Not a single VPN. Cheat Sheet on how to protect yourself and your data
Hi, Habr.
This is us, HideMy.name VPN service . Now we are temporarily working on the HideMyna.me mirror. Why? On July 20, 2018, Roskomnadzor added us to the list of prohibited resources due to the decision of the Medvedevsky district court in Yoshkar-Ola. The court ruled that visitors to our site have unlimited access to extremist materials without registration, and somehow found the book “Mein Kampf” by Adolf Hitler on it. Apparently, for reliability.
We were very surprised by this decision, but we continue to work on hidemyna.me, hidemyname.org, .one, .biz, etc. The prolonged wrangling with Roskomnadzor did not lead to any result. While lawyers and I are contesting blocking and magical court decisions, we are sharing with you basic tips on maintaining privacy on the Internet and news on this topic.

Edward Snowden loves the National Security Agency (probably)
It's no secret that popular Russian services are unsafe. Your correspondence at any time may be in the field of view of domestic observers of the law. We tell what you need to remember, communicating through various channels of communication.
There are many different ways to listen to your phone. Official and legal - SORM, a system of technical means to ensure the functions of operational investigative activities. By law, all mobile operators in the Russian Federation are obliged to install such a system on their PBXs if they do not want to lose their license. There are three types of SORM: the first one was invented in the 80s, the second one was introduced into zero, and the third one they have been trying to impose on operators since 2014. According to RBC , most operators use the second type, but in 70% of cases the system does not work correctly or does not work at all. However, on a landline phone and through a normal call from a mobile, sensitive topics are still better not to be discussed.
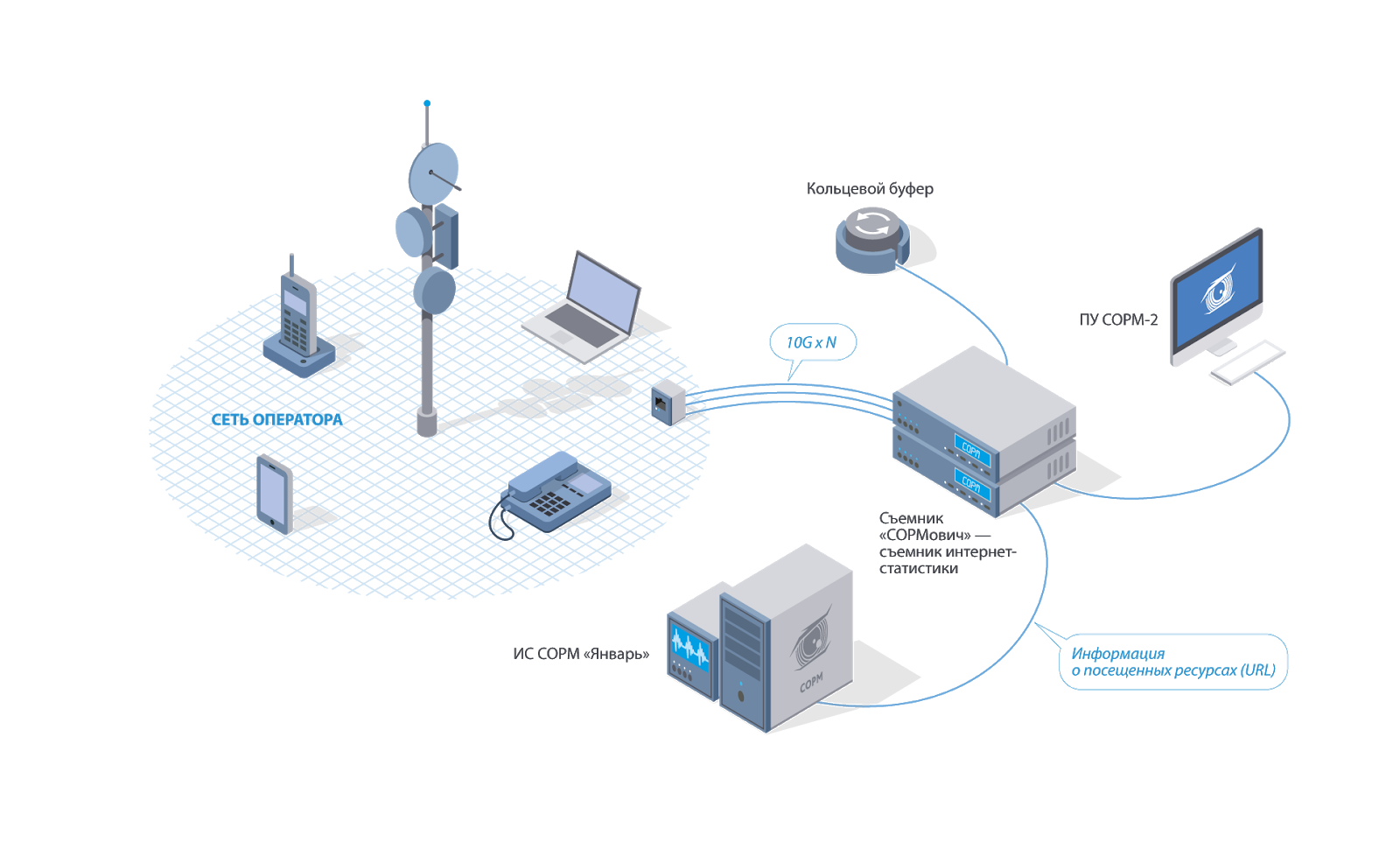
Scheme of work SORM-2 (Source: mfisoft.ru)
According to 97-FZ, any messengers, services and sites that operate in Russia must be entered in the register of the Information Dissemination Organizers . According to the “ Spring Law ”, they are obliged to keep all user data, including voice call recordings and correspondence, for six months. In ORI, by the way, there is also Habrahabr.
The registry is described detail here.on the example of Threema, but the main conclusion is this: now, at the request of the Russian authorities, any information about you may be in law enforcement. Therefore, the first thing that needs to be done to maintain confidentiality is to transfer calls and messages to instant messengers, which are not in the registry of RIS. Or to those that are there, but they refuse to transfer data to the authorities - like Threema and Telegram.
Help : By itself, being in the registry of the ART does not guarantee that the data will be transferred to the authorities. It is necessary to constantly monitor the news and look at the reaction of the messenger when they “come” after it.
Our conversations and messages from the intervention of a third party can protect end-to-end encryption, so E2E messengers are considered the most secure. But this is not quite so: consider the popular options.
Telegram supports end-to-end encryption in its Secret Chats and stores encrypted data about your correspondence in the cloud, which is scattered across different countries with “safe” jurisdiction. But after the article on Habré about the illusion of security of Telegram Passport in Е2Е from Durov, one can begin to doubt.
Of course, communication in Secret Chats is still a good option for paranoids. The server is not involved at all in their encryption: messages are transmitted by peer-to-peer, that is, directly between the participants of the correspondence. To heighten the peace of mind, you can use the self-destruct function of messages on a timer. But do not blindly rely on Telegram. To make it a little more secure, you and your addressee should go into the settings of the messenger and do at least two things:
After that, in addition to the code from the SMS, when you log in from a new device, the application will ask for a password that only you know.
Now confirmation of entry only via SMS does not protect the person who uses the Russian SIM card. Cases of hacking of Telegram accounts through an intercepted SMS message are already known - in 2016, attackers got access to the correspondence of several opposition members, and in 2017, the account of the journalist Dozhd Mikhail Rubin was hacked .

WhatsApp so far avoids the registry of ARI and also uses end-to-end encryption, but with it everything is not so cloudless. Recently, we published news about the residents of Magadan, which brought a criminal case for criticizing the mayor of the city. This story, fortunately, ended in the usual fine. But she confirmed the fears of users: it is not safe to communicate in WhatsApp group chats.
What will happen?
What to do?
If you use a Russian card registered in your name, avoid caustic comments in groups with a name like "Mayor - resignation": for WhatsApp, it is better to leave only personal correspondence and calls.
Viber is also not listed in the registry of the ORI, but it maintains communication with the Russian authorities (in its non-spamming time). This messenger was one of the first to fulfill the new government requirements: it stores the logins and telephone numbers of Russian users in the Russian Federation, but refuses to provide these messages - it refers to the mechanics of end-to-end encryption and corporate policy.
Applealso uses end-to-end, but when registering with iMessage, it creates two pairs of keys: private and public. The message you receive from the same owner of the apple device is sent to you with encryption, which uses the public key. It can only be decrypted using the recipient’s private key, which is stored on its device. How Apple relates to user privacy and what it will do if it receives a request from the government can be read here. There are no cases of the transfer of Russian users' data to the authorities of the Russian Federation.

Source: https://www.apple.com/business/docs/iOS_Security_Guide.pdf
But iMessage has two drawbacks:
To avoid turning iMessage into SMS, you can disable this feature in the settings.
Researchers at the Electronic Frontier Foundation claim that one hundred percent secure option for calls and messages does not exist. If some messengers do not allow the authorities to get your private data, this does not mean that hackers (or the state that can use their services) cannot do this bypassing the laws. To give the user confidence that there is no man-in-the-middle, Telegram has a nice feature: when making a call, both recipients can make sure that they see the same emoji in the upper right corner of the screen - this will be a confirmation of the absence “ intrusion into the compound.
If you need a more reliable way of communication, we recommend not only using secret chats, passwords and two-step / two-factor authentication, but also look at less popular niche applications like Confide or Signal .
I use Signal every day. # note to FBR (Spoiler: they already know)
Email
Popular companies, which make it possible to use their email clients (in Russia, Yandex, Mail.Ru and Rambler), are already included in the registry of the CID, and therefore are not too safe. Yes, Mail.Ru Group calls to stop criminal cases for memes and amnesty convicts, but can give information about your data to the authorities on demand.
Even if you use Western email clients like Gmail or Outlook, enabled two-factor authentication and know that your email is encrypted using the secure SSL / TLS protocol, you cannot be sure that your recipient's email is also secure.
Protection options:
In the case of domestic companies from the ARI registry, no encryption on the user’s side will in principle help. The information is not intercepted, but is stored and transmitted by the end points - like services. The solution can only be replacing them with safer analogues like ProtonMail, Tutanota or Hushmail. More such mail services can be found on this page.
To begin, minimize your stay in the popular Russian social networks - “My World”, “Odnoklassniki” and “VKontakte”. Facebook does not even transfer your data to the Russian special services. At least, such cases are not recorded.

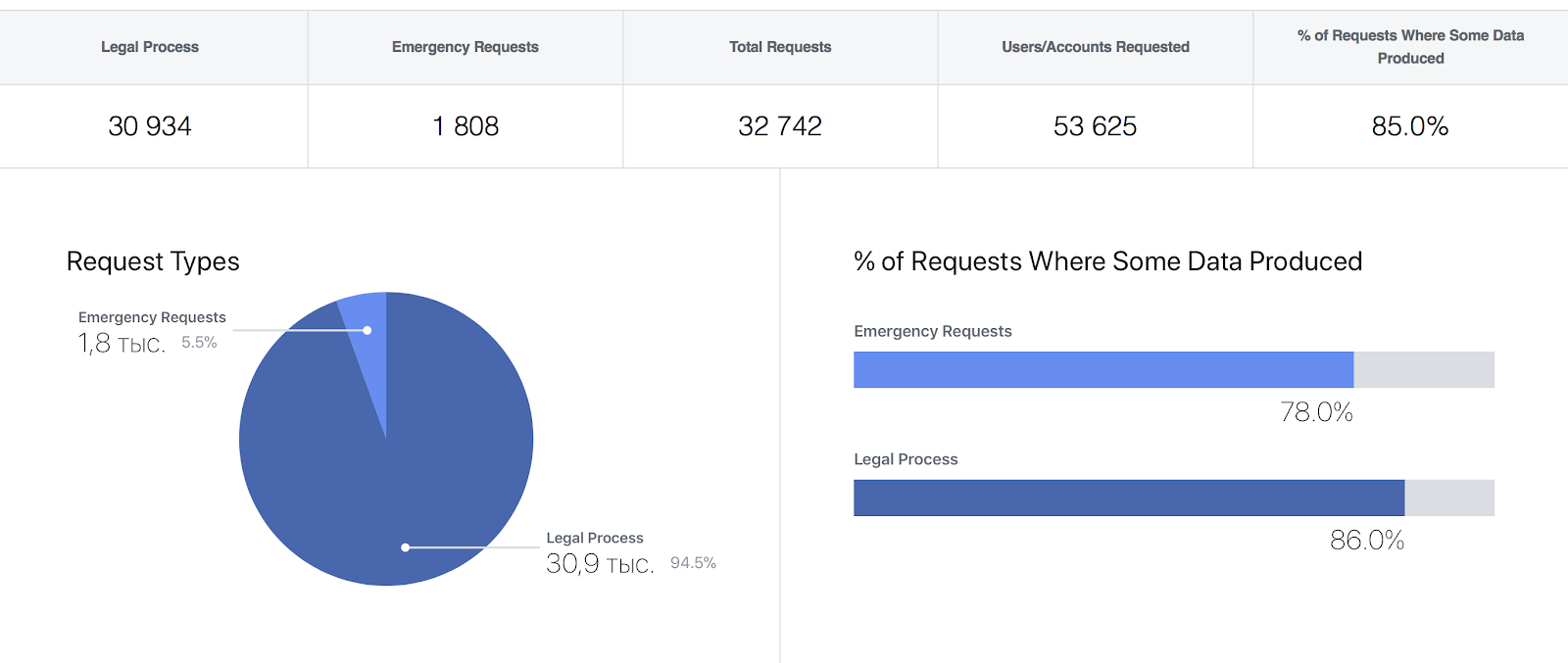
But it is interesting that in 2017, the company still satisfied 85% of requests from the US government: Screenshots from the Facebook Transparency Report If you are too accustomed to VC, but do not want to be in the dock, pay attention to a few things:
In all of the above, it is better to avoid that which can be considered insulting or extremist. Always remember that “distribution” is the communication of “illegal” information to at least one person. A lawyer of the international human rights group Agora, Damir Gainutdinov, claims that according to the law, the CID is obliged to keep and transmit to law enforcement agencies even drafts of unsent messages . More about how not to sit at the repost, read here.
By the way, for some time, anyone who has your phone number can by default find you on VKontakte, even if the page itself does not betray your real identity.
It is possible to prohibit finding you by number in the profile settings (Settings -> Privacy -> Contact me). But this, of course, will not save from the special services. Do not use calls and video calls on VKontakte: it is not known whether the network really encrypts their end-to-end, as the administration claims.
The only good news is that more than half of all popular sites on the Internet already have an https version or have completely switched to using only https versions. The information received and transmitted on such sites is encrypted and cannot be read by third parties. Such resources are marked in green and the word "protected."
This is where the good news ends. Despite the https protocol, the fact of visiting such a site and DNS queries (information about which domains you applied to) still remain visible to the ISP.
But even worse is the other news: the remaining half of the sites work using the usual http-protocol, that is, without data encryption. The solution can be a VPN, which encrypts absolutely all the data received and transmitted so that there is no readable information on the side of the Internet provider and anyone who tries to penetrate between you and the target site. The only thing that will be seen is the fact of connecting to a certain IP address on the Internet (that is, to a VPN server). And nothing more.
We will be happy if life really suddenly becomes so simple: turned on the VPN and forgot about the leakage of sensitive information. But it is not. Regularly check whether your favorite resource is not in the RIS registry, watch how it interacts with authorities, check active connections in the settings of instant messengers and social networks and reset suspicious (and then change passwords).
When working with communication channels and data transfer, only an integrated approach to security and privacy makes sense. Follow the Internet security events in our telegram channel @hidemyname_ru , on the website of Roskomsvoboda and on other resources devoted to events on the Internet and internet, in particular.
What security measures are you taking?
This is us, HideMy.name VPN service . Now we are temporarily working on the HideMyna.me mirror. Why? On July 20, 2018, Roskomnadzor added us to the list of prohibited resources due to the decision of the Medvedevsky district court in Yoshkar-Ola. The court ruled that visitors to our site have unlimited access to extremist materials without registration, and somehow found the book “Mein Kampf” by Adolf Hitler on it. Apparently, for reliability.
We were very surprised by this decision, but we continue to work on hidemyna.me, hidemyname.org, .one, .biz, etc. The prolonged wrangling with Roskomnadzor did not lead to any result. While lawyers and I are contesting blocking and magical court decisions, we are sharing with you basic tips on maintaining privacy on the Internet and news on this topic.

Edward Snowden loves the National Security Agency (probably)
It's no secret that popular Russian services are unsafe. Your correspondence at any time may be in the field of view of domestic observers of the law. We tell what you need to remember, communicating through various channels of communication.
SORM and ORI
There are many different ways to listen to your phone. Official and legal - SORM, a system of technical means to ensure the functions of operational investigative activities. By law, all mobile operators in the Russian Federation are obliged to install such a system on their PBXs if they do not want to lose their license. There are three types of SORM: the first one was invented in the 80s, the second one was introduced into zero, and the third one they have been trying to impose on operators since 2014. According to RBC , most operators use the second type, but in 70% of cases the system does not work correctly or does not work at all. However, on a landline phone and through a normal call from a mobile, sensitive topics are still better not to be discussed.

Scheme of work SORM-2 (Source: mfisoft.ru)
According to 97-FZ, any messengers, services and sites that operate in Russia must be entered in the register of the Information Dissemination Organizers . According to the “ Spring Law ”, they are obliged to keep all user data, including voice call recordings and correspondence, for six months. In ORI, by the way, there is also Habrahabr.
The registry is described detail here.on the example of Threema, but the main conclusion is this: now, at the request of the Russian authorities, any information about you may be in law enforcement. Therefore, the first thing that needs to be done to maintain confidentiality is to transfer calls and messages to instant messengers, which are not in the registry of RIS. Or to those that are there, but they refuse to transfer data to the authorities - like Threema and Telegram.
Help : By itself, being in the registry of the ART does not guarantee that the data will be transferred to the authorities. It is necessary to constantly monitor the news and look at the reaction of the messenger when they “come” after it.
Voice calls and messages
Our conversations and messages from the intervention of a third party can protect end-to-end encryption, so E2E messengers are considered the most secure. But this is not quite so: consider the popular options.
Telegram supports end-to-end encryption in its Secret Chats and stores encrypted data about your correspondence in the cloud, which is scattered across different countries with “safe” jurisdiction. But after the article on Habré about the illusion of security of Telegram Passport in Е2Е from Durov, one can begin to doubt.
Of course, communication in Secret Chats is still a good option for paranoids. The server is not involved at all in their encryption: messages are transmitted by peer-to-peer, that is, directly between the participants of the correspondence. To heighten the peace of mind, you can use the self-destruct function of messages on a timer. But do not blindly rely on Telegram. To make it a little more secure, you and your addressee should go into the settings of the messenger and do at least two things:
- Put the password at the entrance to the application ( Privacy and Security -> Passcode );
- Enable two-step authentication ( Privacy and Security -> Two-Step Verification ).
After that, in addition to the code from the SMS, when you log in from a new device, the application will ask for a password that only you know.
Now confirmation of entry only via SMS does not protect the person who uses the Russian SIM card. Cases of hacking of Telegram accounts through an intercepted SMS message are already known - in 2016, attackers got access to the correspondence of several opposition members, and in 2017, the account of the journalist Dozhd Mikhail Rubin was hacked .

WhatsApp so far avoids the registry of ARI and also uses end-to-end encryption, but with it everything is not so cloudless. Recently, we published news about the residents of Magadan, which brought a criminal case for criticizing the mayor of the city. This story, fortunately, ended in the usual fine. But she confirmed the fears of users: it is not safe to communicate in WhatsApp group chats.
What will happen?
- As soon as you write a message, your phone number will immediately become available to all group members. And by number your identity is easy to calculate.
What to do?
- The solution can be a “left” SIM card or a foreign number — preferably a European one.
If you use a Russian card registered in your name, avoid caustic comments in groups with a name like "Mayor - resignation": for WhatsApp, it is better to leave only personal correspondence and calls.
Viber is also not listed in the registry of the ORI, but it maintains communication with the Russian authorities (in its non-spamming time). This messenger was one of the first to fulfill the new government requirements: it stores the logins and telephone numbers of Russian users in the Russian Federation, but refuses to provide these messages - it refers to the mechanics of end-to-end encryption and corporate policy.
Applealso uses end-to-end, but when registering with iMessage, it creates two pairs of keys: private and public. The message you receive from the same owner of the apple device is sent to you with encryption, which uses the public key. It can only be decrypted using the recipient’s private key, which is stored on its device. How Apple relates to user privacy and what it will do if it receives a request from the government can be read here. There are no cases of the transfer of Russian users' data to the authorities of the Russian Federation.

Source: https://www.apple.com/business/docs/iOS_Security_Guide.pdf
But iMessage has two drawbacks:
- You can write or call through these channels only to the same owner of Apple;
- If you have problems with the Internet connection, the message will go through a regular cellular channel and will become a simple SMS message that can be easily intercepted.
To avoid turning iMessage into SMS, you can disable this feature in the settings.

Researchers at the Electronic Frontier Foundation claim that one hundred percent secure option for calls and messages does not exist. If some messengers do not allow the authorities to get your private data, this does not mean that hackers (or the state that can use their services) cannot do this bypassing the laws. To give the user confidence that there is no man-in-the-middle, Telegram has a nice feature: when making a call, both recipients can make sure that they see the same emoji in the upper right corner of the screen - this will be a confirmation of the absence “ intrusion into the compound.

If you need a more reliable way of communication, we recommend not only using secret chats, passwords and two-step / two-factor authentication, but also look at less popular niche applications like Confide or Signal .

I use Signal every day. # note to FBR (Spoiler: they already know)
Popular companies, which make it possible to use their email clients (in Russia, Yandex, Mail.Ru and Rambler), are already included in the registry of the CID, and therefore are not too safe. Yes, Mail.Ru Group calls to stop criminal cases for memes and amnesty convicts, but can give information about your data to the authorities on demand.
Even if you use Western email clients like Gmail or Outlook, enabled two-factor authentication and know that your email is encrypted using the secure SSL / TLS protocol, you cannot be sure that your recipient's email is also secure.
Protection options:
- When sending sensitive information, encrypt messages using Pretty Good Privacy ( PGP ). This program helps to transform data from a letter into a meaningless set of characters for everyone except the sender and receiver;
- When sending important information, always pay attention to the addressee’s domain and do not write to a suspicious address;
- Check with the addressee in advance if he is not configured to forward or collect mail through the Russian postal service.
In the case of domestic companies from the ARI registry, no encryption on the user’s side will in principle help. The information is not intercepted, but is stored and transmitted by the end points - like services. The solution can only be replacing them with safer analogues like ProtonMail, Tutanota or Hushmail. More such mail services can be found on this page.
Social networks
To begin, minimize your stay in the popular Russian social networks - “My World”, “Odnoklassniki” and “VKontakte”. Facebook does not even transfer your data to the Russian special services. At least, such cases are not recorded.

But it is interesting that in 2017, the company still satisfied 85% of requests from the US government: Screenshots from the Facebook Transparency Report If you are too accustomed to VC, but do not want to be in the dock, pay attention to a few things:

- your saved pictures;
- posts, comments and posts that you write;
- posts that like;
- posts you share;
- friends with whom you are friends.
In all of the above, it is better to avoid that which can be considered insulting or extremist. Always remember that “distribution” is the communication of “illegal” information to at least one person. A lawyer of the international human rights group Agora, Damir Gainutdinov, claims that according to the law, the CID is obliged to keep and transmit to law enforcement agencies even drafts of unsent messages . More about how not to sit at the repost, read here.
By the way, for some time, anyone who has your phone number can by default find you on VKontakte, even if the page itself does not betray your real identity.
It is possible to prohibit finding you by number in the profile settings (Settings -> Privacy -> Contact me). But this, of course, will not save from the special services. Do not use calls and video calls on VKontakte: it is not known whether the network really encrypts their end-to-end, as the administration claims.
Security sites
The only good news is that more than half of all popular sites on the Internet already have an https version or have completely switched to using only https versions. The information received and transmitted on such sites is encrypted and cannot be read by third parties. Such resources are marked in green and the word "protected."
This is where the good news ends. Despite the https protocol, the fact of visiting such a site and DNS queries (information about which domains you applied to) still remain visible to the ISP.
But even worse is the other news: the remaining half of the sites work using the usual http-protocol, that is, without data encryption. The solution can be a VPN, which encrypts absolutely all the data received and transmitted so that there is no readable information on the side of the Internet provider and anyone who tries to penetrate between you and the target site. The only thing that will be seen is the fact of connecting to a certain IP address on the Internet (that is, to a VPN server). And nothing more.
We will be happy if life really suddenly becomes so simple: turned on the VPN and forgot about the leakage of sensitive information. But it is not. Regularly check whether your favorite resource is not in the RIS registry, watch how it interacts with authorities, check active connections in the settings of instant messengers and social networks and reset suspicious (and then change passwords).
Globally
When working with communication channels and data transfer, only an integrated approach to security and privacy makes sense. Follow the Internet security events in our telegram channel @hidemyname_ru , on the website of Roskomsvoboda and on other resources devoted to events on the Internet and internet, in particular.
What security measures are you taking?
