Cisco re-enters the PC segment
By the beginning of the 2000s, a signature approach prevailed in the personal computer protection market, which consisted of detecting predominantly known threats, for which the corresponding signatures were developed, which equipped security tools (antiviruses, host-based intrusion detection systems, etc.). One of the first companies to propose the use of behavioral mechanisms to deal with unknown threats was Okena from Massachusetts, which Cisco acquired in 2003. The Okena StormWatch product was renamed the Cisco Security Agent and the network giant began to offer its customers not only network security features - Cisco Pix firewalls, NetRanger attack detection systems and VPN gateways, but also PC protection tools, entering a new market for themselves.
However, on June 11, 2010, the company made a difficult and even unexpected decision to close this product line. This was partly due to the fact that PC protection was not at that time a priority for Cisco, which focused on network security. Among other reasons, an active transition to mobile devices with their many operating systems was called, for which it was difficult to develop and maintain the Cisco Security Agent. But whatever the true reason, the Cisco Security Agent has ceased to exist and Cisco has again focused its efforts on network security for a long 3 years. So far in 2013, after the acquisition of the world leader in the segment of intrusion prevention and next-generation protection means - Sourcefire, Cisco again did not have a solution for protecting personal computers - FireAMP, where the acronym AMP stands for Advanced Malware Protection. I would like to tell about this decision.
In fact, AMP is a platform for combating malicious code, which is designed to work in different parts of the corporate or departmental network. There is AMP for Networks - a high-speed network gateway for combating malicious code, which can be run either as a standalone device or as a module in firewalls or next-generation intrusion prevention systems, NGFW and NGIPS, respectively. There is also AMP for Content, a malware detection module for content protection tools, the Cisco Email Security Appliance and the Cisco Web Security Appliance. And finally, there is AMP for Endpoint, aka FireAMP, a solution for protecting PCs and mobile devices running Windows, MacOS, Android, etc.

Since AMP is a security platform, it is logical to assume that regardless of the installation location (network, PC or content protection device), the functionality for detecting and blocking malicious code will be similar. The 7 main detection technologies are divided into 2 main types:
Since AMP is a security platform, it is logical to assume that regardless of the installation location (network, PC or content protection device), the functionality for detecting and blocking malicious code will be similar. 7 main detection technologies are divided into 2 main types:

Reputation filtering is very similar to what is done in email protection systems or Internet access control. We have a large database of reputation values with which the analyzed object is compared. The only difference is that traditionally a reputation is assigned to an Internet site (mail server, Web site or IP address), while AMP uses a file reputation, the value of which is stored in the Cisco cloud database.
If a malicious file is detected, its “fingerprint” with metadata and signs of compromise is placed in a cloud database, which is then accessed by all AMP agents for a verdict regarding the new analyzed objects. Cloud analytics is a modern trend that is followed by all the key players in the information security market. All the brain activity of the defense system is carried out into the cloud, which is no longer able to hold the entire base for making decisions “on board”. It used to be anti-virus vendors or manufacturers of intrusion prevention systems equipped their products with an integrated signature database, and security scanner developers included scan databases in their solutions. These databases were regularly updated via the Internet, but the protection system could operate in a confined space that did not have an Internet connection. Today the situation has changed. Too many security events have to be analyzed by a modern protection system. And these events are diverse and diverse. The system itself is not able to work out this avalanche of events - we need "help from the hall", i.e. external analysts. Probably one of the first prototypes of such assistance was the global correlation system implemented in Cisco IPS several years ago. The idea was simple - to give anonymized information about the customer’s network (of course, this function could not be included) into a single center for analysis and development of new signatures, which then should be equipped with all IPS sensors installed by customers as part of the regular update of the signature database. The system itself is not able to work out this avalanche of events - we need "help from the hall", i.e. external analysts. Probably one of the first prototypes of such assistance was the global correlation system implemented in Cisco IPS several years ago. The idea was simple - to give anonymized information about the customer’s network (of course, this function could not be included) into a single center for analysis and development of new signatures, which then should be equipped with all IPS sensors installed by customers as part of the regular update of the signature database. The system itself is not able to work out this avalanche of events - we need "help from the hall", i.e. external analysts. Probably one of the first prototypes of such assistance was the global correlation system implemented in Cisco IPS several years ago. The idea was simple - to give anonymized information about the customer’s network (of course, this function could not be included) into a single center for analysis and development of new signatures, which then should be equipped with all IPS sensors installed by customers as part of the regular update of the signature database.

A similar approach has been applied to other Cisco security features, such as the Cisco ASA 5500-X firewalls and its Botnet Traffic Filter module. Even earlier, such “cloud analytics” was used in content security solutions - E-mail Security Appliance and Web Security Appliance. Sourcefire, recently acquired by us, used the same ideology in its defenses (NGIPS, NGFW, AMP) - the VRT cloud (Vulnerability Research Team) for analytics.
And it's not about the absence or infrequent update. Just the ideology of the “star” (the manufacturer independently collects information about the threats and distributes it among all customers) began to malfunction with an increase in the number and complexity of threats. It was necessary to attract security agents into the ranks of the defenders and the buyers / consumers themselves - they began to transfer information from their devices and security software to the manufacturer, in its IB analytics cloud. It was there that the analysis of information coming from both customers and various sources of the vendor itself was carried out. It was there that the development of methods to combat threats - old and new, was carried out. For IPS / IDS and antiviruses, these were signatures, for content filtering systems, URL bases, spam templates, reputation databases, black lists, etc. For firewalls, lists of botnets (bots and command centers).
Today, in a situation where not only the number of threats is growing, but also their complexity; when protection systems cannot cope with the load, and specialists serving them do not keep pace with the constantly changing threat landscape; when the system resources allocated for protection are limited, you need a new look at the decision about the presence or absence of a threat in the analyzed network traffic, files, mail and Web traffic. And since the security system itself is not able to do this, it remains to “entrust” this work to an external analytical center, which will take on the difficult task of continuously analyzing information about threats received from many disparate sources, constantly analyzing them and updating all means quickly protection connected to this cloud of IB analytics, which Cisco calls Cisco Security Intelligence Operations (SIO). In fact, Cisco now has three such clouds - the “native” Cisco SIO, the Sourcefire VRT cloud and the cloud acquired at the end of May by ThreatGRID. All three clouds are in the process of integration and integration. But back to the AMP.
AMP has another great feature - retrospective analysis, which allows you to detect malware post-factum. Yes, it is unpleasant to admit that 100% protection does not exist and cannot exist. Yes, skipping as a means of protection of any malicious program, especially purposefully developed for a particular company, is possible. But what now, to run to change the place of work, to go into a binge or tear his hair out of grief? Not! One must be prepared for such an event. In the context of a powerful increase in the number of malicious programs, the effectiveness of IS services and the means of protection it uses does not depend on whether all threats can or cannot be repelled, but on how quickly the compromised / infected nodes are detected and localized within the network. And here the retrospective analysis function fits perfectly
How can a threat penetrate the protected perimeter? Yes, whatever. Through an infected flash drive, through synchronization of the tablet with a working PC, through a 3G / 4G modem, through an unauthorized wireless access point ... Yes, through the holes in the firewall in the end. Therefore, it is so important not only to correctly build perimeter protection, but also to be prepared for the fact that malware can "break through" it. The AMP retrospective security feature includes 5 key mechanisms:

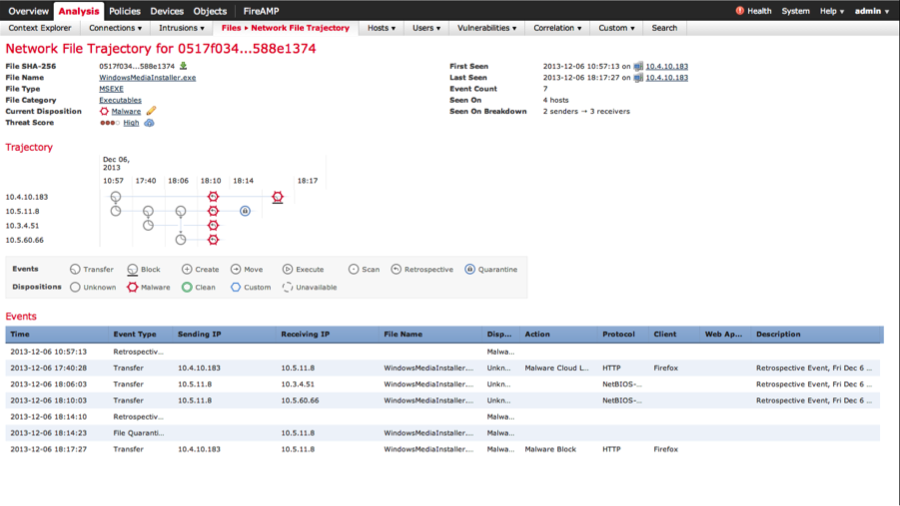
Below we see an illustration of how retrospective security works. At 10:57 on the network, on the node with the address 10.4.10.183, the first appearance of the WindowsMediaInstaller.exe file is recorded. At this point, we do not know anything about this file and pass it inside the network. This is normal. According to Cisco's annual security report, a new malware is detected every 4 seconds. Do we update our protections at such intervals? And if we update, is it at such a speed that new malicious programs are identified by the manufacturer of the protective equipment? In this case, we were able to identify that the file contains malicious code only after 7 hours. In the traditional approach, we can only apply this knowledge to new files that will be analyzed by the security system. But what to do with those files who have already entered the network? Accept and forgive? In the case of the retrospective security feature in Cisco AMP, we even post factum, but we can detect intrusion, as well as all the nodes that are “under the distribution”, which allows us to quickly localize the problem and prevent it from spreading throughout the network.
This solution has one drawback - the dependence on the Internet connection, the management cloud and information security analytics. If the company’s security policies do not allow this or the organization has weak Internet channels, all the advantages of Cisco AMP can turn the anti-malware system into a useless or ineffective program / device. Understanding this, Cisco has proposed a solution called FireAMP Private Cloud, whose mission is to mediate between the Cisco SIO / Sourcefire VRT cloud and the AMP user company. In this case, AMP agents will be managed, as well as apply for updates and a verdict for each analyzed file not to the cloud, but to the FireAMP Private Cloud virtual device located on the territory of the organization itself.
But the issue with access to the Internet still remains. How to make the system work in the complete absence of the Internet? To answer this question, we bought ThreatGRID at the end of May, which offers local security analytics devices that are now integrated with Cisco AMP.
In conclusion, I want to say that the Cisco Advanced Malware Protection solution, in which Cisco now invests large resources, is becoming an integral part of our information security portfolio.
However, on June 11, 2010, the company made a difficult and even unexpected decision to close this product line. This was partly due to the fact that PC protection was not at that time a priority for Cisco, which focused on network security. Among other reasons, an active transition to mobile devices with their many operating systems was called, for which it was difficult to develop and maintain the Cisco Security Agent. But whatever the true reason, the Cisco Security Agent has ceased to exist and Cisco has again focused its efforts on network security for a long 3 years. So far in 2013, after the acquisition of the world leader in the segment of intrusion prevention and next-generation protection means - Sourcefire, Cisco again did not have a solution for protecting personal computers - FireAMP, where the acronym AMP stands for Advanced Malware Protection. I would like to tell about this decision.
In fact, AMP is a platform for combating malicious code, which is designed to work in different parts of the corporate or departmental network. There is AMP for Networks - a high-speed network gateway for combating malicious code, which can be run either as a standalone device or as a module in firewalls or next-generation intrusion prevention systems, NGFW and NGIPS, respectively. There is also AMP for Content, a malware detection module for content protection tools, the Cisco Email Security Appliance and the Cisco Web Security Appliance. And finally, there is AMP for Endpoint, aka FireAMP, a solution for protecting PCs and mobile devices running Windows, MacOS, Android, etc.

Since AMP is a security platform, it is logical to assume that regardless of the installation location (network, PC or content protection device), the functionality for detecting and blocking malicious code will be similar. The 7 main detection technologies are divided into 2 main types:
Since AMP is a security platform, it is logical to assume that regardless of the installation location (network, PC or content protection device), the functionality for detecting and blocking malicious code will be similar. 7 main detection technologies are divided into 2 main types:
- Reputation Filtering
- Accurate signatures. This method is similar to that used by traditional antiviruses that have databases of known malicious programs.
- Fuzzy prints. This method is designed to combat polymorphic malware, the code of which can vary depending on the conditions. AMP looks for similar signs in the analyzed code and, if it matches, issues a verdict on the presence of malicious content, which is blocked.
- Machine learning. This method allows you to evaluate the metadata of the analyzed files in order to detect malware.
- Behavioral analysis
- Indicators of compromise. This method relies on the study of signs, indicators (indicators of compromise), which are inherent in malicious code. For example, if the analyzed file has the functions of self-reproduction, data transmission to the Internet and (or) reception of control commands from any node, then this, with a high degree of probability, can characterize the presence of malicious code in the file.
- Dynamic analysis. This method consists in sending the analyzed file to the cloud “sandbox”, where it is checked from different points of view and a verdict is issued on the presence or absence of signs of malware.
- Advanced analytics. This method allows you to take into account when analyzing suspicious files additional contextual information collected from different sources and using different mechanisms. Usually this method works in tandem with reputational techniques.
- Analysis and correlation of flows. This method uses knowledge of malicious sites and IP addresses that are often involved in malicious activity - sending control commands, accepting stolen data, etc. Detection of the interaction of the analyzed file with such nodes characterizes its harmfulness.

Reputation filtering is very similar to what is done in email protection systems or Internet access control. We have a large database of reputation values with which the analyzed object is compared. The only difference is that traditionally a reputation is assigned to an Internet site (mail server, Web site or IP address), while AMP uses a file reputation, the value of which is stored in the Cisco cloud database.
If a malicious file is detected, its “fingerprint” with metadata and signs of compromise is placed in a cloud database, which is then accessed by all AMP agents for a verdict regarding the new analyzed objects. Cloud analytics is a modern trend that is followed by all the key players in the information security market. All the brain activity of the defense system is carried out into the cloud, which is no longer able to hold the entire base for making decisions “on board”. It used to be anti-virus vendors or manufacturers of intrusion prevention systems equipped their products with an integrated signature database, and security scanner developers included scan databases in their solutions. These databases were regularly updated via the Internet, but the protection system could operate in a confined space that did not have an Internet connection. Today the situation has changed. Too many security events have to be analyzed by a modern protection system. And these events are diverse and diverse. The system itself is not able to work out this avalanche of events - we need "help from the hall", i.e. external analysts. Probably one of the first prototypes of such assistance was the global correlation system implemented in Cisco IPS several years ago. The idea was simple - to give anonymized information about the customer’s network (of course, this function could not be included) into a single center for analysis and development of new signatures, which then should be equipped with all IPS sensors installed by customers as part of the regular update of the signature database. The system itself is not able to work out this avalanche of events - we need "help from the hall", i.e. external analysts. Probably one of the first prototypes of such assistance was the global correlation system implemented in Cisco IPS several years ago. The idea was simple - to give anonymized information about the customer’s network (of course, this function could not be included) into a single center for analysis and development of new signatures, which then should be equipped with all IPS sensors installed by customers as part of the regular update of the signature database. The system itself is not able to work out this avalanche of events - we need "help from the hall", i.e. external analysts. Probably one of the first prototypes of such assistance was the global correlation system implemented in Cisco IPS several years ago. The idea was simple - to give anonymized information about the customer’s network (of course, this function could not be included) into a single center for analysis and development of new signatures, which then should be equipped with all IPS sensors installed by customers as part of the regular update of the signature database.

A similar approach has been applied to other Cisco security features, such as the Cisco ASA 5500-X firewalls and its Botnet Traffic Filter module. Even earlier, such “cloud analytics” was used in content security solutions - E-mail Security Appliance and Web Security Appliance. Sourcefire, recently acquired by us, used the same ideology in its defenses (NGIPS, NGFW, AMP) - the VRT cloud (Vulnerability Research Team) for analytics.
And it's not about the absence or infrequent update. Just the ideology of the “star” (the manufacturer independently collects information about the threats and distributes it among all customers) began to malfunction with an increase in the number and complexity of threats. It was necessary to attract security agents into the ranks of the defenders and the buyers / consumers themselves - they began to transfer information from their devices and security software to the manufacturer, in its IB analytics cloud. It was there that the analysis of information coming from both customers and various sources of the vendor itself was carried out. It was there that the development of methods to combat threats - old and new, was carried out. For IPS / IDS and antiviruses, these were signatures, for content filtering systems, URL bases, spam templates, reputation databases, black lists, etc. For firewalls, lists of botnets (bots and command centers).
Today, in a situation where not only the number of threats is growing, but also their complexity; when protection systems cannot cope with the load, and specialists serving them do not keep pace with the constantly changing threat landscape; when the system resources allocated for protection are limited, you need a new look at the decision about the presence or absence of a threat in the analyzed network traffic, files, mail and Web traffic. And since the security system itself is not able to do this, it remains to “entrust” this work to an external analytical center, which will take on the difficult task of continuously analyzing information about threats received from many disparate sources, constantly analyzing them and updating all means quickly protection connected to this cloud of IB analytics, which Cisco calls Cisco Security Intelligence Operations (SIO). In fact, Cisco now has three such clouds - the “native” Cisco SIO, the Sourcefire VRT cloud and the cloud acquired at the end of May by ThreatGRID. All three clouds are in the process of integration and integration. But back to the AMP.
AMP has another great feature - retrospective analysis, which allows you to detect malware post-factum. Yes, it is unpleasant to admit that 100% protection does not exist and cannot exist. Yes, skipping as a means of protection of any malicious program, especially purposefully developed for a particular company, is possible. But what now, to run to change the place of work, to go into a binge or tear his hair out of grief? Not! One must be prepared for such an event. In the context of a powerful increase in the number of malicious programs, the effectiveness of IS services and the means of protection it uses does not depend on whether all threats can or cannot be repelled, but on how quickly the compromised / infected nodes are detected and localized within the network. And here the retrospective analysis function fits perfectly
How can a threat penetrate the protected perimeter? Yes, whatever. Through an infected flash drive, through synchronization of the tablet with a working PC, through a 3G / 4G modem, through an unauthorized wireless access point ... Yes, through the holes in the firewall in the end. Therefore, it is so important not only to correctly build perimeter protection, but also to be prepared for the fact that malware can "break through" it. The AMP retrospective security feature includes 5 key mechanisms:
- Retrospective. This method allows us to track the time and place of the first occurrence of a file in a controlled network, as well as its current location, which is determined by the maximum coverage of AMP agents on a protected network (on a PC, on a network, and on content analysis tools).
- Attack chain analysis. This method allows you to collect, analyze and save information about how files, processes and communication channels in a protected network behave. In other words, we can analyze how various applications behave, when and by whom they are launched, with whom and at what time they interact, what interfaces they use, etc.?
- Behavioral indicators of compromise. This mechanism allows you to analyze the activity of a file that has fallen into the network and conclude that it is harmful. For example, a file that got inside the organization, got to many nodes, copied confidential information and sent it to an external IP address with a high degree of probability is malicious. Only an analysis of the combination of such indicators helps to identify unknown threats, individual actions of which may go unnoticed by traditional remedies.
- Trajectory analysis. This method allows you to record the time, method, entry and exit point of the file that has entered the file, which allows you to accurately answer the classic questions of incident management at any time: “Where did the malicious program get to the network?”, “Who did the infected node interact with?”, “ Where else did the malware go? ”,“ Who is the source of the problems? ” And all this without network scanning - all information is collected in real time and is ready for use at any time. Cisco AMP has two path analysis mechanisms - File Trajectory (for analyzing file movement over the network) and Device Trajectory (for analyzing file actions on a specific node).
- The hunt for gaps. This mechanism is similar to behavioral indicators of compromise, but it works at a higher level. If indicators of compromise are sought for a specific file, then hunting for gaps is carried out in relation to the entire network. We are looking for similar indicators in what has already happened on the network in the recent past.

Below we see an illustration of how retrospective security works. At 10:57 on the network, on the node with the address 10.4.10.183, the first appearance of the WindowsMediaInstaller.exe file is recorded. At this point, we do not know anything about this file and pass it inside the network. This is normal. According to Cisco's annual security report, a new malware is detected every 4 seconds. Do we update our protections at such intervals? And if we update, is it at such a speed that new malicious programs are identified by the manufacturer of the protective equipment? In this case, we were able to identify that the file contains malicious code only after 7 hours. In the traditional approach, we can only apply this knowledge to new files that will be analyzed by the security system. But what to do with those files who have already entered the network? Accept and forgive? In the case of the retrospective security feature in Cisco AMP, we even post factum, but we can detect intrusion, as well as all the nodes that are “under the distribution”, which allows us to quickly localize the problem and prevent it from spreading throughout the network.

This solution has one drawback - the dependence on the Internet connection, the management cloud and information security analytics. If the company’s security policies do not allow this or the organization has weak Internet channels, all the advantages of Cisco AMP can turn the anti-malware system into a useless or ineffective program / device. Understanding this, Cisco has proposed a solution called FireAMP Private Cloud, whose mission is to mediate between the Cisco SIO / Sourcefire VRT cloud and the AMP user company. In this case, AMP agents will be managed, as well as apply for updates and a verdict for each analyzed file not to the cloud, but to the FireAMP Private Cloud virtual device located on the territory of the organization itself.
But the issue with access to the Internet still remains. How to make the system work in the complete absence of the Internet? To answer this question, we bought ThreatGRID at the end of May, which offers local security analytics devices that are now integrated with Cisco AMP.
In conclusion, I want to say that the Cisco Advanced Malware Protection solution, in which Cisco now invests large resources, is becoming an integral part of our information security portfolio.
