Quadrocopter taught to find vulnerable networks and gadgets at high altitude
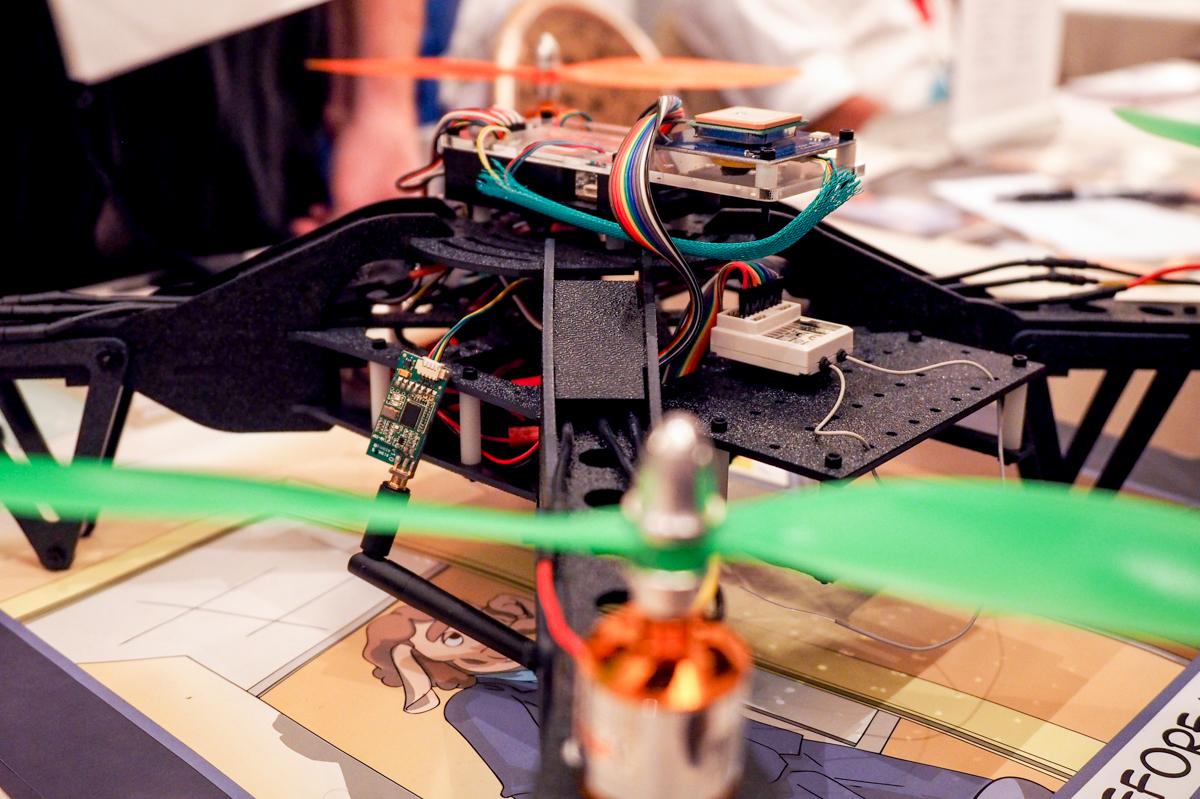
The usual job of an information security specialist is to find ways to compromise the network of your own company in order to know what you need to deal with. Professionals use a large number of methods for their work. One of them is launching a quadrocopter with the corresponding hardware and software “stuffing”. So, the Aerial Assault quadrocopter is equipped with a Raspberry Pi system with Kali Linux . This is a distribution used to conduct a variety of tests of networks and devices for security.
Such a drone, being raised into the air, is engaged in the search for devices and networks that can be hacked. All this information is transmitted to the operator on Earth. The device is built on the basis of Open Source (both software and hardware), so any other person or group of specialists with relevant experience can restore its design.
The Aerial Assault hardware also includes GPS, so the drone remembers where the device or network was susceptible to hacking. The device can operate at rather high altitudes, rising to offices that are located in skyscrapers, and scanning networks and network gadgets in such buildings. It can be premises with network equipment, where there are practically no people, and in a normal situation it is not easy to get there.
Despite the fact that the drone is intended solely for research, there is a chance that someone can use such a device for another purpose - for example, stealing information from a person or company. If you think that the network located on the 30th floor is physically inaccessible to attackers, then think again. The cost of the copter is about $ 2500, and it will be available in a few days on the Wall of Sheep .
In general, after reading this material, if you are working in the office, look through the window - what if a quadcopter hovering outside the window has already found a vulnerability in the corporate network of your enterprise?
