A simple solution for administering phones and tablets + an invitation to tests
This morning we launched the first Russian platform for administering mobile devices from the cloud for trial and commercial use.
You can pick up employee devices there and get the following features:
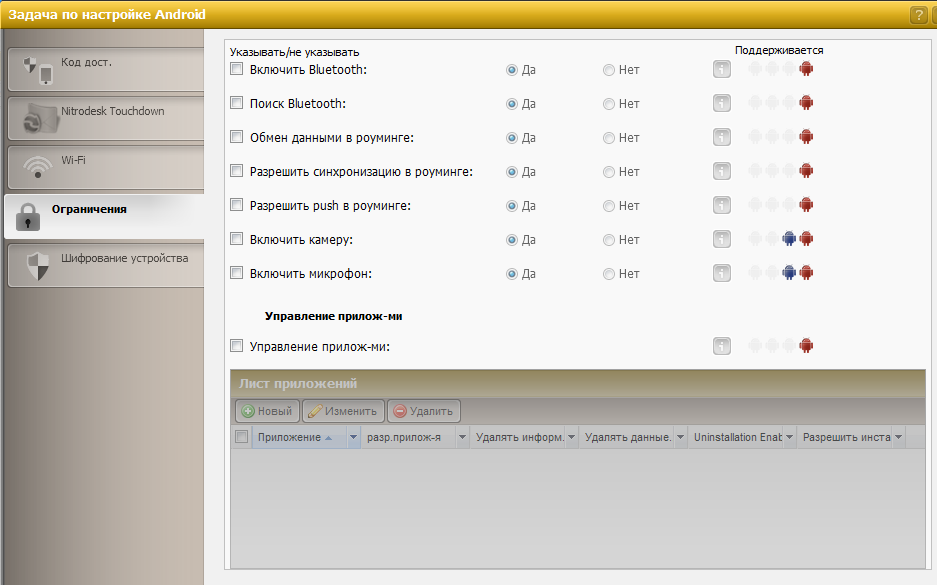
Smartphone restriction settings screen
Below I will tell you in detail about all this, as well as how to implement normal security in my company in two days. And if you are interested, then you can get free access to the platform until January 1, 2014 as part of the pilot commercial operation.
The last three years, probably, the topic of administration of mobile devices of employees (smartphones and tablets with different OSs) is one of the most frequently discussed at security conferences and among system administrators. Each time at such conferences it is said about "user safety and convenience", but we will be honest - the convenience lies only in the fact that they do not take away the phone at the entrance to the company and can configure mail and VPN without it. The main profits are that a lot of load is removed from the IT department and security personnel.
The MDM system was deployed on company servers or integrator servers. Typically, a single implementation for a company with more than 1000 employees cost from several million rubles and took from a month. There are examples of one and a half year implementation projects. Our MDM solution allows you to connect and deploy in a day (the longest part is signing the contract) and work right here and now.
Login page
Several agents are installed on his device (depending on the OS), each with its own functionality. After that, you can roll corporate applications onto the device, for example, an electronic document management system - and this is just an excellent plus for convenience. The MDM platform (Mobile Device Management) itself is just an administration tool, but a tool that provides adequate security so that critical data can be stored on the user's device. And the convenience is not to do this for each device by hand.

A screenshot of the settings, you can see some of the features on the tabs.
The flow of those running after the settings decreases. Now the diagram looks like this:
Once again: you received the number, registered it and indicated the group. Everything, the system works further. You do not even need to see the device or the employee himself.
The headache stops with the possibility of carrying out data and mail leaks. It is clear that whoever needs to be carried away will somehow seek a way, but leaks due to human stupidity will stop for sure. Plus, you won’t have to worry about lost or stolen devices - you can simply wipe them remotely.
You connect to the platform on the mdm.beeline.ru page as an administrator. Then start groups, for example, for different departments (you can work at the level of individual devices, but groups are more convenient). For each group, prescribe your settings and event triggers. Then simply enter the devices by phone numbers and assign a group. Moreover, one device can be in different groups.
Simply reassign him groups, the platform will do the rest.
Any devices with or without any SIM. That is, any personal and corporate phones and tablets.
All major mobile operating systems are supported: Android above 2.3, iOS 5 and above, as well as Windows Phone (7+) and even integration with BlackBerry is possible, but through their BES server. Plus, there is a separate part of the system that supports Symbian devices (deployed here for compatibility with older Nokia devices, although it is almost not used in the USA yet, their share is still quite high). It is important to understand that the control and settings capabilities of devices on Android depend not only on the version of the OS itself, but also on the vendor of a particular device. For example, Samsung of the latest generations has the greatest number of features from Android devices. The usual distribution of functionality: 2.3 - passwords, Exchange, communications, wipe, geolocation. In 3+ added camera controls, VPN, device encryption. In 4+, card management, its encryption, USB management,
In addition, we will constantly update the capabilities of our MDM platform. This migration will not affect end users.
It's simple - only 200 rubles per device per month with daily billing. Payment is taken only for activated devices, that is, if you send a mobile device to the Urals, and activate it in the system only six months later, payment will go from the moment it is activated.
Now it is possible to get free access to the MDM platform until January 2014 as part of testing - at the very end of the topic it is written where to write for this.
Configuration backups are stored on our platform servers in the cloud. Mail and other data that may be related to the concept of “trade secret” are not stored on intermediate servers. Roughly speaking, we provide transportation for management, but we do not store your data.
In addition to basic tools like SSL of your mail - no. All data is transmitted as you send it. There is no additional encryption service: this is done so that you do not have to obtain the appropriate permissions from the supervisory authorities. At the same time, 95% of the questions in practice are closed by the correct VPN setup.
Not. The maximum - he can see the count of mail traffic, but the messages themselves will not get into either the agent applications or the system. The solution does not touch the personal data on the device.
Theoretically, yes, there are such solutions for placement in their data centers, they are offered by various integrators. As I wrote above, in practice it turns out quite expensive at the implementation stage and for a long time. This is clearly not suitable for small and medium-sized businesses. Our solution is very convenient even for companies of 35 employees with 30 smartphones and 20 tablets
About two minutes.
Applications can be seen on the device as ordinary mobile applications. During installation, you must agree with all conditions a couple of times. He needs an Internet channel to receive control commands. In practice, the user, on average, once a month clicks “OK” on the changes that have occurred.
From a single interface (separate only for Symbian), you can configure device settings, restrictions, the corporate application market, event triggers, etc. The web interface works, by the way, on popular mobile browsers on tablets.
It all depends on the task. For example, an information security specialist can see the log of the time and duration of calls (but not hear them yourself), the log of the time of sending SMS (but not the messages themselves), system events, triggers, geolocation data (if enabled), search for corporate content.
Voice data is not affected by the MDM application in any way, nor is personal mail. But do not forget that at the same time you can see the details of calls by time and numbers, the time of sending SMS / MMS, and if the function of saving the geolocation is enabled (according to the requirements of the security department of your company), this data can be compared.
For implementation - to know what a "cloud" or SaaS is. For support - read the instructions 1-2 times. To install on your phone - be able to click "OK".
The fee is charged for devices activated on the platform per month. That is, if you know how many handsets and tablets you have in control, then you can plan costs with an accuracy of one ruble.
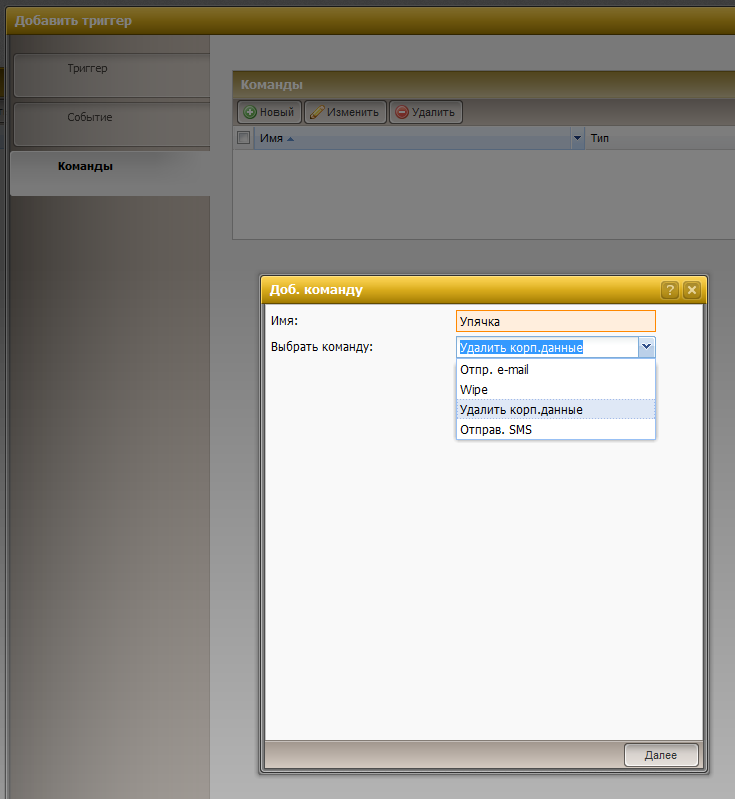
Yes. You can set up triggers by which certain sequences of commands are made. In particular, various threats to corporate data are collected in triggers. Here is an example of setting up an event:

Here is an example of setting up a reaction to it:
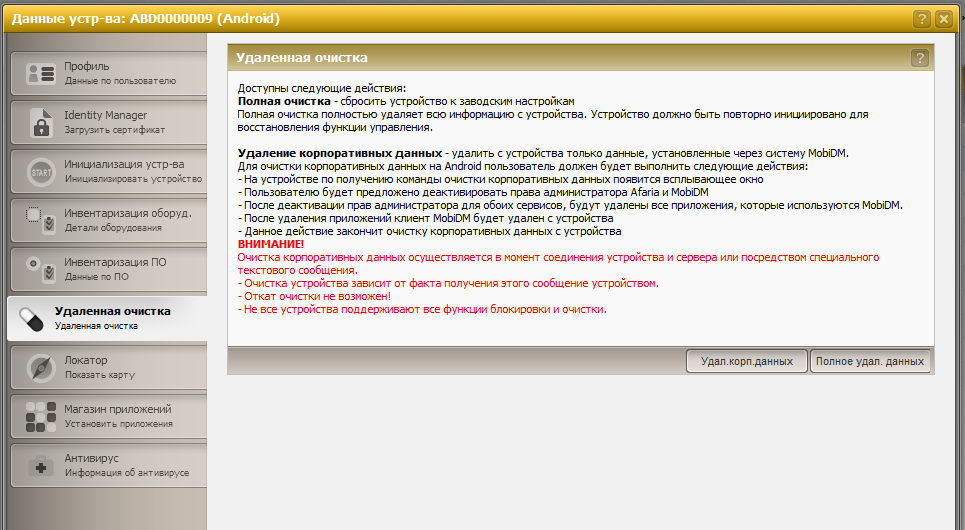
Yes, each individual device belongs to a group and can be controlled. Here, for example, is the data cleaning screen for one of the devices:
This is one of the common questions of journalists. I will explain that the platform does not allow receiving RDP or analogues for remote workstations. The platform allows you to administer devices, provides security policies and many other functions. Using MDM, you can install any application, including solutions for RDP access to your workstation or virtual machine. These applications can be registered on the platform as corporate, and the user will receive them together with the settings package.
1) First you need to understand why you need MDM. To evaluate this, you need:
2) Subscribe to the beta test below, find three or four devices, figure out what can and cannot be done. And how exactly your tasks are solved in practice.
3) Then you need to stock up with examples on the fingers, what will it give to explain to the rest of the departments. Security guards throw you their own, if necessary. Usually they convincingly give an example of the latest incident with the loss of important data.
4) Then the most important thing is to go through the finance department. They will be happy to know that the costs are not capital (a lot of money at once - and only then it will work), but operational (upon use).
5) After that, it is necessary to gather the heads of the IT department, IS, the financial department and those who are involved in mobile employees(possibly frames), if any, and talk about a possible implementation. Most likely, everyone will have their own wishes. By the way, AHO will also be interested - with MDM it is very easy to take an inventory of both software and hardware.
6) As a result, it will be necessary to collect at home:
7) Sign an additional agreement (you need a new document if you are not working with us or a simple additional agreement to the corporate contract for communication, if you are already our corporate client). A new contract can be taken at any sales office or ordered by phone + 7-499-277-77-77 .
8) After that, you can start users on the platform, it is possible together with personnel officers. It’s better to connect not all at once, but by department. In one department (it is better - in its own) it is worth running the procedure to widespread implementation.
9) The first settings are traditionally done:
Any local features like “turn off the camera at the entrance to the production area” and so on already go on.
Usually, the task goes down to the IT department either from the management or through the information security. If there is no such request, but you are simply tired of working manually with a very large fleet of mobile devices, then our platform is also for you. In such a situation, it is necessary to calculate the possible profits from the implementation for everyone (see above) and start.
You can "cleanly" delete all data from the platform. In addition, each user can remove certificates himself and uninstall MDM applications from the device. When the platform is disabled without additional actions, the certificate is revoked.
Write a request to services@beeline.ru with the heading "Application for MDM test from Habr". Please note that the service is available only for individual entrepreneurs or legal entities, therefore, in the letter you need to indicate the full name of the company, company TIN, full name and administrator’s mail for receiving a password, plus the administrator’s cell phone for communication.
In response, I urge you to tell about all the features you need and send bug reports if something strange comes to your attention.
You can pick up employee devices there and get the following features:
- Send security certificates , including data for corporate mail, Wi-Fi, VPN and other settings.
- Create a container for corporate data and clean it if necessary.
- Assign security policies like turning off the camera, tracking the device, and so on.
- Assign triggers to various events , for example, wipe corporate data when trying to jailbreak.

Smartphone restriction settings screen
Below I will tell you in detail about all this, as well as how to implement normal security in my company in two days. And if you are interested, then you can get free access to the platform until January 1, 2014 as part of the pilot commercial operation.
Why is all this necessary?
The last three years, probably, the topic of administration of mobile devices of employees (smartphones and tablets with different OSs) is one of the most frequently discussed at security conferences and among system administrators. Each time at such conferences it is said about "user safety and convenience", but we will be honest - the convenience lies only in the fact that they do not take away the phone at the entrance to the company and can configure mail and VPN without it. The main profits are that a lot of load is removed from the IT department and security personnel.
How was this done before the cloud solution?
The MDM system was deployed on company servers or integrator servers. Typically, a single implementation for a company with more than 1000 employees cost from several million rubles and took from a month. There are examples of one and a half year implementation projects. Our MDM solution allows you to connect and deploy in a day (the longest part is signing the contract) and work right here and now.

Login page
What does the user get?
Several agents are installed on his device (depending on the OS), each with its own functionality. After that, you can roll corporate applications onto the device, for example, an electronic document management system - and this is just an excellent plus for convenience. The MDM platform (Mobile Device Management) itself is just an administration tool, but a tool that provides adequate security so that critical data can be stored on the user's device. And the convenience is not to do this for each device by hand.

A screenshot of the settings, you can see some of the features on the tabs.
What does the IT department get?
The flow of those running after the settings decreases. Now the diagram looks like this:
- The employee sends you his phone number (and mail, if we are talking about the iPad, which can not read SMS),
- You pick up this number in the MDM platform and assign a group (for example - roll the settings like all the employees of the call center),
- The system itself sends the user an SMS with a link to the ordering application agent
- The user downloads it, clicks OK a couple of times on what he is prescribed in the rights and receives all the settings.
Once again: you received the number, registered it and indicated the group. Everything, the system works further. You do not even need to see the device or the employee himself.
What is important for information security?
The headache stops with the possibility of carrying out data and mail leaks. It is clear that whoever needs to be carried away will somehow seek a way, but leaks due to human stupidity will stop for sure. Plus, you won’t have to worry about lost or stolen devices - you can simply wipe them remotely.
What is usually set up first?
- A block of typical Wi-Fi settings, corporate VPN settings, and so on.
- Access to corporate mail.
- If the company uses enterprise applications, then access to them.
- Backup to the platform in case of loss of the device, so that you can raise the profile in a matter of minutes back to the new device.
- Wipe corporate data on dismissal, attempt to jailbreak, etc.
What does the system setup look like?
You connect to the platform on the mdm.beeline.ru page as an administrator. Then start groups, for example, for different departments (you can work at the level of individual devices, but groups are more convenient). For each group, prescribe your settings and event triggers. Then simply enter the devices by phone numbers and assign a group. Moreover, one device can be in different groups.
What if an employee moves from department to department?
Simply reassign him groups, the platform will do the rest.
Which device can be connected?
Any devices with or without any SIM. That is, any personal and corporate phones and tablets.
Which OS are supported?
All major mobile operating systems are supported: Android above 2.3, iOS 5 and above, as well as Windows Phone (7+) and even integration with BlackBerry is possible, but through their BES server. Plus, there is a separate part of the system that supports Symbian devices (deployed here for compatibility with older Nokia devices, although it is almost not used in the USA yet, their share is still quite high). It is important to understand that the control and settings capabilities of devices on Android depend not only on the version of the OS itself, but also on the vendor of a particular device. For example, Samsung of the latest generations has the greatest number of features from Android devices. The usual distribution of functionality: 2.3 - passwords, Exchange, communications, wipe, geolocation. In 3+ added camera controls, VPN, device encryption. In 4+, card management, its encryption, USB management,
In addition, we will constantly update the capabilities of our MDM platform. This migration will not affect end users.
How much is?
It's simple - only 200 rubles per device per month with daily billing. Payment is taken only for activated devices, that is, if you send a mobile device to the Urals, and activate it in the system only six months later, payment will go from the moment it is activated.
Now it is possible to get free access to the MDM platform until January 2014 as part of testing - at the very end of the topic it is written where to write for this.
Where are corporate data stored?
Configuration backups are stored on our platform servers in the cloud. Mail and other data that may be related to the concept of “trade secret” are not stored on intermediate servers. Roughly speaking, we provide transportation for management, but we do not store your data.
Is there data encryption?
In addition to basic tools like SSL of your mail - no. All data is transmitted as you send it. There is no additional encryption service: this is done so that you do not have to obtain the appropriate permissions from the supervisory authorities. At the same time, 95% of the questions in practice are closed by the correct VPN setup.
Can an administrator access personal email on a smartphone?
Not. The maximum - he can see the count of mail traffic, but the messages themselves will not get into either the agent applications or the system. The solution does not touch the personal data on the device.
Is it possible to deploy all the server room at home?
Theoretically, yes, there are such solutions for placement in their data centers, they are offered by various integrators. As I wrote above, in practice it turns out quite expensive at the implementation stage and for a long time. This is clearly not suitable for small and medium-sized businesses. Our solution is very convenient even for companies of 35 employees with 30 smartphones and 20 tablets
How fast does a new device connect?
About two minutes.
Does the employee know about MDM applications, see traces of his activity?
Applications can be seen on the device as ordinary mobile applications. During installation, you must agree with all conditions a couple of times. He needs an Internet channel to receive control commands. In practice, the user, on average, once a month clicks “OK” on the changes that have occurred.
How to admin manage devices?
From a single interface (separate only for Symbian), you can configure device settings, restrictions, the corporate application market, event triggers, etc. The web interface works, by the way, on popular mobile browsers on tablets.
What sees IB?
It all depends on the task. For example, an information security specialist can see the log of the time and duration of calls (but not hear them yourself), the log of the time of sending SMS (but not the messages themselves), system events, triggers, geolocation data (if enabled), search for corporate content.
"Do they listen to my personal conversations?"
Voice data is not affected by the MDM application in any way, nor is personal mail. But do not forget that at the same time you can see the details of calls by time and numbers, the time of sending SMS / MMS, and if the function of saving the geolocation is enabled (according to the requirements of the security department of your company), this data can be compared.
What is the qualification of employees and what is required?
For implementation - to know what a "cloud" or SaaS is. For support - read the instructions 1-2 times. To install on your phone - be able to click "OK".
How accurately are the costs planned?
The fee is charged for devices activated on the platform per month. That is, if you know how many handsets and tablets you have in control, then you can plan costs with an accuracy of one ruble.
Is it possible to detect jailbreak on a device?
Yes. You can set up triggers by which certain sequences of commands are made. In particular, various threats to corporate data are collected in triggers. Here is an example of setting up an event:

Here is an example of setting up a reaction to it:

Is it possible to administer one separately taken device?
Yes, each individual device belongs to a group and can be controlled. Here, for example, is the data cleaning screen for one of the devices:

How quickly can I access a document on my desktop desktop while sitting in a cafe in Amsterdam?
This is one of the common questions of journalists. I will explain that the platform does not allow receiving RDP or analogues for remote workstations. The platform allows you to administer devices, provides security policies and many other functions. Using MDM, you can install any application, including solutions for RDP access to your workstation or virtual machine. These applications can be registered on the platform as corporate, and the user will receive them together with the settings package.
How to implement MDM in your company?
1) First you need to understand why you need MDM. To evaluate this, you need:
- Assess who does what on mobile devices. Most likely, this is primarily about mail. If there is something critical to the "drain", you need to protect.
- If you have enterprise applications, then with MDM it will be much easier.
- Understand how many people in the company use their personal devices and how often they ask for help on Wi-Fi and VPN settings.
- If you have your own tablets or phones distributed (often important for, for example, merchandisers), MDM will be very useful in the work of the IT department to manage them.
- Find out if the task is to collect statistics for the general or commercial about the working day of employees or to increase productivity. If so, then this MDM will help to do this.
2) Subscribe to the beta test below, find three or four devices, figure out what can and cannot be done. And how exactly your tasks are solved in practice.
3) Then you need to stock up with examples on the fingers, what will it give to explain to the rest of the departments. Security guards throw you their own, if necessary. Usually they convincingly give an example of the latest incident with the loss of important data.
4) Then the most important thing is to go through the finance department. They will be happy to know that the costs are not capital (a lot of money at once - and only then it will work), but operational (upon use).
5) After that, it is necessary to gather the heads of the IT department, IS, the financial department and those who are involved in mobile employees(possibly frames), if any, and talk about a possible implementation. Most likely, everyone will have their own wishes. By the way, AHO will also be interested - with MDM it is very easy to take an inventory of both software and hardware.
6) As a result, it will be necessary to collect at home:
- List of users and their contacts.
- List of devices.
- Security policies (what is allowed to which department, what to do when hiring an employee, what to do when firing).
- Certificates for authorization on your mail servers.
7) Sign an additional agreement (you need a new document if you are not working with us or a simple additional agreement to the corporate contract for communication, if you are already our corporate client). A new contract can be taken at any sales office or ordered by phone + 7-499-277-77-77 .
8) After that, you can start users on the platform, it is possible together with personnel officers. It’s better to connect not all at once, but by department. In one department (it is better - in its own) it is worth running the procedure to widespread implementation.
9) The first settings are traditionally done:
- Knurling corporate applications and jailbreak detection.
- VPN for communication with corporate systems.
- Mail (e.g. Exchange).
- Corporate Wi-Fi.
- Configure wipe corporate data.
- Setting up a full wipe when an employee calls tech support with an incident “stole the phone”.
- Strong password policy on the piece of iron (solves 95% of cases of device theft).
- Backups of device settings.
- Determination of the geolocation for employees “in the fields”, for example, couriers.
Any local features like “turn off the camera at the entrance to the production area” and so on already go on.
How to intuitively understand that a company needs a solution?
Usually, the task goes down to the IT department either from the management or through the information security. If there is no such request, but you are simply tired of working manually with a very large fleet of mobile devices, then our platform is also for you. In such a situation, it is necessary to calculate the possible profits from the implementation for everyone (see above) and start.
What do you need to remember?
- Payment - 200 rubles per device per month, but now you can work for several months for free.
- The service is available for legal entities and individual entrepreneurs (and is not available to individuals).
- To activate the service, it is enough to conclude an additional agreement if you are already our corporate client. Or a Beeline mobile agreement with one SIM, if not yet our client.
- At the end of each month, a single invoice is issued for all communication services, where there will also be a subscription fee for MDM, which must be paid within 25 days. If the bill is not paid, the platform goes into freeze mode (saving all settings and data for a while). You can configure automatic notifications to administrators about the status of the account.
- In the supplementary agreement, administrator details for access to the platform (mail, phone, full name) are prescribed. They can be changed immediately after the first login.
What happens when disconnected?
You can "cleanly" delete all data from the platform. In addition, each user can remove certificates himself and uninstall MDM applications from the device. When the platform is disabled without additional actions, the certificate is revoked.
How to get free access to the system?
Write a request to services@beeline.ru with the heading "Application for MDM test from Habr". Please note that the service is available only for individual entrepreneurs or legal entities, therefore, in the letter you need to indicate the full name of the company, company TIN, full name and administrator’s mail for receiving a password, plus the administrator’s cell phone for communication.
In response, I urge you to tell about all the features you need and send bug reports if something strange comes to your attention.
