Short and clear: Flex VPN
The purpose of this article is a little deeper than a superficial acquaintance of the reader with a relatively new method of building VPN connections - flex vpn and the key negotiation protocol IKEv2 as its basis. Here I will try to consider the advantages of IKEv2 and flex vpn and give examples of site-to-site VPN configuration.
I myself am not a major specialist in this topic, so I apologize if something is not completely illuminated.
A very short introduction.
I nternet P rotocol Sec urity is a set of protocols consisting of:
o Authentication Headers (AH) - source authentication and packet integrity control
o Encapsulating Security Payloads (ESP)- Actually, data encryption
o Security Associations (SA) - protocols that provide AH and ESP with the necessary information (a kind of support).
IKEv2, as well as IKEv1, ISAKMP, and a couple of other, less well-known, are just part of the SA protocol group. IKEv2's mission is to provide authenticated key agreement within the ISAKMP framework. The IETF was published in the already quite distant 2005 (IKEv1 - 1998), a full description with all the additions made available in RFC 5996 (September 2010).
IKEv2 Benefits
Simplified Messaging
To start secure communications, you need only 4 (in the simplest case):
The initiator IKE_SA_INIT contains the cryptographic algorithm proposed by the initiator, the initiator key exchange materials (according to Diffie-Hellman), and the initiator nonce timestamp.
The responder's IKE_SA_INIT contains the cryptographic algorithm selected by the responder, the defendant’s key exchange materials, the responder’s time stamp, and, optionally, a certificate request.
IKE_AUTH of the initiator / responder - identifiers, certificates and other necessary information are already transmitted in encrypted form and with integrity protection.
Increased Reliability
All operations now require confirmation from the other side of the VPN connection. Thus, DeadPeerDetection is implemented.
Improved protection against DDoS attacks
An advantage that many experts call the key in modern realities.
Due to the fact that all operations now require confirmation from the other side of the VPN connection, you cannot create a large number of half-open sessions on the attacked device.
The so-called anti-clogging cookies.
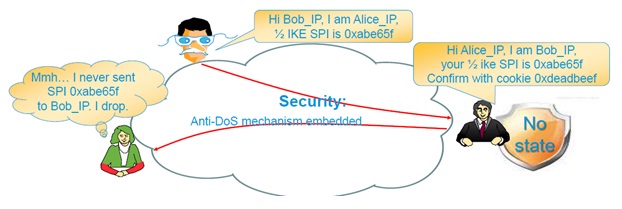
(image from Cisco Expo 2012)
These same cookies increase the efficiency of using the computing resources of VPN agents.
And, finally, Smart Defaults are a bun that minimizes the number of config lines by using the default parameters, which, moreover, can be customized.
In addition to all of the above, to date, a number of IKEv2 extensions have appeared, including Mobility and Multihoming Protocol (MOBIKE), Redirect Mechanism, Quick Crash Detection Method, and some others.
Now directly about flex vpn
Again, the picture from Cisco Expo 2012 - flex vpn features:

Having pondered the garden out of various VPN solutions, reasonable humanity came to its senses, put together everything useful and, armed with IKEv2 in time, blinded a single, monolithic figure, combed and washed without junk and dirt. This is the essence and relevance of flex vpn. By solidity, I mean a single set of CLI commands.
But here comes the drawback: absolute incompatibility with IKEv1.
Since nothing gives a fundamentally new flex vpn, there is no need to rush to remake already implemented solutions. In addition, the implementation is still damp: not all iOS with declared ikev2 support will correctly execute all options for flex vpn interactions.
However, Cisco strongly recommends that you use flex vpn in all new installations.
The list of hardware supporting flex vpn:
- ISR of the second generation (19xx, 29xx, 39xx) with sec-k9 or hsec-k9 license;
- 7200;
- ASR 1000.
Officially, flex vpn is supported since iOS 15.2 (2) T.
The following is an example of the simplest configuration config - site-to-site vpn using smart defaults.
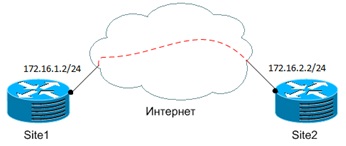
Site1:
crypto ikev2 keyring ikev2-kr
peer Site2
address 172.16.2.2
pre-shared-key local cisco123
pre-shared-key remote 123cisco
crypto ikev2 profile default
match identity remote address 172.16.2.2 255.255.255.255
authentication local pre-share
authentication remote pre-share
keyring local ikev2-kr
interface Tunnel0
ip address 10.10.0.1 255.255.255.252
tunnel source Ethernet0 / 1
tunnel destination 172.16.2.2
tunnel protection ipsec profile default
ip route 192.168.2.0 255.255.255.0 Tunnel0 The
Site2 configuration is symmetric.
As we can see, encryption, transform-set, acl, Diffie-Hellman group were set by default - the dream of an IT specialist who is not familiar and does not want to get acquainted with cryptography. Equipment negotiates by itself.
At the same time, if at one end of the connection the settings are set to smart default, and at the other end with the hands of a hardworking administrator, this does not mean that the crypto session cannot be established.
That is the point.
Smart Defaults is a whole set of possible parameters that devices bypass before finally agreeing.
Preset values:
Encryption: AES-CBC 256, 192, 128, 3DES
Hash: SHA-512,384,256, SHA-1, MD5
Diffy-Hellman group: group 5, 2
crypto ikev2 policy: match any
Transform-set: AES-128, 3DES / SHA, MD5
crypto ipsec profile default: default transform set, ikev2 profile default
It remains only to register an IKEv2 profile with the name default.
The interacting parties agree on a tree traversal algorithm. Those. a device with default values will first try to apply AES-CBC 256 + SHA-512 + group 5, then AES-CBC 256 + SHA-512 + group 2, then AES-CBC 256 + SHA-384 + group 5 ... and so on, until will not pick up the set corresponding to the neighbor.
Simple and convenient, right?
The Cisco website has the document “FlexVPN and Internet Key Exchange Version 2 Configuration Guide, Cisco IOS
Release 15.2M & T” with configs for all occasions.
I myself am not a major specialist in this topic, so I apologize if something is not completely illuminated.
A very short introduction.
I nternet P rotocol Sec urity is a set of protocols consisting of:
o Authentication Headers (AH) - source authentication and packet integrity control
o Encapsulating Security Payloads (ESP)- Actually, data encryption
o Security Associations (SA) - protocols that provide AH and ESP with the necessary information (a kind of support).
IKEv2, as well as IKEv1, ISAKMP, and a couple of other, less well-known, are just part of the SA protocol group. IKEv2's mission is to provide authenticated key agreement within the ISAKMP framework. The IETF was published in the already quite distant 2005 (IKEv1 - 1998), a full description with all the additions made available in RFC 5996 (September 2010).
IKEv2 Benefits
Simplified Messaging
To start secure communications, you need only 4 (in the simplest case):
The initiator IKE_SA_INIT contains the cryptographic algorithm proposed by the initiator, the initiator key exchange materials (according to Diffie-Hellman), and the initiator nonce timestamp.
The responder's IKE_SA_INIT contains the cryptographic algorithm selected by the responder, the defendant’s key exchange materials, the responder’s time stamp, and, optionally, a certificate request.
IKE_AUTH of the initiator / responder - identifiers, certificates and other necessary information are already transmitted in encrypted form and with integrity protection.
Increased Reliability
All operations now require confirmation from the other side of the VPN connection. Thus, DeadPeerDetection is implemented.
Improved protection against DDoS attacks
An advantage that many experts call the key in modern realities.
Due to the fact that all operations now require confirmation from the other side of the VPN connection, you cannot create a large number of half-open sessions on the attacked device.
The so-called anti-clogging cookies.

(image from Cisco Expo 2012)
These same cookies increase the efficiency of using the computing resources of VPN agents.
And, finally, Smart Defaults are a bun that minimizes the number of config lines by using the default parameters, which, moreover, can be customized.
In addition to all of the above, to date, a number of IKEv2 extensions have appeared, including Mobility and Multihoming Protocol (MOBIKE), Redirect Mechanism, Quick Crash Detection Method, and some others.
Now directly about flex vpn
FlexVPN is on old friend with new clothes. It still allows you to do all the cool things but in a better way.
Again, the picture from Cisco Expo 2012 - flex vpn features:

Having pondered the garden out of various VPN solutions, reasonable humanity came to its senses, put together everything useful and, armed with IKEv2 in time, blinded a single, monolithic figure, combed and washed without junk and dirt. This is the essence and relevance of flex vpn. By solidity, I mean a single set of CLI commands.
But here comes the drawback: absolute incompatibility with IKEv1.
Since nothing gives a fundamentally new flex vpn, there is no need to rush to remake already implemented solutions. In addition, the implementation is still damp: not all iOS with declared ikev2 support will correctly execute all options for flex vpn interactions.
However, Cisco strongly recommends that you use flex vpn in all new installations.
The list of hardware supporting flex vpn:
- ISR of the second generation (19xx, 29xx, 39xx) with sec-k9 or hsec-k9 license;
- 7200;
- ASR 1000.
Officially, flex vpn is supported since iOS 15.2 (2) T.
The following is an example of the simplest configuration config - site-to-site vpn using smart defaults.

Site1:
crypto ikev2 keyring ikev2-kr
peer Site2
address 172.16.2.2
pre-shared-key local cisco123
pre-shared-key remote 123cisco
crypto ikev2 profile default
match identity remote address 172.16.2.2 255.255.255.255
authentication local pre-share
authentication remote pre-share
keyring local ikev2-kr
interface Tunnel0
ip address 10.10.0.1 255.255.255.252
tunnel source Ethernet0 / 1
tunnel destination 172.16.2.2
tunnel protection ipsec profile default
ip route 192.168.2.0 255.255.255.0 Tunnel0 The
Site2 configuration is symmetric.
As we can see, encryption, transform-set, acl, Diffie-Hellman group were set by default - the dream of an IT specialist who is not familiar and does not want to get acquainted with cryptography. Equipment negotiates by itself.
At the same time, if at one end of the connection the settings are set to smart default, and at the other end with the hands of a hardworking administrator, this does not mean that the crypto session cannot be established.
That is the point.
Smart Defaults is a whole set of possible parameters that devices bypass before finally agreeing.
Preset values:
Encryption: AES-CBC 256, 192, 128, 3DES
Hash: SHA-512,384,256, SHA-1, MD5
Diffy-Hellman group: group 5, 2
crypto ikev2 policy: match any
Transform-set: AES-128, 3DES / SHA, MD5
crypto ipsec profile default: default transform set, ikev2 profile default
It remains only to register an IKEv2 profile with the name default.
The interacting parties agree on a tree traversal algorithm. Those. a device with default values will first try to apply AES-CBC 256 + SHA-512 + group 5, then AES-CBC 256 + SHA-512 + group 2, then AES-CBC 256 + SHA-384 + group 5 ... and so on, until will not pick up the set corresponding to the neighbor.
Simple and convenient, right?
The Cisco website has the document “FlexVPN and Internet Key Exchange Version 2 Configuration Guide, Cisco IOS
Release 15.2M & T” with configs for all occasions.
