The idea of how to provide employees with temporary access to client resources without shining passwords
A little background
After the lecture at HighLoad ++ 2017. I watched this report, “How we fired the admin”, in the recording. The speaker said that all web companies are having problems with passwords, and I had an idea how to solve this. Most likely, someone has already done it, but, honestly, I don’t know, I just want to describe it, then maybe someone will do it or I will do it myself somehow. I hope if someone decides to do something like this it will be opensource.
Actually description of the problem and how to solve it.
What is the problem, if not strange in the passwords themselves, more precisely so that unscrupulous employees do not take them away from the company.
There are two options for solving this problem.
- Post all changes to the site personally to the head of the company.
- Something to think and do.
In general, we act according to the second option. The first is difficult and expensive if the company consists of a small number of people.
What you have decided to do, now you need to decide how to do it.
Here's the simplest idea right away, why not make a proxy? Well, most likely a super proxy. The scheme of work in principle is simple and I drew it below.

Figure 1 - the general scheme of the system.
As can be seen from the diagram and the idea itself, the main element here will be a proxy server.
His tasks are as follows:
- Accordingly, to receive traffic, or even work at the level of SSH and SFTP commands, to begin with, and send a response from the client’s server to a specialist.
- Authentication and authorization specialist
- Check the legitimacy of the teams, this can be done later.
The structure of the proxy server itself will be as follows:
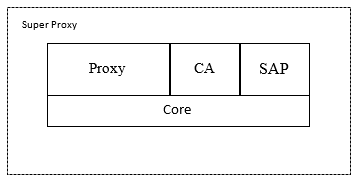
Figure 2 - Block diagram of the super-proxy component of the proxy
- directly
proxies traffic using the SSH protocol, (S) FTP, HTTP, HTTPS CA (Control Access) - Controls the access of specialists to client resources. SAP (Sever Admin Panel) - Directly the server with which the administrator is associated, through the control panel. Core - Directly the core of the system deals with the management of requests between modules and model management.
I think that it is worthwhile to dwell on the access separately, since this was the reason for this.
All users are included in group policies, group policies determine the rules for access to client servers, as well as rules that system administrators are subject to. Group policies have a hierarchical structure, each top level has its own same powers as the bottom level. From the beginning there is a policy '.', It includes all permissions for everything, and it can include one user the main administrator. Then there are two groups for policies, system administrators and projects.
Summary table - administrators and their rights
| Role name | Access rights | |
|---|---|---|
| Group Policy Administrator | Editing users in group policy | |
| Group Policy Administrator | Create Group Policy | Create delete and edit users in Group Policy |
| User Management Administrator | Remove user from group policy | Create delete and edit users |
| Backup manager | Reading information about users and administrators | Reading Group Policy Records |
| Chief Administrator | Everything and everyone else, as well as editing and deleting group policies | Forced change of passwords on client servers |
Group policies themselves contain an entry about the server to which this policy applies.
And users have the following rules, which are prescribed for each user or group separately, in fact, these are Boolean values, which determines whether the object has HTTP / HTTPS access to the resource control panel (admin panel), SFTP / FTP, SSH access.
Now there are a couple of words about the control panel and the client.
The control panel, or everything is clear, but you need to write again, that would be exactly clear.
Control Panel. It is directly needed to manage group policies and the server as a whole, a super proxy. Distributed as a separate application or web service.
Accordingly, administrators have access to the control panel.
The client is simple in appearance, complex inside.
The client needs an application, in the case of HTTP (S), purely theoretically, this application can be a browser directly configured to work through a proxy server, and our proxy server will have to wedge traffic. In general, rather, everything, you will need to develop a separate application that will work over SSH, (S) FTP, HTTP (S), with client servers, through our super-proxy server, or even it will be easier, it will actually install and communicate with the client servers are themselves a super-proxy server, and in the client itself, installed on a computer by specialists, the whole process will be simply emulated.
Consider the example of HTTP (S).
- The client sends a request to the proxy server to contact the client.
- The super proxy server allows it or not, if it does, the super proxy server itself raises the connection and is authorized in the control panel.
- Super-proxy server receives directly the main page of the admin panel.
- The super-proxy server sends this page to the client, replacing the address of the client resource with a special marker.
- The specialist follows the links or fills in the fields in the browser and submits the form. The data goes to the super proxy server.
- The super-proxy server replaces the tokens back to the address of the client resource and accordingly sends it directly to the client resource itself.
With SSH, you can transfer pure text. And directly from the super-proxy server to the client's resource, a normal SSH connection rises.
That's about something like that. Waiting for your feedback in the comments, and links to repositories, if someone decides to make such a system.
