Protection against DDoS attacks as a service of VimpelCom - and the history of tenders won
When a large online tender is announced, sometimes it happens that one application arrives quite quickly, and then the tender site falls under a strong DDoS attack. The attack in a strange way ends at the end of the tender. Since one application has arrived, it is she who wins. Many of our corporate clients face this problem (as well as the usual DDoS attacks from ill-wishers and blackmailers).
Now we provide protection as a service. This is done at two levels: by installing the Radware DefensePro hardware at the client and, if necessary, switching traffic to our cleaning center.
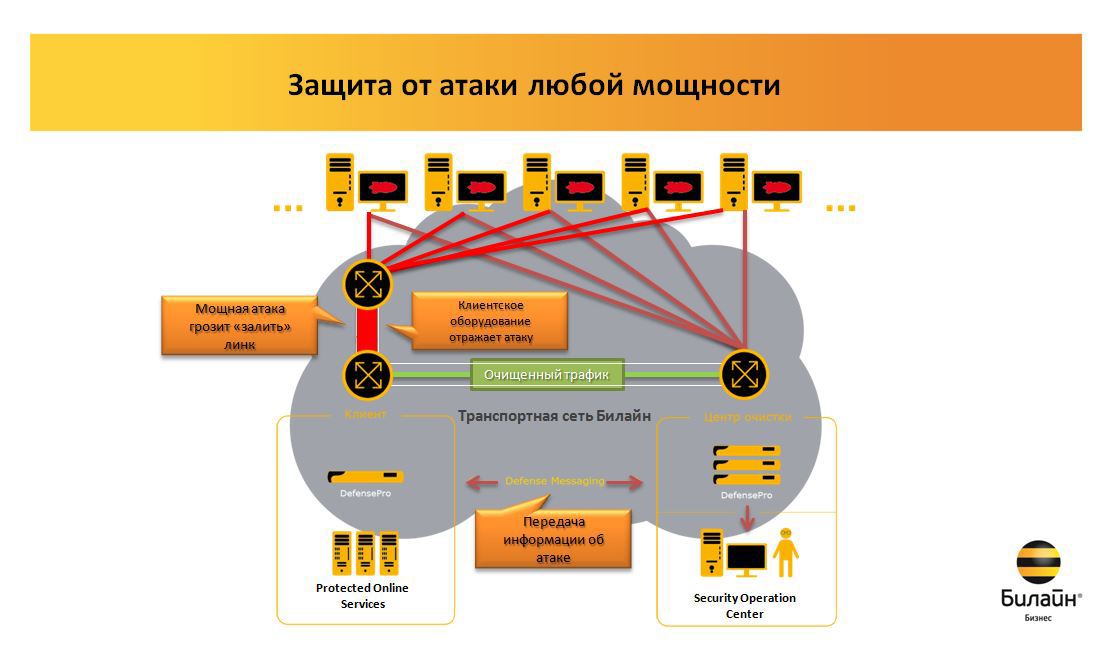
Maximum attack power - 80 Gb / s(at the application level, the more powerful ones are also filtered, but already without guarantees that there is no loss of legitimate traffic), we plan to expand to 160 as necessary. The time from the start to the reflection of the attack on the client side is 18 seconds maximum, on the side of the data center, up to 40 seconds taking into account traffic switching time. When switching, traffic loss does not occur.
As usual, when submitting the service, you first need to sign a contract with Beeline and fill out an order form (application) with the necessary information to connect. After that, DefensePro equipment is mounted and configured up to the first router at the entrance to your network. A dedicated technical channel is created to the control center (transparent to the client: it does not affect the main channel in any way and no bills are issued for it). Physically, this is the same optics (or another channel) as the main line, but the bandwidth is reserved so that even when the Internet access line is completely full at the time of a strong attack, the control channel works fine, and the equipment is available. Equipment through an IP VPN tunnel connects to a cleaning center.
Our equipment is under maintenance, we constantly monitor network activity on your channels. It is still necessary for you to provide a list of protected resources, their type, and also list all the ranges of networks available through communication channels. In addition, in the case of providing protection against DDoS attacks through other communication channels (other providers), it is necessary to provide the parameters of these channels. Integration of all this is done, if necessary, with the help of our specialists. It is possible to connect the service directly under attack (if our Internet channel is available). In this case, all client traffic is switched to the cleaning center. Engineers monitor the progress of attack reflection and, if necessary, participate in attack filtering. This is done within one business day.
The equipment itself does not affect legitimate traffic and has a mechanism for unhindered traffic passage in the event of equipment failure. An emergency bypass is started on the piece of iron (the “copper” ports are equipped with them “out of the box”, external ones are put into the optics) so that even when the scrap metal is inserted into it, the traffic will not be damaged.
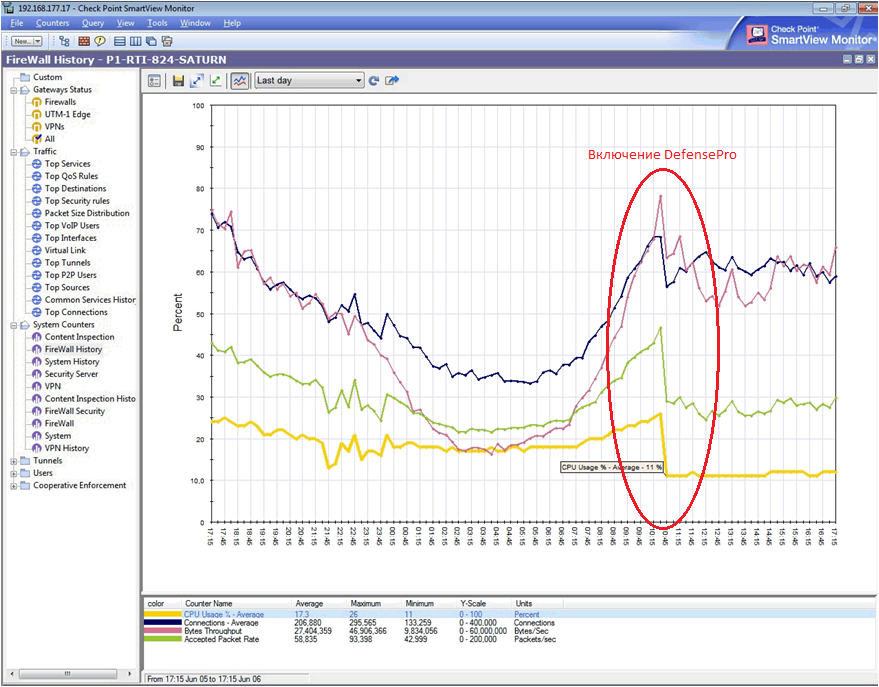
Below is a graph of the Firewall load, which clearly shows the inclusion of the attack reflection mode. It can be seen that the load on the CPU Firewall, located on the perimeter of the network, is reduced by more than 2 times. This is due to the filtering of spurious traffic on Defense Pro installed before the Firewall.
The hybrid scheme “Protection against DDoS attacks” is based on Radware DefensePro equipment. Today, Radware is a global leader in network and application security.
In the defensePro solution used, the following necessary protection mechanisms are implemented:
This list is far from complete, listing all types of protections takes 218 pages in the manufacturer's manual. DefensePro allows you to repel attacks up to the 7th level of the OSI model and at the same time not to cut legitimate users (that is, not to immediately close entire subnets by providers, as less accurate security tools can do).
DefensePro works in-line, invisible to network equipment (Transparent L2 Forwarding). This means that it is impossible to attack him, which guarantees the operation of the equipment in any conditions.
For the first week, the device works in training mode and collects statistics for traffic profiling.In some cases, training can last up to a month. Then the device switches to reflection mode and works with full efficiency. In an emergency installation, the training mode is reduced to the minimum necessary to start reflection, and the customer’s network is fully profiled somewhat later. If during the use for protection new devices or on-line services are added that lead to a change in the traffic profile, the equipment is retrained and adapted itself (even in the mode of reflection of attack, it continues to collect data). To ensure correct filtering with an incomplete training period, or in case of an emergency connection of the service under attack, a technical customer support service for this service is working in Beeline around the clock.
Your device reflects all attacks in the channel band and profiles traffic. When an attack occurs, it forms an attack signature for 18 seconds in a difficult case and 5-6 seconds in the general situation with the existing granular policy (well-described network). The device compares the channel width with the attack power. As soon as (manually set) the criticality value of the channel (for example, 20–30% of its capacity) is exceeded, the device reports to the Beeline cleaning center via a separate control channel about the situation and transmits profiles and signature. Traffic switches to the cleaning center within 40 seconds. The attack lands on our equipment, the return traffic goes to the same Internet channel.
It transfers either the entire segment (with a horizontal UDP flood) or a specific address. Since switching occurs inside the Beeline backbone network, there is no traffic gap.
Reverse switching is performed manually by the customer support service. The same command detects and reflects attacks that were not found in automatic mode. Switching traffic after the attack back is carried out by them manually, since there are no sufficiently accurate algorithms for determining the moments of termination of the attack.
The entire protection system and the cleaning center are organized on the Beeline transport network, which does not limit us to the total bandwidth of the channels that most other DDoS protection providers have to rent.
In case of various attacks at the moment of operation of alternative protection systems aimed at ensuring the availability of the communication channel, end users lose access to the on-line resource of the company. It turns out that the organization’s systems are protected, but the business process is completely stopped until the moment the attack ceases.
In case of using the Beeline DDoS Protection service from Beeline, access to the systems is open to users, while the attack is reflected in parallel and does not affect the passage of legitimate requests.
When attacking a group of slowloris and the like, as well as attacks with a wide geography, a careful approach is required to distinguish live users from bots. For example, to detect attacks inside SSL, the following is done at the hardware level:
Additionally, it is worth noting that the main issue of guaranteed attack reflection is the protection of the communication channel, which cannot be provided on the client side. In this regard, channel protection must be organized at the level of a telecom operator. Beeline cleaning center just solves this problem.
Most of our customers do not plan to talk about the fact that they have such protection installed, for obvious reasons. Nevertheless, spheres can be called - these are banks (traditionally concerned about security before an emergency), state-owned companies and large retail. The situation with tenders has already been described above - therefore, electronic platforms are connected to us. In addition, manufacturing companies come under protection: the fact is that under the terms of tenders it is often necessary to upload certain information on your website, and if suddenly the commission cannot verify this, the application will be withdrawn. As you can guess, putting such a site at the time of the tender is usually quite easy, which some interested parties use.
Actually, you can find out more about protection in the comments, and specify how to connect this service -right here .
Now we provide protection as a service. This is done at two levels: by installing the Radware DefensePro hardware at the client and, if necessary, switching traffic to our cleaning center.

Maximum attack power - 80 Gb / s(at the application level, the more powerful ones are also filtered, but already without guarantees that there is no loss of legitimate traffic), we plan to expand to 160 as necessary. The time from the start to the reflection of the attack on the client side is 18 seconds maximum, on the side of the data center, up to 40 seconds taking into account traffic switching time. When switching, traffic loss does not occur.
How it's done
As usual, when submitting the service, you first need to sign a contract with Beeline and fill out an order form (application) with the necessary information to connect. After that, DefensePro equipment is mounted and configured up to the first router at the entrance to your network. A dedicated technical channel is created to the control center (transparent to the client: it does not affect the main channel in any way and no bills are issued for it). Physically, this is the same optics (or another channel) as the main line, but the bandwidth is reserved so that even when the Internet access line is completely full at the time of a strong attack, the control channel works fine, and the equipment is available. Equipment through an IP VPN tunnel connects to a cleaning center.
Our equipment is under maintenance, we constantly monitor network activity on your channels. It is still necessary for you to provide a list of protected resources, their type, and also list all the ranges of networks available through communication channels. In addition, in the case of providing protection against DDoS attacks through other communication channels (other providers), it is necessary to provide the parameters of these channels. Integration of all this is done, if necessary, with the help of our specialists. It is possible to connect the service directly under attack (if our Internet channel is available). In this case, all client traffic is switched to the cleaning center. Engineers monitor the progress of attack reflection and, if necessary, participate in attack filtering. This is done within one business day.
The equipment itself does not affect legitimate traffic and has a mechanism for unhindered traffic passage in the event of equipment failure. An emergency bypass is started on the piece of iron (the “copper” ports are equipped with them “out of the box”, external ones are put into the optics) so that even when the scrap metal is inserted into it, the traffic will not be damaged.
Below is a graph of the Firewall load, which clearly shows the inclusion of the attack reflection mode. It can be seen that the load on the CPU Firewall, located on the perimeter of the network, is reduced by more than 2 times. This is due to the filtering of spurious traffic on Defense Pro installed before the Firewall.

How it works
The hybrid scheme “Protection against DDoS attacks” is based on Radware DefensePro equipment. Today, Radware is a global leader in network and application security.
In the defensePro solution used, the following necessary protection mechanisms are implemented:
- Behavioral DDoS Protection;
- TCP SYN Flood Protection;
- Connection Limit;
- HTTP Mitigator;
- Behavioral Server-Cracking Protection;
- Bandwidth Management
- Signature Protection;
- Stateful inspection
- Anti-Scanning Protection;
- Stateful Firewall (ACL).
This list is far from complete, listing all types of protections takes 218 pages in the manufacturer's manual. DefensePro allows you to repel attacks up to the 7th level of the OSI model and at the same time not to cut legitimate users (that is, not to immediately close entire subnets by providers, as less accurate security tools can do).
DefensePro works in-line, invisible to network equipment (Transparent L2 Forwarding). This means that it is impossible to attack him, which guarantees the operation of the equipment in any conditions.
For the first week, the device works in training mode and collects statistics for traffic profiling.In some cases, training can last up to a month. Then the device switches to reflection mode and works with full efficiency. In an emergency installation, the training mode is reduced to the minimum necessary to start reflection, and the customer’s network is fully profiled somewhat later. If during the use for protection new devices or on-line services are added that lead to a change in the traffic profile, the equipment is retrained and adapted itself (even in the mode of reflection of attack, it continues to collect data). To ensure correct filtering with an incomplete training period, or in case of an emergency connection of the service under attack, a technical customer support service for this service is working in Beeline around the clock.
Your device reflects all attacks in the channel band and profiles traffic. When an attack occurs, it forms an attack signature for 18 seconds in a difficult case and 5-6 seconds in the general situation with the existing granular policy (well-described network). The device compares the channel width with the attack power. As soon as (manually set) the criticality value of the channel (for example, 20–30% of its capacity) is exceeded, the device reports to the Beeline cleaning center via a separate control channel about the situation and transmits profiles and signature. Traffic switches to the cleaning center within 40 seconds. The attack lands on our equipment, the return traffic goes to the same Internet channel.
It transfers either the entire segment (with a horizontal UDP flood) or a specific address. Since switching occurs inside the Beeline backbone network, there is no traffic gap.
Reverse switching is performed manually by the customer support service. The same command detects and reflects attacks that were not found in automatic mode. Switching traffic after the attack back is carried out by them manually, since there are no sufficiently accurate algorithms for determining the moments of termination of the attack.
The entire protection system and the cleaning center are organized on the Beeline transport network, which does not limit us to the total bandwidth of the channels that most other DDoS protection providers have to rent.
Why don't users suffer
In case of various attacks at the moment of operation of alternative protection systems aimed at ensuring the availability of the communication channel, end users lose access to the on-line resource of the company. It turns out that the organization’s systems are protected, but the business process is completely stopped until the moment the attack ceases.
In case of using the Beeline DDoS Protection service from Beeline, access to the systems is open to users, while the attack is reflected in parallel and does not affect the passage of legitimate requests.
When attacking a group of slowloris and the like, as well as attacks with a wide geography, a careful approach is required to distinguish live users from bots. For example, to detect attacks inside SSL, the following is done at the hardware level:
- First, the 302nd redirect is sent to the user. Approximately half of the botnets do not pass it - as a rule, the stories “let's fill up a competitor cheaply for a seasonal peak” end there.
- If the botnet performs a redirect, each individual client receives Javascript literally on 3 lines. Modern botnets do not pass this script.
- Theoretically, at the moment, a solution has been created that allows you to pass this second level of protection. Especially for such situations, the equipment manufacturer has its own team of ERT specialists (Emergency Response Team), carefully studying closed specialized resources. Accordingly, these experts found and predefined this tool and have protection. Once it is used, the protection will turn on.
- A quick response team is available 24/7 on the support phone. When a new bypass of protection is released, new methods “roll” in 5 minutes. These 5 minutes, the resource will experience problems, but these are the principles of this "shield and sword" race.
Additionally, it is worth noting that the main issue of guaranteed attack reflection is the protection of the communication channel, which cannot be provided on the client side. In this regard, channel protection must be organized at the level of a telecom operator. Beeline cleaning center just solves this problem.
Where is used
Most of our customers do not plan to talk about the fact that they have such protection installed, for obvious reasons. Nevertheless, spheres can be called - these are banks (traditionally concerned about security before an emergency), state-owned companies and large retail. The situation with tenders has already been described above - therefore, electronic platforms are connected to us. In addition, manufacturing companies come under protection: the fact is that under the terms of tenders it is often necessary to upload certain information on your website, and if suddenly the commission cannot verify this, the application will be withdrawn. As you can guess, putting such a site at the time of the tender is usually quite easy, which some interested parties use.
Actually, you can find out more about protection in the comments, and specify how to connect this service -right here .
