Kali Linux introduces an "emergency" password, leading to full disk encryption
- Transfer
Kali Linux introduces an "emergency" password, leading to full disk encryption
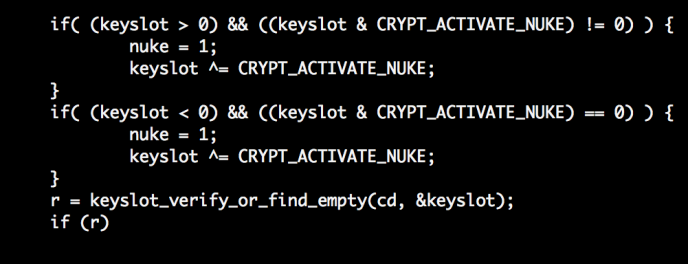
During the latest update, The Offensive Security Developer Team announced on Kali Linux [1]new feature “Emergency self-destruction of LUKS [2]", Designed to encrypt the entire disk using the utility
If you use an encrypted partition with LVM or LUKS in Kali Linux, then you need to enter a password during each boot of the OS - this will decrypt your disk. Those. if your laptop is stolen - do not worry about data safety.
Now you can use a password-destroyer, the entry of which will lead to destruction, rather than decryption of data from your disk during system boot.
In an emergency, entering a password-destroyer will delete all encryption keys, which will lead to a complete loss of access to data.
Without a doubt, I, like almost 3 thousand people, voted in favor of introducing such a feature, as I consider it very popular among hackers and computer security experts using Kali Linux.
Law enforcement agencies are silent about their work. The same NSA or FBI can at any time “ask” you to enter a password. Of course, you can refuse, but the employee can get you later, detain you, refuse to enter the country or in any other way annoy you.
In today's realities, disk encryption, or at least password blocking of a hard disk, is seen as simply necessary. Given the fact that there are quite a few utilities for disk encryption, including free ones - BitLocker, PGPDisk, FileVault, TrueCrypt, and dm-crypt (LUKS).
1. ↑ Kali Linux - an open source operating system based on Debian, designed for pentesting and hacking; includes an appropriate specialized set of utilities.
2. ↑ LUKS (The Linux Unified Key Setup) - specification of disk encryption, defines a platform-independent standard for use in various tools. The LUKS implementation for Linux is based on an extended version of cryptsetup, using dm-crypt as a disk encryption computer.

A little background
Today, full data encryption is the most “secure” storage method. Just think about what information is stored on your computer. Photos of cats , passwords, your email. In the end - working documents containing financial and trade secrets.
What can we say about those people who work in the field of security - their computers are crammed with confidential information related to their work, source codes, research results.
Now think - what if your laptop is stolen or selected by the security service of any airport? I will describe one situation.
You may have noticed the name of Glenn Greenwald, a Guardian employee, author of a series of articles published in July 2013 exposing the NSA thanks to documents provided by Edward Snowden some time ago in news feeds.
In August 2013, one of Glenn’s colleagues was returning from a trip to Berlin when he was stopped by airport security officers. Appealing to the Terrorism Act 2000, it was held for 9 hours, and at the same time all electronic devices were selected, including a mobile phone, laptop, camera, memory cards, DVD discs and even a game console!
In this situation, the person concerned can either steal your data or install spyware without your knowledge. And that’s where full disk encryption can help you keep your data private.
What can we say about those people who work in the field of security - their computers are crammed with confidential information related to their work, source codes, research results.
Now think - what if your laptop is stolen or selected by the security service of any airport? I will describe one situation.
You may have noticed the name of Glenn Greenwald, a Guardian employee, author of a series of articles published in July 2013 exposing the NSA thanks to documents provided by Edward Snowden some time ago in news feeds.
In August 2013, one of Glenn’s colleagues was returning from a trip to Berlin when he was stopped by airport security officers. Appealing to the Terrorism Act 2000, it was held for 9 hours, and at the same time all electronic devices were selected, including a mobile phone, laptop, camera, memory cards, DVD discs and even a game console!
In this situation, the person concerned can either steal your data or install spyware without your knowledge. And that’s where full disk encryption can help you keep your data private.
During the latest update, The Offensive Security Developer Team announced on Kali Linux [1]new feature “Emergency self-destruction of LUKS [2]", Designed to encrypt the entire disk using the utility
cryptsetup. If you use an encrypted partition with LVM or LUKS in Kali Linux, then you need to enter a password during each boot of the OS - this will decrypt your disk. Those. if your laptop is stolen - do not worry about data safety.
Now you can use a password-destroyer, the entry of which will lead to destruction, rather than decryption of data from your disk during system boot.
In an emergency, entering a password-destroyer will delete all encryption keys, which will lead to a complete loss of access to data.
Without a doubt, I, like almost 3 thousand people, voted in favor of introducing such a feature, as I consider it very popular among hackers and computer security experts using Kali Linux.
Law enforcement agencies are silent about their work. The same NSA or FBI can at any time “ask” you to enter a password. Of course, you can refuse, but the employee can get you later, detain you, refuse to enter the country or in any other way annoy you.
In today's realities, disk encryption, or at least password blocking of a hard disk, is seen as simply necessary. Given the fact that there are quite a few utilities for disk encryption, including free ones - BitLocker, PGPDisk, FileVault, TrueCrypt, and dm-crypt (LUKS).
1. ↑ Kali Linux - an open source operating system based on Debian, designed for pentesting and hacking; includes an appropriate specialized set of utilities.
2. ↑ LUKS (The Linux Unified Key Setup) - specification of disk encryption, defines a platform-independent standard for use in various tools. The LUKS implementation for Linux is based on an extended version of cryptsetup, using dm-crypt as a disk encryption computer.
Only registered users can participate in the survey. Please come in.
Would you set yourself a password destroyer?
- 13.2% No 402
- 31.1% Stop Pressing Me! 946
- 55.5% Yes 1685
