Listening to Ukrainian mobile phones: how to do it and how to defend yourself
In the feeds of news sites, you have read more than once about how special services from different countries track negotiations and the transfer of data of ordinary citizens. Now a new scandal is gaining momentum with the wiretapping of Ukrainian subscribers, allegedly carried out from the territory of Russia.
We already wrote about the threats that exist in the world of mobile communications, and today we want to talk again about one of the attack vectors aimed at mobile subscribers.
In short, such a scheme. The attacker introduces himself into the SS7 signaling network, in the channels of which he sends the Send Routing Info For SM (SRI4SM) service message, specifying the telephone number of the attacked subscriber A as a parameter. In response, the home network of subscriber A sends the attacker some technical information: IMSI (international subscriber identifier) and the address of the MSC switch that is currently serving the subscriber.
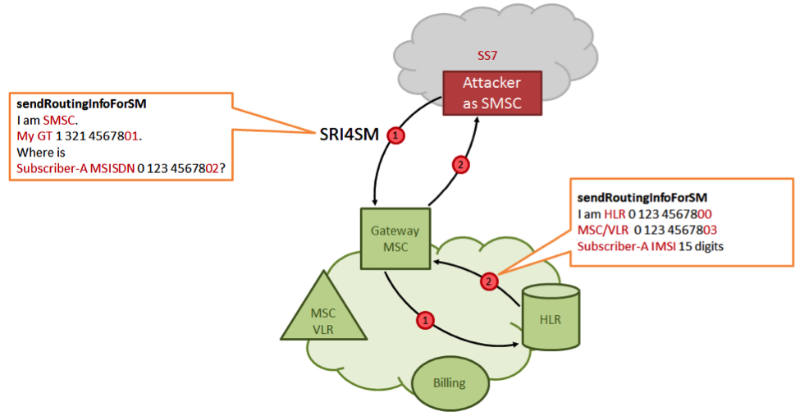
Then the attacker, using the Insert Subscriber Data (ISD) message, implements the updated subscriber profile in the VLR database, changing the billing system address to the address of his pseudo-billing system.

Then, when the attacked subscriber makes an outgoing call, instead of the real billing system, his switch contacts the attacker's system, which gives the switch a directive to redirect the call to a third party, again controlled by the attacker.
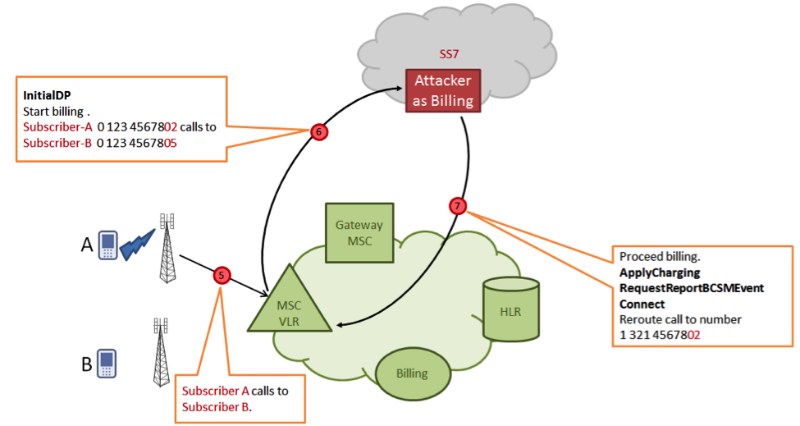
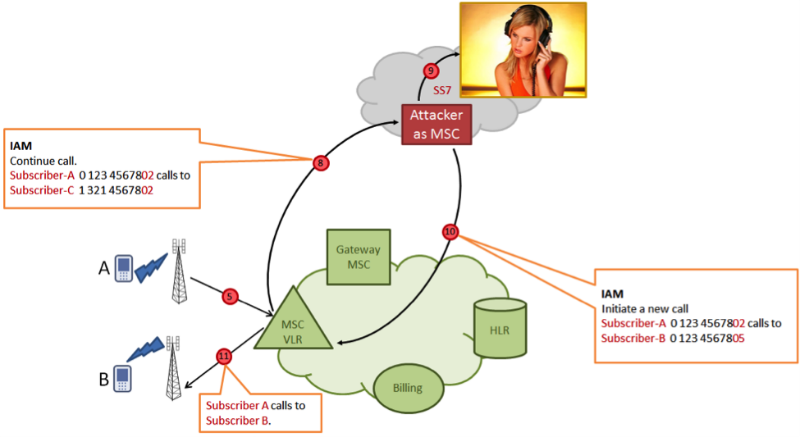
On this third side, a conference call is made up of three subscribers, two of which are real (calling A and called B), and the third is intruded by an attacker unauthorized and has the ability to listen and record a conversation.
I’ll tell skeptics right away: this scheme is not fantastic and, as you can see, is quite practicable. When developing the SS7 signaling system, it did not have protection mechanisms against such attacks. It was understood that the SS7 network itself was rather closed, and the “alien” could not get there. However, times are changing, and you and I are witnessing the malicious use of telephony technology. Unfortunately, one cannot just turn on and enable filtering of SS7 messages from external networks, as this will affect the serviceability of services in roaming. And no operator wants to deprive themselves of income.

In the work of an operator that provides services to a large number of subscribers, there is always a thin line between information security and the availability of services. This is especially acute for mobile operators: the range of services is huge, for all operators it is different, but I want to provide quality service not only to my, but also to other people on my network, and so that my subscribers are not limited in their capabilities when traveling abroad.
It would be nice to close the so-called "vulnerabilities" in the SS7 protocol stack, but any specialist will tell you that this is unrealistic. The classic case is "this is not a bug, this is a feature."
Instead of philosophizing on the architecture of mobile networks, you need to act. For example, do the following:
A little about the benefits of penetration tests. In the network of a telecom operator, their role is not only in identifying vulnerabilities, but also in solving operational problems. For example, in order to understand what the inclusion of a particular security function can affect, you need to conduct many tests taking into account the characteristics of each network. When conducting our SS7 signaling tests, we take into account 10 main types of attacks on the network and mobile subscribers.
Our studies have shown that the vast majority of attacks in SS7 networks begin with the receipt of technical data about the subscriber (IMSI ID, MSC switch addresses and HLR database). These parameters are obtained from the response to the very message SRI4SM, which is mentioned at the beginning of the article.
One security solution is SMS Home Routing, proposed by 3GPP in 2007. It is sometimes called SMS Firewall or SMS Filter.
An additional node is introduced into the operator’s network, which provides filtering of malicious messages SRI4SM. The principle of its work is as follows. When the SRI4SM message arrives in the operator’s network from another network, it is rerouted to the new filtering node. This node sends a normal response, giving out its address as the addresses of the MSC switch and the HLR database, and fake data as the subscriber’s IMSI. If the message SRI4SM was generated by an attacker, he will not receive any useful information in the response, and his attack will be drowned in the first stage. If the SRI4SM message was the beginning of a legal transaction for sending an SMS message, the sender’s network will send this SMS message to the filtering node, and he, in turn, will deliver the message to the addressee inside his home network.
7 years have passed since the issuance of this recommendation, but, as we can see, still not all operators have launched such a solution. And by the way, the SRI4SM message is not the only way to get an IMSI subscriber.
The mobile operator’s network, like any other, is potentially vulnerable. Due to the specificity of mobile networks, attacks in them can be more sophisticated than attacks on the Internet. We recommend that you take measures to protect such networks according to the traditional scenario: a pentest with the identification of problem areas, a security audit with the installation of recommended settings, periodic verification of security settings in accordance with the template. This is the minimum amount of work that will help raise the level of network security just above the baseboard, but this is enough as a first step. Subscribers will sleep better.
PS During the Positive Hack Days IV forum We made a report on possible attacks in the networks of mobile operators, in which we touched on wiretapping of telephone conversations from almost anywhere in the world.
Video: live.digitaloctober.ru/embed/2990#time1400670335
PPS In the comments, please abstract from political addictions so that this post does not provoke a holivar, who are abundant on the Internet. This technical article is dedicated to information security and is not related to the nationality, country of residence, religion or gender of the reader.
Authors: Sergey Puzankov and Dmitry Kurbatov, Positive Research Center.
We already wrote about the threats that exist in the world of mobile communications, and today we want to talk again about one of the attack vectors aimed at mobile subscribers.
In short, such a scheme. The attacker introduces himself into the SS7 signaling network, in the channels of which he sends the Send Routing Info For SM (SRI4SM) service message, specifying the telephone number of the attacked subscriber A as a parameter. In response, the home network of subscriber A sends the attacker some technical information: IMSI (international subscriber identifier) and the address of the MSC switch that is currently serving the subscriber.

Then the attacker, using the Insert Subscriber Data (ISD) message, implements the updated subscriber profile in the VLR database, changing the billing system address to the address of his pseudo-billing system.

Then, when the attacked subscriber makes an outgoing call, instead of the real billing system, his switch contacts the attacker's system, which gives the switch a directive to redirect the call to a third party, again controlled by the attacker.

On this third side, a conference call is made up of three subscribers, two of which are real (calling A and called B), and the third is intruded by an attacker unauthorized and has the ability to listen and record a conversation.

I’ll tell skeptics right away: this scheme is not fantastic and, as you can see, is quite practicable. When developing the SS7 signaling system, it did not have protection mechanisms against such attacks. It was understood that the SS7 network itself was rather closed, and the “alien” could not get there. However, times are changing, and you and I are witnessing the malicious use of telephony technology. Unfortunately, one cannot just turn on and enable filtering of SS7 messages from external networks, as this will affect the serviceability of services in roaming. And no operator wants to deprive themselves of income.

In the work of an operator that provides services to a large number of subscribers, there is always a thin line between information security and the availability of services. This is especially acute for mobile operators: the range of services is huge, for all operators it is different, but I want to provide quality service not only to my, but also to other people on my network, and so that my subscribers are not limited in their capabilities when traveling abroad.
What to do
It would be nice to close the so-called "vulnerabilities" in the SS7 protocol stack, but any specialist will tell you that this is unrealistic. The classic case is "this is not a bug, this is a feature."
Instead of philosophizing on the architecture of mobile networks, you need to act. For example, do the following:
- Conduct SS7 network penetration testing.
- At the same time, organize monitoring of alarm messages on the perimeter of the operator’s network by all available means.
- Analyze the information received and take measures to minimize risks.
Penetration tests
A little about the benefits of penetration tests. In the network of a telecom operator, their role is not only in identifying vulnerabilities, but also in solving operational problems. For example, in order to understand what the inclusion of a particular security function can affect, you need to conduct many tests taking into account the characteristics of each network. When conducting our SS7 signaling tests, we take into account 10 main types of attacks on the network and mobile subscribers.
- Check for disclosure of confidential technical parameters: IMSI of the subscriber; MSC switch address where the subscriber is registered; HLR database address where the subscriber profile is stored. Knowing these parameters, the attacker will be able to carry out more complex attacks.
- Check for the disclosure of data of the cell serving the subscriber. Knowing the cell identifier, an attacker can determine the location of the subscriber. In conditions of urban coverage, the location of the subscriber can be determined with an accuracy of tens of meters .
- Checking for the possibility of violation of the subscriber's availability for incoming calls (DoS per subscriber). In the event of a successful attack, the subscriber-victim stops receiving incoming calls and SMS. In this case, the victim’s mobile device shows the presence of a network. This state of the subscriber-victim will last until the subscriber makes an outgoing call, moves to the coverage area of another switch, or reboots the phone.
- Check for the disclosure of private SMS correspondence. This attack is a consequence of attack number 3. In the event of a successful attack, incoming SMS begin to come to the equipment of the attacker, it will not be difficult to read them. So that the SMS will not be delivered to the recipient subsequently, a notification of receipt is sent to the SMS center.
- Verify the manipulation of USSD commands. In case of a successful attack, the attacker is able to send USSD-commands on behalf of the subscriber. Possible damage will be determined by the set of services provided by the operator via USSD (for example, whether it is possible to transfer funds between subscriber accounts using USSD commands).
- Checking the possibility of changing the subscriber profile in the VLR. In the event of a successful attack, the attacker gets the opportunity to use his equipment as an intelligent platform to expand the capabilities of voice calls and tariffication manipulations.
- Check for the possibility of redirecting outgoing calls. It is a continuation of attack 6. In the event of a successful attack, the attacker is able to redirect outgoing voice calls of the subscriber-victim. In addition, the attack allows an attacker to arrange a conference call by unauthorized “wedging” into a conversation.
- Check for redirection of incoming calls. In the event of a successful attack, the attacker is able to redirect incoming voice calls intended for the subscriber-victim. In addition, calls to destinations with high tariffs may either not be charged, or call charges will be charged to the victim subscriber.
- Verifying the switch’s resilience to a DoS attack. In case of a successful attack, the switch stops processing incoming calls to subscribers within its coverage area.
- Checking the possibility of direct manipulation of billing. In the event of a successful attack, the attacker gets the opportunity to empty the personal account, thus depriving the subscriber of the ability to make calls.
How to protect yourself
Our studies have shown that the vast majority of attacks in SS7 networks begin with the receipt of technical data about the subscriber (IMSI ID, MSC switch addresses and HLR database). These parameters are obtained from the response to the very message SRI4SM, which is mentioned at the beginning of the article.
One security solution is SMS Home Routing, proposed by 3GPP in 2007. It is sometimes called SMS Firewall or SMS Filter.
An additional node is introduced into the operator’s network, which provides filtering of malicious messages SRI4SM. The principle of its work is as follows. When the SRI4SM message arrives in the operator’s network from another network, it is rerouted to the new filtering node. This node sends a normal response, giving out its address as the addresses of the MSC switch and the HLR database, and fake data as the subscriber’s IMSI. If the message SRI4SM was generated by an attacker, he will not receive any useful information in the response, and his attack will be drowned in the first stage. If the SRI4SM message was the beginning of a legal transaction for sending an SMS message, the sender’s network will send this SMS message to the filtering node, and he, in turn, will deliver the message to the addressee inside his home network.
7 years have passed since the issuance of this recommendation, but, as we can see, still not all operators have launched such a solution. And by the way, the SRI4SM message is not the only way to get an IMSI subscriber.
Instead of a conclusion
The mobile operator’s network, like any other, is potentially vulnerable. Due to the specificity of mobile networks, attacks in them can be more sophisticated than attacks on the Internet. We recommend that you take measures to protect such networks according to the traditional scenario: a pentest with the identification of problem areas, a security audit with the installation of recommended settings, periodic verification of security settings in accordance with the template. This is the minimum amount of work that will help raise the level of network security just above the baseboard, but this is enough as a first step. Subscribers will sleep better.
PS During the Positive Hack Days IV forum We made a report on possible attacks in the networks of mobile operators, in which we touched on wiretapping of telephone conversations from almost anywhere in the world.
Video: live.digitaloctober.ru/embed/2990#time1400670335
PPS In the comments, please abstract from political addictions so that this post does not provoke a holivar, who are abundant on the Internet. This technical article is dedicated to information security and is not related to the nationality, country of residence, religion or gender of the reader.
Authors: Sergey Puzankov and Dmitry Kurbatov, Positive Research Center.
