow worked when checking before sending. "This is some kind of nonsense." Since the Chinese are not interested in the device’s fate in any way, and I couldn’t find any signs of technical support, my conscience is completely clear if I try to repair it myself.
Take control of the device
Having disassembled the receiver, immediately upon receipt, I made a microSD image in the state before the first power up and studied the contents a bit, immediately suspecting as the receiver sends data to the server - there were files and scripts with service addresses in / root /.
Reset PI user password
Instructions on changing the “forgotten password” with pictures can be found at this link .
I disassemble the receiver again. To get to the microSD you need to unscrew all the screws and pull out both the boards. Later on, while working with the receiver, I did not assemble it back into the case. I had to replace two microSD with different systems.
We take out the microSD from Rpi, make a backup copy on the computer, if not already done, and edit the file - cmdline.txt .
dwc_otg.lpm_enable=0 console=ttyAMA0,115200 console=tty1 root=/dev/mmcblk0p2 rootfstype=ext4 elevator=deadline fsck.repair=yes rootwaitAdd to the end of this line
init=/bin/shWe return the microSD back to RPi, connect the monitor and keyboard. Connect the power. When the lines stop running on the screen, press Enter. The console prompt appears, in which we type
mount -rw -o remount /
passwd pi
sync
exec /sbin/initThe lines run again and again wait for them to stop running, then turn it off. We take out microSD from RPi. On the computer, edit or restore a backup copy of cmdline.txt - delete “init = / bin / sh”.
For the last time, we return microSD back to RPi. Turn on. Successfully log in with a new password. Enable ssh by typing raspi-config and selecting SSH from the menu.
Then, using the top command, I want to see what the receiver lives with and suddenly notice wget processes and ... dump-1090. Silent scene. I check in the web browser http // XXX.XXX.XXX: 8080 - there is an interface.

Not to say that it was unexpected, but definitely unusual. From the instructions I check Method Two - everything is fine there too: the receiver's icon turned green, and below there was a list of airplanes that he heard.
It would be possible to finish this, but first of all it would be inexcusable to use RPi3 for this. And secondly, if this device worked stably. For example, it disappeared from the list of IP addresses of the DHCP router, while it was available when accessing the previously received IP, and at the same time there was no image on HDMI. But the most important was the instability of the broadcast. According to statistics on the receiver page, it worked several hours a day. Sometimes a full day, sometimes several hours, sometimes zero hours. It took several days to study the system - not every software was installed. Chinese repositories ... The German voice finally convinced that it was necessary to make a healthy person's ADS-B receiver, and for this you need to roll up the PiAware image on another microSD. The original microSD is still useful to find out how it works.At least save files from / root. Preferably make an image.
PiAware
PiAware - Linux software for transferring flight data to FlightAware. Contains fork dump1090-mutability. According to the developers, one of the differences is that it does not send packages to the FlightAware server if they do not differ from the first one. Those. if the plane did not change the speed, altitude, then this data should not be processed, and thus reduces the load on the server.
About two years ago, FlightAware began translating texts on the site into Russian. And much to create your own station PiAware can be found offsite . The essence of creating a station on RPi with RTLSDR comes down to writing to the microSD the finished image of PiAware on Raspbian Linux using Etcher. Further, before you insert the card in RPi and wait for the download, you need to make some changes. To enable SSH access, create an empty file with no extension called ssh in the boot partition. And in the piaware-config.txt file, you can make the necessary settings , for example, specify a static IP or enable WiFi and specify an SSID / password, provided that a supported USB WiFi adapter is connected. The same settings can be made from the console with the command piaware-config Setting_ Possible_values .
If you already have a Flightaware account, then in 5 minutes the station will become attached to the account by receiving a Unique Identifier. And the receiver will have its own statistics page.
By default, user PI has the password flightaware. It’s a good idea to change your password right away.
"Tests"
Tests in quotes, just impressions. Having two devices with almost the same software, you can evaluate their abilities.
I have a free Flightaware receiver and the first thing I experienced was a complete VariFlight antenna. I just replaced it with a Flightaware antenna. And while studying the VariFlight receiver, FlightFeeder statistics was collected on the Flightaware page. The conclusion is disappointing. Although the maximum range, nothing has changed, like FlightFeeder, in the direction of the line of sight, catching some at a distance of 400 km, but the statistics of aircraft per hour / day slipped by 2-3 times. Sure takes the board for 300+ kilometers, but sees a little less messages. What I do not know inside the case of the antenna itself is not collapsible.
A Flightaware antenna was connected to the VariFlight receiver and it showed statistics of the same order. And with a native antenna even lower.

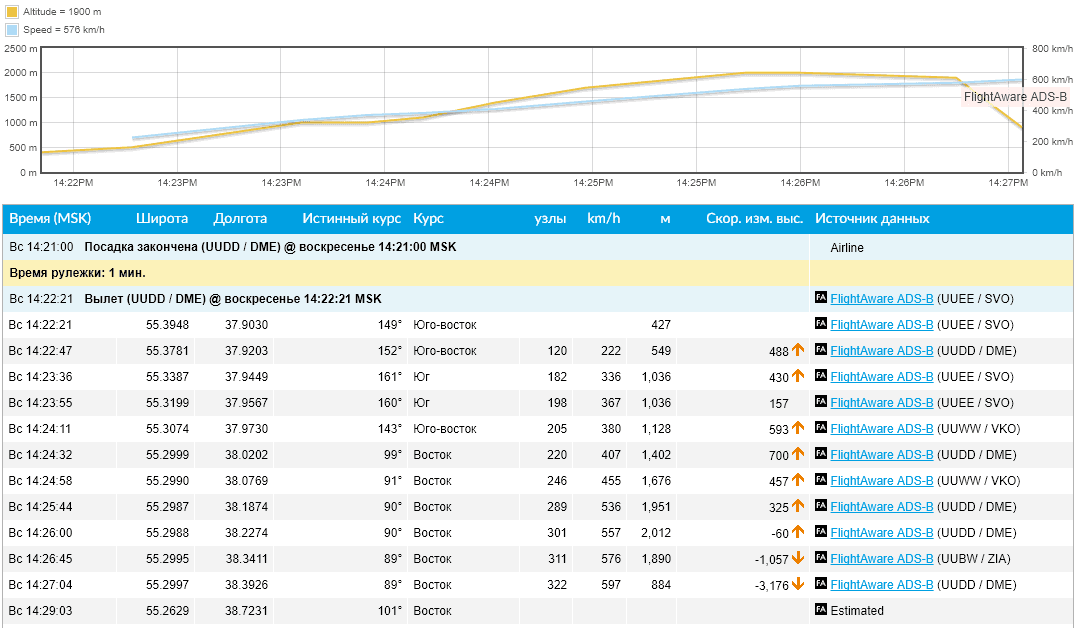
I decipher the statistics. Statistics from 10-05 to 10-07 is the VariFlight receiver with Flightaware antenna. 10-08 the complete antenna was connected and from 10-09 to 10-11 the statistics of the VariFlight kit. 10-12 The send_message.py script has been modified to collect data from Flightaware Flightfeeder. After that, data from it and 10-13 daily statistics based on Flightaware Flightfeeder data went to VariFlight. Further more, for example, for 10-18 - 396 flights, 814176 packages, for 10-19 - 471 flights, 860415 packages.
Let's estimate how the receiver VariFlight is subject to radio interference. To do this, we scan the 800 MHz-1200 MHz range and generate a heat map.
sudo apt-get install python-imaging
sudo wget https://raw.githubusercontent.com/keenerd/rtl-sdr-misc/master/heatmap/heatmap.py
sudo chmod +x heatmap.py
sudo systemctl stop dump1090-fa
sudo rtl_power -f 800M:1200M:100k -i 30 -c 50% -e 30m -g 30 -F 9 >scan.csvAfter half an hour (-e 30m), scanning stops and generate an image.
./heatmap.py scan.csv scan.pngReboot the device to restore the work of dump1090.
And copy the resulting image to a computer using (win) scp.
This is a fragment of a thermal scan map around 1090 MHz. Full image is available by click.

Bright yellow stripes is a mobile connection. Nothing out of the ordinary - he has no prefilters like the Flightfeeder, and he is greatly hampered by mobile stations. In this, it is absolutely the same as the simple “blue whistle” mentioned earlier. Manufacturing in the form of a special expansion card is possible; it makes some sense, for example, the role of “curved tracks” on this board is incomprehensible. Making a specialized board it would not be difficult to install both a low-noise amplifier and a SAW filter at 1090 MHz. Just looking at the scripts in the device, I had an idea why this was done - one script is called acars.py.

As far as the amplifier and filter would improve the characteristics of the receiver shows an example from the above-mentioned group on Facebook. One of the VariFlight Box users connected a specialized dongle from Flightaware instead of a regular receiver, which brought it to the top of the rating from about a thousand users (of course, the installation location and another antenna also affected).

FlightAware launches two dongle models — Pro Stick and Pro Stick Plus, which are still the same “blue whistle” but have a preamplifier, and the latter additionally has a SAW filter that eliminates unnecessary signals in areas with a lot of interference, for example in cities, as well as these models are equipped with an SMA antenna connector. These dongles are used in Flightaware Flightfeeder “orange” receivers.

with the cover removed

The name of the script “acars.py” hints that the absence of any filters is not an error and economy. Address and reporting system of aviation communication(Eng. Aircraft Communications Addressing and Reporting System, ACARS) - a digital radio communication system used in aviation for the transmission of short messages between the aircraft and ground stations. The operating frequency for ACARS in Europe is 131.725 MHz. Therefore, the device can not have a filter only for 1090 MHz, otherwise it will not be able to receive a signal at 131 MHz. What is inside the antenna is unknown, I am not going to break it, but it is obvious that its “wide coverage” is also provided by the creators. Similarly, the method above generated a heat map in the range of 100 MHz-500 MHz. Fragment of the thermal scan map around 450 MHz. The full image is also available by click.

On the heat map are visible control panels, security sensors, wireless door bells, wireless weather station sensors, radio amateurs, FM radio stations, and so on and so forth.
For example, by setting rtl_433, you can see the data of the neighboring wireless sensors of weather stations and, if desired, use them as the author of this article .

And by running rtl_tcp, you can listen to radio amateurs and FM radio.

Interestingly, not all radio amateurs exactly hold the frequency. It was amusing to see how the radio amateurs rated the interlocutor as audible, and the frequency of one of the radio stations was somewhere off to the side.
But the Chinese receiver on the native system showed accuracy - 0 PPM. On the method of measuring PPM can be read on Habré in the article quwy "Once again on the reception of HF on RTL-SDR" . It is highly desirable to adjust the PPM for best reception. What the Chinese did. Piaware has a small error that can and should be removed by specifying the correct PPM value with the command sudo piaware-config rtlsdr-ppm <PPM value>.
RTLSDR Calibration Instructions with rtl_test and kalibrate-rtl
We wait about 10 minutes until the values stabilize. This will be the required ppm.
The accuracy can be increased by signals from mobile phone towers using the kalibrate-rtl utility.
Из списка каналов необходим тот, у кого значение «power» больше.
Полученный номер канала используем в команде kal -c <номер канала> -e <грубое значение PPM, определенное ранее вручную или утилитой rtl_test> -v
В результате получаем «average absolute error». И используем это значение ppm, округленное до целого, в команде sudo piaware-config rtlsdr-ppm <значение PPM>
rtl_test -p We wait about 10 minutes until the values stabilize. This will be the required ppm.
The accuracy can be increased by signals from mobile phone towers using the kalibrate-rtl utility.
sudo apt-get install libtool autoconf automake libfftw3-dev
git clone https://github.com/asdil12/kalibrate-rtl.git
cd kalibrate-rtl
git checkout arm_memory
./bootstrap
./configure
make
sudo make install
kal -s GSM900
Из списка каналов необходим тот, у кого значение «power» больше.
Полученный номер канала используем в команде kal -c <номер канала> -e <грубое значение PPM, определенное ранее вручную или утилитой rtl_test> -v
В результате получаем «average absolute error». И используем это значение ppm, округленное до целого, в команде sudo piaware-config rtlsdr-ppm <значение PPM>
As a result, we can say that the VariFlight receiver for iron is little better than what you can assemble yourself. This is a good base to start practicing this hobby (and showed tests of iron, it can be used for a wide range of other tasks. Especially since there are three free USB ports).
The unique disadvantage of an ADSB receiver is the software and the Chinese interface of the site. If nothing can be done with the Chinese website, then you can modify the software of the receiver itself. The easiest way is to install PiAware and set up distribution on VariFlight. Then you can set up distribution on Flightradar24 and get an account with special conditions there. An example of using an account with special features is access to the archived data of Flightaware (the crash of the An-148 Saratov Airlines).


We give the data on VariFlight
Returning to the contents of the root directory. It can be found on github . The names of the files clearly hint at their functions.
root@raspberrypi:/home/pi# ls /root -l
total 24
drwxr-xr-x 8 root root 4096 Nov 22 2016 dump1090
drwxr-xr-x 5 root root 4096 Oct 16 18:54 get_message
-rwxr-xr-x 1 root root 567 Nov 22 2016 install.sh
drwxr-xr-x 7 root root 4096 Nov 22 2016 rtl-sdr
-rwxr-xr-x 1 root root 62 Nov 22 2016 synctime.sh
-rwxr-xr-x 1 root root 1300 Nov 29 2016 task.sh
install.sh
#!/bin/bash
apt-get update
apt-get install cmake libusb-1.0-0-dev build-essential vim ntpdate -y
apt-get remove ntp
cd get_message/
mv rtl-sdr-blacklist.conf /etc/modprobe.d/
mv dump.sh /etc/init.d/dump
chmod +x /etc/init.d/dump
mv task.sh ../
chmod +x ../task.sh
cd ../rtl-sdr/
mkdir rtl
cd rtl
cmake ../ -DINSTALL_UDEV_RULES=ON
make install
ldconfig
cd ../../dump1090/
make
cd /root/get_message/
python get_ip.py
ps aux | grep py
update-alternatives --config editor
crontab -e
* * * * * /root/task.sh >/dev/null 2>&1
* * */6 * * /root/synctime.sh >/dev/null 2>&1
From the last install.sh lines, you can see that cron adds two tasks — run task.sh every minute and synctime.sh every 6 days.
synctime.sh
#!/bin/bash
/usr/sbin/ntpdate 115.182.42.248 > /dev/null 2>&1
115.182.42.248 - BeiJing Wanglianxuntong Telecom Technology Co., Ltd, Beijing, China.
remarks: Please note that CNNIC is not an ISP and is not
remarks: empowered to investigate complaints of network abuse.
remarks: Please contact the tech-c or admin-c of the network.
task.sh
#!/bin/bash
ps -eaf | grep dump1090 | grep -v grep
if [ $? -eq 1 ]
then
/etc/init.d/dump stop
sleep 1
/etc/init.d/dump start
echo `date "+%G-%m-%d %H:%M:%S"`" dump1090 restart"echo"------------------------------------------------------------------------"elseecho `date "+%G-%m-%d %H:%M:%S"`" dump1090 running"echo"------------------------------------------------------------------------"fi
ps -eaf | grep send_message.py | grep -v grep
# if not found - equals to 1, start itif [ $? -eq 1 ]
then
python -O /root/get_message/send_message.py &
echo `date "+%G-%m-%d %H:%M:%S"`" send_message restart"echo"------------------------------------------------------------------------"elseecho `date "+%G-%m-%d %H:%M:%S"`" send_message running"echo"------------------------------------------------------------------------"fi
ps -eaf | grep get_ip.py | grep -v grep
# if not found - equals to 1, start itif [ $? -eq 1 ]
then
python /root/get_message/get_ip.py
echo `date "+%G-%m-%d %H:%M:%S"`" get_ip restart"echo"------------------------------------------------------------------------"elseecho `date "+%G-%m-%d %H:%M:%S"`" get_ip running"echo"------------------------------------------------------------------------"fiThe script task.sh, run every minute by cron, checks and, if necessary, restarts dump1090, the send_message.py and get_ip.py scripts.
pi@raspberrypi:~ $ ps -eaf | grep dump1090 | grep -v grep
root 830 1 14 Oct12 ? 13:49:25 ./dump1090 --net --net-sbs-port 30003
pi@raspberrypi:~ $ ps -eaf | grep get_ip.py | grep -v grep
pi@raspberrypi:~ $ ps -eaf | grep send_message.py | grep -v grep
root 838 1 0 Oct12 ? 00:09:20 python -O /root/get_message/send_message.py
The get_message directory contains python scripts, one of which, send_message.py, sends data.
root@raspberrypi:/home/pi# ls /root/get_message -l
total 40
-rw-r--r-- 1 root root 954 Nov 22 2016 acars.py
-rw-r--r-- 1 root root 1341 Nov 22 2016 acars.sh
-rw-r--r-- 1 root root 173 Nov 22 2016 config.ini
drwxr-xr-x 8 root root 4096 Nov 22 2016 dump1090
-rwxr-xr-x 1 root root 1731 Nov 22 2016 get_ip.py
drwxr-xr-x 3 root root 4096 Nov 22 2016 get_message1117
-rwxr-xr-x 1 root root 3400 Dec 7 2016 init.sh
-rw-r--r-- 1 root root 33 Oct 16 18:51 md5.txt
-rwxr-xr-x 1 root root 1143 Oct 12 18:16 send_message.py
-rw-r--r-- 1 root root 16 May 27 2016 UUID
init.sh
#!/bin/bash
path='/root/get_message/'
DATE=`date -d "today" +"%Y-%m-%d_%H:%M:%S"`
result=""
UUID=""
execom=""
FromServer=""
SourceMD5=""
device=""if ps -ef |grep dump1090 |grep -v grep >/dev/null
then
device="adsb"elif ps -ef |grep acarsdec |grep -v grep >/dev/null
then
device="acars"else
device="unknow"fi
IpAddr=`/sbin/ifconfig |grep "addr:" |grep -v 127.0.0.1 |cut -d ':' -f2 |cut -d ' ' -f1`
if [ -f "/root/get_message/UUID" ]
then
UUID=`cat /root/get_message/UUID`
fiexecut(){
whilereadcommanddoeval$commandif [ $? -ne 0 ]
then
execom=$command
result=0
breakfi
result=1
done <$path/package/exe.txt
}
removefile(){
rm -rf $path/package
rm -f $path/*tar.gz*
}
main(){
ps -eaf | grep "pic.veryzhun.com/ADSB/update/newpackage.tar.gz" | grep -v grep
if [ $? -eq 1 ]
then
/usr/bin/wget -P $path -c -t 1 -T 2 pic.veryzhun.com/ADSB/update/newpackage.tar.gz
if [ -f "$path/newpackage.tar.gz" ]
then
dmd5=`md5sum $path/newpackage.tar.gz|cut -d ' ' -f1`
if [ "$SourceMD5" = "$dmd5" ]
then
/bin/tar -xzf $path/newpackage.tar.gz -C $pathecho$SourceMD5 > $path/md5.txt
/bin/touch /usr/src/start.pid
echo$DATE > /usr/src/start.pid
execut
if [ $result -eq 1 ]
then
curl -m 2 -s -d UUID=$UUID -d date=$DATE -d execom=$execom -d message="success" http://receive.cdn35.com/ADSB/result.php
else
curl -m 2 -s -d UUID=$UUID -d date=$DATE -d execom=$execom -d message="fail" http://receive.cdn35.com/ADSB/result.php
fi
removefile
else
curl -m 2 -s -d UUID=$UUID -d date=$DATE -d execom="------" -d message="post file has been changed" http://receive.cdn35.com/ADSB/result.php
removefile
fielse
curl -m 2 -s -d UUID=$UUID -d date=$DATE -d execom="------" -d message="download failed" http://receive.cdn35.com/ADSB/result.php
removefile
fifi
}
if curl -m 2 -s pic.veryzhun.com/ADSB/update.php >/dev/null;then
removefile
FromServer=`curl -m 2 -s -d UUID="$UUID" -d IpAddr="$IpAddr" -d Device="$device" pic.veryzhun.com/ADSB/update.php`
SourceMD5=`echo$FromServer|cut -d ' ' -f1`
length=`echo$SourceMD5 |wc -L`
if [ $length -ne 32 ]
then
curl -m 2 -s -d UUID=$UUID -d date=$DATE -d execom="------" -d message="md5 style error" http://receive.cdn35.com/ADSB/result.php
exitfielse
curl -m 2 -s -d UUID=$UUID -d date=$DATE -d execom="------" -d message="curl failed" http://receive.cdn35.com/ADSB/result.php
exitfi
DesMD5=`cat $path/md5.txt`
if [ "$SourceMD5" = "$DesMD5" ]
then
curl -m 2 -s -d UUID=$UUID -d date=$DATE -d execom="------" -d message="no update,md5 without change " http://receive.cdn35.com/ADSB/result.php
exitelse
main
fiThe init.sh script checks if there is an update and installs a new send_message.py
get_ip.py
import socket
import fcntl
import struct
import urllib2
import urllib
import sys,os
import ConfigParser
import hashlib
import json
import uuid
config = ConfigParser.ConfigParser()
config.readfp(open(sys.path[0]+'/config.ini',"rb"))
uuid_file=sys.path[0]+'/UUID'if os.path.exists(uuid_file) :
file_object = open(uuid_file)
mid = file_object.read()
file_object.close()
else :
mid = uuid.uuid1().get_hex()[16:]
file_object = open(uuid_file , 'w')
file_object.write( mid )
file_object.close()
defsend_message(source_data):
source_data=source_data.replace('\n','$$$')
f=urllib2.urlopen(
url = config.get("global","ipurl"),
data = source_data,
timeout = 60
)
tmp_return=f.read()
request_json=json.loads(tmp_return)
request_md5=request_json['md5']
del request_json['md5']
tmp_hash=''for i in request_json:
if tmp_hash=='' :
tmp_hash=tmp_hash+request_json[i]
else :
tmp_hash=tmp_hash+','+request_json[i]
md5=hashlib.md5(tmp_hash.encode('utf-8')).hexdigest()
if (md5 == request_md5):
operate(request_json)
else :
print'MD5 ERR'print"return: "+tmp_return;
defget_ip_address(ifname):
skt = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
pktString = fcntl.ioctl(skt.fileno(), 0x8915, struct.pack('256s', ifname[:15]))
ipString = socket.inet_ntoa(pktString[20:24])
return ipString
defoperate(request_json):if request_json['type'] == 'reboot' :
os.system('/sbin/reboot')
elif request_json['type'] == 'code' :
fileHandle = open ( urllib.unquote( request_json['path'] ) , 'w' )
fileHandle.write( urllib.unquote( request_json['content'] ) )
fileHandle.close()
else :
print'OK'
eth=get_ip_address('eth0')
send_message(mid+'|'+eth+'|')
I especially do not understand the meaning of the network exchange performed by the script. A unique UUID is generated if it is missing. And there is a certain exchange with the addresses specified in the config.ini file. Probably this script is responsible for linking the translated data and IP to the account.
Noteworthy is the line "if request_json ['type'] == 'reboot': os.system ('/ sbin / reboot')".
[global]
name = NEW
ipurl = http://receive.cdn35.com/ADS-B_IP.php
sendurl = http://adsb.feeyo.com/adsb/ReceiveCompressADSB.php
version = 1.0
passwd = 'null'Finally, the script sends the data.
send_message.py
import socket
import urllib2
import urllib
import sys
import ConfigParser
import zlib
import base64
import os,uuid
serverHost = 'localhost'
serverPort = 30003
config = ConfigParser.ConfigParser()
config.readfp(open(sys.path[0]+'/config.ini',"rb"))
uuid_file=sys.path[0]+'/UUID'if os.path.exists(uuid_file) :
file_object = open(uuid_file)
mid = file_object.read()
file_object.close()
else :
mid = uuid.uuid1().get_hex()[16:]
file_object = open(uuid_file , 'w')
file_object.write( mid )
file_object.close()
sockobj = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
sockobj.connect((serverHost,serverPort))
defsend_message(source_data):try:
source_data=base64.b64encode(zlib.compress(source_data))
f=urllib2.urlopen(url = config.get("global","sendurl"),data = urllib.urlencode({'from':mid,'code':source_data}),timeout = 2)
returnTrueexcept Exception,e:
print str(e)
returnTrue
tmp_buf=''while1:
buf = sockobj.recv(1024)
ifnot buf: breakif len(buf) != 0:
tmp_buf=tmp_buf+buf
if buf[len(buf)-1] == '\n':
if send_message(tmp_buf) :
tmp_buf=''I edited the serverHost = 'localhost' string, replacing 'localhost' with 'ff-1234' —the network name of my Flightaware Flightfeeder and rebooting the VariFlight receiver. After that, the data from the Flightfeeder went to VariFlight.
The remaining scripts are receiving ACARS messages. Perhaps the remnants of a functional or a function implemented in the future. Scripts work with /root/acarsdec-3.0/acarsdec, which is missing along this path. ACARSDEC is an ACARS SDR decoder that decodes messages, for example, at a frequency of 131.725 MHz. Apparently it is precisely based on the reception of this frequency, at the receiver input there are no filters at 1090 MHz.

The Address and Reporting Aviation Communication System (ACARS) is a digital communication system used in aviation to transmit short, relatively simple messages between an aircraft and ground stations, either through direct radio communication or via satellite systems.More information about ACARS can be found, for example, here .
The acars.sh script is similar in implementation to task.sh — it restarts acarsdec and the get_ip.py and acars.py scripts if it does not detect the required process.
acars.sh
#!/bin/bash
ps -eaf | grep acarsdec | grep -v grep
if [ $? -eq 1 ]
then
/root/acarsdec-3.0/acarsdec -n 127.0.0.1:8888 -o 0 -p -8 -r 0 127.272 126.475 &
echo `date "+%G-%m-%d %H:%M:%S"`" acarsdec restart"echo"------------------------------------------------------------------------"elseecho `date "+%G-%m-%d %H:%M:%S"`" acarsdec running"echo"------------------------------------------------------------------------"fi
ps -eaf | grep get_ip.py | grep -v grep
# if not found - equals to 1, start itif [ $? -eq 1 ]
then
python /root/get_message/get_ip.py
echo `date "+%G-%m-%d %H:%M:%S"`" get_ip restart"echo"------------------------------------------------------------------------"elseecho `date "+%G-%m-%d %H:%M:%S"`" get_ip running"echo"------------------------------------------------------------------------"fi
ps -eaf | grep acars.py | grep -v grep
# if not found - equals to 1, start itif [ $? -eq 1 ]
then
python /root/get_message/acars.py
echo `date "+%G-%m-%d %H:%M:%S"`" acars restart"echo"------------------------------------------------------------------------"elseecho `date "+%G-%m-%d %H:%M:%S"`" acars running"echo"------------------------------------------------------------------------"fi
/usr/sbin/ntpdate cn.pool.ntp.org > /dev/null
acars.py
#!/usr/bin/env pythonimport socket, traceback ,time,urllib2,urllib,sys,ConfigParser
defsend_message(source_data):try:
f=urllib2.urlopen(url = config.get("global","sendurl"),data = urllib.urlencode({'from':config.get("global","name"),'code':source_data}),timeout = 10)
print"return: "+f.read();
returnTrueexcept Exception,e:
print str(e)
returnFalse
host = '127.0.0.1'
port = 8888
config = ConfigParser.ConfigParser()
config.readfp(open(sys.path[0]+'/config.ini',"rb"))
s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
s.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)
s.bind((host, port))
while1:
try:
message, address = s.recvfrom(8192)
socket_udp_str='{0} :{1} \n\n'.format(time.strftime('%Y-%m-%d %H:%M:%S',time.localtime(time.time())),message)
send_message(socket_udp_str)
except (KeyboardInterrupt, SystemExit):
raiseexcept:
traceback.print_exc()
At work, it looks like this:
PID TTY STAT TIME COMMAND
20726 ? Ss 0:00 \_ sshd: pi [priv]
20732 ? S 0:00 \_ sshd: pi@pts/0
20734 pts/0 Ss 0:00 \_ -bash
20744 pts/0 R+ 0:00 \_ ps -afx
777 tty1 Ss+ 0:00 /sbin/agetty --noclear tty1 linux
907 ? Sl 737:23 ./dump1090 --net --net-sbs-port 30003
915 ? S 11:11 python -O /root/get_message/send_message.py
ps -afx fully
pi@raspberrypi:~ $ ps -afx
PID TTY STAT TIME COMMAND
2 ? S 0:00 [kthreadd]
3 ? S 0:59 \_ [ksoftirqd/0]
5 ? S< 0:00 \_ [kworker/0:0H]
7 ? S 5:28 \_ [rcu_sched]
8 ? S 0:00 \_ [rcu_bh]
9 ? S 0:01 \_ [migration/0]
10 ? S 0:01 \_ [migration/1]
11 ? S 0:05 \_ [ksoftirqd/1]
13 ? S< 0:00 \_ [kworker/1:0H]
14 ? S 0:01 \_ [migration/2]
15 ? S 0:04 \_ [ksoftirqd/2]
17 ? S< 0:00 \_ [kworker/2:0H]
18 ? S 0:01 \_ [migration/3]
19 ? S 0:04 \_ [ksoftirqd/3]
21 ? S< 0:00 \_ [kworker/3:0H]
22 ? S 0:00 \_ [kdevtmpfs]
23 ? S< 0:00 \_ [netns]
24 ? S< 0:00 \_ [perf]
25 ? S 0:00 \_ [khungtaskd]
26 ? S< 0:00 \_ [writeback]
27 ? S< 0:00 \_ [crypto]
28 ? S< 0:00 \_ [bioset]
29 ? S< 0:00 \_ [kblockd]
31 ? S< 0:00 \_ [rpciod]
32 ? S 0:00 \_ [kswapd0]
33 ? S< 0:00 \_ [vmstat]
34 ? S 0:00 \_ [fsnotify_mark]
35 ? S< 0:00 \_ [nfsiod]
44 ? S< 0:00 \_ [kthrotld]
46 ? S< 0:00 \_ [bioset]
47 ? S< 0:00 \_ [bioset]
48 ? S< 0:00 \_ [bioset]
49 ? S< 0:00 \_ [bioset]
50 ? S< 0:00 \_ [bioset]
51 ? S< 0:00 \_ [bioset]
52 ? S< 0:00 \_ [bioset]
53 ? S< 0:00 \_ [bioset]
54 ? S< 0:00 \_ [bioset]
55 ? S< 0:00 \_ [bioset]
56 ? S< 0:00 \_ [bioset]
57 ? S< 0:00 \_ [bioset]
58 ? S< 0:00 \_ [bioset]
59 ? S< 0:00 \_ [bioset]
60 ? S< 0:00 \_ [bioset]
61 ? S< 0:00 \_ [bioset]
62 ? S< 0:00 \_ [bioset]
63 ? S< 0:00 \_ [bioset]
64 ? S< 0:00 \_ [bioset]
65 ? S< 0:00 \_ [bioset]
66 ? S< 0:00 \_ [bioset]
67 ? S< 0:00 \_ [bioset]
68 ? S< 0:00 \_ [bioset]
69 ? S< 0:00 \_ [bioset]
70 ? S< 0:00 \_ [VCHIQ-0]
71 ? S< 0:00 \_ [VCHIQr-0]
72 ? S< 0:00 \_ [VCHIQs-0]
73 ? S< 0:00 \_ [iscsi_eh]
74 ? S< 0:00 \_ [dwc_otg]
75 ? S< 0:00 \_ [DWC Notificatio]
77 ? S 0:00 \_ [irq/92-mmc1]
78 ? S 0:00 \_ [VCHIQka-0]
79 ? S< 0:00 \_ [SMIO]
80 ? S< 0:00 \_ [deferwq]
83 ? S< 0:00 \_ [bioset]
84 ? S 0:11 \_ [mmcqd/0]
87 ? S 0:04 \_ [jbd2/mmcblk0p2-]
88 ? S< 0:00 \_ [ext4-rsv-conver]
89 ? S< 0:00 \_ [ipv6_addrconf]
172 ? S 415:15 \_ [w1_bus_master1]
224 ? S< 0:00 \_ [cfg80211]
227 ? S< 0:00 \_ [brcmf_wq/mmc1:0]
229 ? S 0:00 \_ [brcmf_wdog/mmc1]
493 ? S< 0:00 \_ [kworker/1:1H]
550 ? S< 0:00 \_ [kworker/3:1H]
632 ? S< 0:00 \_ [kworker/u9:0]
633 ? S< 0:00 \_ [hci0]
634 ? S< 0:00 \_ [hci0]
638 ? S< 0:00 \_ [kworker/u9:2]
3856 ? S< 0:00 \_ [kworker/2:1H]
9346 ? S< 0:00 \_ [kworker/0:1H]
15564 ? S 0:00 \_ [kworker/1:0]
17556 ? S 0:00 \_ [kworker/u8:2]
17878 ? S 0:00 \_ [kworker/0:0]
17879 ? S 0:00 \_ [kworker/2:2]
19234 ? S 0:00 \_ [kworker/u8:4]
19566 ? S 0:00 \_ [kworker/3:1]
20143 ? S 0:00 \_ [kworker/2:1]
20259 ? S 0:00 \_ [kworker/3:2]
20352 ? S 0:00 \_ [kworker/0:2]
20416 ? S 0:00 \_ [kworker/1:2]
20600 ? S 0:00 \_ [kworker/3:0]
20601 ? S 0:00 \_ [kworker/2:0]
20605 ? S 0:00 \_ [kworker/u8:0]
20725 ? S 0:00 \_ [kworker/0:1]
1 ? Ss 0:10 /sbin/init
134 ? Ss 1:00 /lib/systemd/systemd-journald
136 ? Ss 0:08 /lib/systemd/systemd-udevd
416 ? Ss 0:09 /usr/sbin/cron -f
426 ? Ss 0:01 /lib/systemd/systemd-logind
429 ? Ss 0:00 avahi-daemon: running [raspberrypi.local]
458 ? S 0:00 \_ avahi-daemon: chroot helper
433 ? Ss 0:00 /usr/bin/dbus-daemon --system --address=systemd: --no
450 ? Ss 0:02 /usr/sbin/thd --daemon --triggers /etc/triggerhappy/t
496 ? Ss 0:03 /sbin/wpa_supplicant -s -B -P /run/wpa_supplicant.wla
498 ? Ssl 0:13 /usr/sbin/rsyslogd -n
636 ? S 0:00 /usr/bin/hciattach /dev/serial1 bcm43xx 921600 noflow
640 ? Ss 0:00 /usr/lib/bluetooth/bluetoothd
729 ? Ss 0:02 /sbin/dhcpcd -q -w
749 ? Ss 0:00 /usr/sbin/sshd -D
20726 ? Ss 0:00 \_ sshd: pi [priv]
20732 ? S 0:00 \_ sshd: pi@pts/0
20734 pts/0 Ss 0:00 \_ -bash
20744 pts/0 R+ 0:00 \_ ps -afx
777 tty1 Ss+ 0:00 /sbin/agetty --noclear tty1 linux
907 ? Sl 737:23 ./dump1090 --net --net-sbs-port 30003
915 ? S 11:11 python -O /root/get_message/send_message.py
From this it is clear that you can take data from PiAware almost without straining, in fact, only by transferring scripts to a new system. And if there is already an existing adsb-station - self-made, Flightradar24, Flightaware, then the existing receiver can be used at your discretion for other personal goals and tasks with a completely clear conscience.
Installing VariFlight on PiAware
We transfer the necessary files to the new system from the old one. Those. the contents of the root directory: the
directory get_message and files install.sh, synctime.sh, task.sh.
In the get_message directory:
- acars.py
- acars.sh
- config.ini
- get_ip.py
- init.sh
- send_message.py
and the UUID file is your VariFlight network ID.
If you want to start sharing data without having a VariFlight Feeder, then the first time you run the script, your UUID is generated. This file and the name of the nearest airport should be sent to chengyi (at) variflight.com to create your account on the service.
Further:
pi@piaware:~ $ sudo apt-get install -y python ntpdate
pi@piaware:~ $ su
root@piaware:~# sh task.sh
root@piaware:~# crontab -eEdit the crontab in nano by inserting
* * * * * /root/task.sh >/dev/null 2>&1Save the file by pressing [Ctrl + O] and close [Ctrl + X].
root@piaware:~# chmod 777 task.sh
root@piaware:~# rebootAfter rebooting, check the page with its statistics flightadsb.feeyo.com/user/rank.
In the fourth column should be a green inscription online. And in the Airport list, the taken airplanes (the third column - how many seconds ago the signal from the aircraft was received).
At this point, my draft “stuck” indefinitely, because here I wanted to write how to run on a router with an openwrt script and ModeSMixer to distribute data to services and thus turn off this receiver and use it for other purposes. But I do not yet have free time and I decided to publish it as it is. Maybe someone will want to order a free receiver and this article will be useful.
ModeSMixer
One receiver can distribute data to several services and is used for this program ModeSMixer.
ModeSMixer is a console application for combining and relaying streams with Mode-S data in various formats. Approximate use case:

The program is designed to combine and retransmit different stream formats ModeS data. The program has no default settings. Everything is set by parameters.
The --inConnect parameter specifies the addresses and ports from which data is received. And the parameter --outServer defines the format and port for the relayed data. The example in the picture will look like this:
./modesmixer2 --inConnect 192.168.0.105:30005 --inConnect 127.0.0.1:30005 --outServer sbs10001:10001 --outServer beast:31001 --globes 32000:tablename:home --location XX.XXXXX:YY.YYYYY --web 8765 &
The --location parameter defines the latitude and longitude of the station installation location, and the --web parameter specifies the port on which the program’s web interface will work. More information about the program can be found here .
By setting up a distribution to several services, the station owner receives a special membership on each service and access to non-public information and the archive of flights for a certain period.
In the case of using PiAware, data is already being sent to FlightAware and all that remains is to collect this data using modesmixer2. And in the case of Variflight, you need to get data in BaseStation format on some free port, for example, 10001. The parameter will look like --outServer msg: 10001. If necessary, you can add port 10002 for the VirtualRadar program: --outServer beast: 10002
./modesmixer2 --inConnect localhost:30005 --inConnect localhost:30105 --outServer msg:10001 --outServer beast:10002 --location <широта>:<долгота> --web 8765 &In order for it to start and restart automatically, you need to edit task.sh, adding:
ps -eaf | grep modesmixer2 | grep -v grep
# if not found - equals to 1, start itif [ $? -eq 1 ]
then
./modesmixer2 --inConnect localhost:30005 --inConnect localhost:30105 --outServer msg:10001 --location <широта>:<долгота> --web 8765 &
echo `date "+%G-%m-%d %H:%M:%S"`" modesmixer2 restart"echo"------------------------------------------------------------------------"elseecho `date "+%G-%m-%d %H:%M:%S"`" modesmixer2 running"echo"------------------------------------------------------------------------"fiFinally, edit the get_message / send_message.py script, specifying the new port with the data:
serverHost = 'localhost'
serverPort = 10001In the meantime,
while this article was in draft, news from China appeared concerning these services. In November 2018, the Chinese authorities began to turn off the ADSB receivers of foreign services. This can be seen in the public statistics of Flightaware stations in China:

The news is that Chinese radarspotting enthusiasts said they received calls from representatives of the Chinese authorities and were visited by the police, who “very nice and polite” asked them to stop transmitting ADS-B data to overseas services that appear to "endanger China’s national security and sovereignty."
Some claimed that they were called, even if they did not receive the receiver from FlightRadar24 and FlightAware. These events caused a stir among enthusiasts, and many of them stopped transmitting ADS-B data. It is known that FlightRadar24 tried to anonymize the user stations in China. It is not clear how effective it is.
Chinese authorities notice in English:

“It threatens the national security and sovereignty of China” by the fact that such services make it possible to locate Chinese (American, European and others except the countries of the former USSR) military aircraft. For example, the weekly trajectory of the US strategic reconnaissance UAV over international waters at an altitude of 16 km:

In the world there are two secondary radar systems from the United States and the USSR. Therefore, these receivers and services cannot show the location of most “Soviet” aircraft, helicopters, if they are not equipped with an “American” radar responder, which is necessary only for flying in airspace, for example, the United States or the EU. Therefore, it is possible to see something interesting in the territory of the Russian Federation in the border areas, preferably by the sea. For example, the above-mentioned American intelligence officer is remarkably visible from Krasnodar. Thanks to this coastal receiver placement, mentioned above, PlaneRadar service periodically gets into the news of the Russian media.
PS VariFlight ADS-B has launched an English version - flightadsb.variflight.com
