The basics of information security of a virtual server. Part 4: Standards and Specifications
This is the fourth article in a series of articles on the subject of "information security basics", which is designed to help you understand and ensure the safety of the system and data on your virtual server or any other machine on the production network. Previously Described Questions:
- Part 1: Types of Threats
- Part 2: Information and means of protection
- Price error
- Part 3: Information Security Models
Today, it is almost impossible for security professionals to do without knowledge of relevant standards and specifications. There are several reasons for this. The formal thing is that the need to follow certain standards, such as “cryptographic” standards or “governing documents,” is enshrined in law. However, the most convincing substantive reasons.
Firstly, standards and specifications are one of the forms of accumulating knowledge, first of all, on the procedural and software-technical levels of information security. They record proven, high-quality solutions and methodologies developed by the most qualified specialists.
Secondly, both of them are the main means of ensuring mutual compatibility of hardware-software systems and their components.
Thirdly, the information security standards have a difficult task to reconcile three different points of view, the “manufacturer of protective equipment”, the “consumer” and the various “certification experts”, as well as create an effective mechanism for interaction between all parties.
Consumers are interested in methods that allow them to choose a product that meets their needs and solves their problems, it can be including VPSrunning Wшndows Server, for which they need a security rating scale. And also the consumer needs a tool with which he will be able to formulate his requirements to the manufacturer. Unfortunately, many consumers often don’t understand that security requirements necessarily contradict not only usability but speed, but more often impose certain restrictions on compatibility and, as a rule, force them to abandon widespread, user-friendly, but less secure means .
Certification experts see standards as a tool that allows them to assess the level of security and provide consumers with the opportunity to make the most effective choice for themselves.
One of the first and most well-known documents was the so-called "Orange Book" developed in the 90s as the "Criteria for the security of computer systems" of the US Department of Defense. It defines 4 security levels, A, B, C, D, where A is the highest level of security, in which, accordingly, the most stringent requirements are imposed.
Although the “Orange Book” was one of the first most famous documents, it is clear that each state that wants to ensure its information security has developed its own documentation - “national standards” in the field of information security. These include European Information Technology Security Criteria, Canadian Computer Systems Security Criteria, as well as British Practical Information Security Management Rules, on the basis of which, by the way, the international standards ISO / IEC 17799: 2000 (BS 7799— 1: 2000). At the moment, the latest version of the standard ISO / IEC 27001: 2013, as well as the "Guiding Documents of the USSR State Technical Commission" (and later Russia).
It should be noted that the Americans praised the activities of the "USSR State Technical Commission." American publications wrote that the Soviet body for protecting information and counteracting technical intelligence carefully scrutinizes everything that is known in the West about the Soviet Union and develops "a huge amount of materials in order to distort the real picture." The commission, they reported, controls all military parades and exercises in which foreigners are present, the construction of missile bases and barracks, while in some areas achievements are deliberately hidden, in others such as missile defense, they are greatly exaggerated. The activities of the State Technical Commission in this area really very soon brought their first fruits. As the American New York Times wrote, already in 1977, as a result of measures,
The results of the "State Technical Commission of the USSR" in the Soviet period were not only an increase in the security of information at the enterprises of the military-industrial complex, tests of new types of weapons at landfills. Serious work has been done to ensure the security of information processed in ACS and computers, in particular, secure computer control systems and confidential document processing tools have been created that exclude leakage of classified information, communication channels have been introduced at the level of government bodies and the high command of the Soviet Army, and much more.
It is also impossible not to note that the previously indicated role of standards is fixed in the Federal Law " On Technical Regulation " dated 12.27.2002 N 184-ФЗ
It should be noted that among the principles of standardization proclaimed in the aforementioned law, Article 7 “Content and application of technical regulations” includes the principle of applying the international standard as the basis for developing a national standard, unless such application is deemed impossible due to the non-compliance of the requirements of international standards with climate and geographical features, technical or technological features or for other reasons, or if the Russian Federation It fell against the adoption of an international standard or individual position.
Article 7. Clause 8:
International standards should be used in whole or in part as a basis for the development of draft technical regulations, unless the international standards or their sections would be ineffective or inappropriate to achieve the goals set forth in Article 6 of this Federal Law, including due to climatic and geographical features Russian Federation, technical and (or) technological features. (as amended by Federal Law of 18.07.2009 N 189-ФЗ)
National standards of the Russian Federation can be used in whole or in part as a basis for the development of draft technical regulations.
Since, from a practical point of view, the number of standards and specifications, including international, national and industry ones in the field of information security is infinite, we give only some of them, a complete list of national standards is provided on the FSTEC of Russia website in the corresponding section "National Standards".
| Designation | Name in Russian |
|---|---|
| GOST R 50739-95 | Computer facilities. Protection against unauthorized access to information. General technical requirements |
| GOST R 50922-2006 | Protection of information. Key Terms and Definitions |
| GOST R 51188-98 | Protection of information. Testing software for computer viruses. Sample manual |
| GOST R 51583-2014 | Protection of information. The procedure for creating automated systems in a secure execution. General Provisions |
| GOST R 53110-2008 | System for ensuring information security of a public communication network. General Provisions |
| GOST R 53111-2008 | Stability of the functioning of the public communication network. Requirements and Verification Methods |
| GOST R 53113.1-2008 | Information technology. Protection of information technologies and automated systems from threats to information security implemented using covert channels. Part 1. General Provisions |
| GOST R 53113.2-2009 | Information technology. Protection of information technologies and automated systems from threats to information security implemented using covert channels. Part 2. Recommendations for organizing the protection of information, information technology and automated systems from attacks using covert channels |
| GOST R 54581-2011 / I | Information technology. Security methods and tools. The basics of trust in IT security. Part 1. Overview and basics |
| GOST R 54582-2011 / | Information technology. Security methods and tools. Fundamentals of confidence in the security of information technology. Part 2. Trust methods |
| GOST R 54583-2011 / | Information technology. Security methods and tools. Fundamentals of confidence in the security of information technology. Part 3. Analysis of confidence methods |
| GOST R ISO 7498-1-99 | Information technology. Interconnection of open systems. The basic reference model. Part 1. The basic model |
| GOST R ISO 7498-2-99 | Information technology. Interconnection of open systems. The basic reference model. Part 2. Information Security Architecture |
| GOST R ISO / IEC TO 13335-5-2006 | Information technology. Security methods and tools. Part 5. Network Security Management Guide |
| GOST R ISO / IEC 15408-1-2012 | Information technology. Security methods and tools. Criteria for assessing the security of information technology. Part 1. Introduction and general model |
For example, consider GOST R 53113.2-2009 “Information Technology (IT). Protection of information technologies and automated systems from threats to information security implemented using covert channels. ”
Part 2. Recommendations for organizing the protection of information, information technology and automated systems from attacks using covert channels.
This standard presents not only the general scheme of the functioning of covert channels in an automated system, the rules for creating a threat model, but also various recommendations for protecting information and the methods used in building an information security system that take into account the existence of such covert channels.
Below in Figure 1, a general diagram of the functioning of covert channels in an automated system is presented.
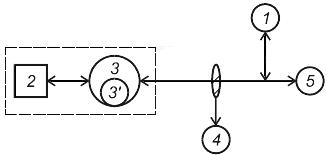
Figure 1 - The general scheme of the mechanism of the functioning of covert channels in an automated system
1 - a security violator (attacker) whose purpose is unauthorized access to restricted information or an unauthorized influence on an automated system;
2 - restricted access information or a critical function;
3 - a subject having authorized access to 2 and 5;
3 '- agent of the security violator, located in a closed loop with 2 and interacting with 2 on behalf of subject 3;
4 - an inspector (software, hardware-software, hardware or person), controlling (her) information interaction 3, crossing a closed circuit, separating the object of information from the external environment;
5 - a subject located outside a closed circuit with which 3 carries out authorized information interaction.
Security threats that can be realized using hidden channels include:
1. Introduction of malware and data;
2. An attacker submits commands to an agent for execution;
3. Leak of cryptographic keys or passwords;
4. Leakage of individual information objects.
Protecting information, information technology and automated systems from attacks using covert channels is a cyclic process that includes the following steps, repeated at each iteration of the process:
1. Risk analysis of the organization’s assets, including the identification of valuable assets and assessment the possible consequences of attacks using covert channels
2. Identification of covert channels and estimate their risk to the organization's assets
3. The implementation of protective measures to counter the hidden channel at
4. The control over the opposition of covert channels.
The cyclicity of the process of protection against information security threats implemented using covert channels is determined by the emergence of new methods for constructing covert channels unknown at the time of previous iterations.
Based on the hazard assessment of hidden channels, taking into account the results of the risk analysis, a conclusion is drawn on the appropriateness or inappropriateness of counteraction to such channels.
Based on the results of identifying hidden channels, an action plan is developed to counter threats implemented using them. These measures may include the implementation of one of the already known (or improvement of existing) methods of countering information security threats implemented using covert channels.
As protective measures, it is advisable to use:
1. Reducing the bandwidth of the information transmission channel;
2. Architectural solutions for building automated systems;
3. Monitoring the effectiveness of the protection of automated systems.
The choice of methods for countering the threats to information security of the VDS server you are renting that are implemented using covert channels and the formation of a plan for their implementation is determined by experts based on the individual characteristics of the protected automated system.
As you can see, even a short list of standards is far from short, not to mention normative acts and recommendations, however, it is necessary to have at least basic knowledge in this area so that you can not only navigate but also put into practice the necessary standards.
