Yota Egg: Vulnerability or feature?
Did you know that in Yota Egg there is a hidden (“not mentioned in the manual”, “unknown to 99% of users” - who like it more) administrative interface that allows you to fine-tune this device and view detailed statistics?
Did you know that access to it is closed by the same username / password admin / admin pair for all devices?
My classmate and friend Mofas, out of purely altruistic motives, shares the Internet of his Yota Egg for everyone around him (for example, in the university cafeteria, for his classmates).
The other day, when the Internet speed slipped to unacceptable tens of kbit / s, I decided to see if this was due to the number of people connected to the point or if the signal level dropped again.
Ping the broadcast address of the Eggs subnet showed only two clients and one ip, which was clearly not the address of the router and did not enter the client pool of addresses:

By going to http://192.168.1.254 and entering the default admin / admin, I got access to all the settings of the router without the knowledge of its owner, because he only knew about the control panel described in the user manualhttp://192.168.1.1 , the password for which he changed, following the instructions of the same manual, immediately after purchase.
As it turned out (in principle, this was not a big secret) Yota Egg is a device of the Korean company Interbro KWI B2200, which I got to the administrative part of.
Apparently, the original kwi b2200 interface seemed Yota to the guys not too friendly for the average user (which is hard to argue with), so they created their own admin panel
(and why show the supplier logo again?), Described its interface and settings in the manual, but they forgot to change the password to the “real” control panel.
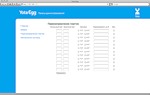
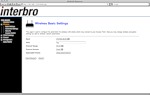
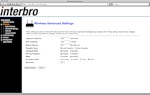
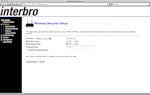
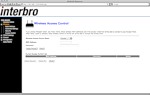
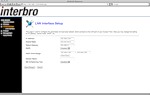
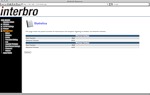
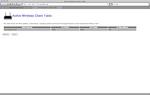
Below are a few screenshots (thanks, Mofas ) of the control panel from Yota and from Interbro:






In no case do not want the negativity towards Yota, but still I want to warn users of this wonderful device from vulnerability.
You just need to go to the address 192.168.1.254 with your web browser, enter the username / password admin / admin and change the password to a new one in the Management → Password section.
Did you know that access to it is closed by the same username / password admin / admin pair for all devices?
As it turned out
My classmate and friend Mofas, out of purely altruistic motives, shares the Internet of his Yota Egg for everyone around him (for example, in the university cafeteria, for his classmates).
The other day, when the Internet speed slipped to unacceptable tens of kbit / s, I decided to see if this was due to the number of people connected to the point or if the signal level dropped again.
Ping the broadcast address of the Eggs subnet showed only two clients and one ip, which was clearly not the address of the router and did not enter the client pool of addresses:

By going to http://192.168.1.254 and entering the default admin / admin, I got access to all the settings of the router without the knowledge of its owner, because he only knew about the control panel described in the user manualhttp://192.168.1.1 , the password for which he changed, following the instructions of the same manual, immediately after purchase.
How did it happen?
As it turned out (in principle, this was not a big secret) Yota Egg is a device of the Korean company Interbro KWI B2200, which I got to the administrative part of.
Apparently, the original kwi b2200 interface seemed Yota to the guys not too friendly for the average user (which is hard to argue with), so they created their own admin panel
(and why show the supplier logo again?), Described its interface and settings in the manual, but they forgot to change the password to the “real” control panel.
Below are a few screenshots (thanks, Mofas ) of the control panel from Yota and from Interbro:














In no case do not want the negativity towards Yota, but still I want to warn users of this wonderful device from vulnerability.
You just need to go to the address 192.168.1.254 with your web browser, enter the username / password admin / admin and change the password to a new one in the Management → Password section.
