Validation of SSL certificates for revocation
Nowadays, one of the most important aspects of secure information transmission is encryption. Transmission data from client to server is encrypted using an SSL certificate. A certificate is a public key certified by a certification authority.
All SSL certificates are usually issued for a limited period, after which they expire and must be reissued. However, there are times when a certificate can be revoked before it expires. There are quite a few reasons for revoking an SSL certificate, the most common of them is that the private key has been lost or compromised, the company registration data has changed, etc.
There are 2 alternative ways to check if the SSL certificate is in revocation lists:
Consider both of these methods in more detail using the Ubuntu console. And as an example, let's check the revocation certificate for the domain habr.com.
Download the certificate of the domain of interest to us:
Thanks legioner for the hint to add the -servername parameter - it is necessary for the correct selection of the certificate, if there are several of them (SNI) on one IP address.
We look at the details of the certificate:
Here we are interested in the “Full Name” item in the “X509v3 CRL Distribution Points” section.
Download this link CLR list:
We tear out the serial number of the certificate:
See if this number is in the CRL list:
If nothing is found, then the certificate is not revoked.
We will display the certificate of the domain of interest to us and the chain of intermediate (Intermediate) certificates:
Save the domain certificate and intermediate certificate into files (code between the lines ----- BEGIN CERTIFICATE ----- and ----- END CERTIFICATE -----):
Define the OCSP server:
Send a request to the OCSP server to check the certificate for revocation:
If everything is correct, the OCSP server should return the certificate information.
Here the last lines are of interest:
The absence of a certificate in the list of revoked is indicated by the value “good”; if the certificate is revoked, the value will be “revoked”.
It is not always convenient to check SSL certificates for manual revocation, so the verification process can be automated.
To do this, use Github to create a ready-made ssl-check-revoc.sh script that checks certificates using the CRL method:
Next, make the script executable:
Now you can check both already installed certificates for the domain and those stored locally in files (option -f):
The ssl-check-revoc.sh script can check certificates not only from the console, it is also quite suitable as a checker for Zabbix, so all the dirty work of tracking certificates into the revocation list can be assigned to the monitoring system.
Go to the Zabbix config /etc/zabbix/zabbix_server.conf and see where the scripts for external checks are:
Copy our script into this directory and restart Zabbix:
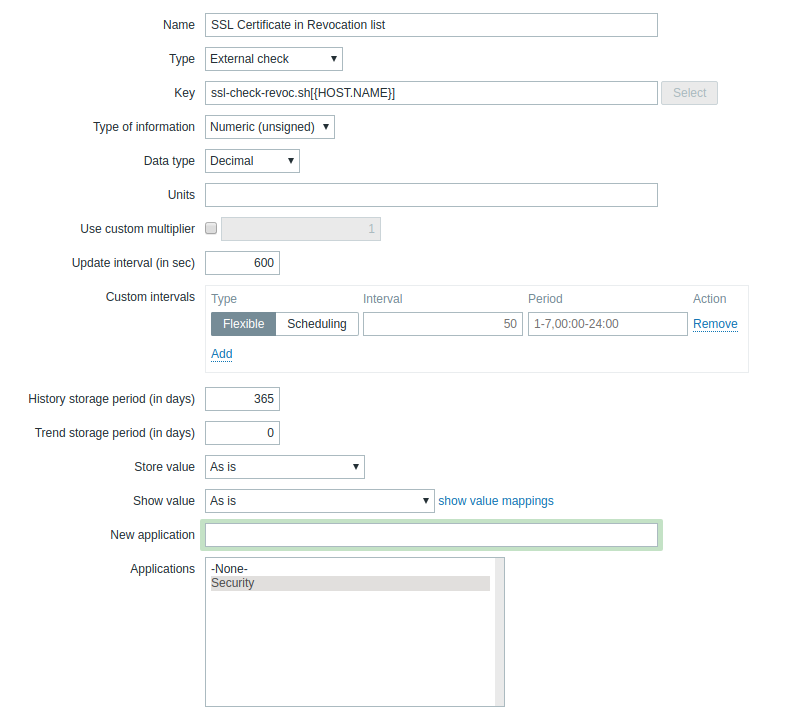
Go to the web interface and create a template (Configuration >> Templates >> Create template). We specify “Template SSL Checking” as the template name. Then inside the template we create the data item (Item) “SSL Certificate in Revocation List”, with “ssl-check-revoc.sh [{HOST.NAME}]” as the key, with the “External check” check type. The inspection interval can be set at your discretion depending on the criticality of the project.
You will also need two triggers:
1. To signal a certificate revocation "Certificate for domain {HOST.NAME} is in revocation list"
Expression: "{Template Custom SSL Checking: ssl-check-revoc.sh [{HOST.NAME}]. Last ()} = 1 "

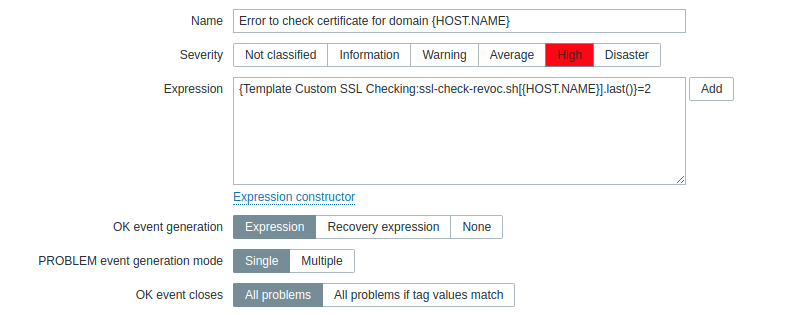
2. To signal an error in case something goes wrong (for example, there are problems with the CLR server, etc.) "Error to check certificate for domain {HOST.NAME}"
Expression: "{Template Custom SSL Checking: ssl-check-revoc.sh [{HOST.NAME}]. Last ()} = 2 "
Do not forget in the actions (Configuration >> Actions) to configure the notification method in case of triggering.
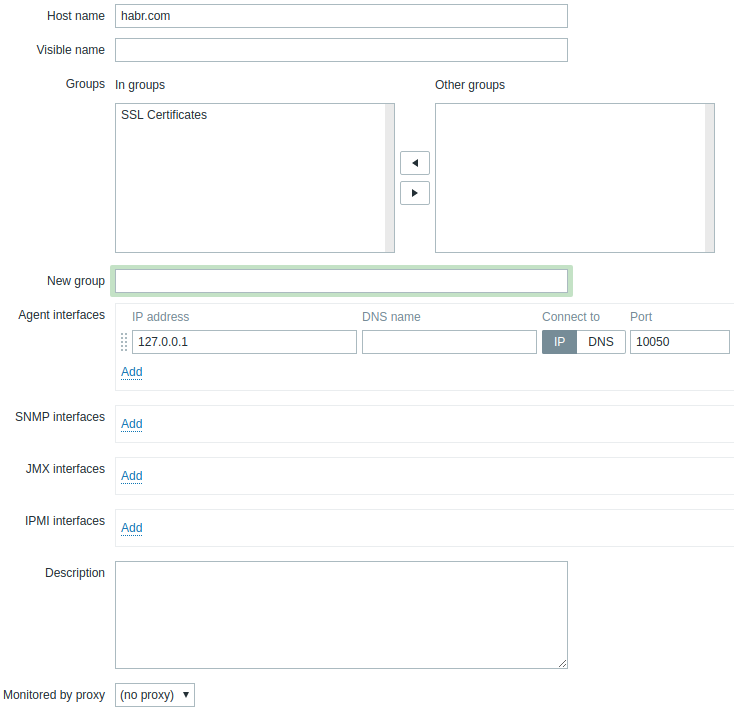
Now it remains to create hosts, whose certificates we will regularly check (Configuration >> Hosts >> Create host). On the Templates tab, we link our Template SSL Checking template.
And that's it! You can sleep peacefully: if the SSL certificate of your domain for any reason falls into the revoked list, Zabbix will immediately inform you.
All SSL certificates are usually issued for a limited period, after which they expire and must be reissued. However, there are times when a certificate can be revoked before it expires. There are quite a few reasons for revoking an SSL certificate, the most common of them is that the private key has been lost or compromised, the company registration data has changed, etc.
There are 2 alternative ways to check if the SSL certificate is in revocation lists:
- CRL (Certificate Revocation List) - checks for the serial number of the certificate in the revocation list.
- OCSP (Online Certificate Status Protocol) - a certificate is sent to a specialized server, where its status is checked.
Consider both of these methods in more detail using the Ubuntu console. And as an example, let's check the revocation certificate for the domain habr.com.
CRL
Download the certificate of the domain of interest to us:
echo -n | openssl s_client -connect habr.com:443 -servername habr.com 2>&1 | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > /tmp/habr.com.crtThanks legioner for the hint to add the -servername parameter - it is necessary for the correct selection of the certificate, if there are several of them (SNI) on one IP address.
We look at the details of the certificate:
openssl x509 -noout -text -in /tmp/habr.com.crtHere we are interested in the “Full Name” item in the “X509v3 CRL Distribution Points” section.
Download this link CLR list:
wget http://crl.comodoca.com/COMODORSADomainValidationSecureServerCA.crlWe tear out the serial number of the certificate:
openssl x509 -in /tmp/habr.com.crt -noout -serialSee if this number is in the CRL list:
openssl crl -inform DER -text -in COMODORSADomainValidationSecureServerCA.crl | grep "90E58B0601C3AD98F07AEE092041C437"If nothing is found, then the certificate is not revoked.
OCSP
We will display the certificate of the domain of interest to us and the chain of intermediate (Intermediate) certificates:
echo -n | openssl s_client -connect habr.com:443 -showcertsSave the domain certificate and intermediate certificate into files (code between the lines ----- BEGIN CERTIFICATE ----- and ----- END CERTIFICATE -----):
/tmp/habr.com.crt
/tmp/intermediate.crtDefine the OCSP server:
openssl x509 -in /tmp/habr.com.crt -noout -ocsp_uriSend a request to the OCSP server to check the certificate for revocation:
openssl ocsp -url http://ocsp.comodoca.com -issuer /tmp/intermediate.crt -cert /tmp/habr.com.crt -textIf everything is correct, the OCSP server should return the certificate information.
Here the last lines are of interest:
Response verify OK
/tmp/habr.com.crt: goodThe absence of a certificate in the list of revoked is indicated by the value “good”; if the certificate is revoked, the value will be “revoked”.
Automation
It is not always convenient to check SSL certificates for manual revocation, so the verification process can be automated.
To do this, use Github to create a ready-made ssl-check-revoc.sh script that checks certificates using the CRL method:
wget https://raw.githubusercontent.com/o-pod/security/master/ssl-check-revoc.shNext, make the script executable:
chmod a+x ssl-check-revoc.shNow you can check both already installed certificates for the domain and those stored locally in files (option -f):
./ssl-check-revoc.sh habr.com -vZabbix
The ssl-check-revoc.sh script can check certificates not only from the console, it is also quite suitable as a checker for Zabbix, so all the dirty work of tracking certificates into the revocation list can be assigned to the monitoring system.
Go to the Zabbix config /etc/zabbix/zabbix_server.conf and see where the scripts for external checks are:
ExternalScripts=/etc/zabbix/externalscriptsCopy our script into this directory and restart Zabbix:
sudo cp ssl-check-revoc.sh /etc/zabbix/externalscripts/
sudo systemctl restart zabbix-serverGo to the web interface and create a template (Configuration >> Templates >> Create template). We specify “Template SSL Checking” as the template name. Then inside the template we create the data item (Item) “SSL Certificate in Revocation List”, with “ssl-check-revoc.sh [{HOST.NAME}]” as the key, with the “External check” check type. The inspection interval can be set at your discretion depending on the criticality of the project.

You will also need two triggers:
1. To signal a certificate revocation "Certificate for domain {HOST.NAME} is in revocation list"
Expression: "{Template Custom SSL Checking: ssl-check-revoc.sh [{HOST.NAME}]. Last ()} = 1 "

2. To signal an error in case something goes wrong (for example, there are problems with the CLR server, etc.) "Error to check certificate for domain {HOST.NAME}"
Expression: "{Template Custom SSL Checking: ssl-check-revoc.sh [{HOST.NAME}]. Last ()} = 2 "

Do not forget in the actions (Configuration >> Actions) to configure the notification method in case of triggering.
Now it remains to create hosts, whose certificates we will regularly check (Configuration >> Hosts >> Create host). On the Templates tab, we link our Template SSL Checking template.

And that's it! You can sleep peacefully: if the SSL certificate of your domain for any reason falls into the revoked list, Zabbix will immediately inform you.
