SAP ABAP: Crossing Checkpoint Charlie in a SAAB (article translated from scn.sap.com)
- From the sandbox
- Tutorial
Good afternoon, dear habrozhitel!
As an ABAP developer, I want to contribute to improving the quality of custom SAP programs. For this purpose, I want to publish a series of translations of articles on interesting and most importantly useful and not very common techniques from the SAP knowledge base ( SAP community network ). The key concepts are quite difficult to translate into Russian, various interpretations create confusion, so I quote them in English.
From the Author:
Strange article title? I bind transaction SAAB and the third letter of the Latin alphabet (Charlie = C). In particular, the article will discuss Logpoints. The ABAP Logpoints are available from the NW2004s version.
Since the introduction of this technique in 2005, the topic has been discussed several times on SCN, for example:
Despite all the advantages of using the checkpoint group, the technology is still not widely used in custom ABAP developments. One of the possible reasons is the developers' lack of use and awareness of the advantages of technology. This article focuses on one of the possible scenarios for using logpoints. Also consider a step-by-step example of using logpoints. Separately, I note that this is not a complete guide to using checkpoint group. For a full study of the topic, I recommend contacting help.sap.com . An example of an ABAP program also does not pretend to be a standard; this code was invented to study a specific example.
Quite often you have to face a recurring problem over and over again. For example, an error occurs in a productive system that cannot be reproduced in either the test or development system. The functional consultant nods to the developer, in turn, the developer is sure that the problem is with the system configuration (i.e. the consultant). The developer compares the code on all systems and does not find any discrepancies. In the test, everything works correctly and the developer again turns to the consultant. The consultant, in turn, checks the configurations, and also does not find differences and considers that there is an error in the ABAP code. The circle is closed. The end user is very worried that his problem is still not resolved and urgently needs to be fixed. The developer decides to consider the problem more deeply. After studying the application log, it can localize the place where the problem occurred, but the reason for its appearance is still not clear. It would be very useful to find out what data the program operates in order to compare with another system, but debugging in the product, for many reasons, is impossible.
Below is an elementary example that allows you to understand how easy it is to use logpoints. The following describes how to declare the input and output parameters of an arbitrary method for their logging (entry in Log). I recommend, for important methods, to declare logging of incoming and outgoing parameters. Developers, in turn, can declare arbitrary variables for logging.
Following the general idea of the article, a class was created with the BORDER_CONTROL method. The method declared input and output parameters (tables). The table structure contains the fields name, description, nationality, date, and an arbitrary flag.
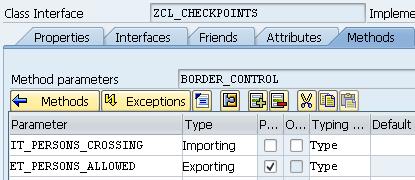

For testing, the program that calls the table processing method is presented below:
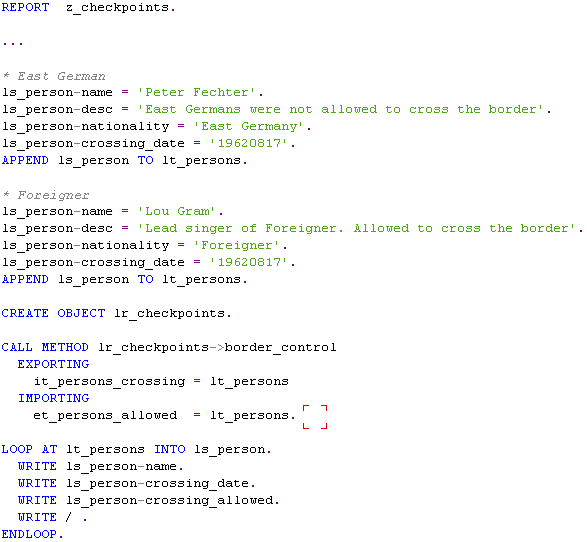
To be able to maintain Logpoint, you must create and activate a Checkpoint Group.
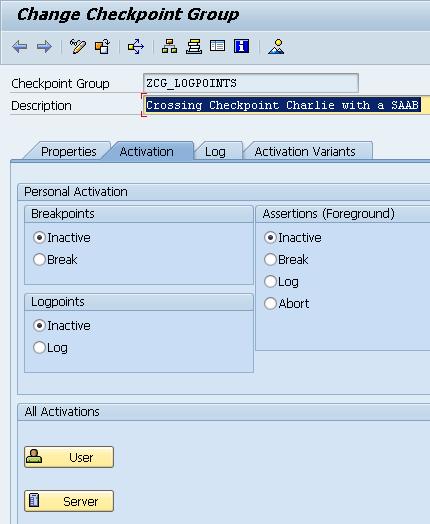
For the Logpoints parameter, change the state to Log.

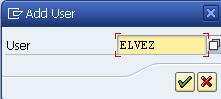
It is also possible to define a specific user for log. The option is available after pressing the User button.
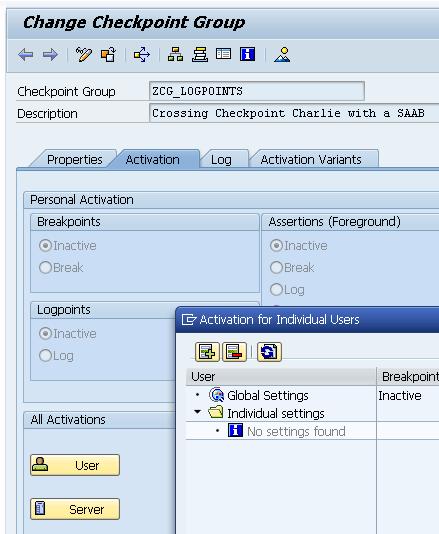
Click and enter the username.
and enter the username.
Save the checkpoint group. When saving, a dialog will be offered where it is necessary to determine the period of activity of the group. Strong recommendation to activate Log immediately before and deactivate immediately after running the program. This recommendation arises because the tables in which the Log records are stored are not automatically maintained and can accumulate impressive data arrays.

After activating the group, run the test program. After processing, a log will be created (SAAP-> Checkpoint group-> Log tab). By opening the
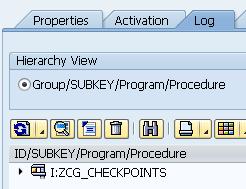
tree with log entries, it is possible to view the variables / tables specified for saving (for the FIELDS parameter for the LOG-POINT operator, see the method code). In this example, the input and output table of the BORDER_CONTROL method are specified as parameters.

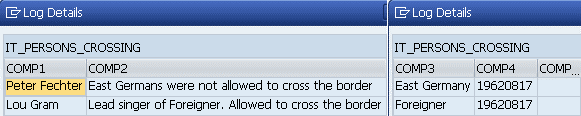
We can see the entries in the incoming table: The
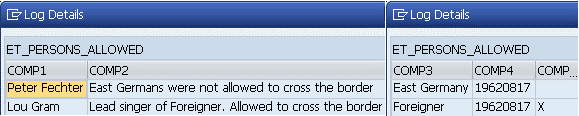
outgoing table contains the processed entries with the flag checked:
Using this information, the developer can get an array of data with which to localize and find a possible problem, or reproduce the situation in another system for further debugging. The time required to supplement your Logpoint code is minimal and the author hopes that the number of checkpoint groups used in user development will increase.
In this article, the author described one example explaining the benefits of using Logpoints. There are many other possible uses not described in this example.
If you are already using checkpoint groups, please write your experience in the comments.
Checkpoint Charlie information can be found here .
The original article can be found atlink .
As an ABAP developer, I want to contribute to improving the quality of custom SAP programs. For this purpose, I want to publish a series of translations of articles on interesting and most importantly useful and not very common techniques from the SAP knowledge base ( SAP community network ). The key concepts are quite difficult to translate into Russian, various interpretations create confusion, so I quote them in English.
From the Author:
Strange article title? I bind transaction SAAB and the third letter of the Latin alphabet (Charlie = C). In particular, the article will discuss Logpoints. The ABAP Logpoints are available from the NW2004s version.
Since the introduction of this technique in 2005, the topic has been discussed several times on SCN, for example:
- Checkpoint-Group the powerful friend of every ABAPer but ... beware! by Andrea Olivieri
- How to Instrument Your ABAP Code With Checkpoint Groups by Claudia Dangers
Despite all the advantages of using the checkpoint group, the technology is still not widely used in custom ABAP developments. One of the possible reasons is the developers' lack of use and awareness of the advantages of technology. This article focuses on one of the possible scenarios for using logpoints. Also consider a step-by-step example of using logpoints. Separately, I note that this is not a complete guide to using checkpoint group. For a full study of the topic, I recommend contacting help.sap.com . An example of an ABAP program also does not pretend to be a standard; this code was invented to study a specific example.
1. Use Case
Quite often you have to face a recurring problem over and over again. For example, an error occurs in a productive system that cannot be reproduced in either the test or development system. The functional consultant nods to the developer, in turn, the developer is sure that the problem is with the system configuration (i.e. the consultant). The developer compares the code on all systems and does not find any discrepancies. In the test, everything works correctly and the developer again turns to the consultant. The consultant, in turn, checks the configurations, and also does not find differences and considers that there is an error in the ABAP code. The circle is closed. The end user is very worried that his problem is still not resolved and urgently needs to be fixed. The developer decides to consider the problem more deeply. After studying the application log, it can localize the place where the problem occurred, but the reason for its appearance is still not clear. It would be very useful to find out what data the program operates in order to compare with another system, but debugging in the product, for many reasons, is impossible.
2. Example
Below is an elementary example that allows you to understand how easy it is to use logpoints. The following describes how to declare the input and output parameters of an arbitrary method for their logging (entry in Log). I recommend, for important methods, to declare logging of incoming and outgoing parameters. Developers, in turn, can declare arbitrary variables for logging.
2.1 Program
Following the general idea of the article, a class was created with the BORDER_CONTROL method. The method declared input and output parameters (tables). The table structure contains the fields name, description, nationality, date, and an arbitrary flag.


For testing, the program that calls the table processing method is presented below:

2.2 Configuring Checkpoint Group
To be able to maintain Logpoint, you must create and activate a Checkpoint Group.

For the Logpoints parameter, change the state to Log.

It is also possible to define a specific user for log. The option is available after pressing the User button.

Click
 and enter the username.
and enter the username. 
Save the checkpoint group. When saving, a dialog will be offered where it is necessary to determine the period of activity of the group. Strong recommendation to activate Log immediately before and deactivate immediately after running the program. This recommendation arises because the tables in which the Log records are stored are not automatically maintained and can accumulate impressive data arrays.

After activating the group, run the test program. After processing, a log will be created (SAAP-> Checkpoint group-> Log tab). By opening the

tree with log entries, it is possible to view the variables / tables specified for saving (for the FIELDS parameter for the LOG-POINT operator, see the method code). In this example, the input and output table of the BORDER_CONTROL method are specified as parameters.

We can see the entries in the incoming table: The

outgoing table contains the processed entries with the flag checked:

Using this information, the developer can get an array of data with which to localize and find a possible problem, or reproduce the situation in another system for further debugging. The time required to supplement your Logpoint code is minimal and the author hopes that the number of checkpoint groups used in user development will increase.
In this article, the author described one example explaining the benefits of using Logpoints. There are many other possible uses not described in this example.
If you are already using checkpoint groups, please write your experience in the comments.
Checkpoint Charlie information can be found here .
The original article can be found atlink .
