Microsoft and Adobe released updates for their products, September 2013
Microsoft announced the release of a series of updates aimed at fixing vulnerabilities in their products. The security fixes announced earlier in the pre-release (September 5) cover more than 50 unique vulnerabilities (4 fixes with Critical status and 10 with Important status). Detailed report (including corrections of corrections with CVE ID) can be found here . One of the MS13-069 updates is aimed at fixing ten Critical vulnerabilities in Internet Explorer (starting from the 6th version and ending with the latest IE 10 for all Windows XP - 8 - RT, x32 and x64 operating systems, server versions of the OS like Moderate). Vulnerabilities are of type Remote Code Execution(memory-corruption) and can be used to covertly install malicious code (drive-by). To apply the hotfix, you need to restart.

In September, details of exploiting the RCE vulnerability in win32k.sys, which was closed by MS13-053 and can be used to bypass the sandbox mode restrictions in the Google Chrome browser, became known in Google (Google Chrome full sandbox bypass w / win32k, WebKit / Blink flaws via CVE-2013- 0912, CVE-2013-1300). A successful demonstration of the exploit bundle for conducting a drive-by attack in the latest [at that time] version of Chrome was demonstrated at Pwn2Own 2013, as we wrote about earlier . In the pastIn a month, Microsoft closed the vulnerabilities in the latest version of Internet Explorer and the ASLR mechanism, which were used to successfully conduct a drive-by attack in the framework of Pwn2Own 2013.

In addition to Internet Explorer, OS components of different versions, Outlook mail client and MS SharePoint were updated. This month's patch tuesday differs from others in a large number of Remote Code Execution (RCE) fixes in Microsoft Office, SharePoint, Windows, and IE. Only 8 updates fix these vulnerabilities through which an attacker can successfully run remote code on a system with vulnerable software.
In the case of the vulnerability in win32k.sys CVE-2013-1300 ( MS13-053 ), which could be used to execute arbitrary code, we are talking about using an undocumented functionwin32k! NtUserMessageCall .
W32KAPI LRESULT NtUserMessageCall (IN HWND hwnd, IN UINT msg, IN WPARAM wParam, IN LPARAM lParam, IN ULONG_PTR xParam, IN DWORD xpfnProc, IN BOOL bAnsi);
This function is used to forward messages between threads during GUI interaction within the Win32 (Windows) subsystem. For some types of messages, it allocates a memory buffer, which will then be filled with the called party, that is, the thread that is waiting for the message. The following is a stack of function calls when a caller sends a message.
The following is a stack of function calls when a message is received by the receiving party, and the buffer allocated by xxxSendMessageEx -> ...-> Win32AllocPoolWithQuota is filled .
xxxInterSendMsgEx is an important function because it is responsible for directly delivering a message from one thread to another. An error in the code is present when the last argument of the NtUserMessageCall bAnsi is incorrectly interpreted by a function that allocates memory and a function that fills it. The function that allocates memory treats this argument as a boolean type. In this case, the value 0 for it is false and means the use of WCHAR characters. A nonzero value is considered by the function as an indication of the use of ASCII characters and the allocation of a memory block of the appropriate size. However, a function that performs a character copy operation believes that this argument is a bitmask and is used to distinguish between ASCII and WCHAR. Thus, when this argument is equal to an even number and not equal to zero, both functions will interpret this value differently. For example, with a value of 2, the highlight function will assume that a buffer of the appropriate size should be allocated to store the string of ASCII characters. When it comes to copying, the CopyOutputString functionwill consider the string as a WCHAR and copy twice as much memory as needed, thus causing a buffer overflow. Using the opportunity to exploit this vulnerability and CVE-2013-0912, an attacker could execute arbitrary code from a browser, thus bypassing the limitations of the sandbox mode.
Update MS13-067 (Critical) addresses ten vulnerabilities in Microsoft Office Server software (Office Web Apps / Server Software). Vulnerabilities CVE-2013-3847, CVE-2013-3848, CVE-2013-3849, CVE-2013-3857, and CVE-2013-3858 are present in Word (part of Office Web Apps 2010 and SharePoint Server 2010) and, through them, an attacker could execute remote code through a specially formed file.
Update MS13-068(Critical) addresses the RCE vulnerability CVE-2013-3870 in the Outlook 2007-2010 mail client. The attacker can execute arbitrary code through a specially crafted message for the vulnerable version of the client. Exploit code would be difficult to build .
The MS13-070 (Critical) update addresses the CVE-2013-3863 vulnerability in the OLE engine of Windows XP SP3 [x64 SP2] and Windows Server 2003 SP2. An attacker can execute arbitrary code with the rights of the current user through a specially formed OLE object. Exploit code likely .
Update MS13-071(Important) addresses the vulnerability CVE-2013-0810 in Windows XP SP3, Server 2003 SP2 and Windows Vista SP2, Server 2008 SP2. The attacker can execute the remote code in the system through a specially formed theme file. Such a file must be delivered to the user, for example, using a phishing message. Thus, the user himself must initiate the opening of the file, otherwise the attack cannot be successful. Exploit code likely .
Update MS13-072(Important) fixes 13 vulnerabilities in Microsoft Office 2003 (Microsoft Word 2003 and Microsoft Word Viewer), Office 2007 (Word 2007 and Office Compatibility Pack), and Microsoft Word 2010 - memory corruption. Most vulnerabilities can be exploited through specially created Office files and lead to remote code execution with current user rights.
Update MS13-073 (Important) fixes three vulnerabilities in Microsoft Excel 2003-2007-2010-2013 and Microsoft Office for Mac 2011. Vulnerabilities can be exploited through specially created Office files and lead to remote code execution with current user rights. Exploit code unlikely .
Update MS13-074(Important) fixes three vulnerabilities in Microsoft Office (Microsoft Access 2007-2010-2013). Vulnerabilities can be exploited through specially crafted Access files and lead to remote code execution with current user rights. Exploit code likely .
The MS13-075 (Important) update fixes the Elevation of Privilege vulnerability CVE-2013-3859 in the Chinese version of Windows, Chinese IME (Input Method Editors). An attacker can execute arbitrary code in kernel mode. Exploit code likely .
Update MS13-076 (Important) fixes seven Elevation of Privilege vulnerabilities in the Win32 subsystem driver, win32k.sys for all Windows XP-Vista-Seven-8-RT x32 and x64 operating systems.Exploit code likely / Exploit code would be difficult to build .
The MS13-077 (Important) update addresses the Elevation of Privilege type vulnerability in Services Control Manager (SCM) services.exe for Windows 7 SP1 and Windows Server 2008 SP1 x32 and x64. Exploit code would be difficult to build .
The MS13-078 (Important) update fixes the CVE-2013-3137 vulnerability of the type Information Disclosure in Microsoft FrontPage 2003 Service Pack 3. Exploit code unlikely .
The MS13-079 (Important) update addresses the Denial of Service vulnerability CVE-2013-3868 in Active Directory for Windows Vista, Server 2008, Seven, Server 2008 R2, Windows 8, and Windows Server 2012 ...Exploit code unlikely .
1 - Exploit code likely The
probability of exploiting the vulnerability is very high, attackers can use the exploit, for example, to remotely execute code.
2 - Exploit code would be difficult to build The
likelihood of exploitation is medium, since attackers are unlikely to achieve a sustainable exploitation situation, as well as due to the technical features of the vulnerability and complexity of the exploit development.
3 - Exploit code unlikely The
probability of exploitation is minimal and attackers are unlikely to be able to develop successfully working code and use this vulnerability to conduct an attack.
We recommend that our users install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (this option is enabled by default).

Adobe has announced the release of updates for its products Adobe Flash Player , Adobe Acrobat and Reader , Shockwave Player .
Patches for Flash Player fix four RCE vulnerabilities CVE-2013-3361, CVE-2013-3362, CVE-2013-3363, CVE-2013-5324, which can be used for remote code execution via memory-corruption.
Components and versions to be fixed.
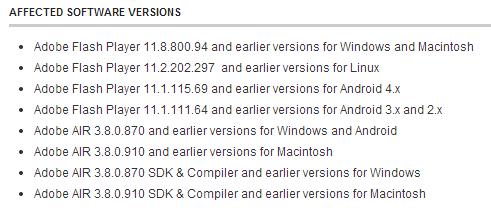
We recommend that users use a check of the version of Flash Player used by your browser, for this you can use the official. Adobe source here or here . Note that browsers such as Google Chrome and Internet Explorer 10 are automatically updated with the release of the new version of Flash Player. You can get Flash update information for your browser at this link .
Current versions of Flash Player for browsers:

Updates for Adobe Acrobat, Reader fix eight RCE vulnerabilities.

be secure.

In September, details of exploiting the RCE vulnerability in win32k.sys, which was closed by MS13-053 and can be used to bypass the sandbox mode restrictions in the Google Chrome browser, became known in Google (Google Chrome full sandbox bypass w / win32k, WebKit / Blink flaws via CVE-2013- 0912, CVE-2013-1300). A successful demonstration of the exploit bundle for conducting a drive-by attack in the latest [at that time] version of Chrome was demonstrated at Pwn2Own 2013, as we wrote about earlier . In the pastIn a month, Microsoft closed the vulnerabilities in the latest version of Internet Explorer and the ASLR mechanism, which were used to successfully conduct a drive-by attack in the framework of Pwn2Own 2013.

In addition to Internet Explorer, OS components of different versions, Outlook mail client and MS SharePoint were updated. This month's patch tuesday differs from others in a large number of Remote Code Execution (RCE) fixes in Microsoft Office, SharePoint, Windows, and IE. Only 8 updates fix these vulnerabilities through which an attacker can successfully run remote code on a system with vulnerable software.

In the case of the vulnerability in win32k.sys CVE-2013-1300 ( MS13-053 ), which could be used to execute arbitrary code, we are talking about using an undocumented functionwin32k! NtUserMessageCall .
W32KAPI LRESULT NtUserMessageCall (IN HWND hwnd, IN UINT msg, IN WPARAM wParam, IN LPARAM lParam, IN ULONG_PTR xParam, IN DWORD xpfnProc, IN BOOL bAnsi);
This function is used to forward messages between threads during GUI interaction within the Win32 (Windows) subsystem. For some types of messages, it allocates a memory buffer, which will then be filled with the called party, that is, the thread that is waiting for the message. The following is a stack of function calls when a caller sends a message.
00,000,008 ffb80530 00000000 nt ExpReleasePoolQuota + 0x21!
Fd6b7168 00000000 ffb80530 nt ExFreePoolWithTag + 0x779!
Ffb80530 00000000 2ba8aa2a win32k UnlinkSendListSms + 0x70!
00243c78 0000000d 00,000,008 win32k xxxInterSendMsgEx + 0xd0a!
Fe243c78 0000000d 00,000,008 win32k xxxSendMessageTimeout + 0x13b!
Fe243c78 0000000d 00,000,008 win32k xxxSendMessageEx + 0xec! <- function through which the allocation of exploited memory is initiated through Win32AllocPoolWithQuota
fe243c78 0000000d 00000008 win32k! NtUserfnOUTSTRING + 0xa7
0001037c 0000000d 00000008 win32k! NtUserMessageCall + 0xc9 <- function called throughSnttcdt01cdt01dttcdt01000Shttdtdt000
Keystdtdttdt000 Keystdtdtdt000 Keystone
The following is a stack of function calls when a message is received by the receiving party, and the buffer allocated by xxxSendMessageEx -> ...-> Win32AllocPoolWithQuota is filled .
a9de17d0 825c4759 a9de1850 a9dd9a84 00,000,008 win32k CopyOutputString! <- directly copy operation
a9de1aa4 82625d85 fe2389a0 0000000d 00,000,008 win32k SfnOUTSTRING + 0x336!
a9de1aec 825f5ad1 0a2389a0 0000000d 00,000,008 win32k xxxSendMessageToClient + 0x175!
a9de1b68 82,638,034 fd96c5a0 2bad6b5a 0171fed8 win32k xxxReceiveMessage + 0x3b8!
a9de1bb8 8263b7e6 a9de1be8 000025ff 00000000 win32k! xxxRealInternalGetMessage + 0x252
a9de1c1c 82a4e89a 0171fed8 00000000 00000000 win32k! NtUserGetMessage + 0x3f <- shadow SDT function
a9de1c1c 77677094 0171fed8 00000000 00000000 nt! KiFastCallEntryfbf7700770000 7700
KiNI691000000 00001 KiFastCallEntrybbf771 7700 KiNIfntrbfbf771 770070 KiFastCallEntrybfbb 7700fntlbfbll 0x1200
0171ff40 7769374e 013d1340 00000000 00000000 ntdll! __ RtlUserThreadStart + 0x70
0171ff58 00000000 013d1340 00000000 00000000 ntdll! _RtlUserThreadStart + 0x1b
xxxInterSendMsgEx is an important function because it is responsible for directly delivering a message from one thread to another. An error in the code is present when the last argument of the NtUserMessageCall bAnsi is incorrectly interpreted by a function that allocates memory and a function that fills it. The function that allocates memory treats this argument as a boolean type. In this case, the value 0 for it is false and means the use of WCHAR characters. A nonzero value is considered by the function as an indication of the use of ASCII characters and the allocation of a memory block of the appropriate size. However, a function that performs a character copy operation believes that this argument is a bitmask and is used to distinguish between ASCII and WCHAR. Thus, when this argument is equal to an even number and not equal to zero, both functions will interpret this value differently. For example, with a value of 2, the highlight function will assume that a buffer of the appropriate size should be allocated to store the string of ASCII characters. When it comes to copying, the CopyOutputString functionwill consider the string as a WCHAR and copy twice as much memory as needed, thus causing a buffer overflow. Using the opportunity to exploit this vulnerability and CVE-2013-0912, an attacker could execute arbitrary code from a browser, thus bypassing the limitations of the sandbox mode.
Update MS13-067 (Critical) addresses ten vulnerabilities in Microsoft Office Server software (Office Web Apps / Server Software). Vulnerabilities CVE-2013-3847, CVE-2013-3848, CVE-2013-3849, CVE-2013-3857, and CVE-2013-3858 are present in Word (part of Office Web Apps 2010 and SharePoint Server 2010) and, through them, an attacker could execute remote code through a specially formed file.
Update MS13-068(Critical) addresses the RCE vulnerability CVE-2013-3870 in the Outlook 2007-2010 mail client. The attacker can execute arbitrary code through a specially crafted message for the vulnerable version of the client. Exploit code would be difficult to build .
The MS13-070 (Critical) update addresses the CVE-2013-3863 vulnerability in the OLE engine of Windows XP SP3 [x64 SP2] and Windows Server 2003 SP2. An attacker can execute arbitrary code with the rights of the current user through a specially formed OLE object. Exploit code likely .
Update MS13-071(Important) addresses the vulnerability CVE-2013-0810 in Windows XP SP3, Server 2003 SP2 and Windows Vista SP2, Server 2008 SP2. The attacker can execute the remote code in the system through a specially formed theme file. Such a file must be delivered to the user, for example, using a phishing message. Thus, the user himself must initiate the opening of the file, otherwise the attack cannot be successful. Exploit code likely .
Update MS13-072(Important) fixes 13 vulnerabilities in Microsoft Office 2003 (Microsoft Word 2003 and Microsoft Word Viewer), Office 2007 (Word 2007 and Office Compatibility Pack), and Microsoft Word 2010 - memory corruption. Most vulnerabilities can be exploited through specially created Office files and lead to remote code execution with current user rights.
Update MS13-073 (Important) fixes three vulnerabilities in Microsoft Excel 2003-2007-2010-2013 and Microsoft Office for Mac 2011. Vulnerabilities can be exploited through specially created Office files and lead to remote code execution with current user rights. Exploit code unlikely .
Update MS13-074(Important) fixes three vulnerabilities in Microsoft Office (Microsoft Access 2007-2010-2013). Vulnerabilities can be exploited through specially crafted Access files and lead to remote code execution with current user rights. Exploit code likely .
The MS13-075 (Important) update fixes the Elevation of Privilege vulnerability CVE-2013-3859 in the Chinese version of Windows, Chinese IME (Input Method Editors). An attacker can execute arbitrary code in kernel mode. Exploit code likely .
Update MS13-076 (Important) fixes seven Elevation of Privilege vulnerabilities in the Win32 subsystem driver, win32k.sys for all Windows XP-Vista-Seven-8-RT x32 and x64 operating systems.Exploit code likely / Exploit code would be difficult to build .
The MS13-077 (Important) update addresses the Elevation of Privilege type vulnerability in Services Control Manager (SCM) services.exe for Windows 7 SP1 and Windows Server 2008 SP1 x32 and x64. Exploit code would be difficult to build .
The MS13-078 (Important) update fixes the CVE-2013-3137 vulnerability of the type Information Disclosure in Microsoft FrontPage 2003 Service Pack 3. Exploit code unlikely .
The MS13-079 (Important) update addresses the Denial of Service vulnerability CVE-2013-3868 in Active Directory for Windows Vista, Server 2008, Seven, Server 2008 R2, Windows 8, and Windows Server 2012 ...Exploit code unlikely .
1 - Exploit code likely The
probability of exploiting the vulnerability is very high, attackers can use the exploit, for example, to remotely execute code.
2 - Exploit code would be difficult to build The
likelihood of exploitation is medium, since attackers are unlikely to achieve a sustainable exploitation situation, as well as due to the technical features of the vulnerability and complexity of the exploit development.
3 - Exploit code unlikely The
probability of exploitation is minimal and attackers are unlikely to be able to develop successfully working code and use this vulnerability to conduct an attack.
We recommend that our users install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (this option is enabled by default).

Adobe has announced the release of updates for its products Adobe Flash Player , Adobe Acrobat and Reader , Shockwave Player .
Patches for Flash Player fix four RCE vulnerabilities CVE-2013-3361, CVE-2013-3362, CVE-2013-3363, CVE-2013-5324, which can be used for remote code execution via memory-corruption.
Components and versions to be fixed.

We recommend that users use a check of the version of Flash Player used by your browser, for this you can use the official. Adobe source here or here . Note that browsers such as Google Chrome and Internet Explorer 10 are automatically updated with the release of the new version of Flash Player. You can get Flash update information for your browser at this link .
Current versions of Flash Player for browsers:

Updates for Adobe Acrobat, Reader fix eight RCE vulnerabilities.
- RCE via stack overflow: CVE-2013-3351
- RCE via memory corruption: CVE-2013-3352, CVE-2013-3354, CVE-2013-3355
- RCE via buffer overflow: CVE-2013-3353, CVE-2013-3356
- RCE via integer overflow: CVE-2013-3357, CVE-2013-3358.

be secure.
