Watch Dogs in real life, or serious vulnerabilities in ACS
It seems to me that many guys, especially at a young age, wanted to be cool hackers. Hack sites, phones, access systems. So I have a little bit of this boyish enthusiasm. Therefore, periodically poking around in various software and did not find anything worthwhile. But one day, luck turned up for me, and even what! ACS, full of vulnerabilities that allow access to control the entire system (opening / closing doors, adding your access card, etc.).
Interesting? Then welcome to kat!
Everything described below was carried out on a test bench. The article was written solely for educational purposes and in general this is all an invention of the author.
SKUD - access control and management system
It so happened that at one time I worked at a construction and road enterprise, where I wrote a set of programs for issuing passes, issuing food for these passes and reporting. I needed to integrate all this with one fairly popular ACS. The developers responded to documentation requests for a long time, and the deadlines burned. I had to understand their software myself.
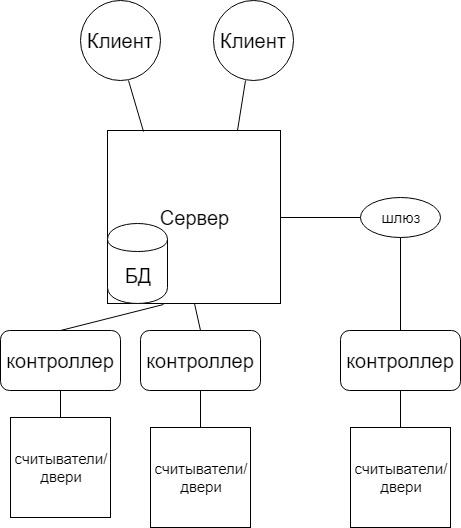
Approximate ACS operation scheme
I started learning from the database. The ACS server works with the firebird 2.5 database. The login and password for it turned out to be standard, which is already very alarming, but the password can be set in the program settings. Passwords in the database to the accounts are hashed, but without salt, which is bad, but again uncritical. It stores all the passage zones, users, their card numbers, accesses and controller addresses.
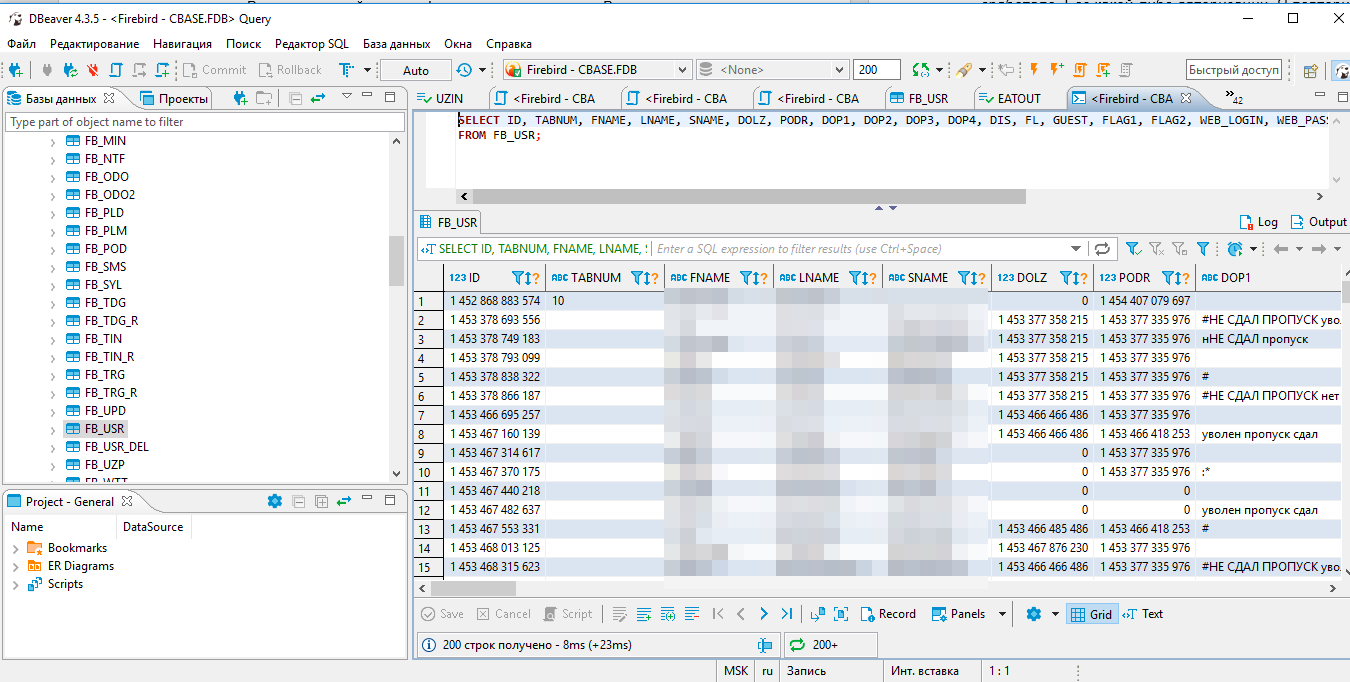
Db
Next, we take some program for traffic sniffing (I took “SmatrSniff”, the first one that can view localhost traffic) and see what the client sends to the server. All data goes over TCP and some over UDP in unencrypted form. And here the fun begins. The server first sends the clear password from the database, its location, and only then checks the username and password!
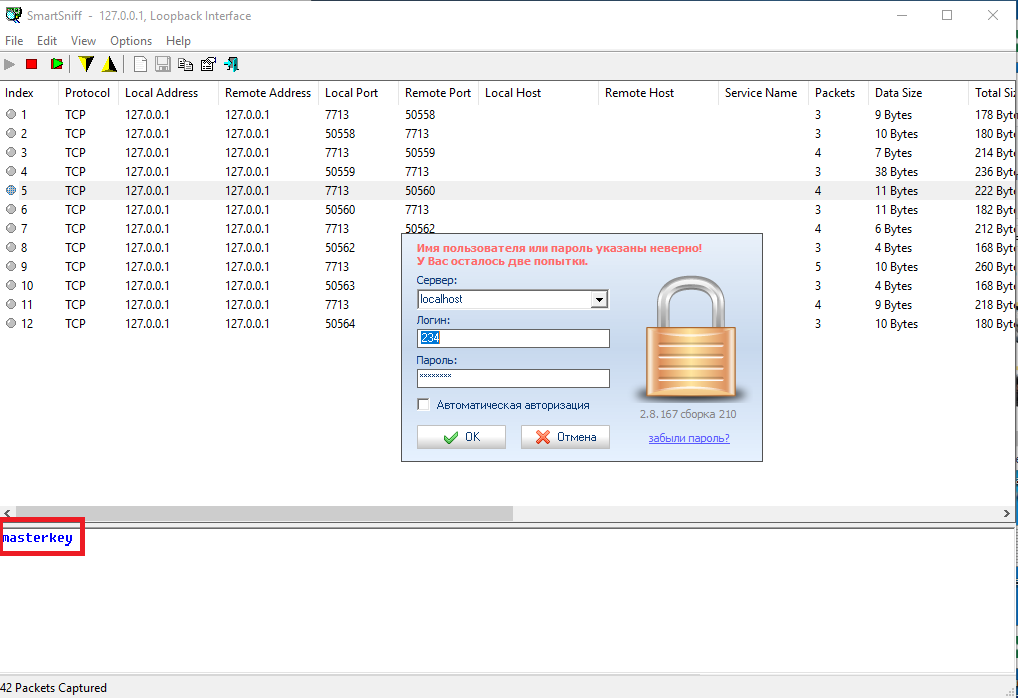
Password from the masterkey database
It turns out that, without knowing the username and password, we can get full access to the database, which gives us almost limitless possibilities. We can give ourselves a card with access to any object. Prescribe your card to another user and go under his name. But for this data to be uploaded to the controllers, you need to give a command to the server from the client. Although we can take the password for the client from the database, use the open MD5 databases and try to find the password for the hash (I’ll remind you that the passwords in the database are salt-free), but if the password is complicated, then most likely nothing will work. We'll have to wait for someone to click on the full upload button.
Then I looked, and does authorization affect anything at all. To do this, I tried to repeat requests to the server using “TCP / IP Builder”. And yes, subsequent requests to the server do not work without authorization (sends a refusal in response). Here I am a little depressed, because for integration I will have to implement a repetition of the entire authorization chain and only then send a package to load data into the controller.
Finally, I decided to repeat the request to transfer the door to open mode. The server answered “ok” and the door was beeping. Without any authorization. I repeated the same from another computer on the local network and it worked too.
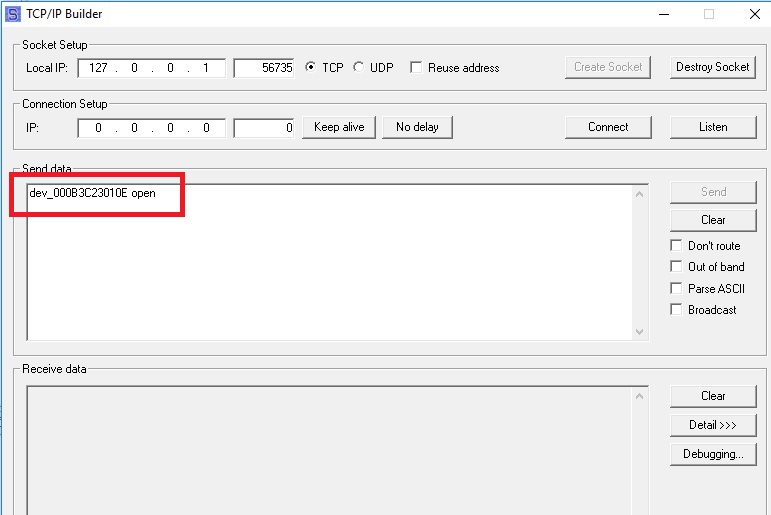
Approximate type of package
This means that we can open / close any door from any computer on the local network. Prescribe a card for yourself and immediately download this data to the controllers. Then calmly go through the objects and delete all the logs of our visit.
I killed a couple of hours to learn the protocol of communication between the controller and the server in order to finally break it, but I could not fully understand the data format. But I am sure that there is no protection. The packages definitely have the mac addresses of the controller and server / gateway (binding to the server goes to the mac address, there are no encryption keys and the like in the database, so you can most likely pretend to be the server for the controller knowing the mac server). Unfortunately, there are no dumps or access to the equipment, so I can’t show it.
As a result, we have full access control vulnerabilities, which give us unlimited access to passages to objects. Due to the low cost of components and free software, this ACS is very common. She stands in many schools in Moscow, and I saw her at other sites. The company prides itself on prizes at various events. I do not specifically name the organization, nor did I write to them about it. Because I believe that such vulnerabilities at the architecture level cannot be fixed without rewriting all the software from scratch and updating all the equipment of people who bought this system (there are several more serious holes at the architecture level, but describing them would triple the article). For those who have learned from the ACS screen and it is installed in you, I advise you to completely isolate the network (which is considered to be “best practices”), in which all the components of the system are located, and access to the database for adding employees is done only through a VPN. Proper routing configuration can also help.
