Nemesida Scanner - Web Application Vulnerability Scanner

Nemesida Scanner is designed to identify vulnerabilities in web applications such as SQL injection, XSS, LFI / RFI, XXE, Open-redirect, search for components with known vulnerabilities and critical data in the public domain, identify weaknesses in the configuration of a web application, port scan, etc. Nemesida Scanner is provided as a console version for popular Linux distributions.
Why write your own scanner, if they are already so full? Let's figure it out. Most modern scanners are heavyweight GUI applications (or a web version in the form of a web server, DBMS, etc.) (besides the fact that they are quite expensive). Console (light) versions of scanners undoubtedly exist, but they have both advantages and disadvantages. An example of an excellent console scanner is the highly specialized wpscan. The console version of w3af is rather confused in terms of settings.
Therefore, we decided to implement a simple but multi-functional scanner that does not load the system and has rich (and constantly added) functionality.
Nemesida Scanner contains a large database of modern attack vectors and payloads, is not demanding on hardware. There is also a “lite version” of Nemesida Scanner used by Nemesida WAF to identify vulnerabilities in web applications and create virtual patch rules.
Description
Nemesida Scanner is an excellent assistant in performing works on the analysis of web application security and penetration testing, allowing you to:
- identify various web vulnerabilities, such as: SQL injection, XSS, LFI / RFI, XXE, Open-redirect;
- identify components with known vulnerabilities;
- detect critical data (files, directories, subdomains) in the public domain;
- Define versions and types of installed CMS, as well as their plugins;
- Identify web application configuration flaws
- select passwords;
- scan ports and define services.
Installing a scanner is pretty trivial. The following is an example installation in Debian (there is also a CentOS version) You need to install the dependencies:
# apt-get update && apt-get install apt-transport-https Add repository:
# echo "deb https://nemesida-security.com/ns/debian stretch non-free" > /etc/apt/sources.list.d/NemesidaScanner.listInstall the gpg.key key:
# wget -O - https://nemesida-security.com/ns/gpg.key | apt-key add -And complete the installation:
# apt-get update && apt-get upgrade && apt-get install nscanner-cliAfter installation, specify the license key in the file /opt/nscanner-cli/nscanner-cli.conf (parameter: "license_key ="). License key for the work of "Nemesida Scanner": 9cfc363d886c85f51cb0c9abe6c10cf1.
Example run command:
# nscanner-cli --host http://example.com.ru --auth admin:password --sql --pdf /tmp/report.pdfExamples of using
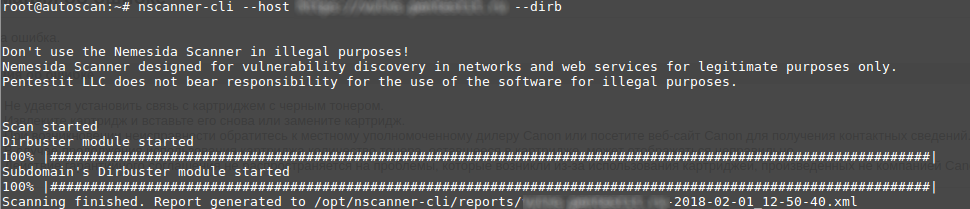
There is no need to use several tools to test penetration of a web application; everything you need is already included in the Nemesida Scanner. For example, at the beginning of testing, you need to scan the ports of the investigated web server:
nscanner-cli --host https://testsite --port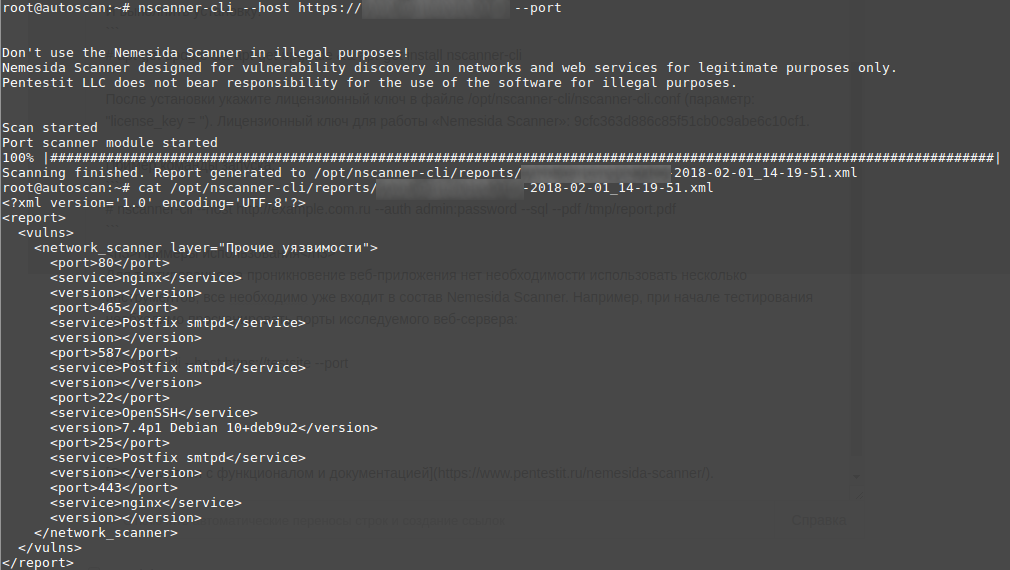
The use of Nemesida Scanner for illegal and unlawful purposes is prohibited.
UPD: supports work in official distributions specified in the repository. Work in other distributions is not guaranteed.
